This blog was co-written by Leo Garcia, Sr. Specialist - Cybersecurity..
Stories from the SOC is a blog series that describes recent real-world security incident investigations conducted and reported by the AT&T SOC analyst team for AT&T Managed Threat Detection and Response customers.
Executive Summary
This Investigation was initiated on the basis of several Network Anomaly alarms triggered by ongoing suspicious activity on an employee device owned by a financial institution. During the discovery phase of the Investigation, we identified abnormal egress traffic to a known Indicator of Compromise (IOC) based on intelligence from the Open Threat Exchange™ (OTX®). After a carefully curated analysis of the activity at hand was presented to the customer, we worked closely with their IT personnel to remediate the concerning behavior and implement safeguards to help prevent similar occurrences.
Investigation
Initial Alarm Review
Indicators of Compromise (IOCs)
The initial alarm surfaced as the result of egress traffic to the OTX IOC 222[.]186[.]19[.]221, an IOC found in several OTX pulses with the designation of ‘Actively Malicious’.
Figure 1 - Initial Alarm
Expanded Investigation
Alarm Detail
During our preliminary analysis, we suspected this behavior to be an attempt to create a VPN through the client’s firewall to ultimately connect to a malicious host. Upon further review, we determined that the nature of these egress attempts implied the potentiality of a compromised system. Following the completion of our reconnaissance efforts, we presented our actionable information to the customer and requested their consent to continue our efforts.
After reviewing the investigation, the customer was quick to respond and requested guidance on how to proceed with employing a firewall rule to prevent further outbound traffic.
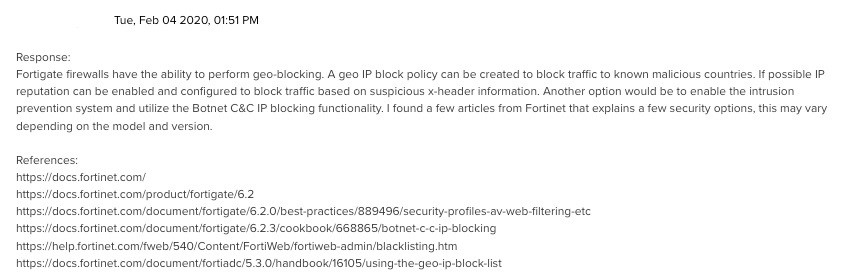
Given the limitations of their experience with firewall policies, we facilitated relevant documentation for ‘geo-blocking’ the origin country of the IOC.
Figure 2 - Analyst Recommendation
After equipping our client with the necessary guidance to execute our suggested course of action, the customer informed us of their proposed next steps. At this juncture, we acknowledged the customer’s response and concluded the investigation.
Persistent Alarms
Shortly after the closing of the initial Investigation, alarms similar to those first examined began to reoccur. Considering the potential implications of persistent behavior of this nature, we made the conscious decision to re-open and continue our investigative efforts. The newly generated alarm varied slightly from the others in the respect that the most recent activity appeared to be a Remote Desktop Protocol (RDP) connection attempt. Though the customer had enforced firewall blacklisting on ingress traffic, we conveyed our recommendation to block outbound traffic as well.
Response
Building the investigation
Bearing in mind the RDP activity, we decided to do a complete port scan of the customer asset in question in order to facilitate actionable insight with greater granularity.
Figure 3 - Asset Scan Results
Based on the results of the asset scan, we provided additional recommended actions to the customer. Tapping 15 years of sysadmin experience, we were able to also describe industry best practices for hardening an asset of this category.
Figure 4 - Analyst Recommendation
Customer Interaction
Figure 5 - Continued Communication
Though the customer attempted to work with their remote employee, they were unable to successfully void the concerns of continued beaconing activity and decided to act on the subsequent steps recommended by our team and distribute a new system to the affected employee.