Executive summary
In the current cyber landscape, adversaries commonly employ phishing as the leading technique to compromise enterprise security. The susceptibility of human behavior makes individuals the weakest link in the security chain. Consequently, there is an urgent need for robust cybersecurity measures. Phishing, which capitalizes on exploiting human behavior and vulnerabilities, remains the adversary's top choice. To counter this threat effectively, ongoing education and awareness initiatives are essential. Organizations must recognize and address the pivotal role of human vulnerability in cybersecurity.
During regular business hours, an alarm was generated due to a customer’s user that had interacted with a potentially malicious phishing link. This prompted a thorough investigation conducted by analysts that involved leveraging multiple Open-Source Intelligence (OSINT) tools such as VirusTotal and URLscan.io. Through a meticulous examination, analysts were able to unveil suspicious scripts within the phishing webpage’s Document Object Model (DOM) that pinpointed an attempt to exfiltrate user credentials. This detailed analysis emphasizes the importance of proactive cybersecurity measures and showcases the effectiveness of analysts leveraging OSINT tools along with their expertise to accurately assess threats within customer’s environments.
Investigation
The alarm
The Managed Detection and Response (MDR) Security Operations Center (SOC) initially received an alarm triggered by a potentially malicious URL that a user received in their inbox. Office 365's threat intelligence feed flagged this URL as potentially malicious. The initial steps in addressing this alarm involve two key actions.
First, it is crucial to determine the scope of impact on the customer's environment by assessing how many other users received the same URL. Second, a thorough validation process is essential to confirm whether the URL is indeed malicious. These initial steps lay the foundation for a comprehensive response to safeguard the security of the environment.
To determine how many users received the same URL, a comprehensive search within the customer's environment revealed that no other users received the same URL. As a result, only one user is affected, suggesting that this is an isolated incident and does not appear to be part of a targeted attack on the customer's environment. With this understanding, the focus can now shift to the second step: Validating the reputation of the URL.
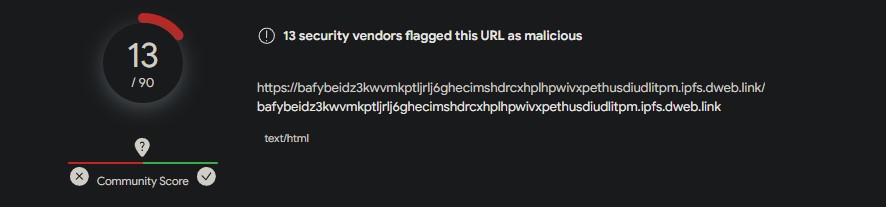
By employing the OSINT tool VirusTotal and inputting the URL received by the user, we aim to assess its potential threat level. VirusTotal aggregates results from various security vendors to provide a comprehensive analysis. In the current evaluation, 13 out of 90 security vendors classify this URL as malicious. It's important to note that while the number of vendors flagging the URL is a key factor, a conclusive determination of malicious intent typically considers a consensus among a significant portion of these vendors. A higher number of detections by diverse security platforms strengthens the confidence in labeling the URL as malicious.
With a potentially malicious URL identified, it is imperative to delve deeper to ascertain the underlying reasons for its malicious reputation. Analysts will utilize a tool such as URLscan.io for this purpose. URLscan.io serves as a sandbox, providing a risk-free environment for visiting websites. This tool is instrumental in conducting a thorough examination to uncover the nuances contributing to the URL's malicious classification.
After entering our identified malicious URL into URLscan.io, we can examine the webpage intended for our customer's user. Upon visiting this URL, a PDF file is prepared for user download. However, a mere screenshot of the webpage is insufficient to provide a definitive reputation. To obtain more insight, we must delve deeper into the webpage by examining its DOM.
The DOM comprises the essential components of a webpage, encompassing HTML, CSS, and JavaScript that define the structure, presentation, and behavior of the page. URLscan.io facilitates a convenient examination of the DOM. In reviewing the DOM, particular attention is given to identifying any malicious scripts that may be present. The focus is often on searching for the HTML tags, which denote script elements within a webpage.
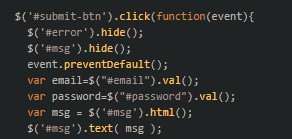
In the evaluation of the DOM associated with the potentially malicious URL, multiple tags are observed. Within these tags, it becomes apparent that upon the user's interaction with the "download all" button, a prompt will request them to input their email and password.
This is the start of the script that defines the email and password variables.
Continuing through the script, more concerning code emerges. While the user is prompted to enter email and password information, it becomes apparent that the adversary has crafted code designed to falsely claim that the entered email and/or password is incorrect, even if it is not. This behavior aligns with typical phishing activities, where malicious actors attempt to induce users to enter their credentials multiple times. This tactic aims to exploit potential typos or errors in the entered information, ensuring that the adversary ultimately obtains the correct credentials from the victim.
After the user submits their credentials, the user's email and password are transmitted to the website “hxxps://btmalta.cam/wefmail/email (1).php” via an AJAX POST request. In the context of web development, an AJAX (Asynchronous JavaScript and XML) POST is a technique that allows data to be sent to a server asynchronously without requiring a page refresh. Unfortunately, malicious actors exploit this functionality to surreptitiously transmit sensitive user information, as observed in this instance.
Conducting OSINT on the aforementioned site ("hxxps://btmalta.cam/wefmail/email (1).php") reveals a malicious reputation, notably marked by its relatively recent creation, being only 80 days old from the registry date. The registration age of a domain is a useful factor in assessing its credibility. In this case, the combination of a newly registered domain and indications of malicious activity raises significant concerns. It strongly suggests that the adversary is likely utilizing this domain to collect the user-entered email and password deliberately.
Considering the aforementioned details, it becomes more evident that this is a credible phishing attempt targeting one of our customers' users. The method of data transmission, the malicious reputation of the domain, and its recent registration collectively underscore the severity of the situation.
Customer interaction
After the findings were observed, an investigation was created for the customer to review. If the customer’s affected user entered any credential information, this means the user account should be considered compromised. Since this affected a user within the customers Office365 environment, it was recommended for the customer follow the guidelines set by Microsoft in an event of an email account compromise: Responding to a compromised email account
How to combat against phishing attempts
In the ongoing battle against phishing attempts, implementing effective strategies is paramount to fortifying cybersecurity defenses. Listed below are some of the many key practices and countermeasures to safeguard your organization from falling victim to malicious phishing activities.
- Ensure that users go through regular security training to learn about the dangers of potential phishing attempts.
- Employ processes that allow users to report potential phishing emails that they receive.
- Ensure users are properly utilizing Multi-Factor Authentication (MFA)
- Ensure strong password policies are in place to prevent any weak or insecure passwords from being used.
- To check to see if your password or email has ever been involved in a data breach you can use the free tool https://haveibeenpwned.com/ to check.