Executive Summary
Stories from the SOC is a blog series that describes recent real-world security incident investigations conducted and reported by the AT&T SOC analyst team for AT&T Managed Threat Detection and Response customers.
The most critical element in combating malicious attempts on technology today is visibility. When considering the sheer amount of various cloud, firewall, IDS/IPS, anti-virus, etc. offerings, integrations are a necessity to enable effective security. Unified management is unachievable unless you can effectively consume and correlate a variety of log feeds that can be analyzed through the proverbial “single pane of glass.” By leveraging the AlienApp for Office365, we presented a compromised Office365 account to the customer who then confirmed our suspicion, reset the account, and implemented multi-factor authentication for that user. Though the AlienApp provides an incredibly insightful view of an Office365 environment, the ability to correlate events across multiple data sources enables an analyst to understand and determine the baseline activity of our clients, enhancing our detection and response capabilities.
Investigation
Initial Alarm Review
Indicators of Compromise (IOCs)
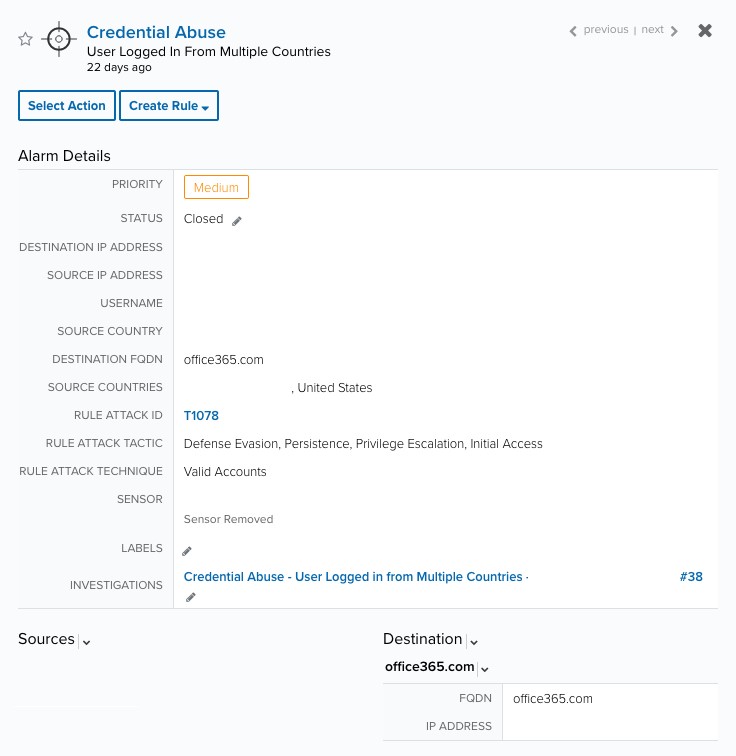
The initial alarm surfaced as the correlated result of two UserLoggedIn events that were within 10 minutes of each other but originated from 2 distinct countries. The abnormalities in login behavior indicate that a user’s credentials were most likely compromised.
Figure 1 - Initial Alarm
Expanded investigation
Alarm Detail
Also included in the alarm details is the associated MITRE ATT&CK® rule attack ID, which afforded the ability to efficiently and expeditiously gather relevant information about this potential attempt to compromise the customer’s Office 365 account. The synopsis for this attack technique is defined as the attempt to “… steal the credentials of a specific user or service account using Credential Access techniques or capture credentials earlier in their reconnaissance process…”
Correlation Rule Logic
Figure 2 - Correlation Logic
Correlated Events
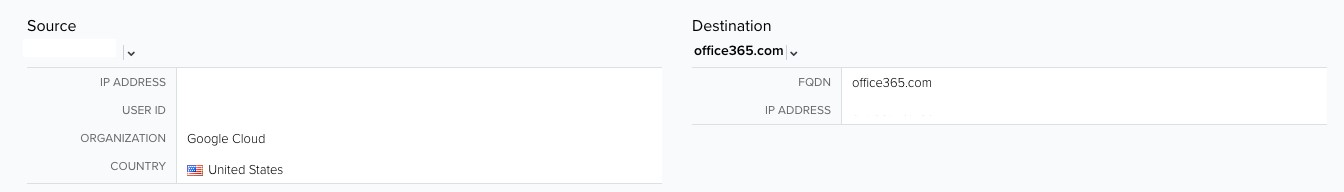
Figure 3 - U.S. Login Event
Simultaneous logins were detected from both the United States and a foreign country, generating two events, like the one pictured above, with different source countries. These successful logins occurred within two minutes of one another; thus, triggering the Credential Abuse alarm.
Response
Building the investigation
The successful login attempts’ origin and volume deriving from the United States fall within the baseline activity for this user. However, there was a sudden surge in attempts from a foreign country that aligned with the timeline of when this account had appeared to have been successfully compromised.
Customer interaction
In order to effectively articulate the login irregularities to the customer, our team did a retrospective query to analyze successful authentication attempts for this particular Office365 user. Utilizing advanced query capabilities within USM Anywhere, we presented information to the customer showing the source countries for all events created over a 48-hour period. Four of those events were generated in the US, while 10 of them were generated in a foreign country.
In addition to attaching data visualizations, we presented notes to the customer and asked their team to confirm whether or not the activity at hand was legitimate and/or expected. The notes included the compromised user account, the source IP addresses, and the countries the account was logged in from.
Customer Response(s)
Our customer’s staff reviewed the analysis that was provided, confirmed the trepidations pertaining to the credential compromise, and shared the subsequent steps that were taken to remediate this activity. The account was in fact compromised and corrective action was taken to prevent further malicious intent. The granularity of detail offered by the AlienApp for Office365 equipped our team with a host of information that ultimately allowed us to assist the customer in mitigating future Office365 intrusion attempts via this compromised account.