Twitter can be both an extremely fun and infuriating medium to communicate via. Limited to 140 characters, one has to resort to creative ways to make a point succinctly.
Last week, we thought we’d kick the proverbial hornets nest with a tweet chat on the topic of threat intelligence. As expected, the conversation flowed fast and furious and often down many rabbit holes; continuing long after the hour we had set aside for the chat.
Here are some of the highlights of our favourite comments:
Q2: How do you evaluate Threat Intelligence sources (how do you decide what's good)? #secchat #AskAnAlien
— AlienVault (@alienvault) May 7, 2015
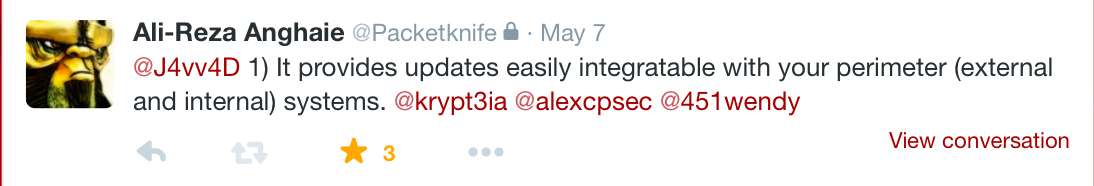
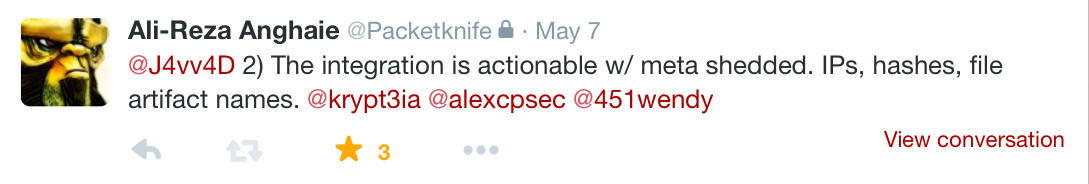
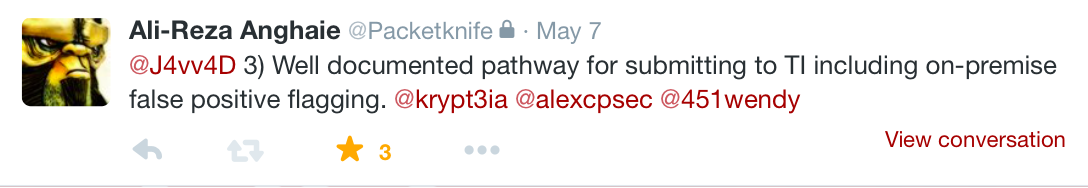
Ali-Reza Anghaie fired off a rapid succession of tweets that he seemingly had queued up and saved for this precise moment in time
Wendy Nather chimed in with her viewpoint
"Good threat intel" = Magic 8 balls "Bad threat intel" = pew-pew maps https://t.co/BkePp85oIE
— Wendy Nather (@451wendy) May 7, 2015
@J4vv4D @J4vv4D depends on audience. for Infosec,no. For infosec to show management to get funding #HFYes! :blush:
— Chris J (@rattis) May 7, 2015
And then we were off to the races. Quentyn Taylor felt the reputation of a threat intel provider was of importance when deciding on the quality of the feed.
@alienvault past experience - do they have a good track record ?
— Quentyn Taylor (@quentynblog) May 7, 2015
Gabe touched upon the oft-mentioned aspect of context.
@J4vv4D @krypt3ia @alexcpsec @451wendy Intel that puts other data in context is good. All else is bad.
— Gabe The Engineer (@gdbassett) May 7, 2015
On a more technical level, Alex Pinto felt that the sources of threat intel data was of great importance.
@J4vv4D not coming from lazy low-interaction honeypots or unconfigured sandboxes is a start @krypt3ia @451wendy @alienvault
— Alex Pinto (@alexcpsec) May 7, 2015
Ian Amit touched on the importance of threat intel needing to be relevant to a company’s own threat model. Adding weight to Gabe’s earlier comment about the data needing to be contextually relevant.
@J4vv4D @alexcpsec @krypt3ia @451wendy @alienvault 1. Show me the relevance to MY threat model. 2. What can I DO with it (modify controls)?
— Iftach Ian Amit (@iiamit) May 7, 2015
@krypt3ia @J4vv4D @alexcpsec @451wendy @alienvault 1. who are your threat communities (derives MO/tools). 2. Make sure you cover all of them
— Iftach Ian Amit (@iiamit) May 7, 2015
@krypt3ia @J4vv4D @alexcpsec @451wendy @alienvault Then figure if the regular vs apt mix makes sense.
— Iftach Ian Amit (@iiamit) May 7, 2015
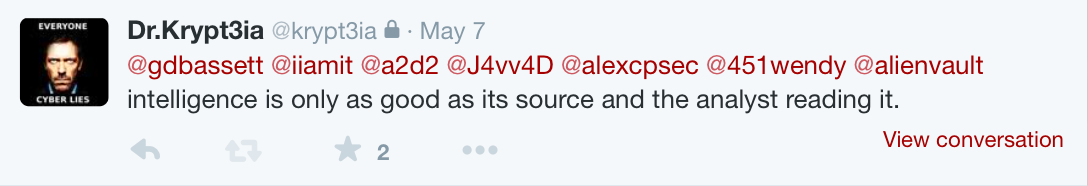
Dr. Kryptia lamented the disproportionate focus put on APTs (advanced persistent threats) versus the basic threats which more common attack
Our own Jaime Blasco shared his thoughts on the question as to the importance of incorporating threat intelligence into an information security program.
Q3: How important is incorporating threat intelligence into an information #security program? #secchat #AskAnAlien
— AlienVault (@alienvault) May 7, 2015
1) @alienvault Threat Intelligence is becoming more and more important since traditional security controls ... #secchat #AskAnAlien
— Jaime Blasco (@jaimeblascob) May 7, 2015
2) are not longer enough to detect and prevent modern threats and a constantly changing threat landscape #secchat #AskAnAlien @alienvault
— Jaime Blasco (@jaimeblascob) May 7, 2015
@alienvault I think it is fast becoming a commodity/necessity but is also in danger of going the way of antivirus tools #AskAnAlien
— Kevin Neely (@ktneely) May 7, 2015
On the uses of threat intelligence, Dan Glass reminded everyone that threat intelligence is a program and not a product.
@iiamit @451wendy @gdbassett @krypt3ia @a2d2 @J4vv4D @alexcpsec TI is a program, not a product. IOC is an input TI analyst would use.
— dan.g (@djglass) May 7, 2015
To Dan’s point, AlienVaults’ Andy Manoske clarified the company perspective on IOC’s and threat intelligence.
@iiamit @gdbassett @krypt3ia @J4vv4D @alexcpsec @451wendy @alienvault Our perspective: IoCs are raw data, instrumentation is TI
— Andy Manoske (@a2d2) May 7, 2015
Dan’s comment also tied into Wendy’s comment that questioned the true nature of indicators of compromise (IOCs) and whether they are just an evolution of signatures used in traditional anti-virus detection technologies.
@iiamit @gdbassett @krypt3ia @a2d2 @J4vv4D @alexcpsec IOCs are just big-ass signatures -- discuss
— Wendy Nather (@451wendy) May 7, 2015
Ian Amit summed up the sentiment in the only way you can on the internet, via a meme.
@451wendy @gdbassett @krypt3ia @a2d2 @J4vv4D @alexcpsec What's to discuss? IOC=signatures. It's not TI. pic.twitter.com/FI2Zu0vP3Y
— Iftach Ian Amit (@iiamit) May 7, 2015