Executive summary
Every day, billions of emails are sent out, some legitimate, while others are used to target unsuspecting users. According to the FBI, phishing attacks were the most common type of cybercrime in 2020. The reason these are so commonly used is because phishing tools are easy to get a hold of and attackers are taking advantage of the weakest link when it comes to security – the employees. The phishing tools are typically cheap and simple, requiring little to no IT experience of their user making them available to a broad range of people. Even when preventative tools are in place, if the employees are not properly trained, they can still fall victim. A well-crafted phishing attack can fool the average user into clicking a link or trick the user into forwarding the email to coworkers. In this case this is just what happened.
The AT&T Managed Threat Detection and Response (MTDR) analyst team was notified that a user fell subject to a phishing email. The user received an email that was quarantined by Microsoft Office Advanced Threat Protection (ATP), but still opened the email, clicked a link and entered their credentials. The customer was notified about the successful phishing attack and requested additional information about what occurred between the successful attack and when the account was disabled. Within 45 minutes, the MTDR analyst created an Investigation, attached all suspicious logs, and a report containing all the events between the attack and lockout. Due to the rapid information gathering, the customer was able to quickly start the remediation process and determine if any sensitive information may have been compromised.
Investigation
Initial Alarm Review
Indicators of Compromise (IOC)
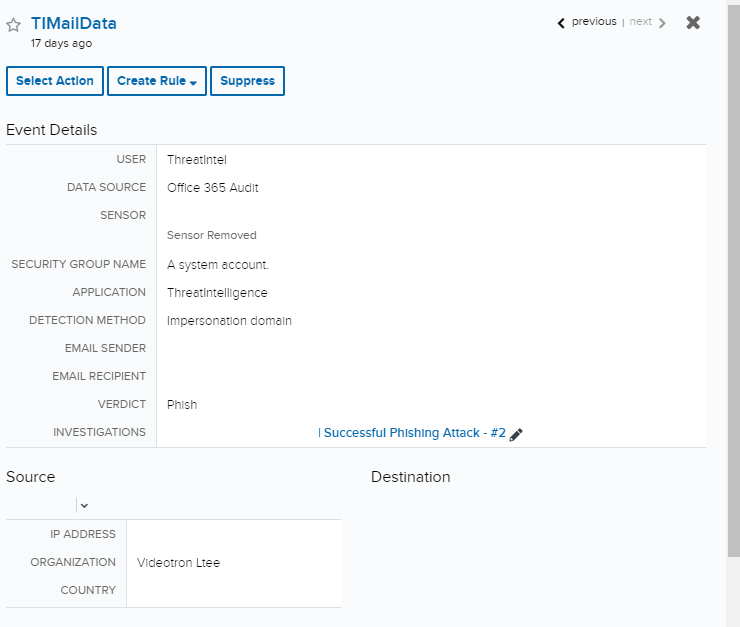
A user received an email which they believed to be legitimate. The body of the email contained a phishing link which prompted the user to enter their credentials. After some time had passed the user realized that this may not have been legitimate and reported it to their security team.
Expanded investigation
The analyst was able to find the event from the original email, failed logons from a suspicious IP after the email, and SharePoint activity that followed the compromise. The analyst quickly created a report of the suspected activity which included the events for failed logons and the anomalous SharePoint activity.
When the customer’s security team requested assistance, the analyst team sprang into action. Within thirty minutes of contact, the MTDR analyst reviewed this user’s behavior and created an Investigation containing all of the findings of the email compromise. A review of the audit log revealed that the email came from a suspicious IP and organization, and it was originally quarantine and flagged due to “Domain Impersonation”. Even with this first layer of defense, the user still fell for the phishing attack and launched the suspected link and entered their credentials.Event Deep Dive
Response
Building the Investigation
In the Investigation, the customer was provided two CSV reports containing all activity between the successful phishing attack and the compromised account being disabled. The suspicious events were also attached to the investigation, including SharePoint events for suspicious behavior, allowing the investigator easier access to review the activity.
Customer interaction
Due to the rapid response of the MTDR team, we were able to work with the customer to quickly determine what other information may have been exposed. It was determined that the account credentials were compromised and a password change was enforced. Luckily, no successful logons from suspicious IPs were seen before the account was disabled. The company was able to quickly move from quarantining the account to reviewing data that may have been compromised.