Watering hole attacks – or the hijacking of legitimate websites to push malware – are increasing dramatically. These attacks are like traditional drive-by downloads, with one major difference: they are highly targeted in nature and detecting these attacks is notoriously difficult.
With watering holes, attackers target anywhere from a single company or government agency to larger communities of interest – such as industries or groups of companies.
I interviewed Victor Obando, Sr. SE at AlienVault, on this topic. We discussed how IT teams can detect watering hole attacks and the best methods to mitigate the impact to the organization. This is Victor:

According to Victor, attackers are opportunistic increasingly taking advantage of simple mistakes humans tend to make. Watering hole attacks are interesting in that they are very passive in nature and can develop over a long time frame. They involve compromising an existing trusted site or creating a site that looks legitimate, perhaps with a misspelling that will snare some unsuspecting users – perhaps amricanexpress.com. Then they wait until a victim comes to them by responding to a phishing email or mistyping a valid URL.
Question: How do attackers create watering hole attacks?
Answer: Here’s a slide we use to talk about this:

Question: Can you give me a scenario of how this might work?
Answer: Sure. To start with, these attacks can be very difficult to detect due to the fact that they might look just like usual business activity.
In many cases these attacks have victims on both sides. The first victim is the one who owns the compromised website used for the watering hole attack. The second one is the actual targeted victim of the attacker - in this case anyone who has a legitimate need to access the previously mentioned site.
To illustrate this a bit, let’s say a particular attacker is after a well-known car manufacturer and is looking for ways to infiltrate the organization. Then here comes Bob. Bob has a small manufacturing business that produces bolts and nuts for the car industry. He has set up a website for his customers where they can obtain information about production status and details about the parts he makes.
This small business has come to the attacker’s attention due to the level of interactions his targeted victim (the car manufacturer) has with it. In addition, as a small business, Bob might not have a strong security practice and/or the internal expertise to implement security controls. Bob might say, “I’m just making nuts and bolts” and not invest in security, so compromising his site might be a simple task for the attacker and poor Bob might never even notice.
The attacker then finds a way to inject a Java script into Bob’s website that will redirect his victims to another site that looks very similar to Bob’s where he can prepare more reliable exploitation kits and distribute malware.
Once the attacker is done setting up Bob’s counterfeit website, all he needs to do is sit and wait. It’s just a matter of time until someone from the target car manufacturer with a system that’s not up-to-date on security updates to visit Bob’s website for information. As soon as they load the site they’ll be redirected to the malicious site, giving the attacker the opportunity to compromise the system.
The ramifications of these attacks can be catastrophic. The targeted car manufacturer might have to spend millions of dollars recovering from such attack. If data was exfiltrated, the cost might even be higher, and even put the company’s reputation at risk. For Bob, the damage can be even worse as losing his primary customer might mean the end of his business.
Question: I understand problems with users clicking on links on websites and downloading malware, but how can water holing work even if users don’t click on anything?
Answer: Every website contains a number of ways to indicate to web applications how to display content, since the visitor may be visiting using a PC, Mac, tablet or phone, and applications optimize their display to the device. These interactions are required for the site to tell the device how to display the information appropriately. Attackers abuse that information to figure out things like the visiting device type, browser type and version, Java and Flash version. With this information, scripts can look for vulnerability matches. Then appropriate attacks are launched all without the user clicking on anything. These are known as drive-by download attacks.
Question: I’ve heard of people reimaging systems, figuring that will solve their problems, only to discover the problems simply come back. How is this possible?
Answer: People don’t always take the time to understand the root cause of the problem they have. Even after reimaging a system, users can go right back to malicious sites as things such as favorites can take them back there. If applications such as Flash and Java aren’t updated frequently, even reimaging can be ineffective
Question: How does Network IDS help with things like this?
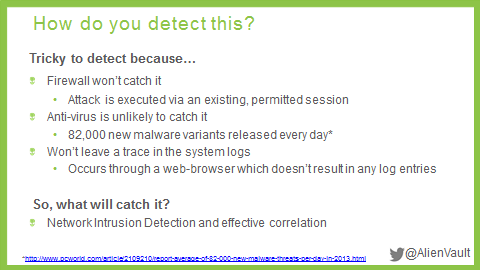
Answer: While vulnerability scans can be pretty good at finding flaws on web servers and web applications when thinking about the end user side, applications such as Flash and Java become a more challenging problem. Vulnerability scans are typically done periodically to limit the impact on performance, such as once a month. Passive Vulnerability Detection utilizing Network IDS is great for finding vulnerabilities in the interim. Here’s a slide we use to talk about passive network detection and its effectiveness with water holing attacks:
Check out this webcast on the topic featuring Victor.