IT compliance management solutions
Achieve IT compliance management and security goals faster with one unified solution.
Complete IT Compliance & Security Management in a Single Pane of Glass
IT compliance management is often a manual process that requires you to deploy and monitor multiple IT security point products to satisfy regulatory or industry requirements. You also must aggregate data from multiple IT systems into a single view or set of reports to prove to management and auditors that your IT controls are in place and working. While a SIEM or log management tool can help automate that effort, it’s not enough to meet the stringent requirements of today’s widely-accepted regulatory compliance standards, such as PCI DSS, HIPAA, GDPR, and others.
Unified Security Management™ (USM) is a unified solution for complete security and IT compliance management. It combines the essential security technologies needed to demonstrate compliance against today’s most challenging regulatory standards and to continuously monitor your networks, cloud environments, and endpoints—all in a single pane of glass. It combines asset discovery, vulnerability assessment, intrusion detection, behavioral monitoring, endpoint detection and response, file integrity monitoring, orchestrated incident response, SIEM, log management, compliance reporting, and continuous threat intelligence updates.
USM breaks through the complexity and expense of having to manage multiple point security solutions, giving today’s resource-limited IT security teams a centralized security and IT compliance solution that’s affordable, easy to use, and can be deployed in as quickly as one day.
Discover how the USM platform helps to accelerate and simplify security and IT compliance management:
- Automates log collection, analysis, and event correlation in a single console, alerting you to suspicious and anomalous activities
- Continuously discovers your assets and vulnerabilities in dynamic environments
- Centralizes threat detection across all your environments: AWS, Azure, on-premises, as well as cloud apps like Office 365 and G Suite
- Detects and reports on changes to your critical files and registries with built-in file integrity monitoring (FIM)
- Enables faster incident investigation and response with proactive endpoint queries, automated response actions, and advanced security orchestration
- Simplifies compliance reporting with out-of-the-box, predefined compliance reports, and highly customizable data search and analytics
- Securely stores your log data in the Secure Cloud for up to 90 days online, and in cold storage for the life of the active USM Anywhere subscription.
- Certified compliant with PCI DSS, HIPAA, and SOC 2, giving you assurance and alleviating the burden of log storage in your own compliance certification process
Maintain IT Compliance with Continuous Monitoring
Compliance is never done. Even after the auditors leave, you must continuously maintain your compliance practices, which if performed manually, can consume an overwhelming amount of resources, especially for small IT security teams. Still, failure to stay in compliance can result in substantial fines, along with damage to your company’s reputation or brand.
USM makes it simple and automatic to maintain your IT compliance practices between audits, so you can focus on what really matters—keeping your organization secure from the latest threats.
Continuous Asset Discovery & Vulnerability Scanning
To satisfy most regulatory standards, you must maintain visibility of all of your in-scope assets and their vulnerabilities. The USM platform continuously scans your environment to dynamically discover all of your cloud and on-premises assets. Internal vulnerability scans run regularly, and you can run an on-demand vulnerability scan of any asset group, for example a PCI CDE asset group.
Automated Log Collection, Analysis, & Event Correlation
USM automatically collects, aggregates, and correlates log data from systems, devices, and applications in your cloud and on-premises environments. And, with our lightweight, adaptable Alien Agent, you can collect in-depth endpoint data, even as your endpoints move on and off the corporate network. As such, you get full-environment correlation across your cloud, on-premises networks, and endpoints for the most comprehensive security visibility. You’ll automatically be alerted to suspicious and anomalous activities, and very importantly, have full context of the threat, so you can speed investigation.
Continuous Threat Intelligence Updates from Alien Labs
To protect your organization from the latest malware-based threats and vulnerabilities, as mandated by many regulatory compliance standards, you need the up-to-date threat intelligence in your IT compliance management solution. Yet, most organizations simply don’t have the resources to stay ahead of emerging threats.
With USM, that’s okay. The platform receives continuous threat intelligence updates automatically from the Alien Labs Security Research Team. This team scours the global threat landscape and delivers ready-to-use threat intelligence in the form of continually updated correlation rules, new intrusion detection and vulnerability signatures, optimized endpoint queries, up-to-date remediation guidance, and more, in order to combat the latest threats. The platform also receives crowd-sourced threat intelligence from the Open Threat Exchange® (OTX™), a worldwide community of security practitioners and researchers who openly contribute threat data on new attacks as they unfold in real-time in the wild.
Automated Incident Response & Orchestration
Next-generation compliance standards not only mandate that you prevent and detect intrusions in your environment, but also that you respond to incidents quickly and efficiently. USM empowers you with proactive endpoint queries, automated response actions, and advanced security orchestration so that when an incident occurs, you can work to immediately contain or otherwise respond to the threat. This orchestration extends to third-party security tools like Palo Alto Networks and Cisco Umbrella, so you can centralize your threat detection and incident response activities in the USM platform.
Compliance-Ready Log Storage
USM stores your log data in the Secure Cloud. Up to your most recent 90 days of events are searchable in the USM platform, and logs are stored in cold storage for up to one year. And because the USM platform is certified compliant to widely-accepted compliance standards, including PCI DSS, HIPAA, and SOC 2, you can rely on our secure log storage as you pursue your own certification efforts.
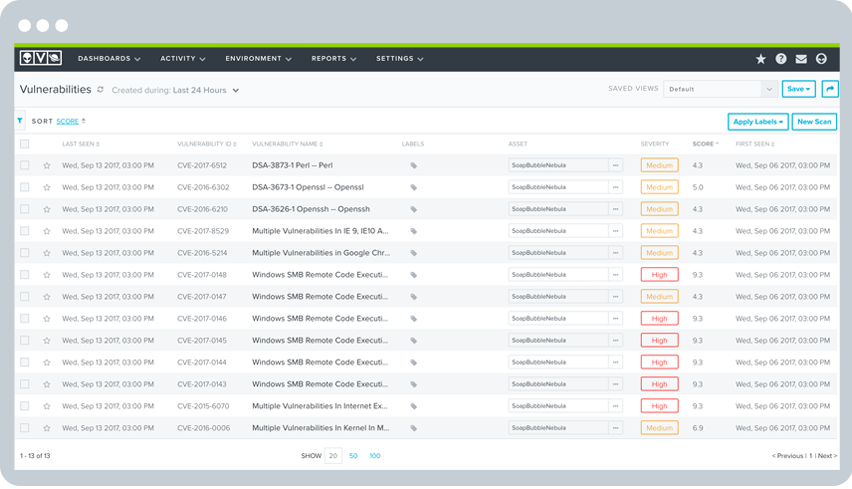
Audit-Ready Compliance Reporting
To meet compliance mandates of PCI DSS, HIPAA, and other regulatory standards, you must demonstrate that you regularly monitor your IT environments and that your IT controls are working. This demands rigorous reporting on your assets, vulnerabilities, and potential threats, which can be very time-consuming if done manually and can slow down or jeopardize your audit process.
Predefined Compliance Reports
USM delivers a vast library of “audit-ready” predefined reports for PCI DSS, HIPAA, and NIST CSF, helping you to accelerate your compliance process and be ready faster for your next audit. Also available are reports that facilitate regular review of events from key data sources such as your firewalls, or by key event types such as authentication events. The USM platform gives you centralized visibility of all your cloud and on-premises assets, vulnerabilities, threats, and log data from your firewalls and other security tools, so you always have the most complete and contextual data set at your fingertips.
Save & Export Custom Reports
In addition to predefined reports, USM makes it incredibly simple to create custom reports, so you can satisfy the reporting needs of your compliance auditor, your executives, and your board. It provides a highly efficient and fast way to search, filter, and analyze your security-related data. You can save and export any custom search as an HTML or CSV report and add visual data elements, perfect for analyzing trends or presenting an executive-level summary.
Create & Save Custom Data Views
Complementing the predefined and custom reports, the USM platform also gives you the ability to easily create and save custom views on events and alarms, so you can quickly and regularly review data related to a specific threat, user, or system that you want to focus on. You simply select the search terms and data fields you want presented in the view and save it for quick reference at any time.






