LevelBlue Cybersecurity Training
Get expert instruction & hands-on practice with Unified Security Management.
- GETTING STARTED: Course Overview
- MODULE 1: Introduction to USM Anywhere
- MODULE 2: Setting up USM Anywhere
- MODULE 3: NIDS and Log Collection
- MODULE 4: A Tour of USM Anywhere
- MODULE 5: An Introduction to Sensor Apps and BlueApps™
- APPENDIX: ConnectWise Manage Integration
- APPENDIX: Threat Detection and Response for Government
Launchpad for USM Anywhere™
GETTING STARTED: COURSE OVERVIEW
This self-paced course gives security engineers, analysts, and project team members an introduction to USM Anywhere™. Get an overview of product setup, configuration and functionality so that you can start using USM Anywhere immediately!
MODULE 1: INTRODUCTION TO USM ANYWHERE


Introduction & Objectives • 2 Minutes
This video introduces Module 1 and defines the learning objectives.
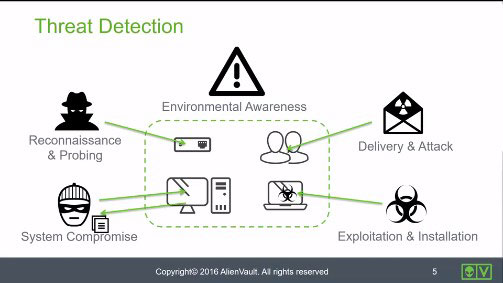

Threat Detection & Security Management • 11 Minutes
This video examines the threats that exist today, the challenges you face keeping your environment secure and how USM Anywhere can assist you through its 5 essential tools (Asset Discovery, Vulnerability Assessment, Intrusion Detection, Behavioral Monitoring, SIEM: Security Information and Event Management).


AlienVault Labs, OTX, & Threat Intelligence • 7 Minutes
This video introduces AlienVault Labs, our team of security researchers who work to keep up to date on the latest malware and attacker tools on the security landscape and provide AlienVault Threat Intelligence updates to USM Anywhere for targeted detection of the latest threats. We will also discuss the Open Threat Exchange® (OTX™), the world’s first open threat intelligence community, that enables collaborative defense with open access and collaborative research.
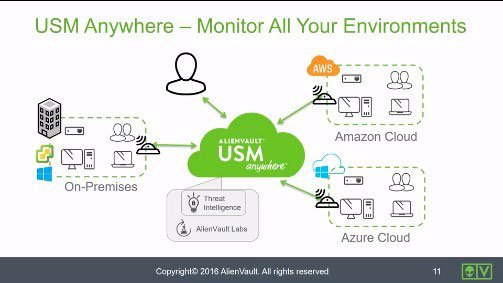

Monitoring All Your Environments • 2 Minutes
This video briefly introduces the USM Anywhere architecture and shows how your cloud based and on-site environments can be monitored from one central location, giving you a single pane of glass from which to view all your Assets.


Summary & Closing • 1 Minute
This video provides links to resources that may be useful if you are new to security operations. We also review what we have learned in Module 1.
MODULE 2: SETTING UP USM ANYWHERE

Introduction & Objectives • 2 Minutes
This video introduces Module 2 and defines the learning objectives.
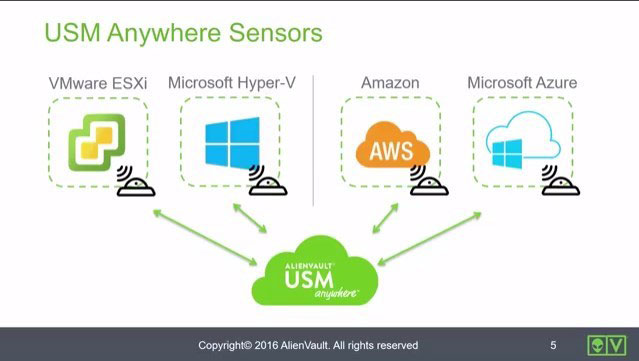

Sensor Overview • 2 Minutes
This video introduces the USM Anywhere Sensor. It describes the sensor's purpose and shows you the different sensor types available.
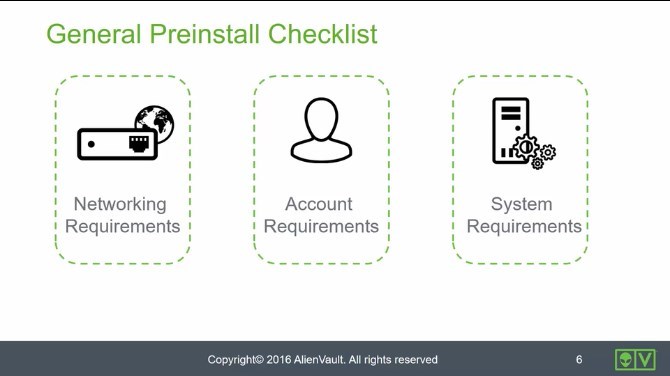

Preinstall Checklist • 6 Minutes
This video provides details to consider before starting the deployment of your first sensor to help everything run smoothly. We review a checklist that looks at networking, account, and system requirements.

Common Sensor Functionality • 2 Minutes
This video identifies the functionality that applies to all sensor types with one exception that we will highlight.
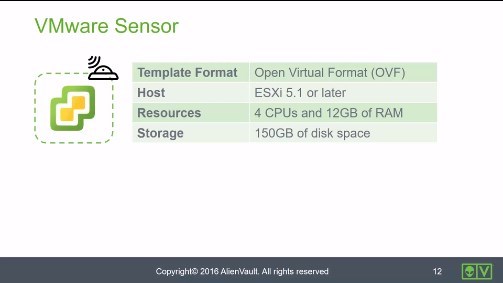

VMware Sensor • 2 Minutes
This video identifies the specifications and functionality that apply to the VMware ESXi sensor.
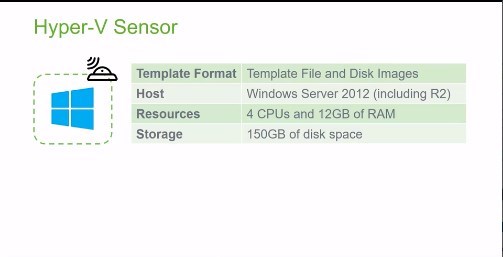

Microsoft Hyper-V Sensor • 2 Minutes
This video identifies the specifications and functionality that apply to the Microsoft HyperV sensor.


Amazon Web Services Sensor • 3 Minutes
This video identifies the specifications and functionality that apply to the Amazon Web Services sensor.
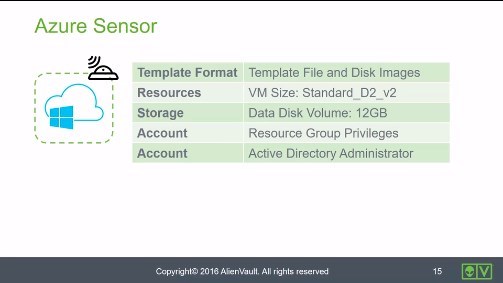

Microsoft Azure Sensor • 2 Minutes
This video identifies the specifications and functionality that apply to the Microsoft Azure sensor.
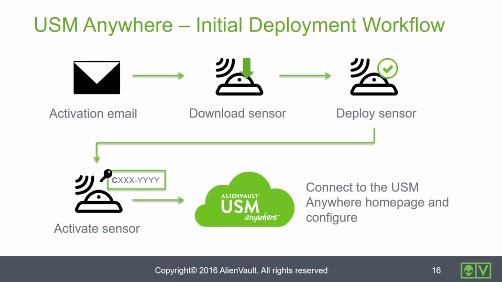

Initial Deployment Workflow • 2 Minutes
This video walks through overall workflow from a high level as it relates to setting up USM Anywhere for the first time.
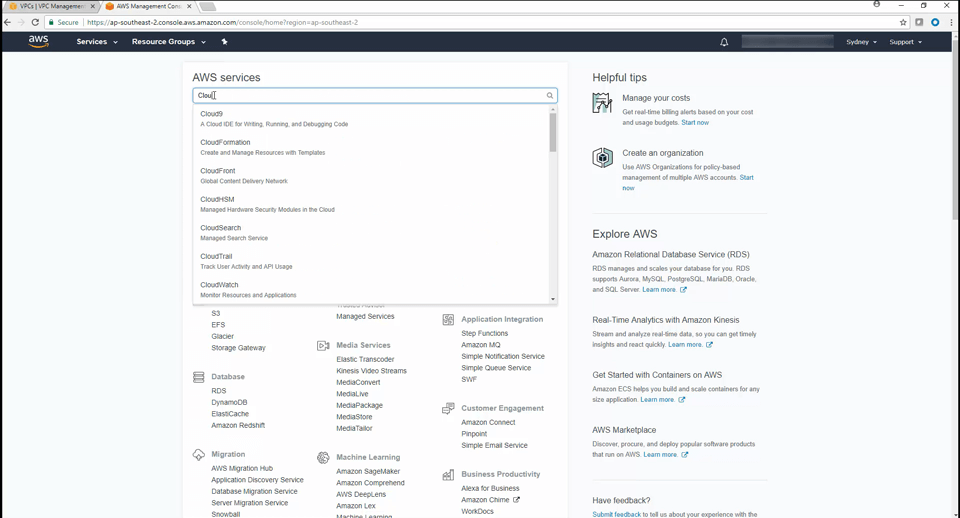

AWS Sensor Deployment Demo • 14 Minutes
This video demonstrates the initial deployment and configuration of an AWS sensor. It also demonstrates the sensor activation through the web UI. If you want to learn more about AWS sensor deployment, comprehensive documentation can be found on the AWS Sensor Deployment page.


CloudFormation Template Overview • 17 Minutes
This video reviews the contents of the CloudFormation template used to deploy the AWS Sensor. It explains what each section of the template is for and what it is doing in your AWS environment.
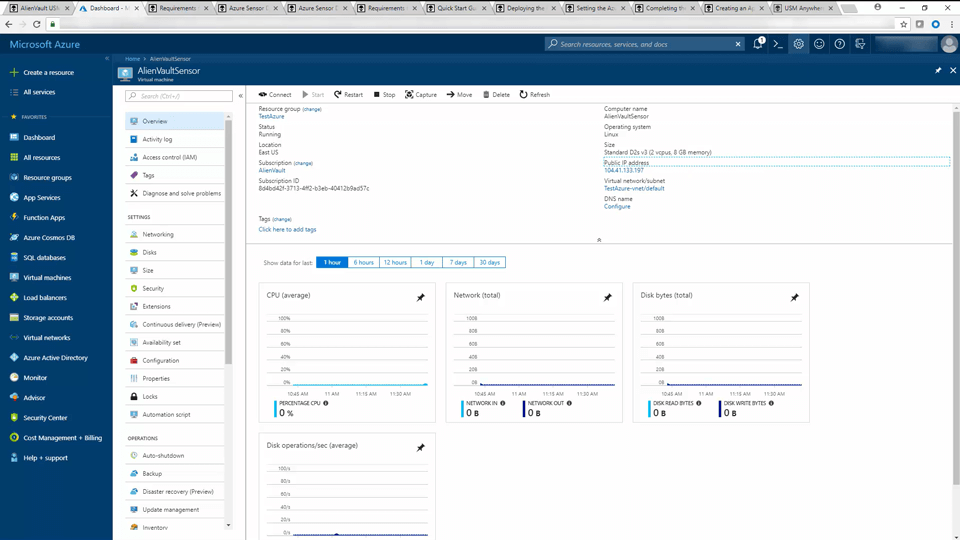

Azure Sensor Deployment Demo • 9 Minutes
This video demonstrates the initial deployment and configuration of an Azure sensor. It also demonstrates the sensor activation through the web UI. If you want to learn more about Azure sensor deployment, comprehensive documentation can be found on the Azure Sensor Deployment page
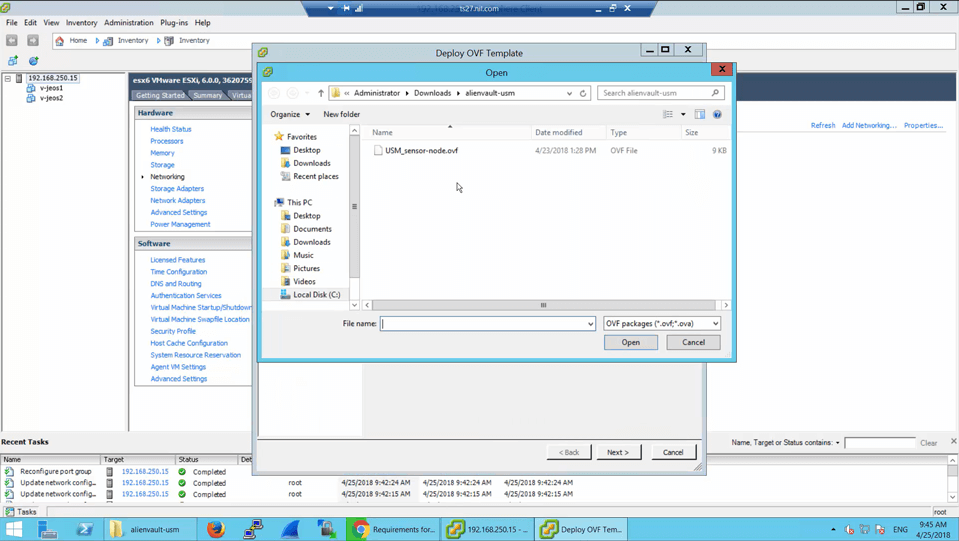

VMware Sensor Deployment Demo • 5 Minutes
This video demonstrates the initial deployment and configuration of a VMware sensor. It also demonstrates the sensor activation through the web UI. If you want to learn more about VMware sensor, comprehensive documentation can be found on the VMware Sensor Deployment page
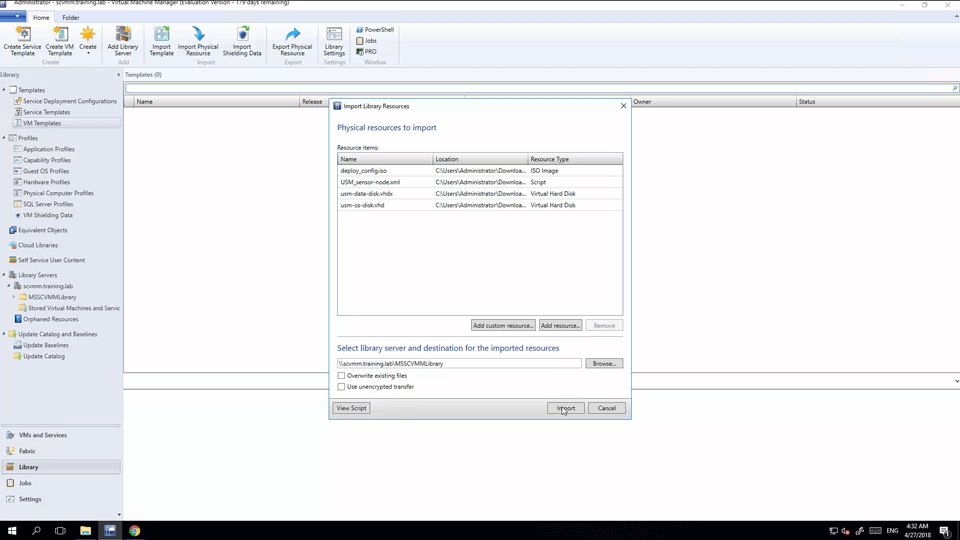

Hyper-V Sensor Deployment Demo • 6 Minutes
This video demonstrates the initial deployment and configuration of a Hyper-V sensor. It also demonstrates the sensor activation through the web UI. If you want to learn more about Hyper-V sensor deployment, comprehensive documentation can be found on the Hyper-V Sensor Deployment page
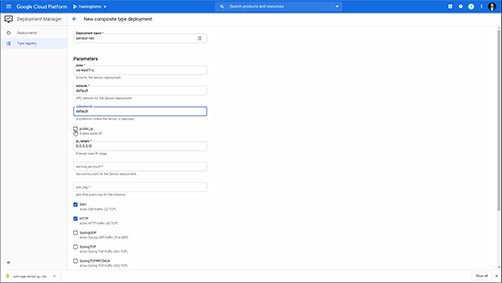

GCP Sensor Deployment Demo • 7 Minutes
This video demonstrates the initial deployment and configuration of a Google Cloud Platform sensor. It also demonstrates the sensor activation through the web UI. If you want to learn more about GCP sensor deployment, comprehensive documentation can be found on the GCP Sensor Deployment page.

Sensor Setup Wizard • 4 Minutes
This video demonstration walks through the VMware Sensor setup wizard, highlighting the purpose of each screen.


Connecting Additional Sensors • 4 Minutes
This video demonstrates the connection of an additional sensor to USM Anywhere. We will see how additional authentication codes are generated on the USM Anywhere web UI.
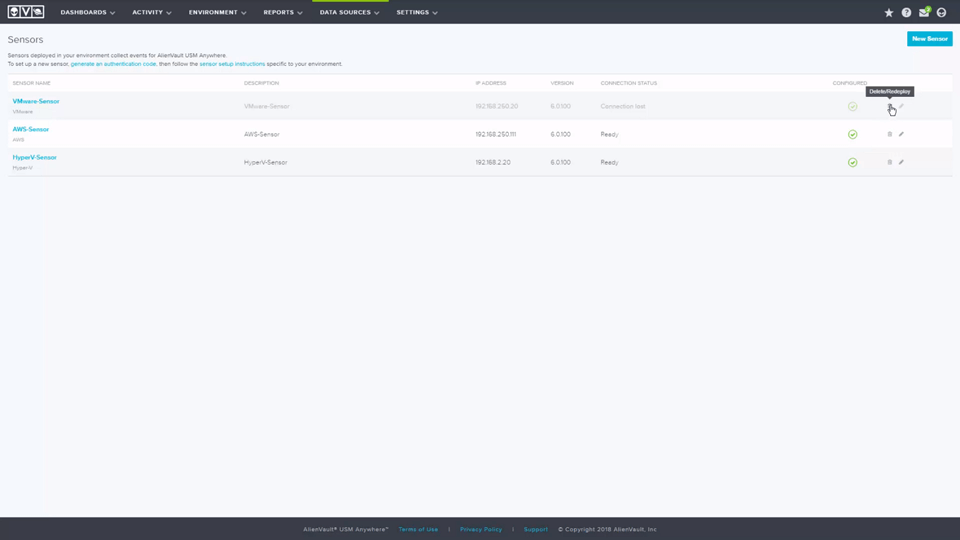

Sensor Redeployment Procedure • 3 Minutes
This video demonstrates how to replace an existing sensor with a newly deployed one. You will see the procedure to ensure that all assets, jobs, events and so on that were associated with the old sensor are retained and linked to its replacements. If you want to learn more about redeploying sensors , comprehensive documentation can be found on the Redeploying a Sensor page
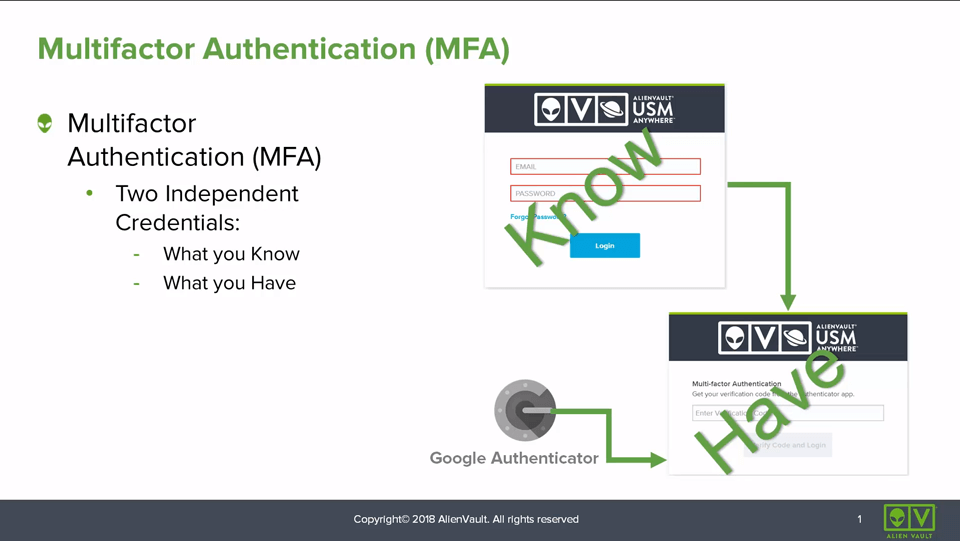

Multi-Factor Authentication • 5 Minutes
This video demonstrates how to configure Multi-Factor Authentication for USM Anywhere user accounts. If you want to learn more about Multi-Factor Authentication, comprehensive documentation can be found on the Using Multi-Factor Authentication page
MODULE 3: NIDS and Log Collection
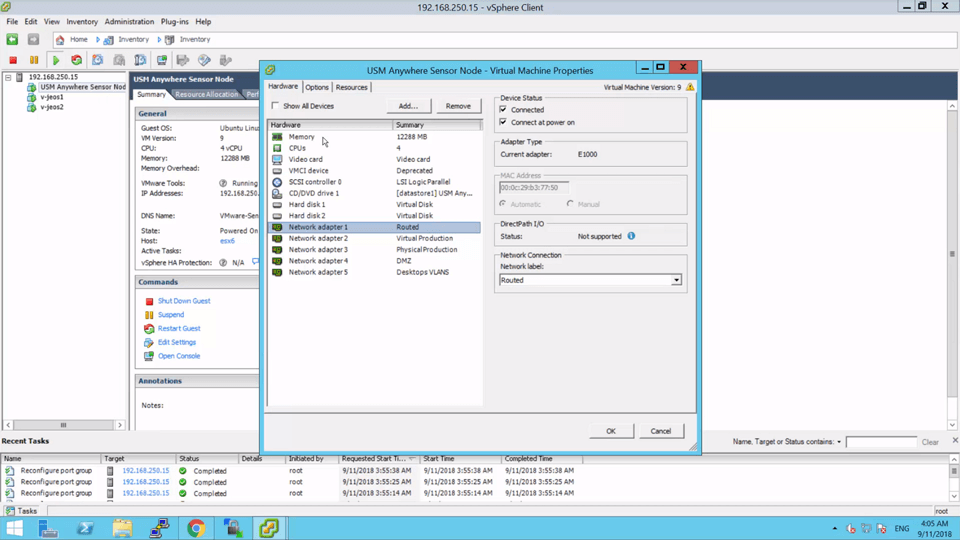

Configuring NIDS on VMware • 7 Minutes
This video demonstrates how to configure your VMware ESX server to forward both physical and virtual network traffic to your VMware Sensor for monitoring. If you want to learn more about configuring Network Intrusion Detection (NIDS) in your environment, comprehensive documentation can be found on the Network Setup and Configuration page

Configuring NIDS on HyperV • 4 Minutes
This video demonstrates how to configure your Microsoft HyperV server to forward both physical and virtual network traffic to your HyperV Sensor for monitoring. If you want to learn more about configuring Network Intrusion Detection (NIDS) in your environment, comprehensive documentation can be found on the Network Setup and Configuration page
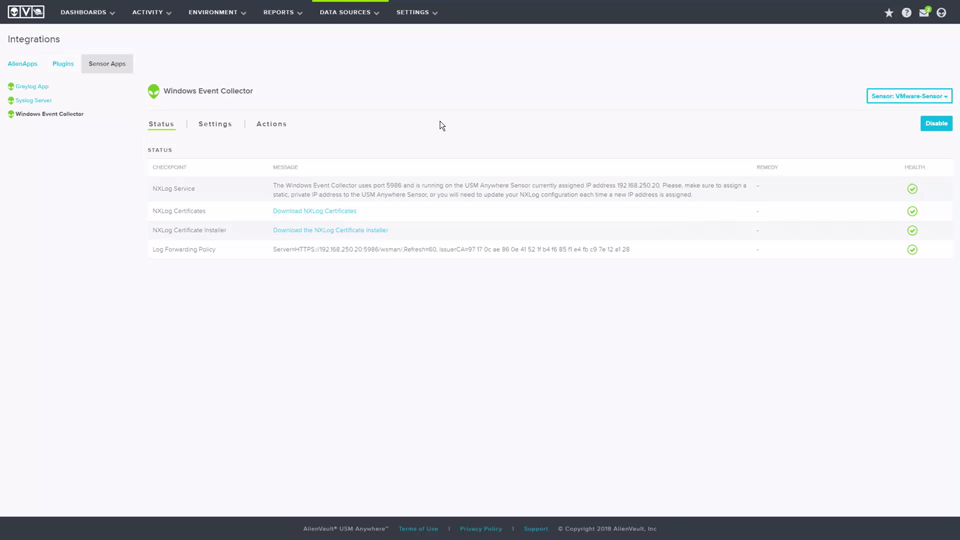

Configuring Windows Event Collection • 4 Minutes
This video demonstrates how to configure your Microsoft Windows Server 2008 (or newer) to forward logs to a sensor using Windows Event Forwarding. You will see how to install the required certificate on your system and how the group policy can be updated to forward the events. If you want to learn more about configuring Windows Event Collection in your environment, comprehensive documentation can be found on the Using the Windows Event Collector Sensor App page

Configuring CloudTrail (AWS) • 5 Minutes
This video demonstrates how to configure AWS to capture CloudTrail Logs which monitors account activity from your environment. You will then see how USM Anywhere is configured to retrieve and analyse this information to create events. If you want to learn more about configuring USM Anywhere to monitor CloudTrail Logs, comprehensive documentation can be found on the AWS Log Discovery and Collection in USM Anywhere page
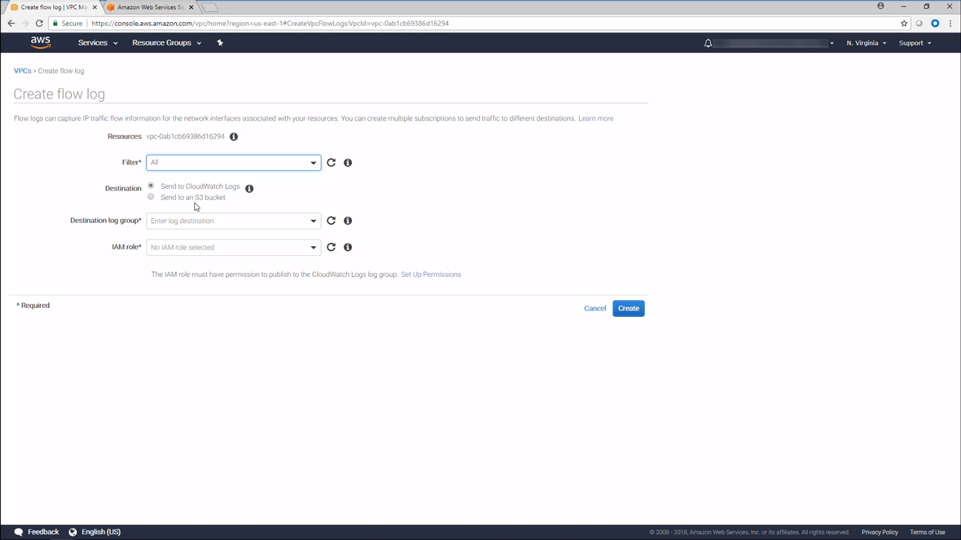

Configuring VPC Flow Log Collection (AWS) • 14 Minutes
This video demonstrates how to configure AWS to capture VPC Flow Logs which represent network information from your environment. You will then see how USM Anywhere is configured to retrieve and analyse this information to create events. If you want to learn more about configuring USM Anywhere to monitor VPC Flow Logs, comprehensive documentation can be found on the Amazon VPC Flow Logs page

Configuring the CloudWatch Agent (AWS) • 9 Minutes
This video demonstrates how to configure AWS CloudWatch Agent on an asset so it will send its logs to CloudWatch. You will then see how USM Anywhere is configured to retrieve and analyse this information to create events. If you want to learn more about configuring USM Anywhere to monitor CloudWatch, comprehensive documentation can be found on the AWS Log Discovery and Collection in USM Anywhere page
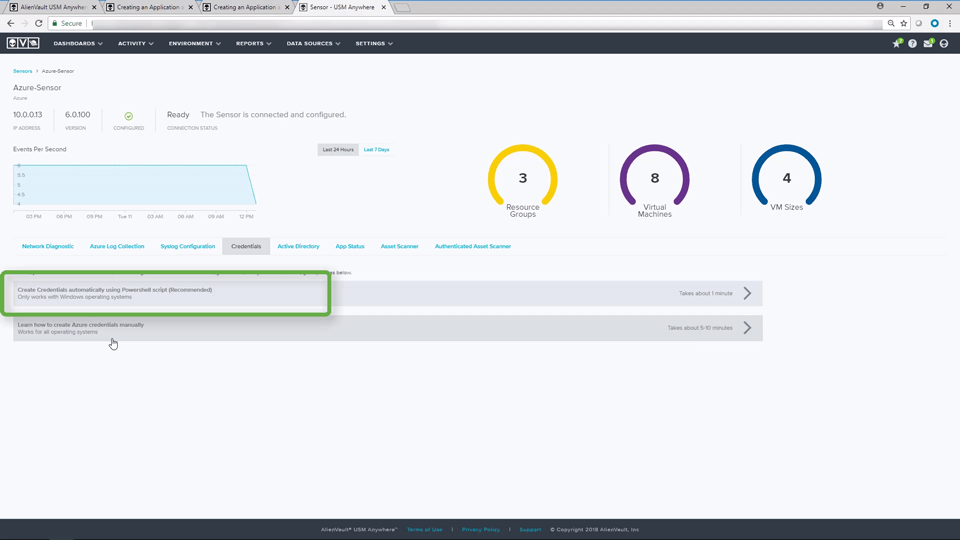

Configuring Azure Sensor Credentials • 8 Minutes
This video demonstrates how to obtain Azure credentials and configure your USM Anywhere sensor to communicate with Azure. You will see how to obtain all the required credentials using a powershell script and where to enter these details in USM Anywhere. If you want to learn more about configuring USM Anywhere to communicate with Azure, comprehensive documentation can be found on the Creating an Application and Obtaining Azure Credentials page
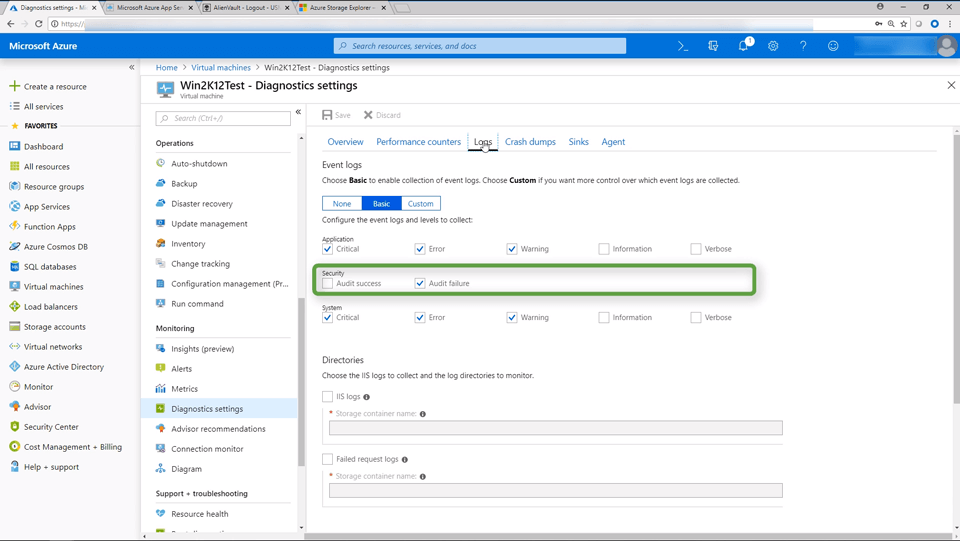

Configuring Azure Agent Logging (Windows) • 14 Minutes
This video demonstrates how to enable Azure agent logging on a Windows asset. You will see how to configure event log collection and configure the scheduled job to pull the logs from Azure. If you want to learn more about configuring Azure Agent Logging, comprehensive documentation can be found on the Azure Log Discovery and Collection in USM Anywhere page
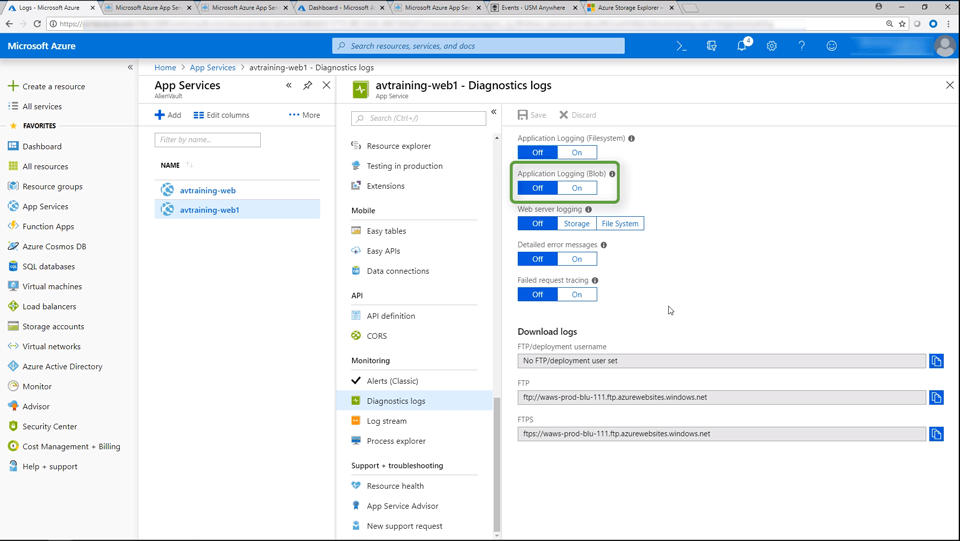

Configuring Azure Web App Logging • 10 Minutes
This video demonstrates how to enable Azure Web App logging. You will see how to configure diagnostic (application) logging and configure the scheduled job to pull the logs from Azure. If you want to learn more about configuring Azure Web App Logging, comprehensive documentation can be found on the Azure Log Discovery and Collection in USM Anywhere page


Endpoint Detection & Response (EDR) • 14 Minutes 54 SECONDS
This video introduces you to the AlienVault Agent. The AlienVault Agent extends the Endpoint Threat Detection and Response (EDR) capabilities of AlienVault® USM Anywhere™. It includes host-based threat detection, file integrity monitoring, Windows log collection and response actions, all without a sensor. Each agent will talk directly to AlienVault® USM Anywhere™. This makes the agent particularly useful for monitoring remote assets.
MODULE 4: A TOUR OF USM ANYWHERE


A Tour of USM Anywhere - Demo • 10 Minutes
In this video we hear from Garrett Gross, our Director of Field Enablement at AlienVault. He will take you through some of the benefits and additional value USM Anywhere has to offer, focused on how you or your team might leverage USM Anywhere on a day-to-day basis.
Module 5: AN INTRODUCTION TO SENSOR APPS AND ALIENAPPS™

Sensor Apps and AlienApps • 27 Minutes
This video introduces you to Sensor Apps and AlienApps™ in USM Anywhere. We define the differences between the two app types, showing the actions that can be leveraged and how these actions can be invoked through use cases for each type. Finally, we provide a demonstration of the Sensor Apps and AlienApps™ UI.

Introduction and Overview • 2 Minutes
This video introduces you to the series on USM Anywhere’s AlienApps. AlienApps provide integrations with third-party security and productivity tools to extend your security orchestration capabilities. If you want to learn more, comprehensive AlienApp documentation can be found on the AlienApps™ Guide page.

Cisco Umbrella AlienApp • 10 Minutes
This video introduces you to the Cisco Umbrella AlienApp and details how it integrates with Cisco Umbrella to provide both detection and response capabilities. If you want to learn more, comprehensive Cisco Umbrella AlienApp documentation can be found on the AlienApp for Cisco Umbrella page.


Jira AlienApp • 6 Minutes
This video introduces you to the Jira AlienApp and details how it integrates with Jira Service Desk and Jira Software to allow you to create and track tickets directly from USM Anywhere. If you want to learn more, comprehensive Jira AlienApp documentation can be found on the AlienApp for Jira page

G Suite AlienApp • 5 Minutes
This video introduces you to the G Suite AlienApp and details how it integrates with G Suite to allow you to monitor user access, privilage escalation, file access and actions from USM Anywhere. If you want to learn more, comprehensive G Suite AlienApp documentation can be found on the AlienApp for G Suite page.

Office 365 AlienApp • 8 Minutes
This video introduces you to the Office 365 AlienApp and details how it integrates with Office 365 to allow you to monitor user access, privilege escalation, Exchange mailbox activity and the presence of potential ransomware on OneDrive and SharePoint. If you want to learn more, comprehensive Office 365 AlienApp documentation can be found on the AlienApp for Office 365 page.
Appendix: CONNECTWISE MANAGE INTEGRATION
NOTE: This module only applies to customers who have purchased USM Anywhere ConnectWise Edition directly from ConnectWise.
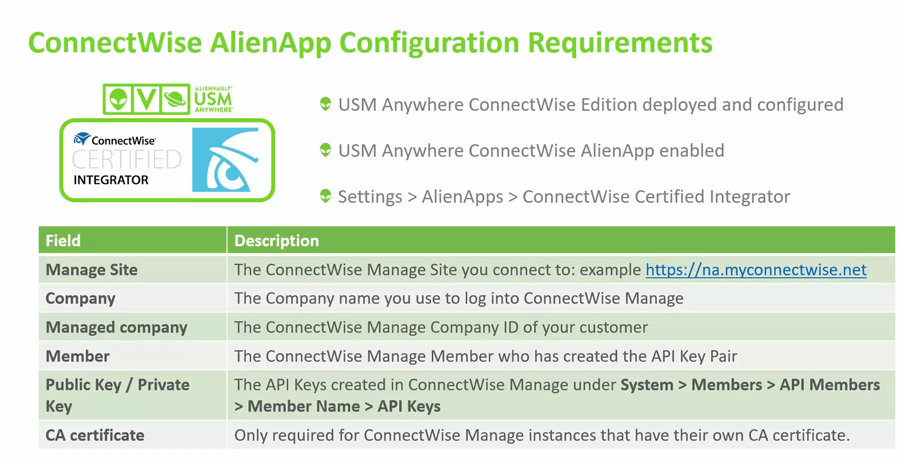

Overview of ConnectWise Manage Integration • 5 Minutes
This video introduces the ConnectWise AlienApp™ providing details on the functionality it offers when integrated with ConnectWise Manage. It also provides a summary of the configuration requirements to be aware of for a smooth integration.


Preparing ConnectWise Manage for Integration • 4 Minutes
This video demonstration identifies the required information you will need to gather from ConnectWise Manage to configure the ConnectWise AlienApp™. This will include the creation of the Public / Private API Key pair.

Configuring the ConnectWise AlienApp™ • 7 Minutes
This video demonstration walks through the configuration of the ConnectWise AlienApp™. It will examine the ConnectWise AlienApp structure and the scheduled jobs created to synchronize Assets, Alarms, and Vulnerabilities with ConnectWise Manage. Finally, it identifies how to confirm that information is flowing to ConnectWise Manage.

Reviewing the Integration Functionality • 4 Minutes
This video demonstrates how to access the USM Anywhere Web UI directly from ConnectWise Manage. It will also identify Alarms and Vulnerabilities in USM Anywhere and correlate them to the Service Tickets created in ConnectWise Manage.
Appendix: Threat Detection and Response for Government


Introduction and Objectives • 3 Minutes
This video introduces Module 1 and defines the learning objectives.

Connecting Sensors • 3 Minutes
This video demonstrates the connection of a sensor. We will see how authentication codes are generated on the web UI.

GCP Sensor deployment • 13 Minutes
This video demonstrates the initial deployment and configuration of a Google Cloud Platform sensor. It also demonstrates the sensor activation through the web UI. If you want to learn more about GCP sensor deployment, comprehensive documentation can be found on the GCP Sensor Deployment page.


AWS Sensor deployment • 14 Minutes
This video demonstrates the initial deployment and configuration of an AWS sensor. It also demonstrates the sensor activation through the web UI. If you want to learn more about AWS sensor deployment, comprehensive documentation can be found on the AWS Sensor Deployment page.

Azure Sensor Deployment • 12 Minutes
This video demonstrates the initial deployment and configuration of an Azure sensor. It also demonstrates the sensor activation through the web UI. If you want to learn more about Azure sensor deployment, comprehensive documentation can be found on the Azure Sensor Deployment page.


VMware Sensor deployment • 5 Minutes
This video demonstrates the initial deployment and configuration of a VMware sensor. It also demonstrates the sensor activation through the web UI. If you want to learn more about VMware sensor, comprehensive documentation can be found on the VMware Sensor Deployment page.


HyperV Sensor deployment • 6 Minutes
This video demonstrates the initial deployment and configuration of a Hyper-V sensor. It also demonstrates the sensor activation through the web UI. If you want to learn more about Hyper-V sensor deployment, comprehensive documentation can be found on the Hyper-V Sensor Deployment page.
Launchpad for USM Appliance
GETTING STARTED: COURSE OVERVIEW
This self-paced course gives security engineers, analysts, and project team members an orientation to USM Appliance™. It is designed to accelerate your awareness of the full range of features in the USM platform, making you more effective on day one.


Course Overview • 4 Minutes
This video provides and overview of the AlienVault USM Appliance Launchpad course including learning objectives, target audience, and requirements.
MODULE 1: USM APPLIANCE OVERVIEW


USM Appliance Overview • 13 Minutes
This video introduces AlienVault Unified Security Management® (USM) and describes in detail the five essential tools: Asset Discovery, Vulnerability Assessment, Intrusion Detection, Behavioral Monitoring, SIEM: Security Information and Event Management.

USM Appliance Architecture • 9 Minutes
This video describes USM Appliance architecture, emphasizing the function of the Sensor, Server, and Logger, and details how information flows between these components.

Open Threat Exchange® (OTX™) & AlienVault Labs • 6 Minutes
This video introduces AlienVault Labs, our team of security researchers who work to keep up to date on the latest malware and attacker tools on the security landscape and provide AlienVault Threat Intelligence updates to USM Appliance for targeted detection of the latest threats. We will also discuss the Open Threat Exchange® (OTX™), the world’s first open threat intelligence community, which enables collaborative defense with open access and collaborative research.
MODULE 2: VERIFYING OPERATIONS

User Interface • 13 Minutes
This video describes the USM Appliance UI in detail, going through the primary, secondary, and utility menus.
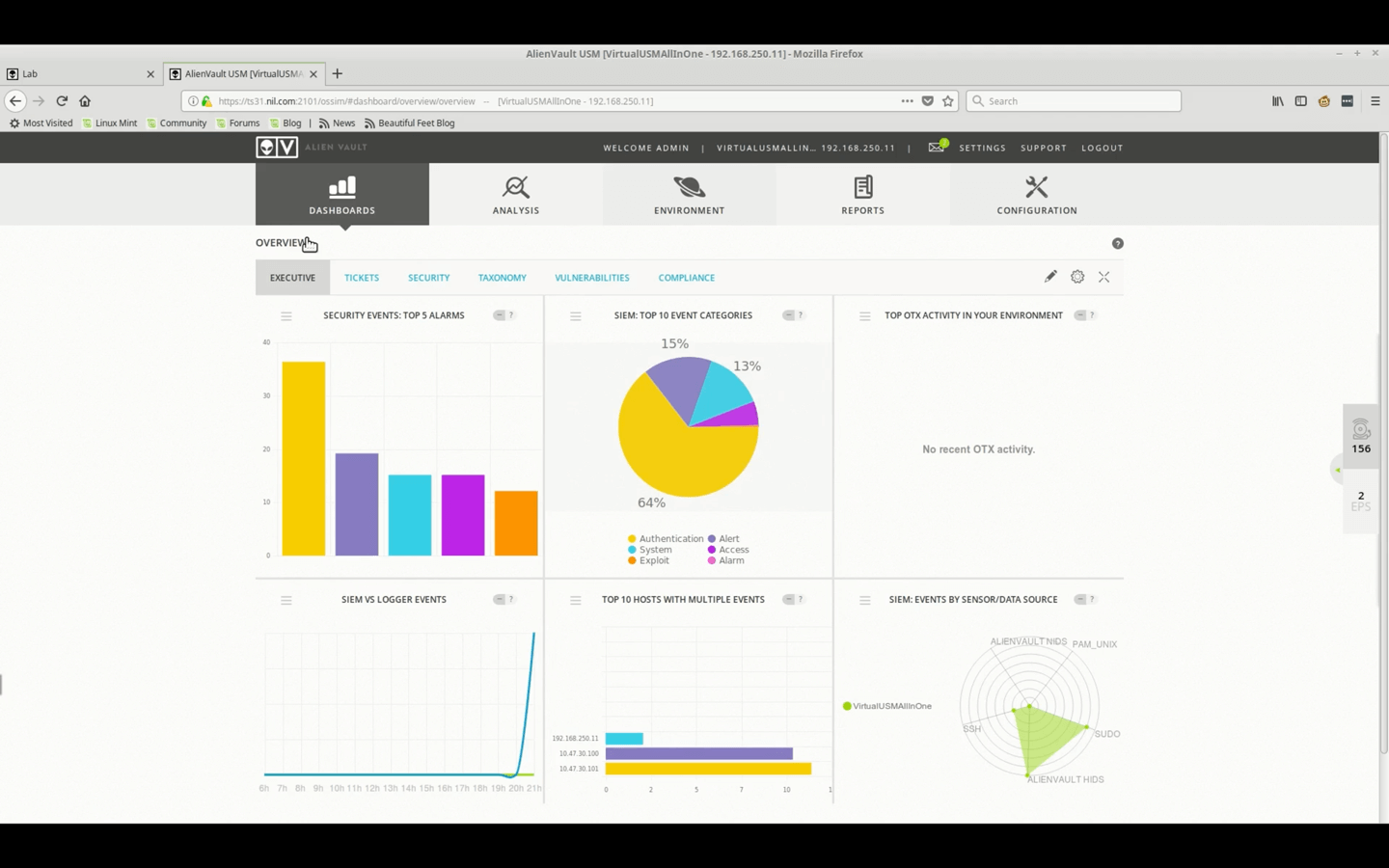

User Interface Demo • 7 Minutes
This video demonstrates the USM Appliance UI, going through a variety of the primary, secondary, and utility menus.


Verifying Operations • 6 Minutes
This video shows how to verify that USM Appliance is configured correctly to receive and process data so you are alerted to threats in your environment.
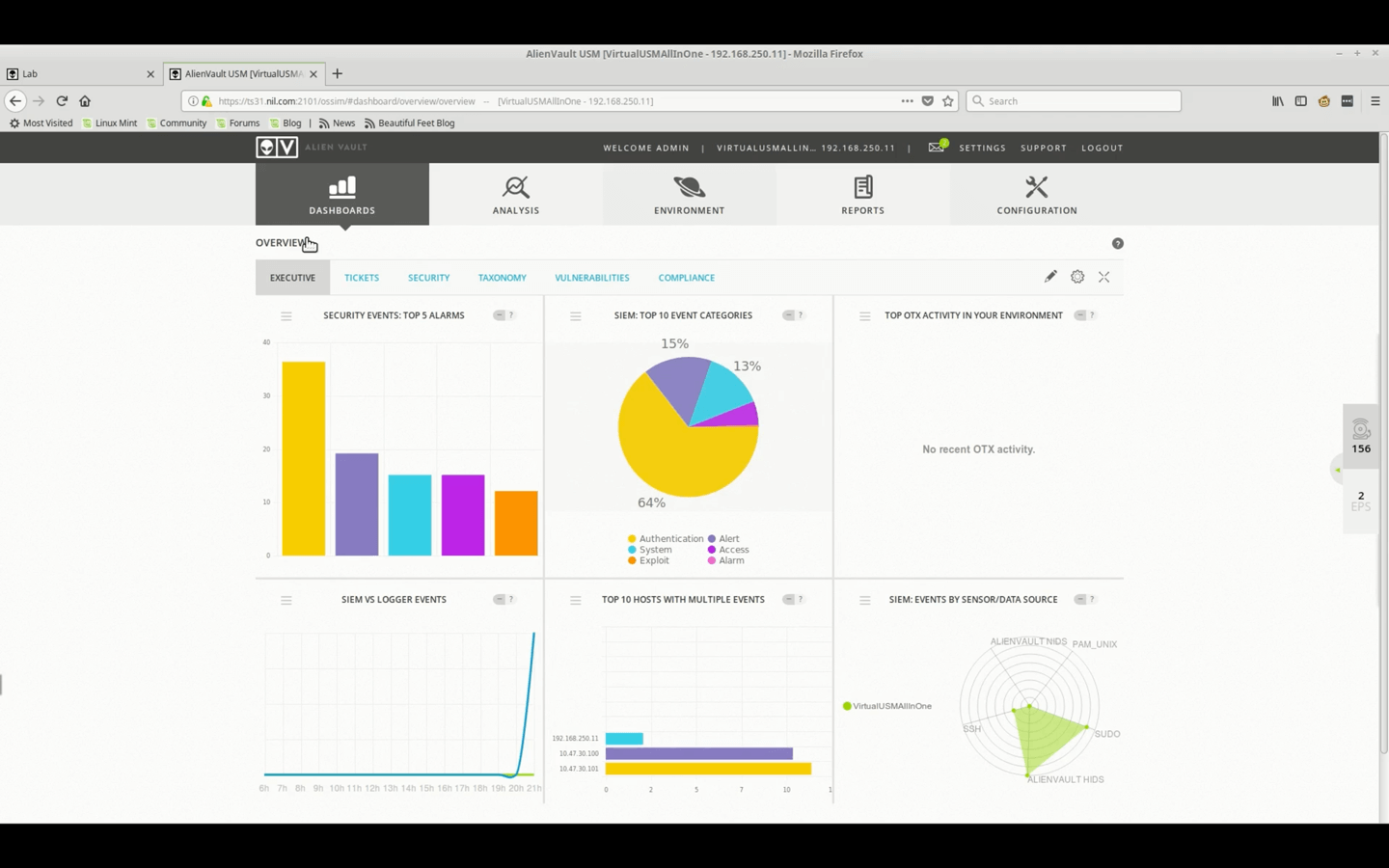

Verifying Operations Demo • 14 Minutes
This video demonstration will show how to validate that events, alarms, and raw logs are flowing and being displayed correctly.
MODULE 3: ASSET MANAGEMENT


Asset Overview • 11 Minutes
This video introduces Assets as they apply to USM Appliance. We go into detail on how Assets are presented in the web UI, including all associated functionality.


Asset Management • 20 Minutes
This video reviews how to manage Assets and their details in USM Appliance. We also introduce the concept of Asset Values and explain their importance.


Adding Assets • 13 Minutes
This video explains all the methods for adding Assets into USM Appliance. We will review adding Assets manually, importing from a CSV file, importing from SIEM Events, and importing through Asset Discovery Scans.
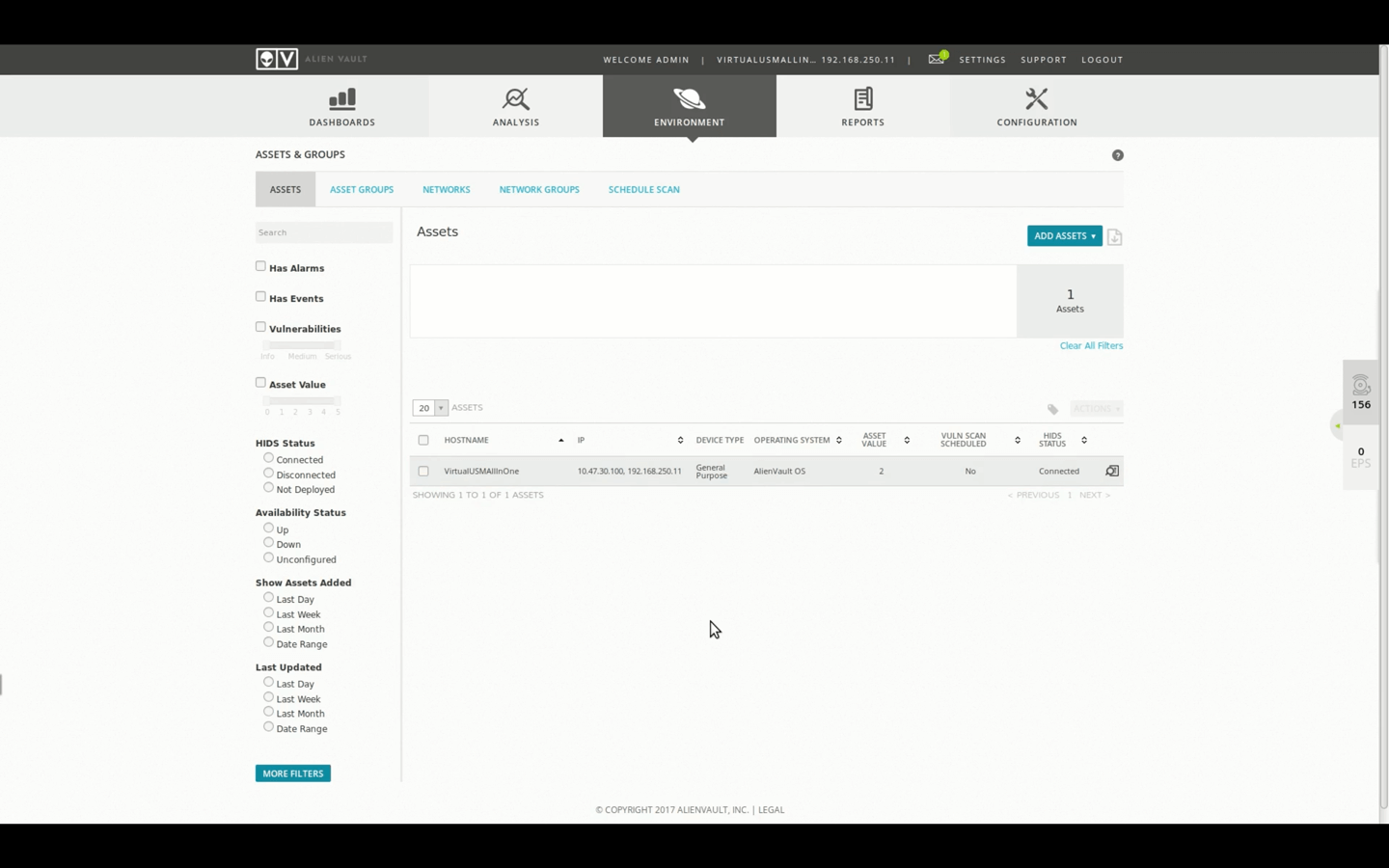

Adding and Managing Assets Demo • 20 Minutes
This video demonstrates how Assets can be added into USM Appliance. We will then see how the newly added Asset can be managed.
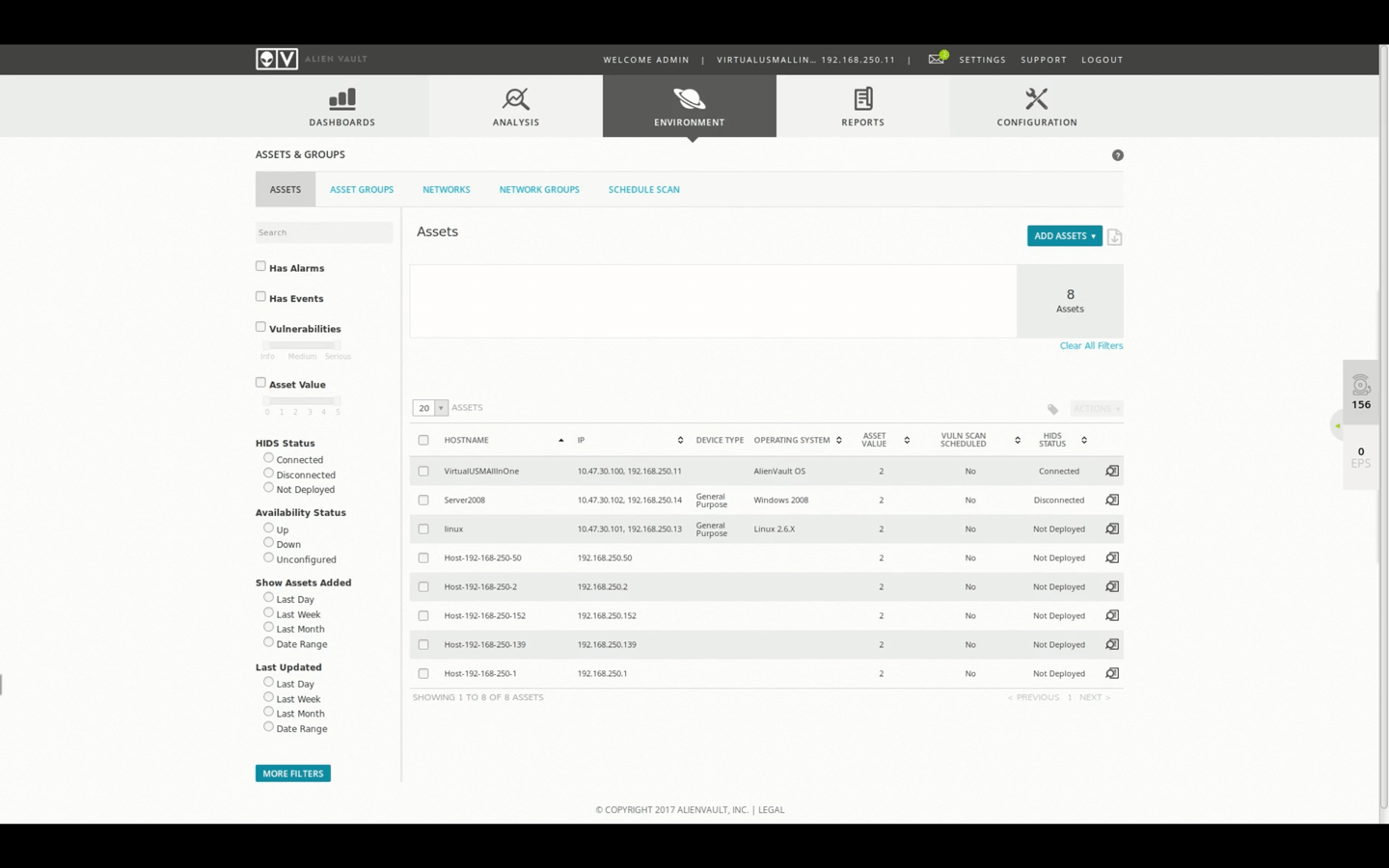

Asset Organization Demo • 18 Minutes
This video demonstrates how Assets can be organized in USM Appliance. This is achieved through the use of Asset Groups, Networks, Network Groups, and Asset Labels.
MODULE 4: POLICIES


Introduction to Policies • 17 Minutes
This video explains the flow of Events in the USM Appliance Server as it applies to Policies and Correlation Directives. We will look at the components that make up a Policy Rule and the considerations around creating Policies.
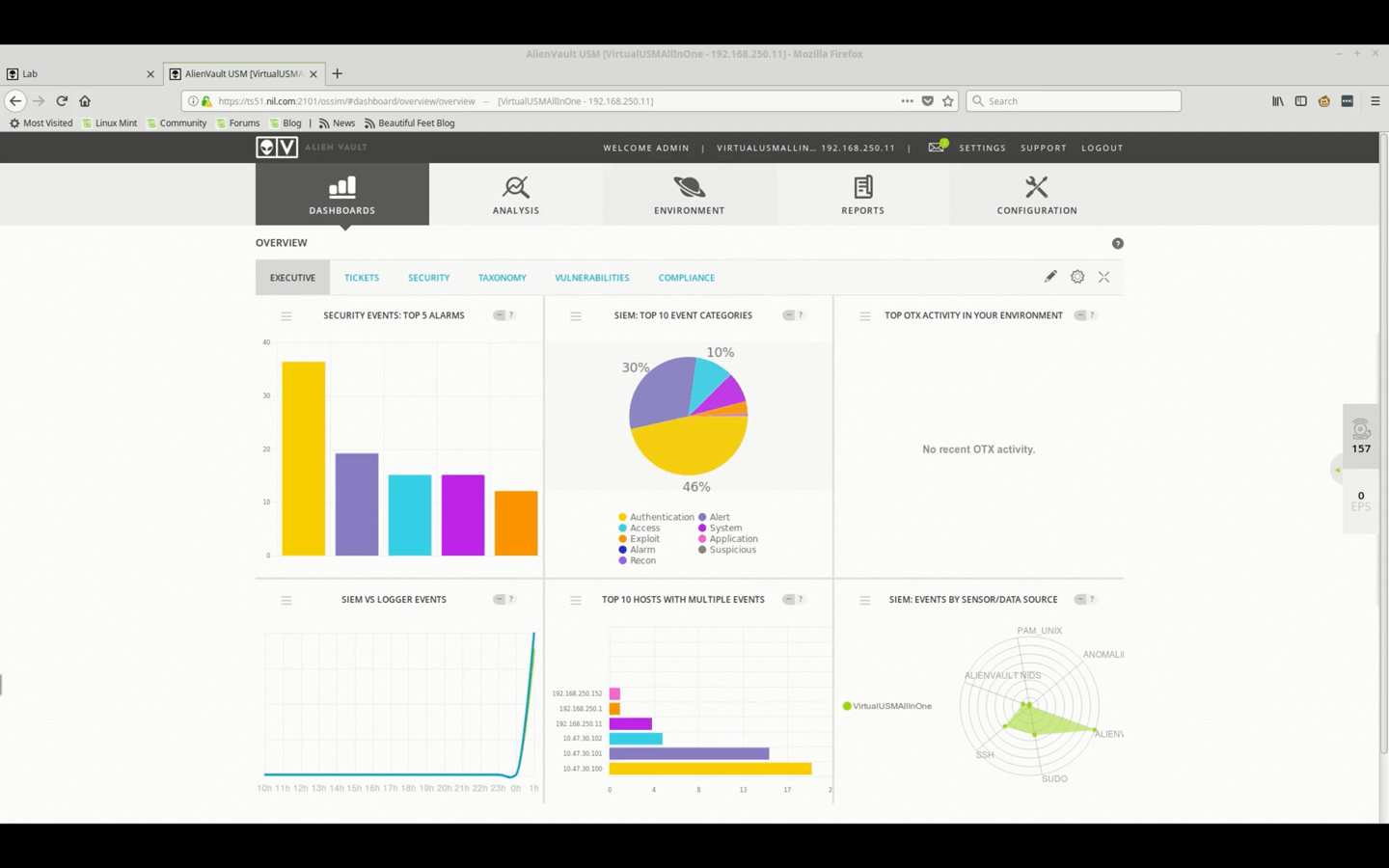

Policy Demo - Primary Events • 28 Minutes
This video demonstrates how Policies can be created for Events that are received by USM Appliance as HIDS or NIDS information. It will show all the criteria involved as well as the actions that can be triggered by the Policy.
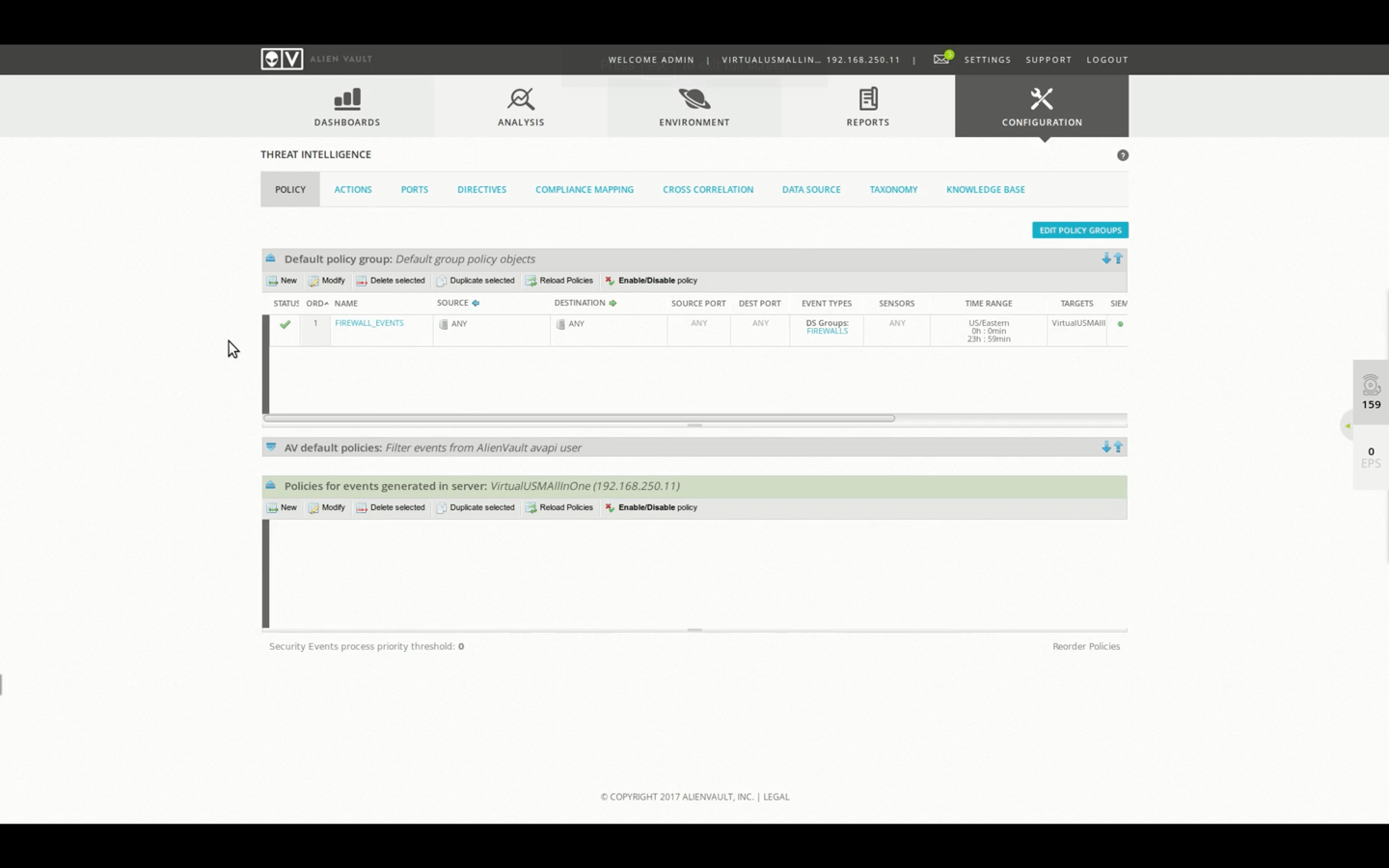

Policy Demo - Directive Events • 12 Minutes
This video demonstrates how Directive Events can be created under Policies, and outlines the differences from Primary Events.
MODULE 5: SECURITY ANALYSIS


Introduction to Security Analysis • 14 Minutes
This video introduces the USM Appliance security analysis process. It also reviews the Alarm remediation process to help you validate an Alarm, put measures in place to address the issue, and plan to implement solutions so security incidents can be avoided in the future.
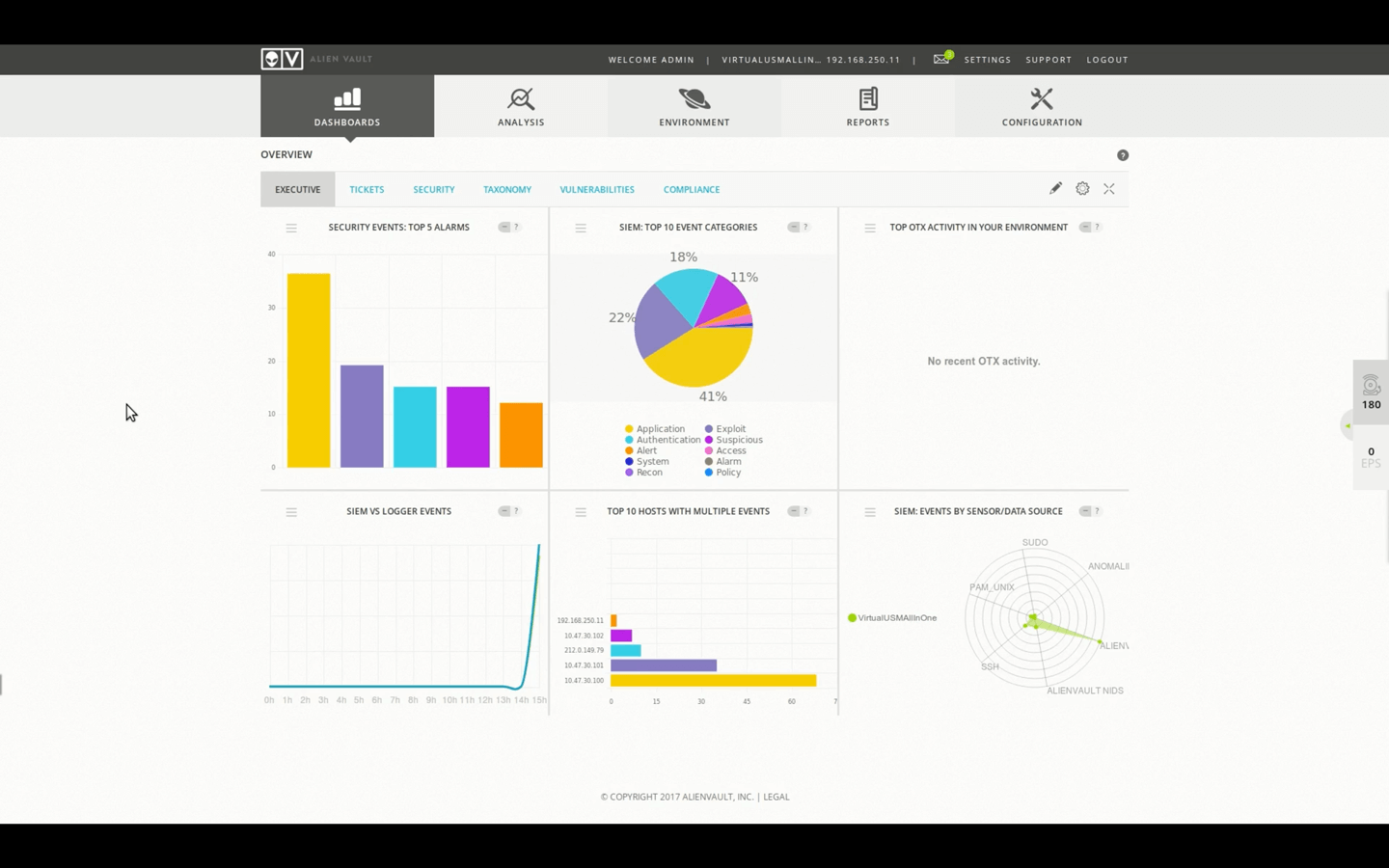

Security Analysis - Dashboards and Ticketing Demo • 24 Minutes
This video demonstrates how you can begin with security analysis in USM Appliance, highlighting how to leverage the dashboards and the ticketing system to aid you in the process of accessing the health of your environment.
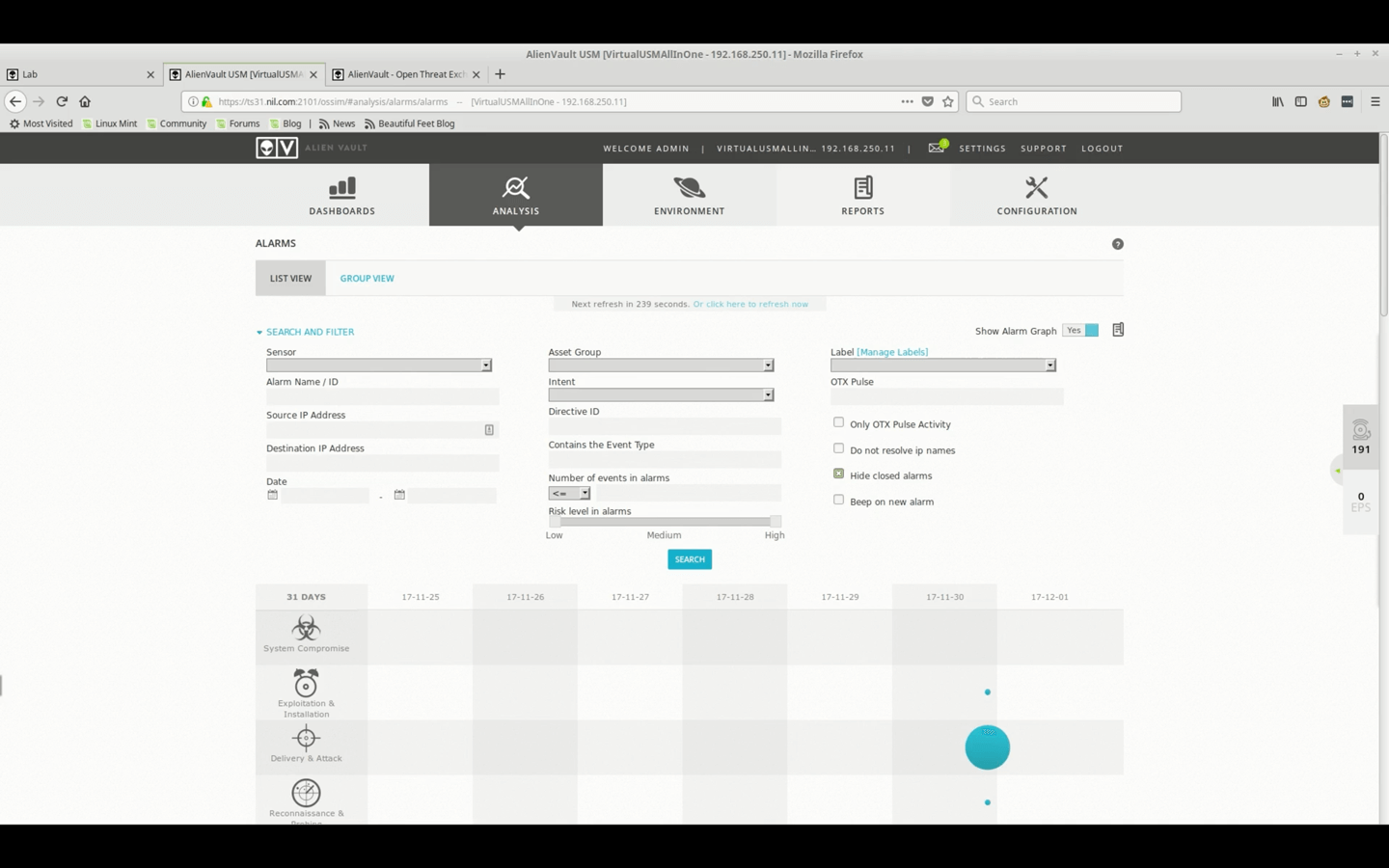

Security Analysis - Investigating Alarms Demo • 36 Minutes
This video demonstrates how to investigate Alarms in USM Appliance. It looks at Alarm priority, the Events that triggered the Alarm, and their underlying logs.
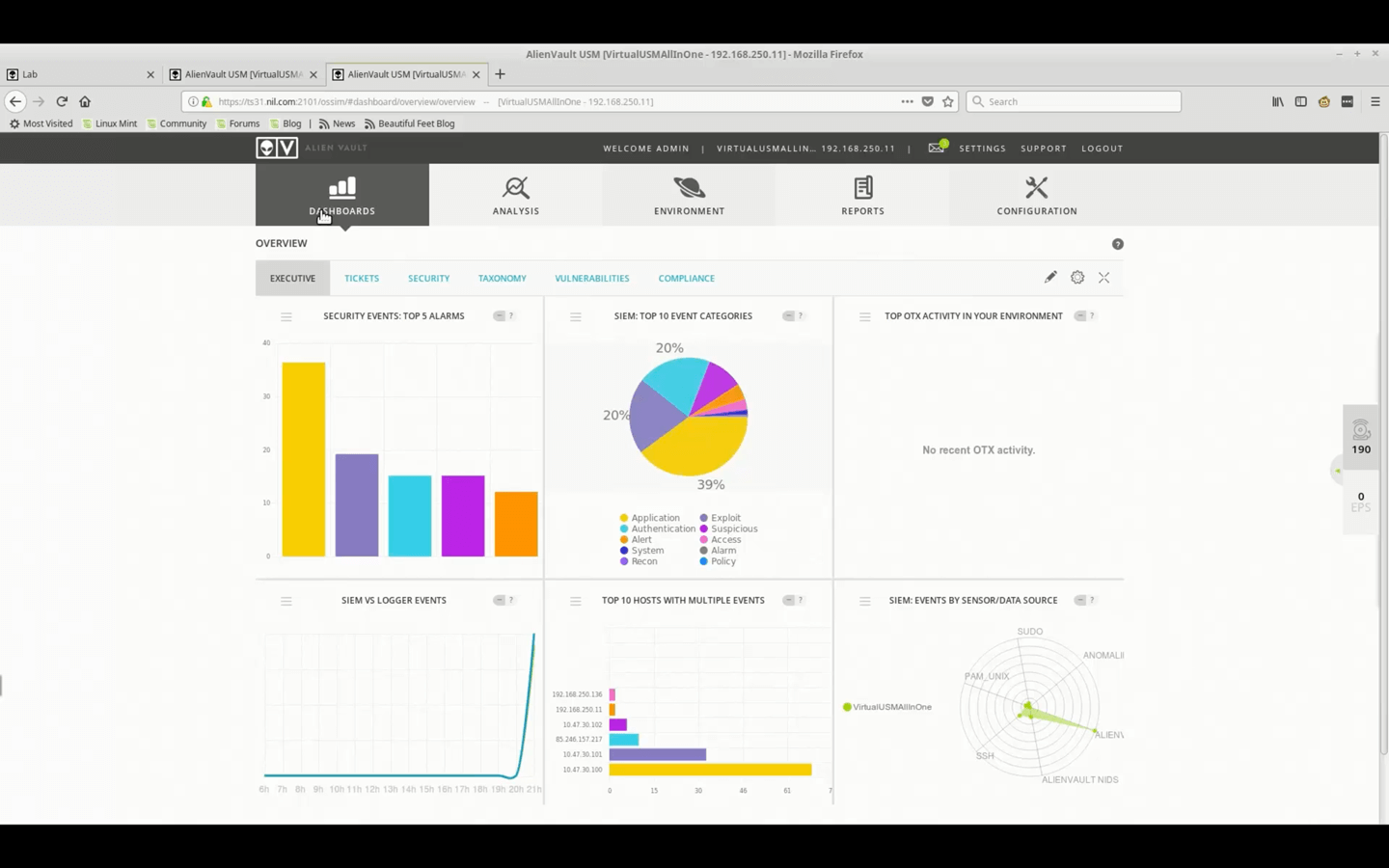

Vulnerabilities, Reporting and Raw Logs Demo • 22 Minutes
This video examines the Asset Vulnerability information that can be discovered in USM Appliance. It also examines the reporting capabilities available, as well as detailing how to query and export raw logs.
Launchpad for USM Central™
Getting Started: Course Overview
This self-paced course gives Managed Security Service Providers (MSSPs), Managed Service Providers (MSPs), and enterprise customers an orientation to USM Central™. It is designed to introduce you to the USM Central platform and show you how you can connect existing USM Anywhere™ and USM Appliance™ deployments. You will also see how USM Central collects and centralizes alarm details to deliver a consolidated view into threats that have been identified, so you can respond quickly and effectively.

Course Overview and Objectives • 1 Minutes
This video provides an overview of the USM Central Launchpad course including learning objectives, target audience, and requirements.
Module 1: Introduction to USM Central

Introduction to USM Central • 7 Minutes
This video introduces you to USM Central and reviews its capabilities. It includes a recorded demonstration of USM Central and an orientation of the web UI.
MODULE 2: Adding USM Anywhere to USM Central

Adding USM Anywhere to USM Central • 4 Minutes
This video describes how an existing USM Anywhere deployment is connected to USM Central. It includes a recorded demonstration of the steps involved in configuring the connection, and shows how the USM Anywhere information is represented.
MODULE 3: Adding USM Appliance to USM Central

Adding USM Appliance to USM Central • 4 Minutes
This video describes how an existing USM Appliance deployment is connected to USM Central. It includes a recorded demonstration of the steps involved in configuring the connection, and shows how the USM Appliance information is represented.
Module 4: Role-Based Access Controls

Role-Based Access Controls • 6 Minutes
This video describes how USM Central implements role-based access control. This video includes a recorded demonstration of the steps involved in configuring Role-Based Access Control within USM Central.
Module 5: Orchestration Rules Management

Orchestration Rules Management • 4 Minutes
This video describes how USM Central manages and shares orchestration rules between connected USM Anywhere deployments. This video includes a recorded demonstration of the steps involved in configuring, creating, filtering, disabling/enabling, and sharing rules within USM Central.
Module 6: Application Programming Interface (API) Framework
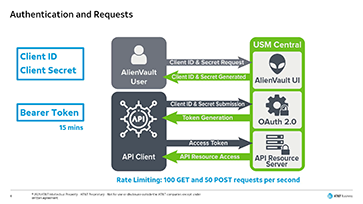

USM Central API Overview • 4 Minutes
This video introduces you to the USM Central API and describes how to authenticate and make requests to obtain information about alarms in USM Central. If you want to learn more, comprehensive documentation can be found on the USM Central API page.

USM Central API Authentication Demo • 9 Minutes
This video demonstrates how to obtain a Client ID and Secret from USM Central. We then show you how these credentials can be used to authenticate against OAuth 2.0 to obtain an access token which enables you to make requests against the USM Central API. If you want to learn more, comprehensive documentation can be found on the USM Central API page.
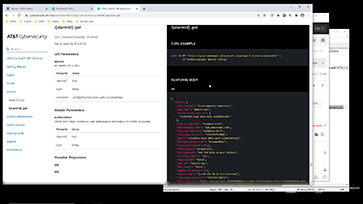

USM Central API Request Demo • 7 Minutes
This video demonstrates how to use the bearer token obtained in the previous demo to make request for alarm information against the USM Central API. We look at the request structure and identify how it can be modified to obtain specific information. If you want to learn more, comprehensive documentation can be found on the USM Central API page.
Tell Us What You Think!
We value your feedback and would love to know your thoughts on our Launchpad for USM. We would greatly appreciate you taking a few moments to complete our survey!