Discover the benefits
Continuous protection with proactive detection and response
Advanced threat detection and response
Automated threat prevention, detection, and response that helps identify, isolate, and roll back infected devices to keep endpoints in a constant clean state.
Simplified experience
A single agent with consolidated security functions merges multiple agents into one to help reduce complexity and simplify management.
Persistent protection
Logic and analysis performed on the endpoint agent, not in the cloud; helping protect endpoints in real time, even when offline.
Expertise you can count on
Our SOC analysts, security engineers, and threat hunters provide onboarding, 24x7 monitoring, and threat investigation services to alleviate the burden on in house teams.
Features
Enterprise-grade managed endpoint security
Features |
Details |
|---|---|
| Autonomous endpoint agent | Endpoints are fortified with tamper protection and patented AI algorithms that live on devices, catching malicious activity in real time as well as autonomously taking remediation actions to help keep the endpoints in a constant clean state. |
| Respond and rollback | SentinelOne’s capabilities extend beyond protection to autonomous responses. By automatically mapping and tracking all endpoint activity, the platform takes pinpointed actions to respond, remediate, and even rollback activity to previous safe states. |
| IoT Discovery and Control | Rogue and IoT device discovery across the network extracts even more value from endpoint cybersecurity. Discover and segment assets to allow for protection, compliance, and control measures to be taken - with zero additional software, network hardware, and consoles. |
| Cloud Protection | Help protect your cloud-native and dynamic container workloads in AWS and Azure, including full support for Kubernetes and Docker. Gain best-of-breed protection and container EDR visibility to the enterprise’s fastest growing attack surface – the cloud. |
| 24X7 Dedicated SOC Team | Endpoint security monitoring, management, and support including active threat hunting, forensic mapping, and continuous investigation, triage, and response to threats. |
| High Touch Service Delivery | Provides policy configuration, Incident Response Plan (IRP), on-going system tuning, and training on the platform. |
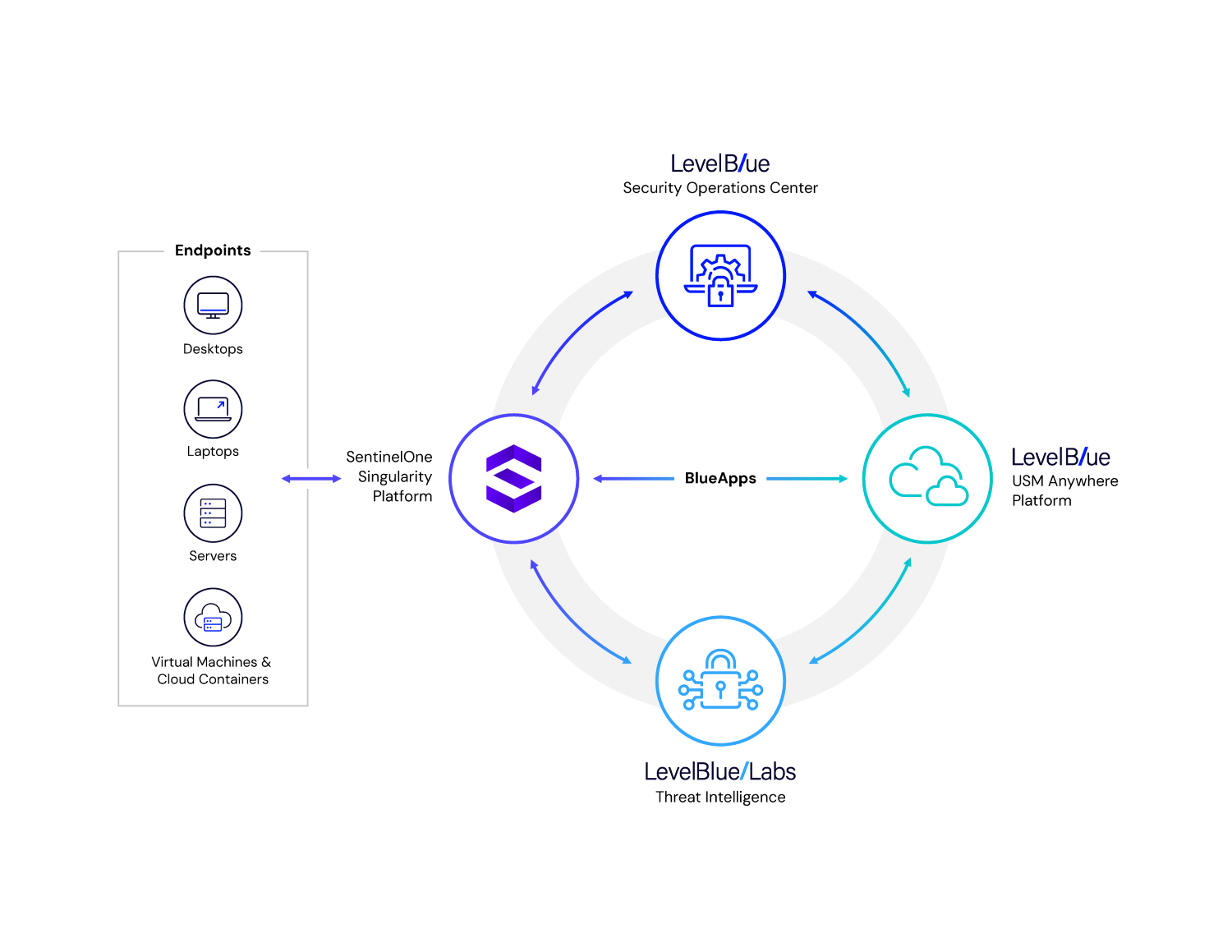
| Deep Integration | Enhanced detection and response through platform integration and LevelBlue Labs Threat Intelligence and Open Threat Exchange (OTX). |
| Optional bundled value | When bundled with our LevelBlue Managed Threat Detection and Response (MTDR), gain additional correlation advantages that accelerate threat detection and response. |
FAQs
You have questions. We have answers.
What is managed endpoint security?
The goal of managed endpoint security is to protect an organization’s endpoints from cyber attackers through increased visibility across devices and proactive threat prevention, detection, and response. With an effective endpoint security program, you can understand the true expanse of your enterprise assets including any device vulnerabilities and respond to threats in real time to mitigate risks. With our Managed Endpoint Security, customers can rely on expert guidance at every step from our SOC analysts, security engineers, and threat hunters.
What is endpoint detection and response (EDR)?
Endpoint detection and response (EDR) refers to endpoint security solutions that detect suspicious behavior, investigate threats, isolate infected endpoints, and provide automated remediation or response guidance to resolve cybersecurity incidents.
What is managed threat detection and response (MTDR/MDR)?
Managed threat detection and response (MTDR) solutions go beyond endpoints to detect, investigate, and respond to cyber threats. A sophisticated managed detection and response service centralizes security visibility across the cloud, on premises networks, and endpoints, and provides proactive security monitoring, alarm validation, and incident investigation and response. Our Managed Threat Detection and Response is fueled with continuously updated threat intelligence from LevelBlue Labs to help identify emerging threats and keep your defenses up to date.
What is the difference between SIEM and EDR?
SIEM (Security Information and event Management) refers to a central risk management tool which stores and analyzes data from many different log sources and provides incident investigation and response. EDR (Endpoint Detection and Response) focuses on detecting threats at the endpoint, isolating infected endpoints, and also provides incident investigation and response. , as well non-traditional endpoints in the cloud.
What other solutions fall under endpoint security?
Endpoint security can cover many different types of endpoints, including servers, mobile devices, cloud containers, and IoT devices. An organization’s endpoint security strategy can involve mobile security, cloud security, and endpoint management solutions like UEM (Unified Endpoint Management). Our Managed Endpoint Security with SentinelOne delivers comprehensive security for different types of endpoints, including traditional endpoints like desktops and servers, as well non-traditional endpoints in the cloud.