Stories from the SOC is a blog series that describes recent real-world security incident investigations conducted and reported by the AT&T SOC analyst team for AT&T Managed Threat Detection and Response customers.
Executive summary
The impact of Data Exfiltration, which is the act of copying or transferring data from a computer or server without authorization, has increased over the years and it can be difficult to detect because data is transferred regularly for normal business purposes. If not monitored accurately, company data can be stolen without anyone being aware. Companies in every industry, no matter the size, have sensitive data that must remain private (e.g. PHI, PII, PCI). Numerous examples in current events show how ‘stolen data’ can be detrimental to the productivity, reputation, and overall morale of the affected users. Not to mention the cost of disaster recovery, paying a ransom, or providing closure to customers of companies who have been breached.
The AT&T Managed Threat Detection and Response Security Operations Center (SOC) observed a connection between a customer asset and an indicator of compromise (IOC) with a known reputation as part of a malicious network ecosystem to host and/or distribute malware. Facilitated by a relationship with Darktrace and their Cyber Intelligence Platform, an alarm was produced based on the observance of data being transferred out of the network over a 4-hour period via several external connections. Upon the acknowledgment of the alarm, the SOC was able to research correlating events and provide the customer a detailed explanation of what took place within the customer environment thus aiding in the mitigation of this threat.
Investigation
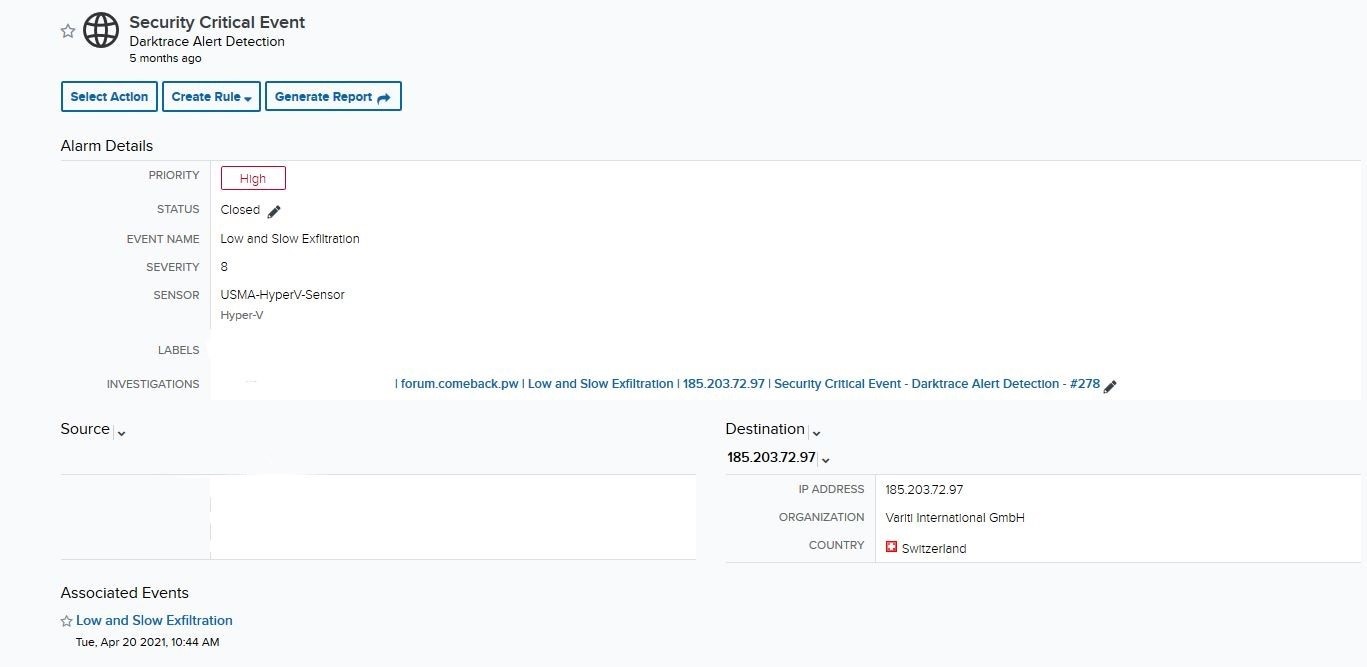
Initial Alarm Review
Indicators of Compromise (IOC)
A Sensor deployed in the customer environment was able to provide a parsed view of the alarm where we discovered a potential IOC that had been communicating with a customer asset. The analysts researched the foreign IP address using open source intelligence tools (OSINT), but did not find that it had a malicious reputation. Knowing that did not necessarily mean the activity was benign, the analysts investigated the event further to confirm the reputation of all IOCs present.
Expanded Investigation
Events Search
Upon looking into event logs of the alarm, another IOC < forum[.]comeback[.]pw > is produced. When cross-referenced with another OSINT tool, the domain is flagged for malicious intent.
Event Deep Dive
‘Suspicious’ alarms associated with the affected customer asset around the time of the original event were added to the Investigation, providing supporting detail for the customer.
Response
Building the Investigation
Based on the severity of the original alarm, and the fact that the IPs and domains provided different outcomes (one being malicious, one being benign), the SOC opened an Investigation. All supporting evidence was included in the Investigation, and a recommendation for remediation was also provided.
Customer Interaction
The customer was contacted immediately via telephone in accordance with their Incident Response Plan (IRP) after the investigation was created. Once assessed, the customer was able to confirm that the activity reported was not related to normal business activity. Configuration changes were carried out on the affected customer asset, mitigating the threat. The MTDR team provided a quick and concise breakdown of the event, along with a recommendation for remediation which made remediation seamless and timely for the customer.