Executive summary
Credential harvesting is a technique that hackers use to gain unauthorized access to legitimate credentials using a variety of strategies, tactics, and techniques such as phishing and DNS poisoning. Phishing is the most frequent type of cyber threat and can lead to more harmful attacks such as ransomware and credential harvesting.
According to recent research, phishing assaults targeted credential harvesting in 71.5% of cases in 2020. 72% of employees admitted to clicking on a phishing email's malicious link, making it easy for attackers to gather credentials.
Phishing is a type of social engineering attack that tricks victims into disclosing personal information or downloading malicious software. It is one of the most difficult cyber threats to eliminate as it relies on human defenses, and organizations must consistently teach personnel to spot the newest phishing techniques.
The Managed Extended Detection and Response (MXDR) SOC team received an alert regarding a user clicking on a suspicious URL in an email and the subsequent traffic was allowed. However, ProofPoint effectively rewrote the URL to prevent some of the potential threats. The SOC team notified the customer about the successful phishing attack by creating an investigation report containing all the events between the attack and lockout.
Investigation
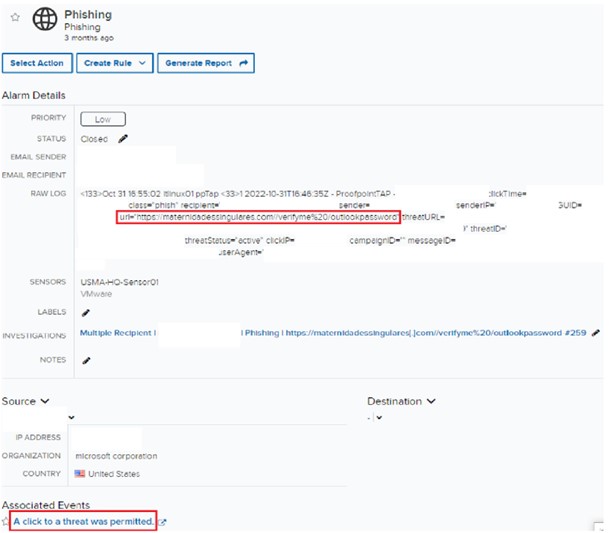
Initial alarm review
Indicators of Compromise (IOC)
The first alert was triggered when a user clicked on a link contained in a phishing email, which was permitted to pass through. The email's content was crafted to deceive the user into divulging their login credentials. Because the link's URL did not have a signature indicating a poor reputation on Open-Source Intelligence (OSINT), ProofPoint did not intercept the initial click.
Expanded investigation
Events search / Event deep dive
While investigating phishing cases, you must check all recipients who received the same phishing email and who clicked the attachment URL, and whether the firewall allowed the HTTP URL request or not. A review of the previous ninety days of events revealed there was one additional recipient, however, logs showed the email was quarantined after user’s click. The first click on the malicious URL by the initial user was allowed. However, ProofPoint’s URL defense feature conducted a heuristic behavioral-based analysis and determined the URL to be malicious. As a result, the second click by the initial user and any subsequent clicks by other users were effectively blocked by ProofPoint.
After conducting an OSINT analysis, it was determined that the sender's email fails to pass DMARC (Domain Message Authentication Reporting and Conformance), and MX record authentication. This raises concerns regarding the legitimacy of the email. Also, OSINT searches indicate that both recipient emails have been compromised, though the exact time remains unknown.
DMARC is a protocol used to authenticate emails and prevent phishing attacks by verifying the sender's domain. It checks if the sender's domain matches the domain in the emails "From" header. If they do not match, the email is fraudulent and can be rejected or marked as spam. On the other hand, MX records are DNS records that specify the mail server responsible for accepting email messages on behalf of a domain. Attackers can use MX records to redirect email traffic to a fraudulent mail server and steal sensitive information. Therefore, DMARC and MX records are crucial in preventing phishing attacks by ensuring that email traffic is directed to legitimate mail servers and verifying the authenticity of email senders.
Further investigation into the email's URL using advanced tools like Urlscan.io and screenshotmachine.com identified it as malicious - attempting to extract user outlook credentials. However, the attachments' file hash has no OSINT record, which renders static analysis impossible to determine whether the file attachment poses a threat or not. Therefore, it would be a good option to identify the file by analyzing it with a full sandbox* analysis.
A sandbox is a controlled environment used to test software and applications without affecting the host system. Sandboxing is important because it helps to identify and mitigate potential security vulnerabilities, viruses, and malware. It also minimizes the risk of damage to the production system by limiting the impact of potential threats to the sandbox, providing an extra layer of security against malicious activity.
Reviewing for additional indicators
At this point, the attacker tried to get “Initial Access (tactic)” into the network by using a “phishing” technique based on the Mitre Att&ck Framework.
During the initial access phase of a cyberattack, attackers use techniques like exploiting vulnerabilities or phishing to gain their first foothold in a network. This foothold then enables them to conduct further attacks. To prevent this, organizations should have a robust defense strategy and perform regular security assessments.
ProofPoint approach
ProofPoint's URL Defense feature works to protect users from malicious links. This feature uses a two-step approach to ensure maximum protection.
Firstly, if a URL doesn't have any known malicious signatures, ProofPoint's URL Defense feature allows the user to click on it using a "URL rewritten" feature. This feature prevents many types of malicious activity, but it's important to note that until ProofPoint's heuristic-based analysis determines whether the URL has any potentially malicious behavior, the user may be vulnerable to credential loss if they share their credentials.
Once the user clicks on a URL, ProofPoint's system analyzes the destination website to identify any potential signs of malicious behavior. If any suspicious activity is detected, access to the website is blocked, and a warning message is displayed to the user. However, if the system doesn't detect any malicious behavior, the user is able to proceed to the destination website.
It's important to note that ProofPoint's URL Defense feature provides significant protection against malicious links, but it may not be able to detect every instance of phishing or malware-based attacks. Therefore, users should remain vigilant when clicking on links in emails and take additional security measures such as multi-factor authentication and employee training to help mitigate the risk of credential loss.
Response
Building the investigation
An investigation was created by following the incident response process. The investigation included identifying the incident, finding the root cause of the incident and Indicators of compromise. Then we made recommendations to the customer on mitigation/remediation steps. We communicated with the customer to ensure necessary actions are executed.
Recommended mitigation steps were:
- Resetting the account password to a stronger one
- Removing the email and email attachments
- Enabling Multi-Factor Authentication (MFA).
- Blocking the URL domain and IP.
- Running an antivirus scan on the asset.
Incident response is an organizational approach and process to manage cybersecurity breaches, incidents, or cyberattacks. It includes multiple steps:
- Identifying an incident/attack
- Minimizing damage
- Eradicating the root cause
- Minimizing recovery cost and time
- Learning lessons from the incident
- Taking preventative action
Customer interaction
The MXDR team responded quickly to the incident and worked with the customer to identify the problem. They confirmed that someone lost their account credentials, but fortunately, no suspicious logins were detected before the account was disabled. The company confirmed they followed the recommended steps, so the email and attachments were quarantined, the URL blocked, and the affected device was scanned by antivirus.