It’s been a busy season in the world of information security, and one of the more notable events was the successful attack on Sony. Initially, it looked like a targeted attack aimed solely at leaking in-theater and unreleased movie titles; not a benign move but definitely something the movie studio could easily recover from.
Then we started to see the attack for what it really was: an all-out malicious attack on the Sony brand, leaking not only digital copies of movies but also exposing the personal information of Sony employees, future film script, confidential emails between studio execs, and even explicit financial information about the studio as well as some of their actors.
Meanwhile, our AlienVault Labs threat research team, led by Jaime Blasco, has been tracking this event and quickly discovered that a particularly nasty piece of wiper malware had been used in conjunction with these attacks. Wiper malware is so-named because it exists to wipe the hard drive (and usually the master boot record) of a computer, rendering it useless. We have seen wiper malware before (remember “Shamoon” and “Dark Seoul”?) and while the malware seems to be of similar architecture and intent, the intent of the attacks appears to differ greatly. While the Shamoon and Dark Seoul attacks were executed by unknown forces, this recent event came from a clearly defined source: “Guardians of Peace” or G.O.P.
Our Labs team has already released several IDS signatures to detect the custom-built malware used in the latest attacks communicating with external C&C servers. You will, however, need to update USM as soon as possible to enjoy the benefit of this detection.
We push out regular updates of our Threat Intelligence to keep our customers up-to-date against the latest threats. To view some of the threat intelligence updates we’ve provided our AlienVault USM customers, check out our AlienVault Forum: https://success.alienvault.com/s/topic/0TO0Z000000oRS2WAM/att-alien-labs
You can update AlienVault Unified Security Management (USM) one of two ways:
Update via the web based user interface
1. Log into the USM web UI
2. From the menu up top, select “Configuration”, then “Deployment"
3. Under “AlienVault Components Information,” the USM components with available updates will have a clickable yellow arrow under the “New Updates” column.
4. Select which USM component you would like to update by clicking the arrow.
5. Review the available updates and select either “Update” to update the USM version as well as the Threat Intelligence or select “Update Feed Only” to update only the Threat Intelligence.
Update via the Appliance Menu
- Log into your USM appliance
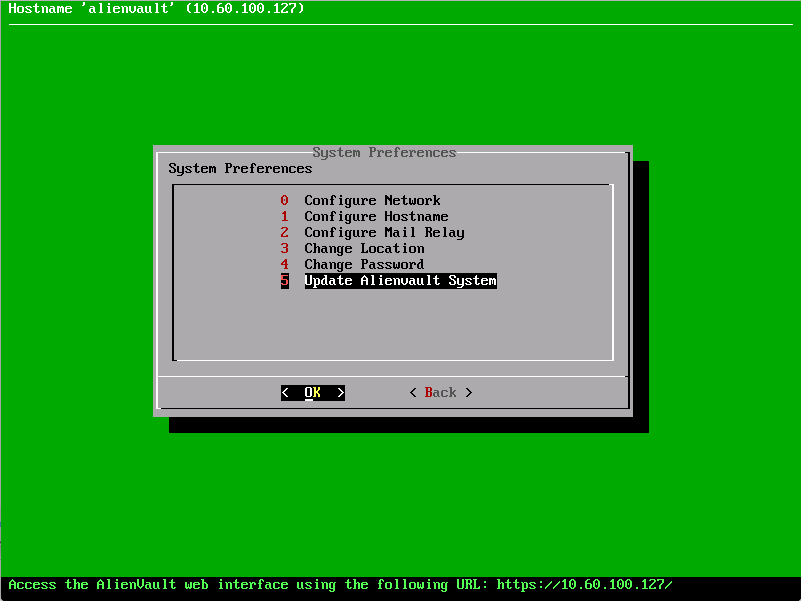
2. Select “System Preferences"
3. Select “Update AlienVault System"
4. Choose “Update Threat Intelligence” (you can also update USM here by selecting “Update System”)
So, nobody wants to be the next Sony - please update USM now to be protected! If you don't already have USM, please check it out.