Stories from the SOC is a blog series that describes recent real-world security incident investigations conducted and reported by the AT&T SOC analyst team for AT&T Managed Extended Detection and Response customers.
Executive summary
Internal Reconnaissance, step one of the Cyber Kill Chain, is the process of collecting internal information about a target network to identify vulnerabilities that can potentially be exploited. Threat actors use the information gained from this activity to decide the most effective way to compromise the target network. Vulnerable services can be exploited by threat actors and potentially lead to a network breach. A network breach puts the company in the hands of cybercriminals. This can lead to ransomware attacks costing the company millions of dollars to remediate along with a tarnished public image.
The Managed Extended Detection and Response (MXDR) analyst team received two alarms regarding an asset performing network scans within a customer's environment. Further investigation into these alarms revealed that the source asset was able to scan 60 unique IPs within the environment and successfully detected numerous open ports with known vulnerabilities.
Investigation
Initial alarm review
Indicators of Compromise (IOC)
The initial alarm that prompted this investigation was a Darktrace Cyber Intelligence Platform event that was ingested by USM Anywhere. The priority level associated with this alarm was High, one level below the maximum priority of Critical. Network scanning is often one of the first steps a threat actor takes when attempting to compromise a network, so it is a red flag any time an unknown device is scanning the network without permission. From here, the SOC went deeper into associated events to see what activity was taking place in the customer’s environment. The image shown below is the Darktrace alarm that initiated the investigation.
Expanded investigation
Events search
Utilizing the filters built into USM Anywhere , the events were narrowed down to the specific source asset IP address and Host Name to only query events associated to that specific asset. The following events were found that provide more information about the reconnaissance activity that was being observed.
Event deep dive
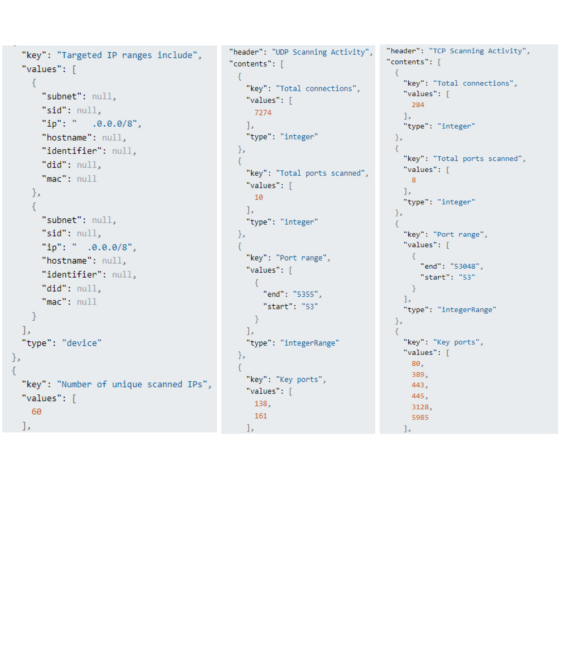
Upon reviewing the logs from the events shown above, the SOC was able to determine that the source asset scanned two separate Classless Inter-Domain Routing (CIDR) blocks, detecting, and scanning 60 unique internal devices for open ports. As shown in the log snippets below, the scans revealed multiple open ports with known vulnerabilities, most notable is Server Message Block (SMB) port 445 which is the key attack vector for the infamous WannaCry malware. Looking at the logs we can also see that the source asset detected port 5985, the port utilized by Windows Remote Management (WinRM). WinRM can be used by threat actors to move laterally in environments by executing remote commands on other assets from the compromised host. These remote commands are typically batch files performing malicious activity or implanting backdoors to maintain persistence in the network. Lastly, we can see the asset scanning for Lightweight Directory Access Protocol (LDAP) port 389. LDAP traffic, if not encrypted properly, can be sniffed with Wireshark and potentially expose sensitive information such as usernames and passwords.
Reviewing for additional indicators
After the initial analysis of the source asset, we pivoted our event search to include assets within the target IP ranges. Using the filters in USM Anywhere, the SOC was able to search the events in the customers environment for the targeted IP addresses and analyze all events searching for any anomalous activity that would indicate a breach took place. Further review into the customer's network did not reveal any additional activity following the scanning. The SOC was unable to find any evidence that the threat actor advanced from reconnaissance to weaponization, or further up in the kill chain. This suggests that the activity is isolated for the time being.
Response
Building the investigation
Due to the nature of reconnaissance scanning, this could potentially be a threat actor attempting to discover vulnerable services on assets within the environment. The customer was advised to quarantine the asset off the network and investigate the source of the scanning activity to determine if a compromise took place. It was recommended to run a full Antivirus scan on the asset to ensure that this activity was not related to malware attempting to move laterally in their environment.
Customer interaction
The customer was notified via phone call as defined in their Incident Response Plan (IRP). The customer was able to isolate the asset off the network to prevent any additional network scans. They then began to investigate the asset by performing a software inventory of the machine to determine the source of the network scanning and reviewing the Windows Event Viewer logs to determine the user account associated with the scanning activity. The quick response of the MXDR team allowed the customer to investigate the asset before any additional actions took place as a result of the initial network scans that triggered the alarms.