Hybrid cloud security solutions
Get comprehensive hybrid cloud security with USM Anywhere.
Benefits
Complete visibility of your hybrid cloud security environments from one pane of glass
The rising popularity of hybrid cloud infrastructure presents a significant challenge for security professionals. Though many organizations find that their infrastructure needs are best met with a combination of on-premises, private cloud, and public cloud environments, traditional security solutions that were not built with the cloud in mind are difficult to adapt for hybrid cloud security.
While one of the benefits of public cloud architecture is that it mitigates certain traditional security risks, some of the features that make cloud infrastructure more secure also make it impossible to, for example, monitor network traffic via a SPAN port. At the same time, the elastic nature of cloud environments introduces new security concerns that must be considered within a hybrid cloud security plan.
USM Anywhere™ provides complete visibility of your security posture across your on-premises, private cloud, and public cloud environments, leveraging purpose-built cloud sensors with direct hooks into cloud APIs to address cloud-specific security needs.
Detect and report on cloud-based intrusions
Detect intrusions in the cloud with cloud IDS, access cloud-native sensors for AWS and Azure and manage cloud data with graph-based analytics.
Security monitoring built for the cloud
Put user activity at your fingertips with cloud access logs and make sense of cloud activity with correlation rules.
Unified security for cloud, hybrid and on-premises
Centralize security across infrastructures with capabilities like asset discovery, vulnerability scanning, IDS, behavioral monitoring and SIEM.
Updated threat intelligence built into your security plan
Receive curated threat intelligence updates from the AT&T Alien Labs security research team - built directly into your USM Anywhere deployment.
Our Cybersecurity is trusted & verified
Our Cybersecurity makes compliance a top priority for your organization and for ours. We have adopted the NIST Cybersecurity Framework (CSF), aligning our security controls and processes with industry-proven security best practices. We use our own USM platform to demonstrate and maintain compliance, working with third-party auditors to regularly test our systems, controls, and processes.





* The ISMS that governs USM Anywhere, USM Central
Detect and report on cloud-based intrusions
Public cloud adoption offers some security advantages, most notably that cloud service providers generally take ownership of securing their own infrastructure through the shared responsibility model. Within this model, the security burden for your public cloud environments is divided between you and the service provider. Providers are responsible for securing the cloud infrastructure they offer, whereas the security of everything deployed within the cloud is completely up to you.
Although this arrangement lifts a portion of the hybrid cloud security burden from your shoulders, it also introduces new challenges. With sole ownership of cloud infrastructure security, service providers have been able to shrink your attack surface by abstracting away the network infrastructure. However, these architectural changes make it impossible for you to use traditional security methods such as network intrusion detection (NIDS) in the cloud.
Without the right monitoring tools to show you what’s happening in the cloud, you’re flying blind. Luckily, USM Anywhere provides everything you need to secure the public cloud, alongside your on-premises and private cloud security.
USM Anywhere gives you the highest possible level of control over your cloud security posture with sensors built to integrate with cloud infrastructure. USM Anywhere sensors hook directly into cloud APIs to leverage the security controls offered by cloud service providers, giving you complete visibility into your cloud environments
Using USM Anywhere, you can identify what is deployed in your cloud environments, scan for vulnerabilities, monitor user activity, detect intrusions, and collect log data to support compliance efforts.
In addition, the high volume of data generated by cloud environments can be overwhelming without the right tools to manage it. USM Anywhere uses a powerful graph-based analytics engine to make your security analysis faster and more effective. As a result, you can view a complete state model of your environment at any given time and even compare different time periods.
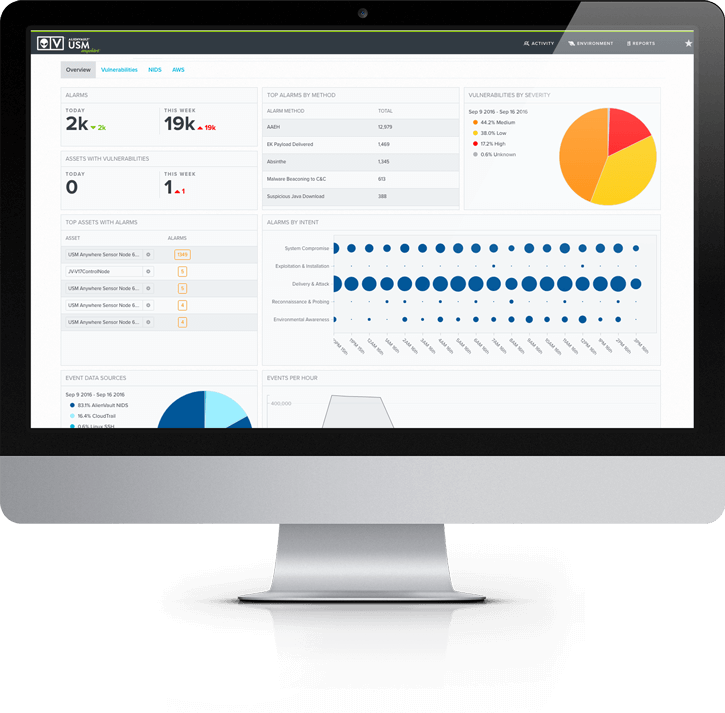
Security monitoring built for the cloud
Hybrid cloud security relies on an understanding of the unique security challenges posed by cloud environments. Unlike network environments, the cloud represents an elastic model, meaning that additional cloud resources can be spun up quickly according to your organization’s needs. This is great for rapidly changing organizations, but it also means that an intrusion or stolen root access key can result in a substantial bill.
Some hybrid cloud threats are specific to public cloud infrastructure, like the stolen root key example. Others apply to both cloud and network environments, but not always in the same ways. For example, your cloud environment may be resilient to a DDOS attack that would cause downtime in a network environment. However, the resources engaged to handle that influx of traffic can affect your monthly bill.
While cloud architecture mitigates some traditional network security threats, many still apply. If an attacker can breach your cloud environment through a vulnerable OS or application, your entire environment can be compromised. To secure your hybrid cloud infrastructure, you need a solution specifically built to address these threats in the cloud.
Control starts with knowing what’s deployed in your environments, which is essential under the shared responsibility model but can be an obstacle in rapidly-changing cloud environments. USM Anywhere allows you to discover assets across your infrastructure, including cloud environments, and stay on top of changes that occur. Once you have an inventory of the assets in your environments, you can perform vulnerability scans to find and patch weak points.
USM Anywhere provides visibility into user activity in the cloud to help you detect cloud-specific threats. Given the dynamic nature of the cloud, it’s important to monitor your cloud environments for suspicious root account logins, changes in security policies and privileges, and other unusual activities.
With USM Anywhere, you can understand which users and systems are interacting with your cloud environments, what assets they have accessed, and what they may have changed. By detecting suspicious activity quickly, you can reduce the time an attacker can use to compromise your organization’s sensitive data—or drive up your monthly bill.
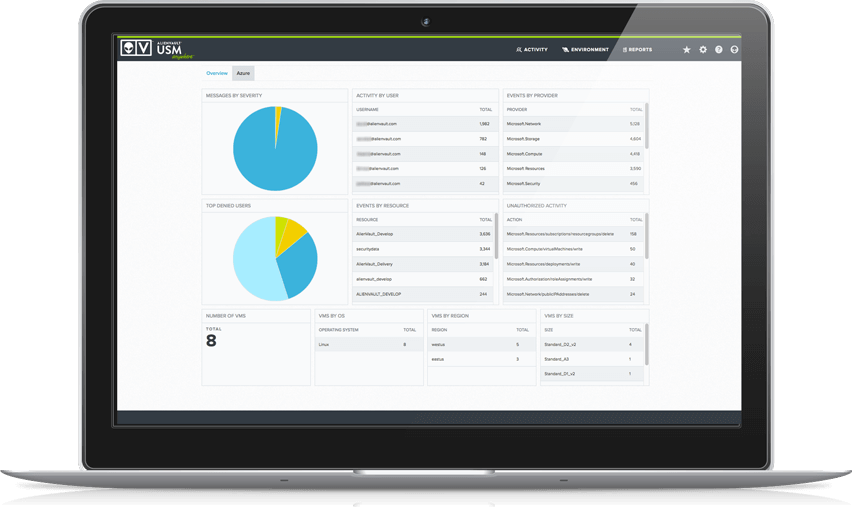
Unified security for cloud, hybrid and on-premises
Hybrid cloud security raises the challenge of finding appropriate solutions for the full breadth your infrastructure. Whereas on-premises and private cloud environments call for one set of tools, public cloud security requires purpose-built tools that operate differently than traditional network security solutions.
Layering single-point solutions is a recipe for headaches and high costs. Without a way to integrate all the security functionalities you need, it’s impossible to form a complete understanding of your security posture.
USM Anywhere provides one unified solution for your on-premises, private cloud, and public cloud environments, including the five essential capabilities you need to secure your hybrid cloud infrastructure.
Asset Discovery
Discover and inventory the assets across your network and cloud environments, including AWS, Azure, VMware, and Hyper-V.
Vulnerability Scanning
Detect and remediate vulnerable assets in your cloud and on-premises environments with regularly-scheduled vulnerability scans from within a single solution.
Intrusion Detection
Identify threats with network intrusion detection (NIDS), host intrusion detection (HIDS), and cloud intrusion detection (CIDS), all integrated within a single solution.
Behavioral Monitoring
Detect suspicious behavior with out-of-the-box correlation rules, continuously updated by the expert AT&T Alien Labs Security Research Team.
SIEM and Log Management
Correlate and analyze security event data from across your cloud and on-premises critical infrastructure to prioritize response efforts and support compliance requirements.


