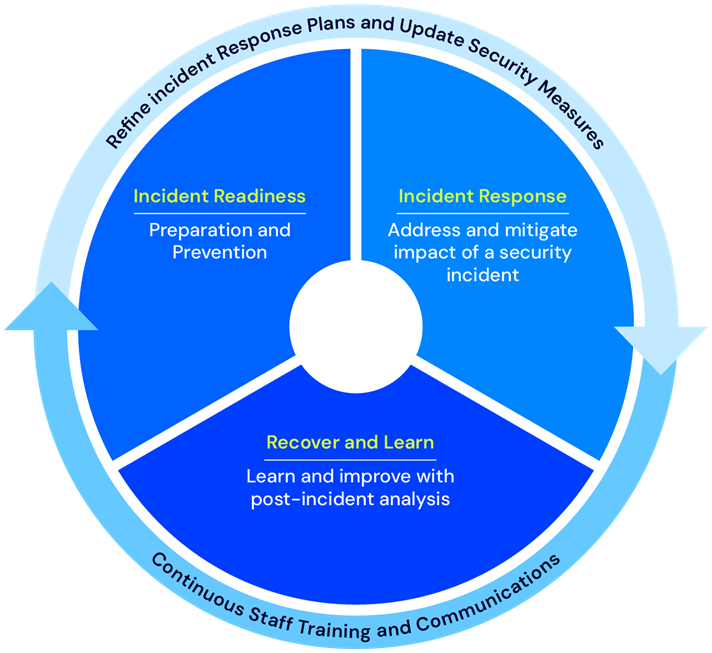
Reduce the damage
Achieve swift, comprehensive cybersecurity incident response
Containment and eradication
Implement measures to isolate security incidents and eliminate the root cause
Recovery and restoration
Return affected systems and data to a secure state; repair damaged assets, and restore compromised data
Reporting and documentation
Document the incident, its cause, the organization’s response, and lessons learned to improve future responses
Incident management and coordination
Take a structured approach to managing an incident with our expert insight and strategic recovery advice
Incident response expertise
Receive expert guidance and support with LevelBlue's Cybersecurity Incident Management
Incident triage
Navigate cyberthreats effectively
Our Cybersecurity’s team can identify, contain, and mitigate security incidents originating from external sources or within an organization to minimize damage and restore normal operations.
Reduce the effects of cyberattacks
Getting in front of a cyberattack quickly is crucial.
Our Cybersecurity can provide a systematic evaluation, prioritization, and handling of any incident—effectively addressing threats and minimizing their impact.
Incident management and coordination
Analyze the attack to determine the methodology and extent of any damage
Our Cybersecurity’s incident response approach can enable you to obtain and examine digital copies of storage devices to uncover valuable information, evidence, or additional potential threats in digital forensics investigations.
Get the bigger picture with analysis and correlation
Every incident reveals something about the attacker’s methods.
Our Cybersecurity forensics team can examine and link data from various sources—such as system logs and network traffic—to identify patterns and detect anomalies.
Remediation support
Strengthen cybersecurity with incident insights
Our experienced specialists provide expert guidance and assistance to address and resolve security vulnerabilities or incidents, helping you restore normal operations and strengthen defenses against future threats.
Get communication and reporting support
We assist in effectively conveying information about security incidents to relevant stakeholders, as well as documenting actions taken and lessons learned to improve future responses.
Analyze the attack to determine the methodology and extent of any damage
Get the bigger picture with analysis and correlation
Strengthen cybersecurity with incident insights
Get communication and reporting support
Discover the benefits
Recover quickly with Incident Response as a Service and turn insights into fortified protection
Quick analysis and recovery
Rapidly mitigate threats to minimize down time and reduce the overall impact on operations
Scalability and adaptability
Obtain the infrastructure and resources needed to scale your services and adapt quickly to changes in the threat landscape or regulatory environment
Advanced forensics
Access the tools, technologies, and resources needed to provide investigative procedures
Trusted experts
Partner with experts who have the skills and experience to support or supplement your team when suspected unauthorized, illegal, or malicious activities are detected
FAQs
You have questions about Cybersecurity Incident Management? We have answers.
What is incident response and why is it important?
Incident response is a strategy for handling and managing the aftermath of a security breach or cyber attack, also known as an IT incident, computer incident, or security incident. The goal of incident response is to manage the situation in a way that limits damage, reduces recovery time and costs, and ensures that information is not compromised.
What are the key steps in an incident response plan?
Creating an incident response plan is an undertaking that requires extensive strategic work and broad discussion across your enterprise. To begin, it’s advised that you prioritize your assets—asking questions along the lines of ‘What are our most important assets?’ and, just as important, ‘What assets would a cybercriminal target for an attack?’ Once you have developed a prioritized list of top-tier applications, users, networks, databases, and other key assets, you can begin to develop an accurate picture of what’s on your network, and how data traffic moves in normal circumstances. Should you require expert guidance, LevelBlue has a team of cybersecurity experts, ensuring that your organization receives top-notch guidance and support. Our broad portfolio of solutions allows our experts to create holistic incident readiness and response programs that address people, process, and technology considerations.
What is the difference between incident response and disaster recovery?
Incident response goes well beyond simply getting back to work after an attack as one might in simple ‘disaster recovery’. A well-planned incident response not only discovers what happened and how, it provides valuable insights into the attack, as well as illustrating what improvements can be introduced to ensure your network is prepared for the evolution of cyberattacks. LevelBlue can tailor an incident response to meet the unique needs of your organization, ensuring that your security posture is strengthened in the most effective and efficient manner possible.
Should we test our incident response plan?
Testing your plan is one of the most important things you can undertake to help ensure that a cyberattack doesn’t paralyze your enterprise or cause long-term financial and reputational damage. Testing is essential for every aspect of cybersecurity because numerous analyses have shown how damaging even a minor attack can be to an organization if it is not quickly and expertly addressed. Partnering with us gives you access to state-of-the-art tools, resources, and technology to help protect your organization from cyber threats.
What role does incident response play in the legal and compliance aspect of a cyberattack?
The legal requirements related to a cyberattack can vary widely, depending on what your business is and where you do business. Cyberattacks can have broad financial implications beyond loss of data or delays in getting back to work. Having an effective, strategic incident response plan in place—and investing the time to test it regularly—can play a vital role in ameliorating the situation in the case of an attack.