The content of this post is solely the responsibility of the author. AT&T does not adopt or endorse any of the views, positions, or information provided by the author in this article.
In the realm of data security, there exists a captivating technique known as whitespace steganography. Unlike traditional methods of encryption, whitespace steganography allows for the hiding of sensitive information within whitespace characters, such as spaces, tabs, and line breaks.
This inconspicuous approach to data concealment has gained significant attention in recent years as a means of secure communication. In this blog, we will delve into the world of whitespace steganography, exploring its techniques, applications, tools, and ethical considerations for educational purposes.
Whitespace steganography is a method of concealing data within whitespace characters that are often overlooked or deemed insignificant. By strategically modifying the frequency or arrangement of whitespace characters, hidden messages can be embedded within a text document. To the naked eye, the document appears normal, but those aware of the encoding technique can retrieve the concealed information.
In whitespace steganography, several techniques are employed to conceal information effectively. These techniques include altering the frequency of whitespace characters, such as adding or removing spaces, tabs, or line breaks. Another approach involves manipulating the arrangement of whitespace characters to represent encoded data. Various algorithms, such as the Least Significant Bit (LSB) technique, can be utilized to embed and extract hidden messages from whitespace.
Whitespace steganography finds applications in a range of scenarios where secure communication and data protection are paramount. Some common use cases include:
- Covert communication: Whitespace steganography allows individuals to exchange sensitive information discreetly, evading detection and interception.
- Document protection: Concealing critical information within whitespace characters can help protect sensitive documents from unauthorized access or tampering.
- Digital watermarking: Hidden within whitespace, digital watermarks can be embedded in images or documents to protect intellectual property or verify authenticity.
Numerous open-source tools are available that facilitate whitespace steganography. These tools provide features and functionalities for encoding and decoding hidden messages within whitespace characters. Notable examples include Snow, Steghide, OpenStego, and Whitespace. There are also closed source or commercial whitespace steganography tools that offer advanced capabilities and additional security features. These tools often provide user-friendly interfaces, encryption algorithms, and integration with other security technologies. Some popular closed-source tools include SilentEye, OutGuess, and Masker.
In this blog, we will use Snow (Steganographic Nature of Whitespace) to see a working example of whitespace steganography -the tool can be downloaded from here.
As per the documentation, The Snow program runs in two modes - message concealment, and message extraction. During concealment, the following steps are taken.
Message -> optional compression -> optional encryption -> concealment in text
Extraction reverses the process.
Extract data from text -> optional decryption -> optional uncompression -> message
Now, let’s look on a working example.
We have downloaded the 32-bit version of Snow, and we’ve ensured that Java runtime environment (JRE) is installed on our system. Once everything is in place extract Snow to the desired directory. To run Snow, you will need to run command prompt as administrator and move to the directory where you have extracted Snow.
Once you are in the directory, you will need an input file (we are using a text file for demonstration)
Now, let us try to conceal a message “Hello There.” using Snow.
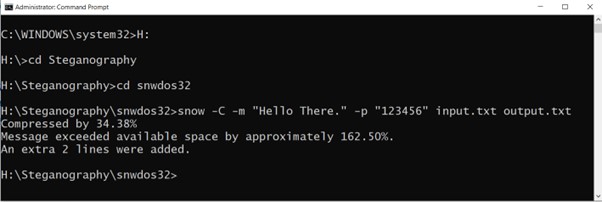
In the above example we concealed a message in the input file and created an output file using Snow (to avoid any contradiction we kept the input file in same directory as Snow)
In the above example we used -C for compression, -p for password and -m for message.
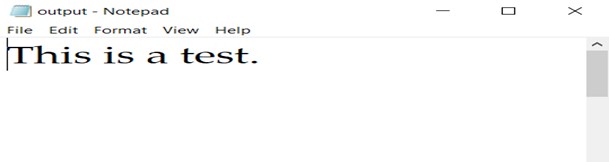
Now let us take a look at the output file.
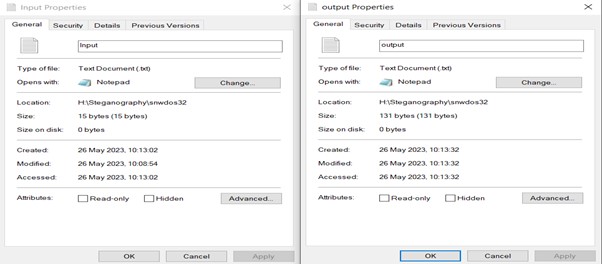
Now let’s see if there are any differences in size of input and output files.
We can observe that there is a difference in size - however, when we open the output file it looks the same as the input file.
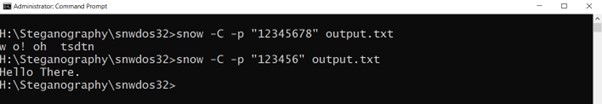
Now, let’s try to read the hidden message. Let’s run the command prompt as administrator and move to the directory of Snow where the output file is located.
So, I tried with wrong password once and then with the correct password as you can see below:
This was a demonstration of whitespace steganography using Snow and is purely for educational and research purposes to understand how it works in real life scenarios.
Steganalysis: Detecting steganography
Steganalysis refers to the detection and analysis of hidden messages within digital content. While whitespace steganography can be difficult to detect, specialized techniques and tools are available to identify potential instances of concealment. Steganalysis plays a vital role in identifying potential misuse and ensuring responsible use of steganography. We’ll dive deep into steganalysis in coming blogs.
Ethical usage and disclosure are crucial when it comes to steganography. It is important to adhere to legal regulations and privacy laws governing data security and communication. Whitespace steganography should be used responsibly for educational purposes only, emphasizing the importance of obtaining proper consent and ensuring ethical practices.
Whitespace steganography offers a remarkable approach to secure communication and data protection. By harnessing the power of seemingly innocuous whitespace characters, sensitive information can be concealed within plain sight. Understanding the techniques, applications, and tools associated with whitespace steganography enables individuals to navigate the field responsibly. As technology continues to advance, the future of whitespace steganography holds the potential for further innovations in secure communication and data privacy.