James Rodriguez – Senior Specialist, Cybersecurity
Executive summary
Over the past several months, AT&T Managed Detection and Response (MTDR) security operations center (SOC) analysts have seen an increase in the usage of phishing emails containing malicious QR codes. In a recent example, a customer that was victimized by a phishing attempt provided the AT&T analysts with an email that was circulated to several of its internal users. The analysts reviewed the email and its included attachment, a PDF containing a QR code and an urgent message claiming to be from Microsoft.
When the targeted user scanned the QR code, they were directed to a counterfeit Microsoft login page designed to harvest usernames and passwords. This type of attack is called “quishing.”
Unfortunately, several users fell victim to the attack, and their credentials were compromised. However, our analysts were able to engage with the customer and guide them through the proper remediation steps.
Encouraging targeted users to act quickly and scan the code using their phone (which often is not as secure as the rest of a company’s network) is a standard tactic employed by threat actors. By doing this, they hope to convince the user to act without thinking and forgo proper security practices allowing the threat actor to bypass traditional security measures in place on a company network.
Threat actor tactics
The threat actor used a Windows authentication setup for multi-factor authentication (MFA) to initiate the attack. The targeted users received a phishing email indicating MFA needed to be set up on their account. The email included a PDF attachment with instructions directing them to scan the included QR code, which was malicious.
Once the users scanned the QR code, they were redirected to a fake Microsoft sign-in page on their phone. Here, they entered their legitimate login credentials,which were then stored and made available to the threat actor.
Investigation
Once the customer suspected the email was malicious, they contacted the AT&T team and provided a copy of the PDF file with the included QR code. The team analyzed the file and the QR code (see Image 1) and identified the associated destination as “srvc1[.]info/mcrsft2fasetup/index.html.”
Image 1: PDF file from customer containing malicious QR code
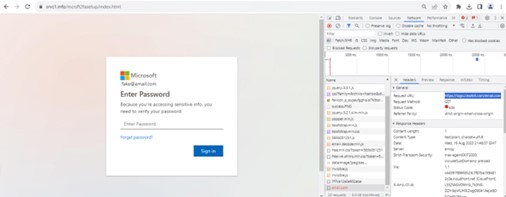
The QR codes associated URL sends the user to a credential harvester masquerading as a Microsoft login page. (See Image 2.)
Image 2: Credential harvester masquerading as login page
AT&T SOC analysts analyzed the credential harvester using a fake email and the Google Chrome Inspector tool to record any outbound connections when clicking the “Sign In” button (see Image 2). Only one network connection was made, which resulted in a 404 HTTP response code to the external domain “logo.clearbit[.]com/email.com.” Research into clearbit[.]com found it is associated with Clearbit B2B Marketing Intelligence, which is listed as a legitimate marketing tool for identifying customers and sales exchanges.
Analysts used open-source intelligence (OSINT) to further research the initial associated domain “srvc1[.]info” but found no additional information as the domain was recently purchased. Further investigation revealed that the owner’s identity was hidden, and there was no additional data available. The customer confirmed that neither the Clearbit nor the srvc1 external domains were known or a part of normal business use within their environment.
Remediation
AT&T SOC analysts worked closely with the customer to identify which users had received the email and to verify whether any credentials were submitted on the login page. During this time, the analysts provided detailed instructions to the customer on how to close all active sessions and instructing them to reset user credentials. Closing all active sessions prior to any credential resets is critical since the threat actor will retain access to the user’s account until they are completely logged out.
The customer was also directed to remove the phishing email from all user inboxes within their environment and to block all external domains associated with the QR code. Analysts conducted further review of the affected user accounts to confirm that no data had been successfully exfiltrated and that there were no other indicators of the email being circulated internally. Once the incident had been fully remediated, the client was able to take the lessons learned to better inform their teams of the dangers of phishing and malicious QR codes.
Protect yourself against malicious QR codes
Phishing attacks and credential harvesters have been in use for some time. However, as the use of QR codes becomes more commonplace, take care to verify the domain that a QR code is associated with before you scan it.
Additionally, avoid scanning the QR code with your mobile device. Typically, there are less security measures in place on a mobile device than on a network-connected corporate device.