In this blog, lets focus on the intersection of psychology and technology, where cybercriminals manipulate human psychology through digital means to achieve their objectives.
Our world has become more interconnected over time, and this has given rise to an entirely new breed of criminal masterminds: digital criminals with deep psychological insights who use technology as the ultimate battlefield for social engineering activities. Welcome to social engineering - where your mind becomes the battlefield!
Before the digital revolution, social engineering was practiced face-to-face and practitioners of this form were known as "con men," regardless of gender. Today however, cybercriminals use psychological methods to trick individuals into compromising their systems, divulging sensitive data, or participating in malicious activities unwittingly.
An unsuspecting employee receives an email purporting to be from an official subscription service for software used at their organization, prompting them to log-in as quickly as possible and avoid having their account frozen due to inactivity. Following a link in this email leading them directly to a convincing fake login page, unknowingly giving away their credentials which give a threat actor access to company systems and confidential data. This deception was an ideal example of Business Email Compromise (BEC). An attacker created an urgent phishing email designed to distort employee judgment. There was reconnaissance conducted beforehand by threat actors, so they already possessed information regarding both an employee's email address and web-based applications, making the attack became even more effective.
Social engineering is one of the primary strategies criminals use in their attempts to attack our systems. From an information security perspective, social engineering is the use of manipulative psychological tactics and deception to commit fraud. The goal of these tactics is to establish some level of trust to convince the unsuspecting victim to hand over sensitive or confidential information.
Here are some books that offer a range of perspectives and insights into the world of social engineering, from the psychology behind it to practical defenses against it. Reading them can help you better understand the tactics used by social engineers and how to protect yourself and your organization.
1. Influence: The Psychology of Persuasion" by Robert B. Cialdini
Robert Cialdini's classic book explores the six key principles of influence: reciprocity, commitment and consistency, social proof, liking, authority, and scarcity. While not solely focused on social engineering, it provides valuable insights into the psychology of persuasion that are highly relevant to understanding and defending against social engineering tactics.
2. "The Art of Deception: Controlling the Human Element of Security" by Kevin D. Mitnick
A former hacker turned cybersecurity consultant, delves into the art of deception and social engineering. He shares real-life examples of social engineering attacks and provides practical advice on how to protect yourself and your organization from such threats.
3. "Ghost in the Wires: My Adventures as the World's Most Wanted Hacker" by Kevin D. Mitnick In this autobiography, Kevin Mitnick recounts his personal experiences as a hacker and social engineer. He provides a fascinating insider's perspective on the tactics used by hackers to manipulate people and systems, shedding light on the world of cybercrime and social engineering.
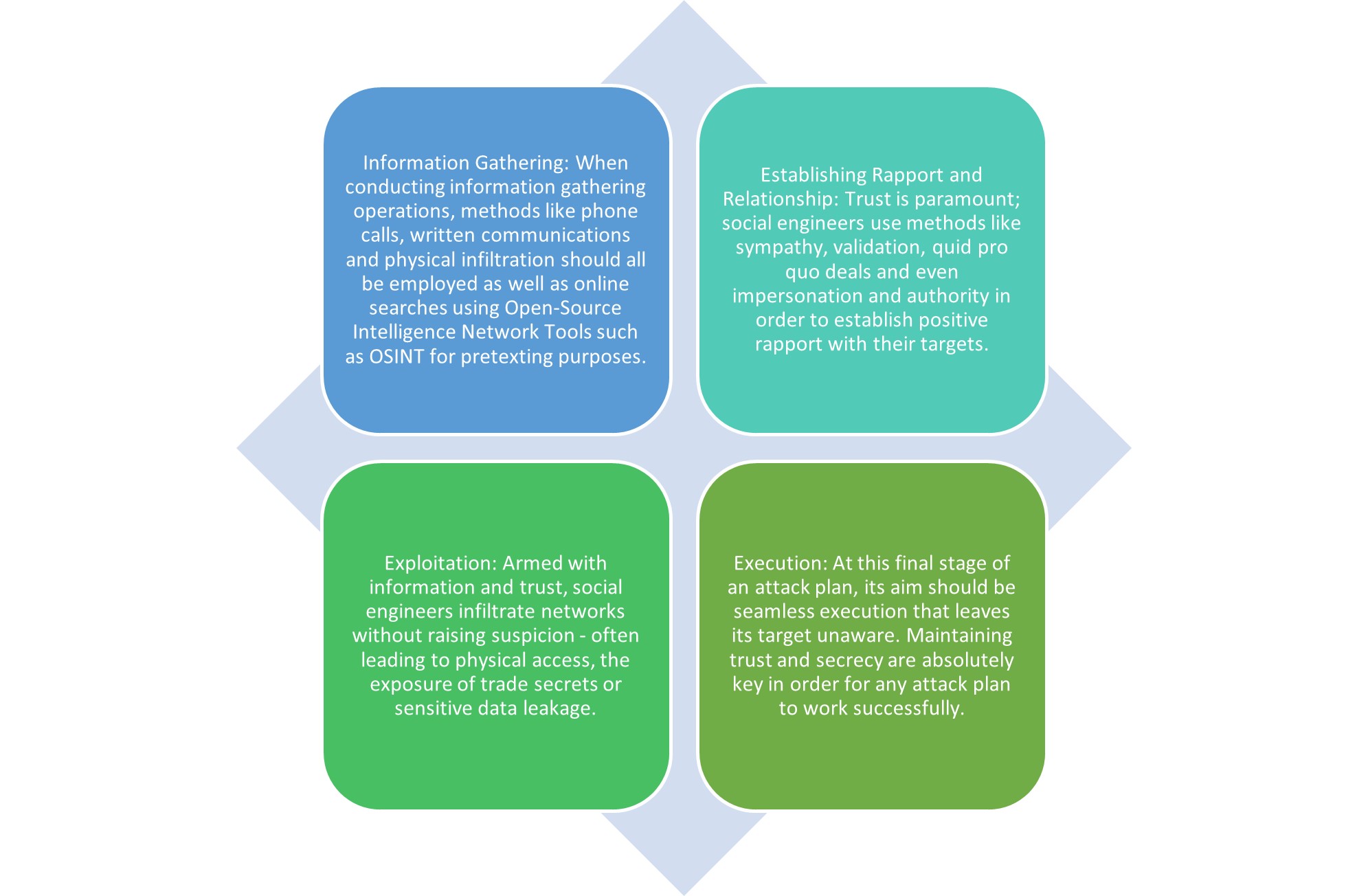
4. "Social Engineering: The Art of Human Hacking" by Christopher Hadnagy Summary: A comprehensive guide to social engineering techniques and strategies. It covers various aspects of human hacking, including information gathering, building rapport, and exploiting psychological vulnerabilities. It's an excellent resource for those looking to understand and defend against social engineering attacks.
5. "No Tech Hacking: A Guide to Social Engineering, Dumpster Diving, and Shoulder Surfing" by Johnny Long, Jack Wiles, and Scott Pinzon
Explores low-tech and non-digital methods of social engineering, including dumpster diving, physical intrusion, and eavesdropping. It provides insights into how attackers can exploit physical vulnerabilities and offers countermeasures to protect against such tactics.
6. "Phishing Dark Waters: The Offensive and Defensive Sides of Malicious Emails" by Christopher Hadnagy and Michele Fincher
Focusing specifically on email-based social engineering attacks, this book examines phishing techniques in detail. It provides insights into the tactics used by attackers to trick individuals into revealing sensitive information and offers guidance on how to defend against phishing threats.
7. "The Confidence Game: Why We Fall for It . . . Every Time" by Maria Konnikova
While not exclusively about social engineering, this book delves into the psychology of deception and the reasons why people often fall victim to scams and cons. It provides valuable insights into the vulnerabilities of human cognition and behavior that social engineers exploit.
Cyberattacks increasingly depend on human interaction for successful execution. Threat actors use psychology to exploit vulnerabilities and compromise systems. With sufficient awareness, training, policies, and procedures organizations can protect themselves against these insidious attacks by keeping aware of emerging vulnerabilities through training sessions, policies, and procedures as well as their regular assessment by skilled personnel.