LevelBlue Managed Threat Detection and Response
LevelBlue Managed Threat Detection and Response
Protect your organization with 24x7 security monitoring powered by our award-winning LevelBlue USM platform and LevelBlue Labs™ threat intelligence.
Overview
Break through the cost and complexity of protecting your business
Improve your defenses against advanced threats in the cloud and on premises
Scale your security and compliance efforts without complexity or hiring constraints
Get started detecting and responding to threats in as little as 30 days
Features
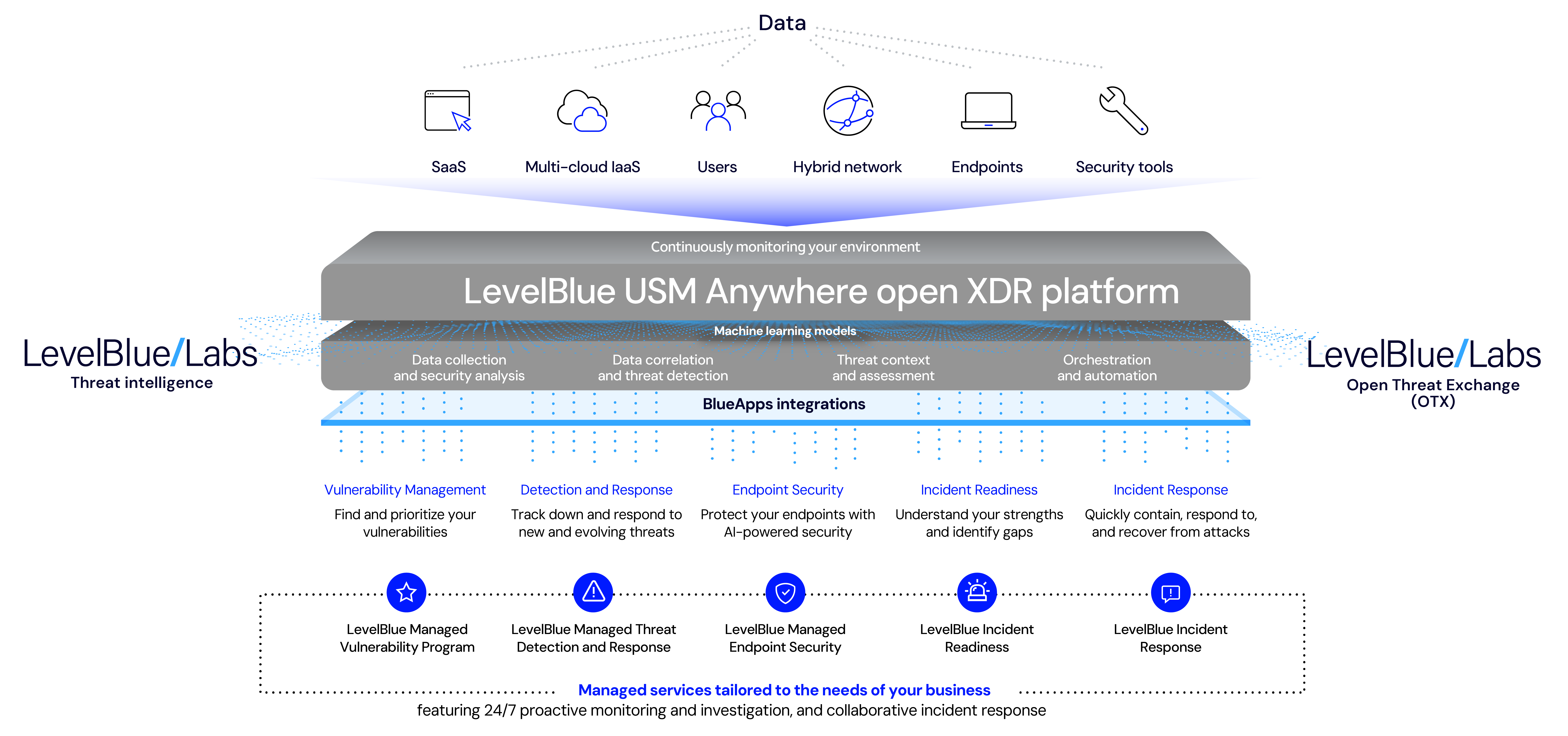
Extending detection and response across the attack surface
24x7 proactive security monitoring and investigation from the our SOC
Our expert SOC analysts leverage our decades of managed security expertise to help you to protect your business by monitoring and disrupting advanced threats around the clock.
Built on Unified Security Management (USM)
With multiple security capabilities in one unified platform, we go beyond other MDR services to provide centralized security visibility across your cloud, networks, and endpoints, enabling early, effective detection and a rapid time to deployment.
Powered by LevelBlue Labs threat intelligence
With unrivaled visibility of our IP backbone, global USM sensor network, and the Open Threat Exchange (OTX), LevelBlue Labs delivers continuous, tactical threat intelligence to the USM platform to keep your defense up to date.
Pricing
Break through the cost and complexity of threat detection and response
Managed Threat Detection and Response
Protect your business 24x7 at a starting price less than what it would take you to hire a single security analyst.
Starting at
$6,695
per month
Awards
Featured resource
Our Cybersecurity Training (ACT) learning portal
Advance your cybersecurity knowledge with continuous training.

FAQ
USM Anywhere vs Managed Threat Detection and Response (MTDR): How do they compare?
The key difference between USM Anywhere and MTDR is who is responsible for managing the solution. Both USM Anywhere and MTDR are built on our award-winning Unified Security Management (USM) platform and include the essential security capabilities, but MTDR has the added benefit of our SOC expertise. With MTDR, you can free up your internal resources to focus on more strategic initiatives and allow our security experts to handle the monitoring of your environment for threats 24x7 at a starting price less than what it would take you to hire a single security analyst.
What security capabilities does this MDR service include?
Managed Threat Detection and Response is built on our own Unified Security Management (USM) platform, which combines the essential security capabilities needed for effective threat detection and response in a single pane of glass. Key capabilities include asset discovery, vulnerability assessment, Network Intrusion Detection (NIDS), Endpoint Detection and Response (EDR), and SIEM event correlation and log management. In addition, through the platform’s BlueApps integration framework, the security monitoring and orchestration capabilities can extend to other security technologies, such as Palo Alto Networks® Next-Generation Firewall, giving you broad threat coverage for effective, early detection and rapid response.
How does the SOC analyst team interact with my own security team?
In addition to continuous monitoring and incident investigation, our analyst team leads regular review calls with your security team to cover all investigations and incident response activities. Our analysts host regular meetings with your team to review service metrics related to our SLAs, and to review progress towards your security program objectives and may provide recommendations for improvements.
How is the solution deployed?
Deployment is fast and simple, thanks to our high-touch service delivery model and a modern SaaS platform deployment model. Within 30 days of signing the contract, our SOC analysts can be monitoring your critical infrastructure and responding to threats according to your individualized Incident Response Plan.
Start your on-boarding experience with a Cybersecurity consulting engagement. Our highly skilled consultants lead a threat model workshop to identify and guide deployment requirements and establish future security program objectives. Based on the in-depth analysis of your environment from our Cybersecurity Consultants, our SOC analysts are able to install, configure, and tune your USM platform deployment according to your requirements and integrate with other security technologies that are in scope of our BlueApps framework.








