Azure PCI DSS compliance
Be ready for Azure PCI DSS compliance with AlienVault USM Anywhere.
Accelerate Azure PCI DSS Compliance & Security Monitoring
If your organization transmits, processes, or stores credit card data in your Azure cloud environment, you likely need to achieve Azure PCI DSS Compliance. This requires you to demonstrate that you have in place robust security controls to monitor changes in critical infrastructure, detect vulnerabilities, protect cardholder data, and much more.
For small IT security teams or for teams with limited Azure security monitoring experience, this can seem like a daunting task.
However, it doesn’t have to be complex or costly to implement the security controls needed to achieve PCI DSS compliance in your Azure cloud and on-premises environments.
AlienVault® USM Anywhere™ helps you to simplify and accelerate your Azure PCI DSS Compliance by combining multiple essential security capabilities onto a single platform that supports many PCI DSS 3.2 requirements. USM Anywhere provides native security monitoring for Azure cloud environments as well as your physical and virtual on-premises infrastructure and retail outlets, so you can centralize your entire compliance management and security monitoring program onto a single, affordable solution.
AlienVault USM Anywhere allows you to:
- Discover all your Azure environment assets, including OS details, while satisfying Azure scanning policies
- Identify vulnerabilities like unpatched software or insecure configurations
- Centrally collect and analyze log data from cloud and on-premises infrastructure, including Azure cloud
- Correlate security events automatically with AlienVault Labs predefined rules
- Understand the objectives of threats targeting your network
- Speed incident response with built-in remediation guidance for every alert
- Monitor and report on security controls required for HIPAA compliance
Our Cybersecurity is trusted & verified
Our Cybersecurity makes compliance a top priority for your organization and for ours. We have adopted the NIST Cybersecurity Framework (CSF), aligning our security controls and processes with industry-proven security best practices. We use our own USM platform to demonstrate and maintain compliance, working with third-party auditors to regularly test our systems, controls, and processes.





* The ISMS that governs USM Anywhere, USM Central
Reduce the Complexity of PCI DSS Compliance in Azure
USM Anywhere delivers multiple essential security capabilities in one unified solution, so you can reduce the number of security tools you need to purchase to demonstrate Azure PCI DSS Compliance.
By bringing together asset discovery and inventory, vulnerability assessment, intrusion detection, behavioral monitoring, SIEM event correlation, and log management onto a single affordable solution, USM Anywhere aligns with the goals of PCI DSS.
Build and Maintain a Secure Network and Systems
USM Anywhere provides security monitoring of your Azure cloud environment as well as your on-premises environment, allowing you to monitor configuration changes to your network firewalls and routers, identify weak or default passwords, and at the same time identify Azure configuration issues that may leave you exposed.
Maintain a Vulnerability Management Program
USM Anywhere’s built-in asset inventory, vulnerability assessment, threat detection, and log analysis capabilities provide the continuous security visibility you need to detect and respond to intrusions and vulnerabilities quickly.
Implement Strong Access Control Measures
SIEM event correlation and log analysis in USM Anywhere captures all user account activities on critical systems in Azure and in your data center, as well as collection and correlation of valid and invalid authentication attempts, so you always know who is trying to access your cardholder data environment (CDE).
Regularly Monitor and Test Networks
Continuous monitoring of user access to your Azure data processing resources and testing for vulnerabilities in your environment are not only requirements for PCI compliance but also critical security monitoring activities. USM Anywhere combines vulnerability assessment, event correlation, and log management to give you the security visibility you need in one central location.
Maintain an Information Security Policy
USM Anywhere supports your information security policy by helping you to detect breaches sooner and to respond faster by enabling automated incident response and giving you all the relevant security data you need at your fingertips along with response guidance and threat intelligence.

Measure Up to the Most Challenging PCI DSS Requirements
PCI DSS REQUIREMENT 10: LOGGING & AUDIT TRAILS
PCI DSS Requirement 10 is one of the most commonly misunderstood PCI DSS requirements. In short, Req. 10 deals with the “who, what, where, and when” of users who access your sensitive data.
10.1 - 10.5 deal with collecting and securing audit logs, tracking access to cardholder data, admin actions, failed logins, and attempted changes to the audit trail.
USM Anywhere collects user activity data from your applications, systems, devices, and Azure cloud infrastructure. The data is parsed and immediately available to search on and run reports to evaluate what individual users are doing across your infrastructure. Additionally, USM Anywhere timestamps the data and stores it in a write once, read many (WORM) log storage to prevent tampering or modification of the data.
10.7 requires you keep audit history for at least one year, with a minimum of three months immediately available for analysis. USM Anywhere stores data online for 90 days, making it easy to view, analyze, and report on the data as required by PCI DSS. USM Anywhere also retains the data long term for a full year and includes options to store the data for longer if needed. This simplifies log management and secures long-term raw log retention for PCI DSS compliance, even in high-volume environments.
PCI REQUIREMENT 11: VULNERABILITY ASSESSMENT
PCI DSS Requirement 11 centers on continuous testing of your environment to identify vulnerabilities, intrusions, and unauthorized system changes.
Out of the box, AlienVault USM Anywhere provides vulnerability assessment that allows you to detect and assess weaknesses of the systems in your Azure and on-premises environments. USM Anywhere’s continuous asset discovery and vulnerability scanning identifies vulnerabilities and correlates the data gathered by asset discovery scans with known vulnerability information for richer context.
By unifying the security data from its built-in asset discovery, vulnerability assessment, and intrusion detection capabilities, USM Anywhere provides the full situational awareness needed to reliably test your security systems and processes.
PCI DSS REQUIREMENT 12: INCIDENT RESPONSE PLANNING
With the Azure-native cloud sensor in USM Anywhere, you gain the assurance of complete security visibility and continuous threat detection for your Azure cloud environment. When an incident happens, USM Anywhere provides security orchestration and automated incident response as a first line of defense, and gives you all the relevant security data you need to respond quickly and to mitigate the potential damage of a breach.
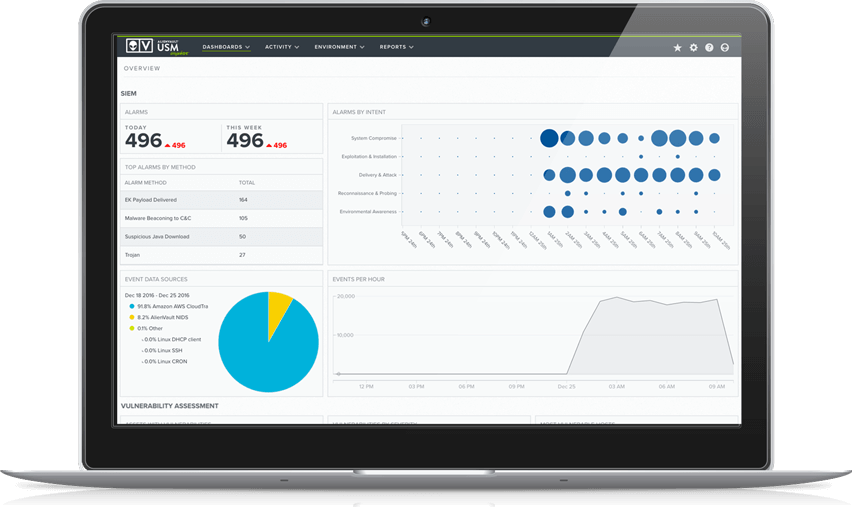
Discover How AlienVault USM Supports
PCI DSS Requirements
PCI Requirement
PCI Sections LevelBlue USM Addresses
How LevelBlue USM Helps
1. Install and maintain a firewall configuration to protect cardholder data.
1.1, 1.2, 1.3
- Built-in asset discovery provides a dynamically updated inventory of assets across your cardholder data environment, ensuring only authorized endpoints are deployed.
- Capture events relating to configuration changes on firewalls and routers, including when user accounts get updated.
- Discover unauthorized communications, such as between untrusted networks and systems within the cardholder data environment.
2. Do not use vendor-supplied defaults for system password and other security parameters.
2.1, 2.2, 2.3, 2.4, 2.6
- Identify use of default system accounts on Windows machines.
- Non-customizable File Integrity Monitoring can detect changes to predetermined paths in Windows and Linux systems.
- Identify vulnerabilities such as where an application may have a cryptographic algorithm vulnerability and recommend if patches or workarounds are available.
- Help identify specific services, ports, systems, and users
- Built-in asset discovery provides a dynamically updated inventory of what systems are operational in your environment, and what software is running on each.
- Discover and monitor assets running on-premises and in cloud environments (including Azure, VMware, Hyper-V, AWS, GCP)
3. Protect stored cardholder data
3.6, 3.7
- Monitor for changes to Office 365 policies, including data loss prevention (DLP), information management, and more.
- File Integrity Monitoring can detect when SSH or similar cryptographic keys are modified.
- Unified log review and analysis, with triggered alarms for high-risk systems.
4. Encrypt transmission of cardholder data across open, public networks
4.1, 4.3
- Identify when network traffic goes to unauthorized networks.
- Identify systems using compromised or insecure protocols that may increase their risk of being attacked.
- Monitor for changes to Office 365 policies, including Information Management and more.
5. Protect all systems against malware and regularly update antivirus software or programs
5.1, 5.2, 5.3, 5.4
- Identify systems susceptible to known vulnerabilities, or that may not have antivirus installed and/or operational.
- Identify for indicators of malware-based compromise, and orchestrate manual and automated actions to isolate infected systems and block malicious domains.
- Monitor and store events from antivirus solutions that could indicate a compromise, or attempt to disable antivirus software.
- Monitor for changes to Office 365 policies, including Information Management and more.
6. Develop and maintain secure systems and applications
6.1, 6.2
- Identify systems susceptible to known vulnerabilities, with systems ranked as 'high,' 'medium,' and 'low' risk vulnerabilities.
- Identify patches or workarounds available to vulnerable systems.
7. Restrict access to cardholder data by business need to know
7.1, 7.3
- Identify attempts to access systems using privileged accounts.
- Identify escalation of privilege attempts.
- Monitor for changes to Office 365 policies, including Information Management and more.
8. Identify and authenticate access to system components
8.1, 8.2, 8.5
- Aggregate logs and events from systems, applications, and devices from across your on-premises and cloud environments.
- Identify attempts to use retired or default user credentials.
- Monitor and alarm on Group Policy errors.
9. Restrict physical access to cardholder data
N/A
- Not applicable.
10. Track and monitor all access to network resources and cardholder data
10.1, 10.2, 10.3, 10.4, 10.5, 10.6, 10.7, 10.8
- Aggregate, analyze, and archive logs and events from systems, applications, and devices from across your on-premises and cloud environments.
- Identify logon success and failures.
- Identify privilege escalation attempts.
- Identify where systems are out of sync with the current time and/or Domain Controller, or for non-typical traffic on port 123.
- Identify unauthorized attempts to access or modify key logs.
- Identify where security tools, such as antivirus and firewalls, have been disabled or have failed to start.
- Captures all user account creation and modification activities.
11. Regularly test security systems and processes
11.1, 11.2, 11.4, 11.5, 11.6
- Assess systems for vulnerabilities, and where found rank them as 'high', 'medium,' and 'low' risk.
- Monitor access to and attempt to modify system and application binaries, configuration files, and log files.
- Monitor user and administrator activities in cloud environments such as Azure and AWS, and within cloud applications such as Office 365.
- Apply labels to alarms.
- Generate incident tickets within popular solutions like ServiceNow, directly from within the USM Anywhere console.
12. Maintain a policy that addresses information security for all personnel
12.1, 12.5, 12.8
- Monitor for changes to Office 365 policies, including Data Leakage Protection (DLP), information management, and more.
- Monitor all administrative activities through popular authentication and authorization solutions like Azure Active Directory.
- Monitor network traffic for violations of policy, such as communications that cross your cardholder data environment perimeters.