What is Situational Awareness in Cyber Security? The concept of Situational Awareness is an extremely important one in information security cyber security operations. Situational Awareness is defined as: “Within a volume of time and space, the perception of an enterprise’s security posture and its threat environment; the comprehension/meaning of both taken together (risk); and the projection of their status into the near future.” [CNSSI 4009]. The National Institute of Standards and Technology (NIST) has a draft publication for Interagency Report (IR) numbered 7756 that outlines the CAESARS (Continuous Asset Evaluation, Situational Awareness and Risk Scoring) Framework.
On aspect introduced within the NIST IR 7756 is continuous monitoring, which is defined and presented as in an architectural diagram. The diagram presents the interrelation and ecology of the multiple layers of continuous monitoring elements. It is important to keep in mind that this is an information flow diagram and does not represent any specific technology solution.
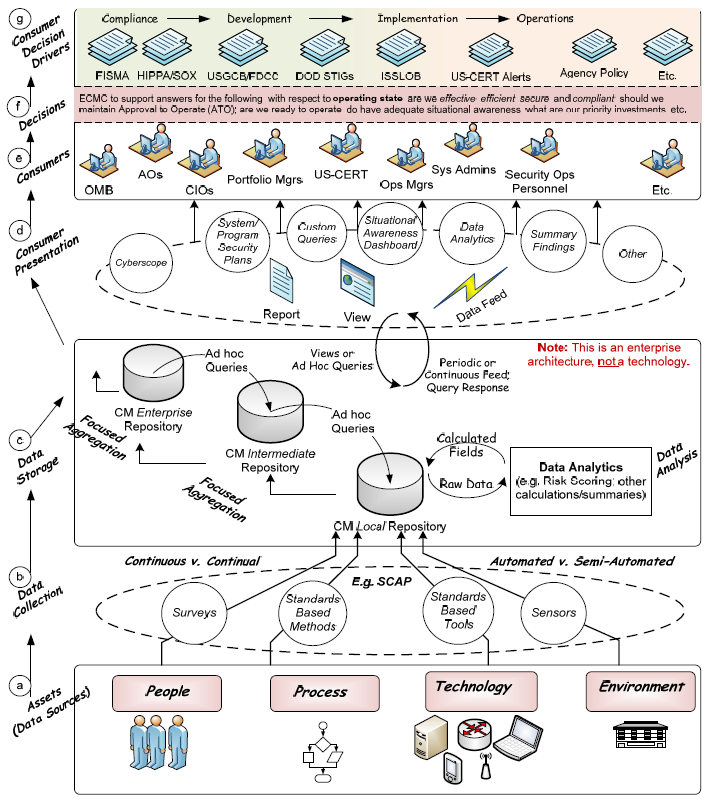
Diagram of the elements of ‘Continuous Monitoring’ in NIST IR 7756 Draft 2 Page 11
The following definition is provided: “Continuous monitoring is ongoing observance with intent to provide warning. A continuous monitoring capability is the ongoing observance and analysis of the operational states of systems to provide decision support regarding situational awareness and deviations from expectations.” As well there are eleven domains that have to be considered for situational awareness in information security; they are:
- Vulnerability Management
- Patch Management
- Event Management
- Incident Management
- Malware Detection
- Asset Management
- Configuration Management
- Network Management
- License Management
- Information Management
- Software Assurance
There can be much debate on the merit and methods of philosophies such as Situational Awareness in network security. One fundamental aspect of Situational Awareness is its dynamicity. The ability to be dynamic and respond to new and evolving threat models. This is in direct contrast with the paradigm of classic information security, which is similar to fortress and castle building and somewhat static in design.
Traditional information security can use risk management to prescribe a set of controls to achieve a security baseline. For application development Threat Modeling is an approach for analyzing and mitigating the security of an application. However, in a dynamic threat landscape a new way of thinking may be to seek dynamic threat modeling for the network as the ‘application’. To respond to the needs of the dynamic landscape of network attacks, the following characteristics are fundamental for the network to possess:
- Monitoring activated on all network hosts.
- Monitoring information written to local log files and log data shipped to a Security Information and Event Management (SIEM) system.
- The SIEM will then correlate and analyze the incoming log data for possible attack patterns.
- The SIEM should contrast and compare the incoming log data to the Common Vulnerability & Exposures (CVE) and the Common Configuration Errors (CCE) databases available from Miter and NIST, as well as threat based databases for the purposes of providing insights into any incoming attacks.
- Network hosts should be classified in an asset database that can then be used to carry out vulnerability scans and track of the results of the scans for remediation.
- Any vulnerabilities found in regards to an asset should be classifies against CVE and CCE databases and remediated in accordance to established strategies.
- Following good practice for configuration management and change control, all code patches should be tested, in a test environment, before being implemented into a production environment.
- Any vulnerable system which cannot be code patched should have extra monitoring, armoring or hardening leveraged against it.
- Incident Response Plans (IRP) should be created to deal with different classes and types of incidents, such as described NIST SP 800-61r2 ‘Computer Security Incident Handling Guide’.
- Augment network security by extending monitoring activities across people, processes and environments and not just the technology elements of the enterprise.
In conclusion, the fundamental aspects of security - whether physical security or cybersecurity - are controlling access, monitoring the environment, and being able to respond to incidents when they occur. In the new paradigm, security can be delivered by using Situational Awareness of the environment and responding to the threat level detected rather than by designing a fortress with the expectation of being able to withstand any and all attacks. Situational Awareness in Cyber Security is not any single product; it is a philosophy that has to be realized by the intelligent use of the products and processes that encompass the information systems network.
Find Robert on LinkedIn.
References: