Hosted IDS: Host-based intrusion detection system
Protect your critical systems in on-premises, cloud, and hybrid environments with the built-in host-based intrusion detection system (HIDS) of USM Anywhere.
Monitor and Protect Your Critical Systems with Host-based IDS
A host-based IDS is an intrusion detection system that monitors the computer infrastructure on which it is installed, analyzing traffic and logging malicious behavior. An HIDS gives you deep visibility into what’s happening on your critical security systems. With it, you can detect and respond to malicious or anomalous activities that are discovered in your environment.
On its own, host intrusion detection does not give you a complete picture of your security posture. You must be able to correlate your HIDS log data with other critical security data and with the latest real-world threat intelligence.
Unified Security Management® (USM) eases security analysis and correlation by combining host-based IDS along with network- and cloud-based IDS, and other essential security capabilities in a single, unified security environment. With it, you can easily manage your cloud and on-premises security posture from a single pane of glass. In addition, continuous threat intelligence updates from the Alien Labs Security Research Team are delivered to USM, backed by the Open Threat Exchange® (OTX™)—the world’s first open threat intelligence community.
Detect Changes & Threats to Your Critical Systems
- Detect Unauthorized Access Attempts
- Identify Anomalous Activities
- Know When and Who Accessed & Changed Critical Files with File Integrity Monitoring (FIM)
- Protect the Integrity of your Assets and Data
Deploy Host IDS as part of a Unified Security Management Platform that includes:
- Asset Discovery & Inventory
- Vulnerability Assessment
- Network & Cloud IDS
- Behavioral Monitoring
- Incident Response
- SIEM Event Correlation and Log Management
Stay Vigilant with the Latest Threat Intelligence from Alien Labs and OTX
- Alien Labs Researches Threats for You
- Continuous Threat Intelligence Continuously Automatically
- Community-powered Threat Data from the Open Threat Exchange (OTX)
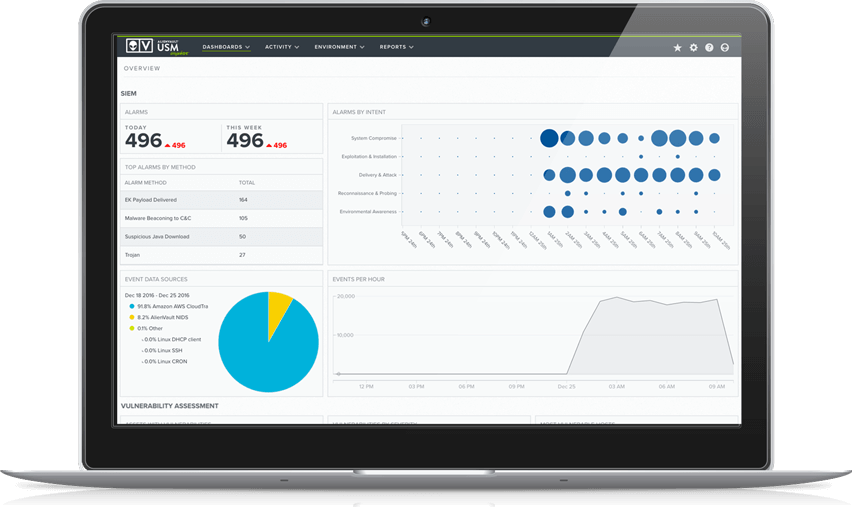
Detect Threats to Your Critical Systems
USM’s built-in host-based intrusion detection system (HIDS) monitors your critical systems and alerts you to any unauthorized or anomalous activities that occur.
A lightweight agent runs on each monitored host, tracking any changes made to critical system files, configuration files, log files, registry settings, and even important content files. The HIDS agent collects this information and sends it to the USM platform for evaluation and correlation with other environmental data and threat intelligence.
With the USM platform’s host-based IDS, you gain granular visibility into the systems and services you’re running so you can easily detect:
- System compromises
- Privileged escalations
- Installation of unwanted applications
- Modification of critical application binaries, data, and configuration files (e.g. registry settings, /etc/passwd)
- Rogue processes
- Critical services that have been stopped, or that failed to start
- User access to systems
Detect Unauthorized & Anomalous Activities
When malicious or anomalous activities occur on a system—such as brute force authentication-based attacks or a user logging into an unauthorized asset—HIDS detects the activities and sends them to the USM platform for analysis. When an alarm is generated in the USM platform, it captures all you need to know about the incident, including asset information (OS, software, and identity), vulnerability data, network communication, raw log data, and more.
Identify Changes and Access to Critical Files with File Integrity Monitoring (FIM)
File integrity monitoring allows you to track access and changes made to sensitive files on your critical systems, and is specified for compliance with regulations and standards like PCI DSS. This provides a necessary audit trail and allows you to validate that the changes were authorized, expected, and did not jeopardize the integrity and security of your system and application binaries, and configuration and data files.
View Failed Attempts to Gain System Access
Know which of your assets attackers are trying to infiltrate before they get in. The USM platform’s HIDS capability generates events on failed authentication attempts for Windows, MySQL, remote access, SSH service, and more.
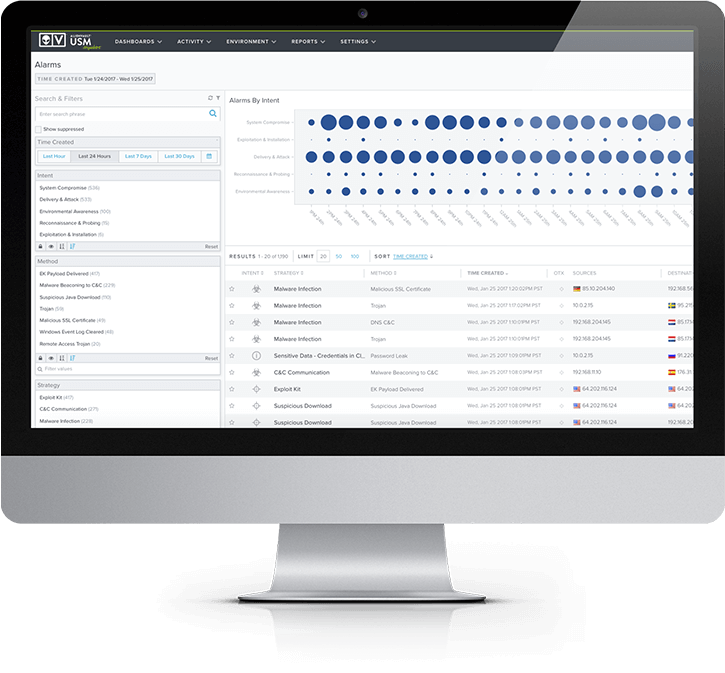
Deploy Host IDS as part of a Unified Security Management Platform
In USM, the host intrusion detection system is natively integrated out of the box with other essential security capabilities. This significantly reduces the cost and complexity of integrating multiple disparate security tools and data sources. Instead, the USM platform delivers complete visibility of your security posture on Day One and continues to update your environment with the latest security intelligence as new threats emerge or evolve in the wild.
USM combines the following essential security capabilities in a unified security management platform.
Asset Discovery & Inventory
The USM platform automatically scans and discovers all the IP-enabled devices in your environment, how they’re configured, what services are listening on them, and any potential vulnerabilities and active threats being executed against them.
Vulnerability Assessment
With vulnerability management in USM, you can find the weak spots in your environment that expose you to threats and remediate them before intrusions occur. And, when intrusions do occur, you have a unified view of important asset and vulnerability data so you can respond faster. USM performs authenticated and unauthenticated vulnerability scanning as well as continuous passive monitoring with the most up-to-date vulnerability signatures from the Alien Labs Security Research Team.
Network and Cloud Intrusion Detection System (IDS)
The IDS capabilities of the USM platform detect known threats and attack patterns targeting your vulnerable assets. It scans your network traffic and activities within cloud environments (including AWS and Microsoft Azure), looking for the signatures of the latest attacks, malware infections, system compromise techniques, policy violations, and other exposures, and it raises alarms in USM to alert you as soon as threats are identified.
Behavioral Monitoring
The behavioral monitoring capabilities of the USM platform help identify anomalous user and administrator activities that fall outside of your baseline or “normal” operations. USM works to identify suspicious events, such as changes to technical policies, the creation and deletion of significant volumes of user accounts, and more.
Incident Response
The USM platform delivers detailed information on detected threats, along with recommended guidance on how to contain and mitigate the threat. Built-in AlienApps deliver the ability to orchestrate responses, whether manually or automatically, working with third-party solutions like Palo Alto Network Firewalls, Cisco Umbrella, Carbon Black, and more to implement responses such as isolating infected systems, and blocking access to known malicious IP addresses and domains.
SIEM & Log Management
The USM platform incorporates powerful SIEM and centralized logging capabilities, so you can readily identify and investigate security incidents from a single console. Security events from across monitored environments and the host-, network-, and cloud-IDS capabilities of the USM platform are aggregated and correlated, and when incidents are identified you have immediate 360° visibility of the actors, targeted assets and their vulnerabilities, methods of attack, and more.