Stories from the SOC is a blog series that describes recent real-world security incident investigations conducted and reported by the AT&T SOC analyst team for AT&T Managed Threat Detection and Response customers.
Executive summary
In the second half of 2021 the AT&T Managed Threat Detection and Response (MTDR) security operations center (SOC) observed an increasing number of attacks against vulnerable Exchange servers. A number of these attacks were attempting to leverage proxyshell vulnerability to gain access to customer’s networks. In one particular instance, a coordinated effort between the SOC analysts, Threat Hunters and the Incident Response team from AT&T Cybersecurity Consulting allowed AT&T Cybersecurity to quickly identify and mitigate the threat before real damage was done.
Due to the various tactics, techniques, and procedures (TTPs) observed, this attack has been associated with the ransomware-as-a-service (RaaS) group known as Conti. The team observed several tactics associated with Conti affiliates including Proxyshell usage, CobaltStrike Payload, and various remote desktop software such as AnyDesk, Atera, and Splashtop. If not for the quick response by the MTDR SOC, the next steps would have likely involved the exfiltration and encryption of critical customer data.
Investigation
Initial alarm review
Indicators of Compromise (IOC)
Initial alarm came in for remote use of powershell in order to download a file from IP “redacted” and drop it under the C: drive. Shortly after this alarm, the SOC analysts and Threat Hunters began conducting log analysis on the impacted Exchange server. The dropped file “new.dll” had signatures associated with CobaltStrike which is believed to have been used for lateral movement.
Expanded investigation
Events Search
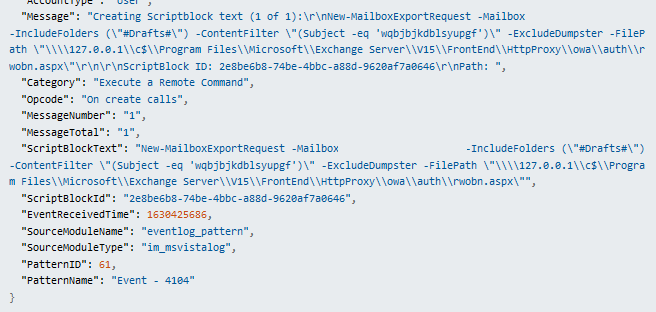
Upon diving into the logs, the team quickly uncovered a number of alarming events. Around the time the remote powershell was executed, we uncovered the attacker dropping a shell on to publicly accessible directories on the Exchange server in order to execute arbitrary remote commands. The New-MailboxExportRequest cmdlet was used to write the shell from impersonated users account. The log below shows the webshell “rwobn.aspx ” being written to an accessible directory. This vulnerability/exploit leveraged CVE-2021-31207.
Next we observed the attacker downloading two additional executables “vmhelp.exe” and “fix.exe”. The IP ranges seen in these two outbound request have been seen in CobaltStrike beaconing ranges. Following Conti TTPs, it’s believed these additional executables could have been enumeration or scanning tools used in the coming events uncovered.
Event deep dive – Lateral movement
We then observed the attacker performing lateral movement pivoting from the Exchange server on to a domain controller.
Pinging to domain controller
RDP login onto domain controller
Audit logs were cleared on domain controller
Reviewing for Additional Indicators – Remote Tools
The attacker then made system firewall rule exceptions in order to allow the usage of remote tools “Splashtop.exe” and “Anydesk.exe”. It is at this point that MTDR team was able to undertake mitigation actions and stop the attack from progressing.
Response
Building the Investigation
Thanks to the quick response of the MTDR team, all impacted assets were quickly identifed allowing the customer to quickly isolate them from the network. We also recommended the customer reset admin credentials, as these privileged accounts were leveraged in some of the TTPs observed.
In the detection, containment, and eradication phases, the MTDR team leveraged the deep visibility capilities of SentinelOne to further investigate the customers assets and ensure any uncovered remnants of the attack were quarantined and removed from the affected systems, including the executables detailed in this report.
The MTDR SOC continued close monitoring efforts in search of evidence of back-door persistance or potential dormant malware. As seen in the screen shot below, the team was able to uncover additional malware, related to Cryptominer, that would have been detrimental to the recovery process of the customer.
Customer interaction:
Upon discovering these events, the customer was contacted immediately and call was established to communicate our findings to key stakeholders. This investigation encompassed many hours and involved the efforts of several team members within MTDR. A special thanks goes out to Kenneth NG and Amer Amer, MTDR Threat Hunters, whose expertise and knowledge assisted the customer in identifying and remediating the affected systems. Due to the collective effort of the MTDR team, customer was able to stop the attack from progressing which could have crippled the customers network and business operations.