Before I got into cybersecurity, I spent years as a technical support agent for Windows end users of Windstream, an American ISP. Although Windstream is an ISP, they also offered a general Windows client OS remote support service for their predominantly rural customers.
Many of my malware-related tickets were to fix problems caused by users who installed Trojans. A lot of Windows Trojans present themselves as useful utilities such as drefragmentation tools, registry fixers, and ironically, antivirus software.
The Windows registry has been a component of every client version of Windows from 3.1 to 10. It's how the platform organizes low level configuration settings, and the settings of many first and third party Windows applications. I think of Windows registry keys as the rough equivalent of .conf files in Linux and UNIX based OSes, but with a set hierarchy.
The Windows Registry editor can be launched in Windows by executing “regedit” from the Run menu. The program is hidden from the GUI, perhaps as a way of preventing users who may not know what they're doing from making changes that might break their operating system.
Whether or not Windows registry fixing utilities are actually useful is a controversial topic.
According to Malwarebytes Labs, Registry cleaners are “digital snake oil.” They believe that making changes to the registry with those utilities at best make improvements that are so subtle that they're barely perceivable, and at worst do harm that can be significant enough to require a complete reinstallation of Windows. If users believe that their Windows performance is improved after running a utility, it's a placebo effect.
BleepingComputer.com says there's no statistical evidence of the performance improvement claims of registry utility vendors. Each vendor has different criteria for what constitutes a “bad entry.” Some utilities don't make a backup of the registry before making changes to it, so if something bad is done it cannot be easily reversed. Removing registry entries can make malware removal more difficult, and the usefulness of making changes to the Registry is overrated and can be dangerous.
Microsoft Support's official statement on third party registry utilities is that they don't recommend their use. They aren't liable for problems caused by those applications, but if one is used, they recommend backing up the registry first.
There are a lot of third-party applications that advertise themselves as registry fixing utilities that can be downloaded from the internet. They cannot all be malware, but I suspect that some of them are. I decided to do a little experiment of my own, to see if any popular registry utilities might threaten the security of Windows PCs.
Experiment Methodology
I installed a virtual machine of Windows 10 Pro with Oracle VirtualBox under Kubuntu Linux. I gave my VM a 32GB virtual disk, and 2GB of RAM. I used all of the default settings during the installation process.
I used the default Express settings during the Windows 10 installation process.
I made a System Restore point as soon as the installation was finished. That way, I can try to revert to the equivalent of a clean install of Windows 10 after I tested each application. Installing a new Windows 10 VM for each of the six applications I was testing would be tedious!
I found each of the six applications on the web. For each application, I installed it with its Installation Wizard, and then I ran its Registry fixing function. Afterwards, I made a copy of the HKEY-LOCAL-MACHINE hive for later testing in RegRipper. As the entire registry is huge, I decided to focus on just that hive, as it's the most likely to change with installing local applications. Even that component was nearly 200MB!
Then, after installing each application, I ran a Malwarebytes antivirus scan of the C drive with updated signatures. Their scan now includes a heuristics analysis too, which I really like. I then saved a log, and chose to quarantine and remove any malware the scan found, including Potentially Unwanted Programs (PUPs). PUPs are executables that may be malicious - subject to interpretation. Saying safe files get a “green light”, and definite malware gets a “red light”, PUPs get a “yellow light”.
With .reg files and malware scan logs from each of the six applications, I booted up Kali Linux.
I viewed the Malwarebytes logs in a text editor, and I analyzed the .reg files with RegRipper and its Security plugin.
CCleaner
 CCleaner is a very popular Windows application that's developed by Piriform. Its most well-known feature is its main Cleaner function. It clears the caches of many applications, including specific web browsers and the file manager.
CCleaner is a very popular Windows application that's developed by Piriform. Its most well-known feature is its main Cleaner function. It clears the caches of many applications, including specific web browsers and the file manager.
A registry cleaning function has been added to more recent versions of CCleaner. For this experiment, I ignored the Cleaner function, and went straight to Registry functionality.
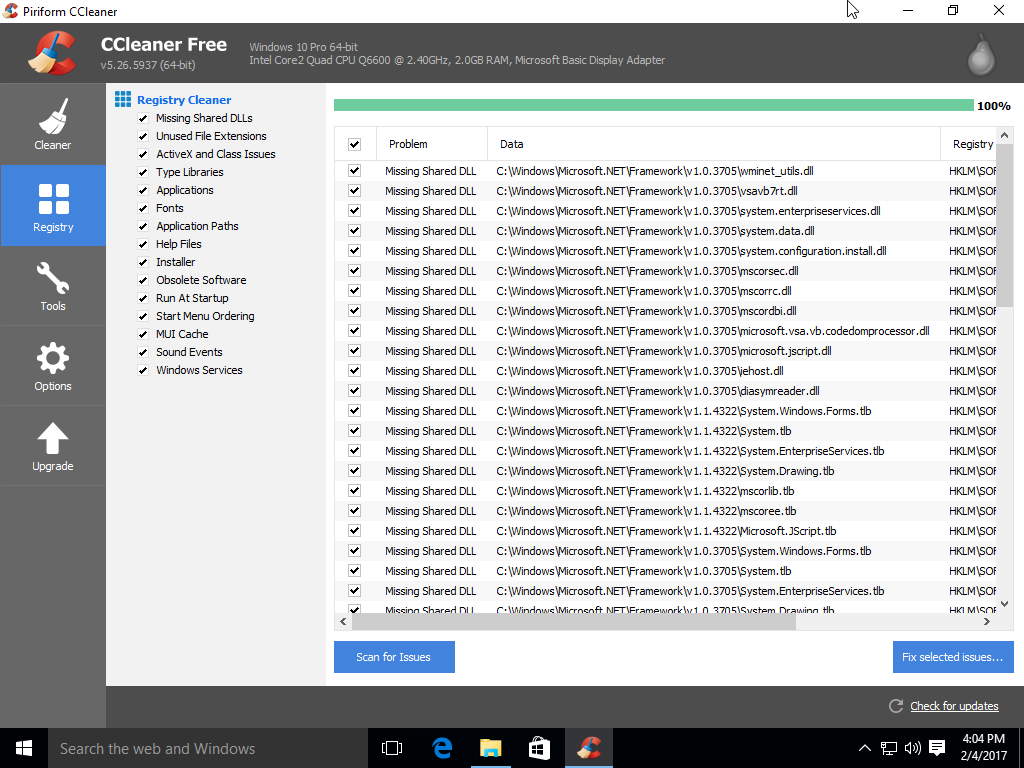 All of the errors found were missing shared DLL entries. I removed all of them.
All of the errors found were missing shared DLL entries. I removed all of them.
My Malwarebytes scan didn't identify CCleaner or any of its associated files as malicious or as a PUP.
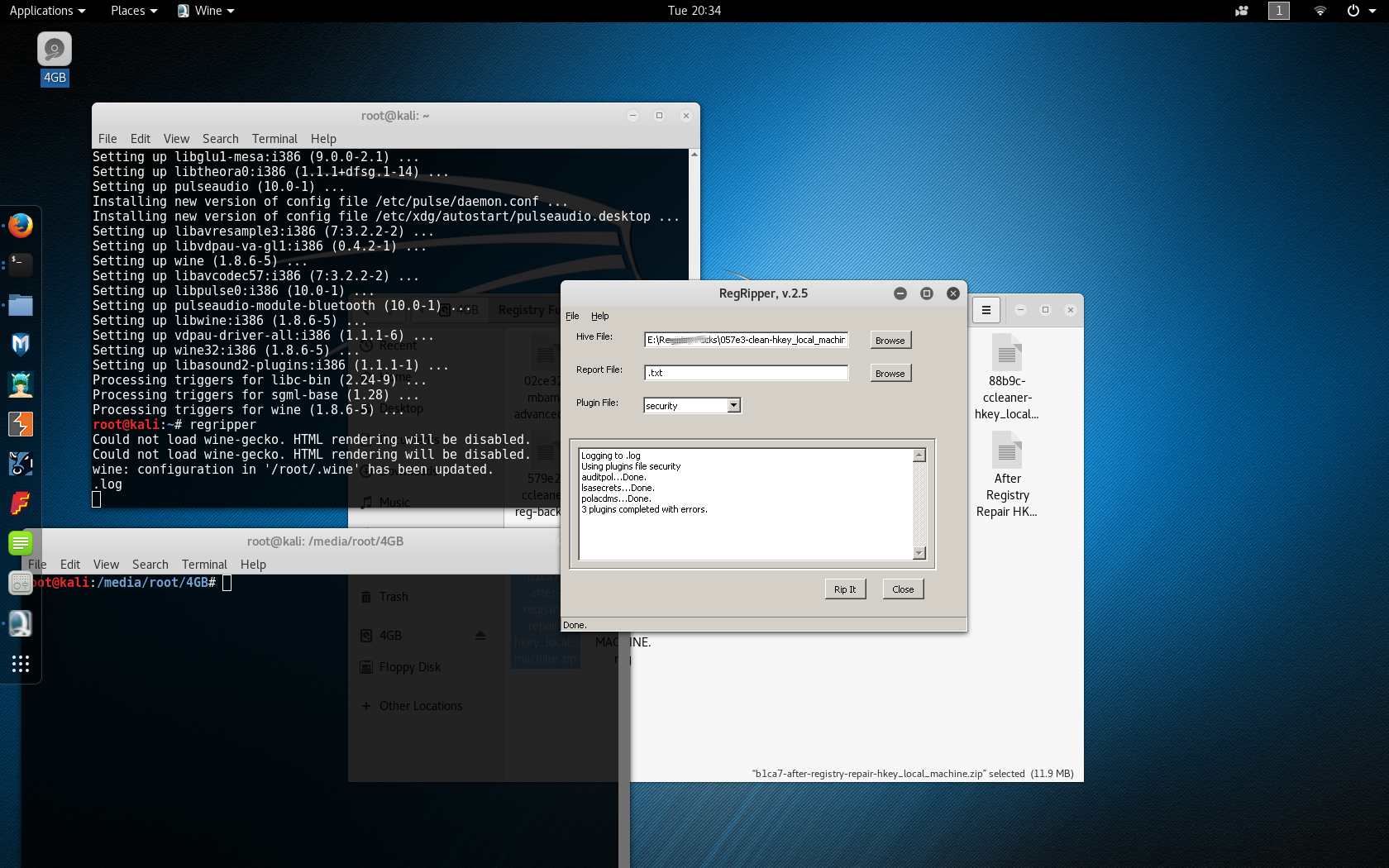 Later on, I ran RegRipper on HKEY-LOCAL-MACHINE from after running CCleaner's registry fixer. I used the Security plugin, which has three components- auditpol, lsasecrets, and polacdms.
Later on, I ran RegRipper on HKEY-LOCAL-MACHINE from after running CCleaner's registry fixer. I used the Security plugin, which has three components- auditpol, lsasecrets, and polacdms.
Auditpol just checks the audit policy from the Security hive. No changes were made. Lsasecrets looks for passwords and keys, including those related to VPNs and autologon. Again, no changes from a clean install of Windows 10. Polacdms extracts and parses the unique Security Identifier (SID) of a user or security principal in Windows. Access control lists are used to determine a user's file, folder, and group permissions. A unique SID makes sure that a security access measure applies to a specific user. Nothing malicious was found with that plugin, either.
Conclusion: CCleaner is “clean” on maliciousness directed toward registry.
Registry Repair
Next tool I tested was Registry Repair. Its GUI suggests that it scans a bunch of components under My Computer, including fonts, adware and spyware, and file associations.
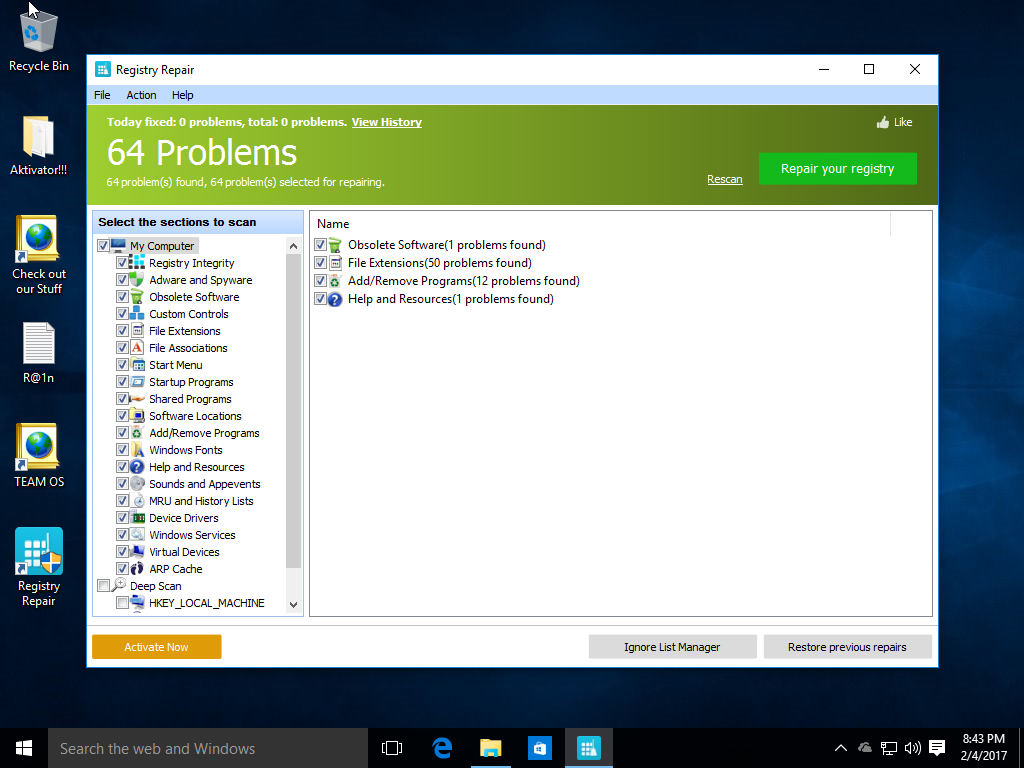 64 problems were found on a clean install, which made me a bit suspicious. No fixes for those 64 apparent problems or “Deep Scans” of specific hives are available without paying for the program.
64 problems were found on a clean install, which made me a bit suspicious. No fixes for those 64 apparent problems or “Deep Scans” of specific hives are available without paying for the program.
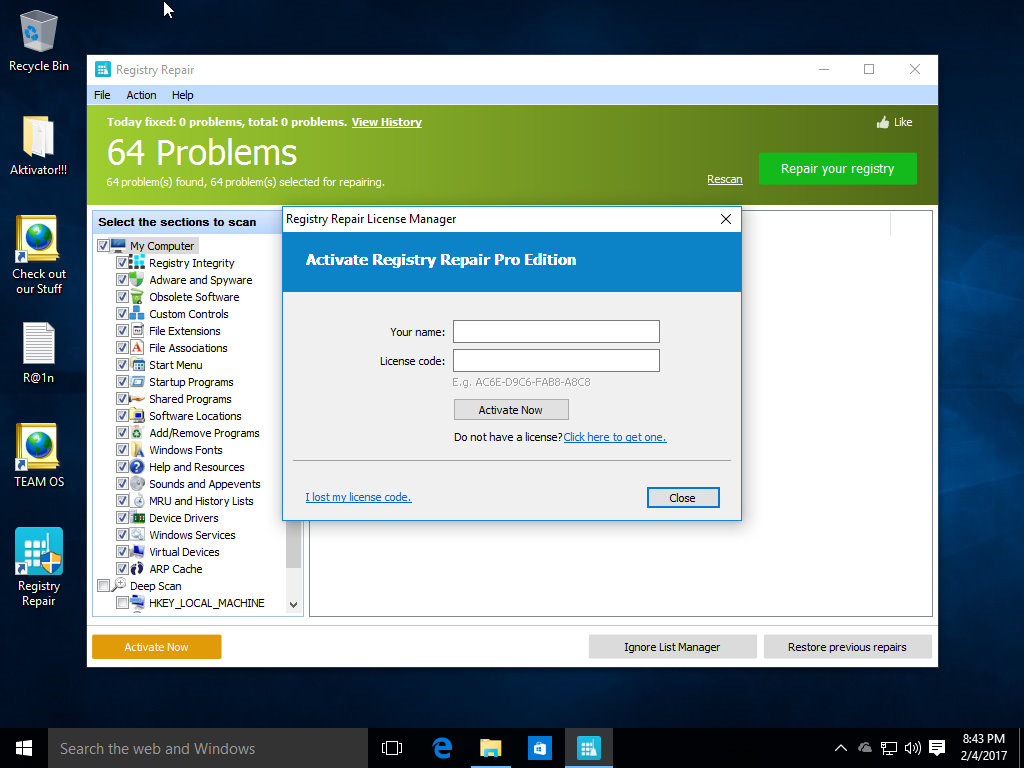 I didn't enter an activation key, so apparently nothing was done.
I didn't enter an activation key, so apparently nothing was done.
Malwarebytes didn't find Registry Repair to be malicious, and RegRipper's security plugin found nothing of interest in HKEY-LOCAL-MACHINE.
Conclusion: Meh, Registry Repair didn’t seem to do anything terrible.
System Mechanic
System Mechanic's scan took a long time on a clean Windows 10 install. It was so boring!
Anyway, it said that the System Status was apparently “GOOD,” but it found 224 supposed issues. Those included 221 junk files, one registry issue, and defragmentation was apparently overdue on a brand new NTFS format and Windows 10 install. Oh really?
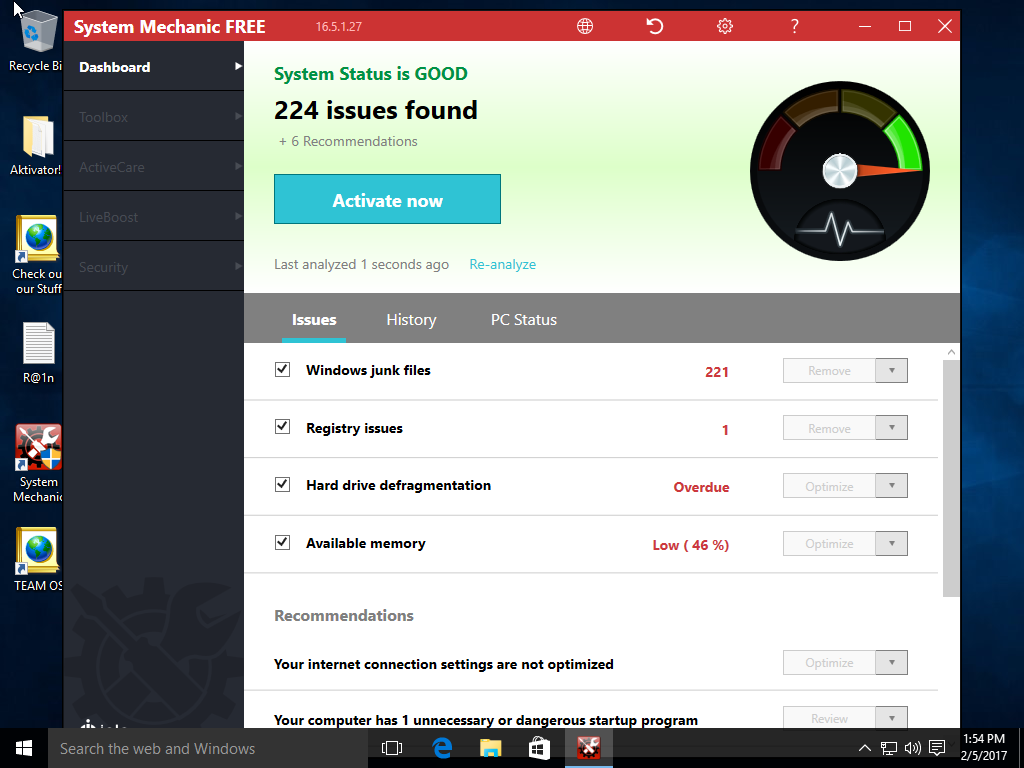 Like Registry Repair, System Mechanic will do nothing without a paid activation. Also like Registry Repair, Malwarebytes found nothing of importance, and nor did RegRipper.
Like Registry Repair, System Mechanic will do nothing without a paid activation. Also like Registry Repair, Malwarebytes found nothing of importance, and nor did RegRipper.
Conclusion: Meh, System Mechanic wasn’t found to do anything malicious.
Advanced SystemCare
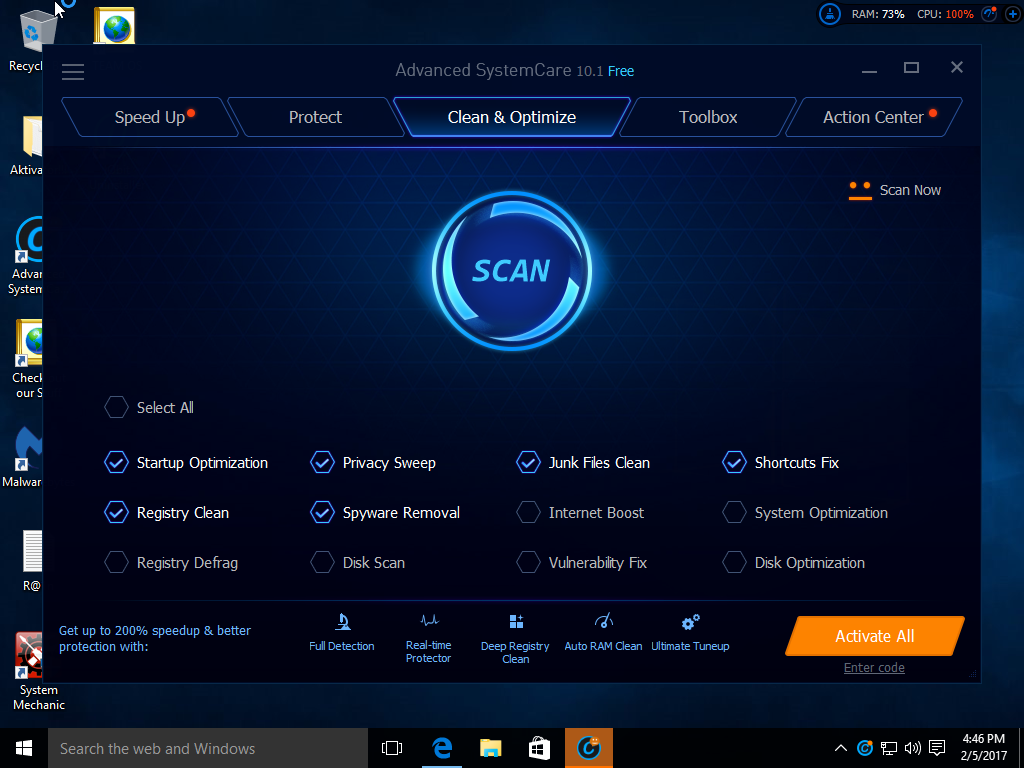 Advanced SystemCare had the most complex GUI and feature set of any of the six applications I tested.
Advanced SystemCare had the most complex GUI and feature set of any of the six applications I tested.
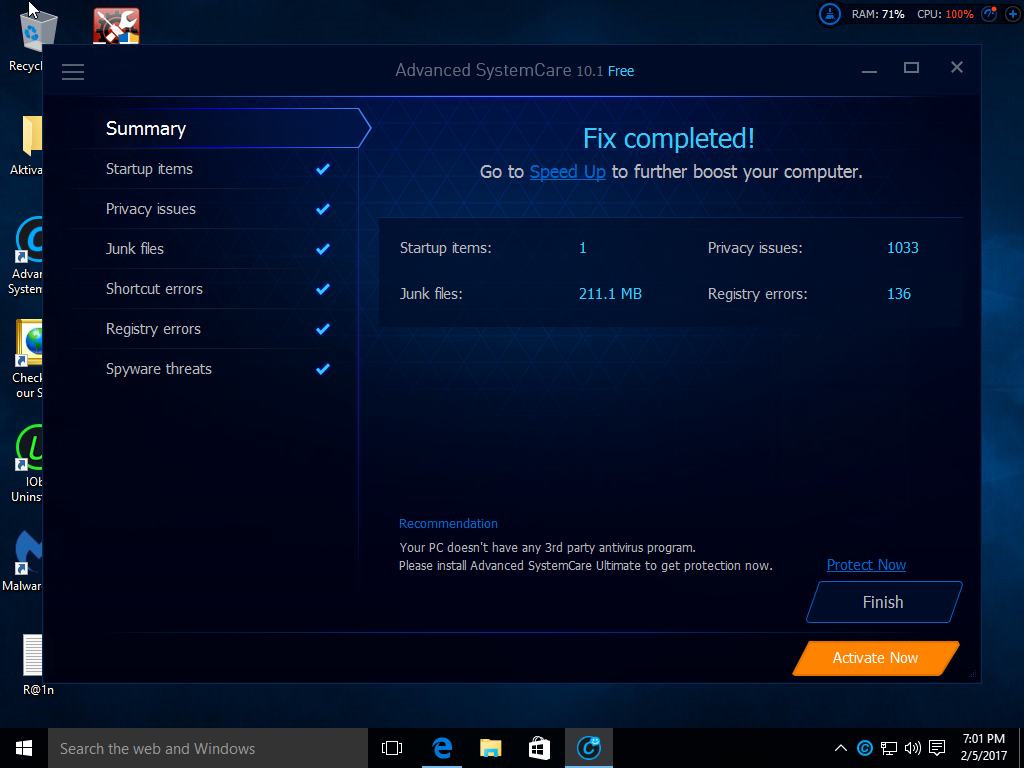 Like System Mechanic and Registry Repair, it seemed to find a lot of problems which probably aren't even real issues. It also would make no changes without activation.
Like System Mechanic and Registry Repair, it seemed to find a lot of problems which probably aren't even real issues. It also would make no changes without activation.
Malwarebytes nor my RegRipper analysis found any concerns with Advanced SystemCare.
Conclusion: Meh, no evidence Advanced SystemCare made malicious changes.
Advance System Care
No, I've made no typo. The fourth application I tested was Advanced SystemCare, and the fifth was Advance System Care. Suspicious? You should be.
I found it from Softonic's website. Everything about that website and Advance System Care screams Trojan to me.
The GUI and the installer wanted to remind me that it uses Microsoft technologies, implying a Microsoft endorsement that doesn't exist.
Of course it found 29 issues on a clean Windows 10 install.
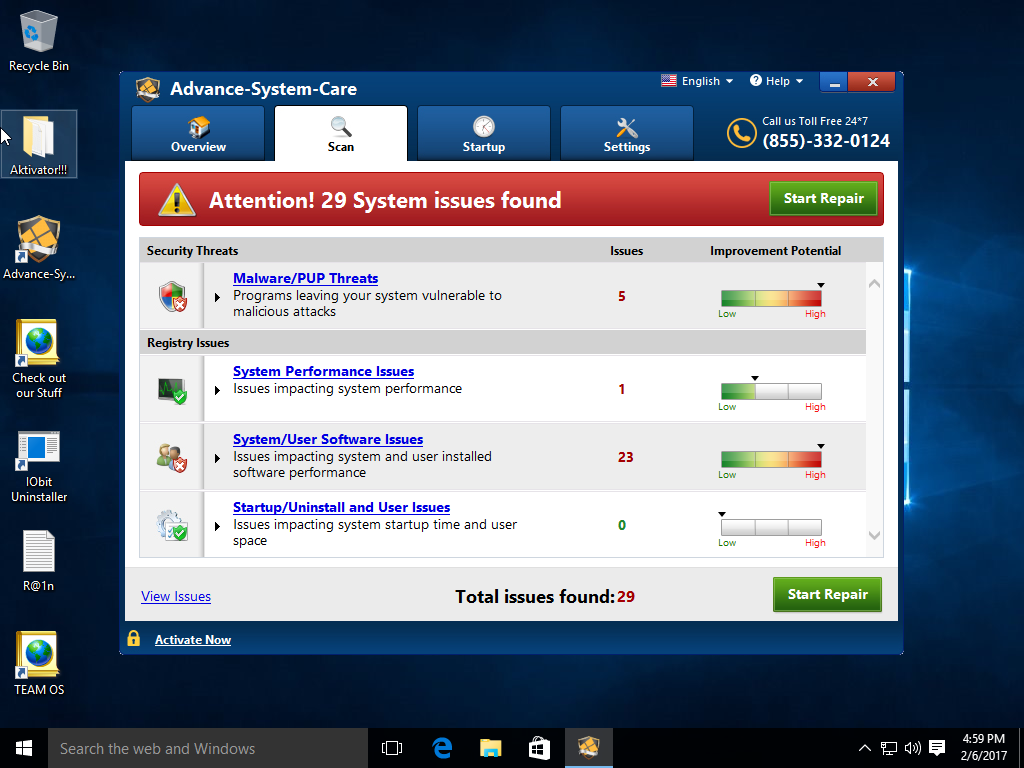 I really didn't want to call the advertised toll free number.
I really didn't want to call the advertised toll free number.
The program insists that you pay for an activation before it does anything.
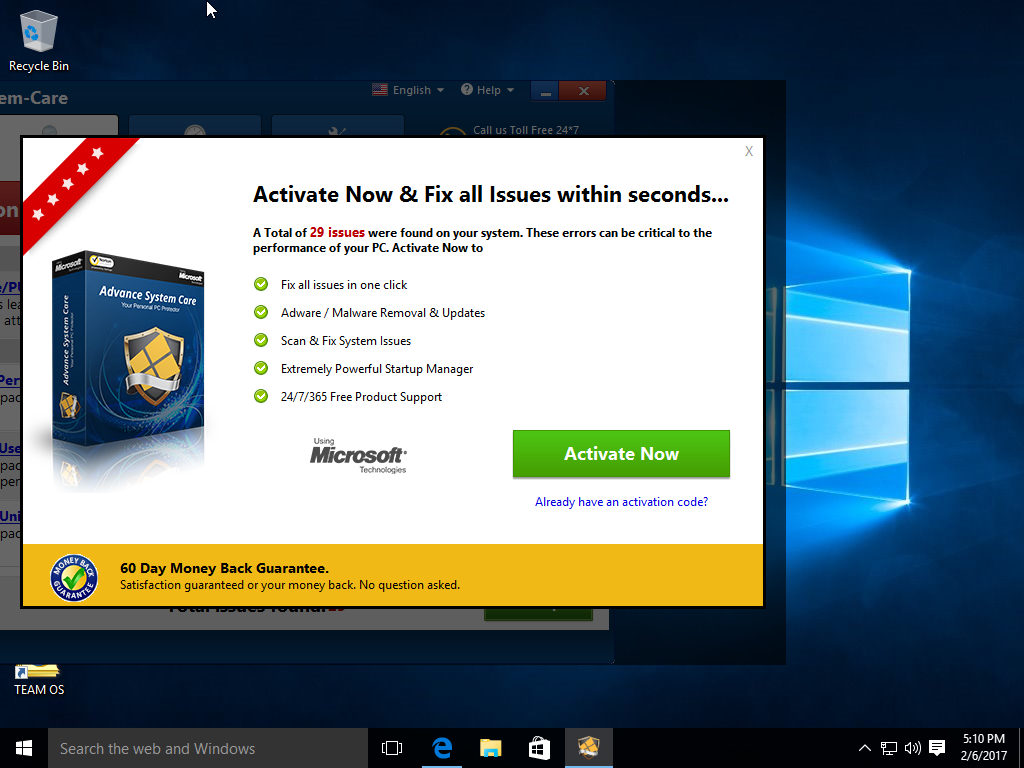 My RegRipper analysis turned up nothing. But MalwareBytes identified Advance System Care as a PUP.
My RegRipper analysis turned up nothing. But MalwareBytes identified Advance System Care as a PUP.
Conclusion
CCleaner was the least suspicious of the applications I tested. Its cache cleaning is actually a great feature. Whether or not removing missing DLL registry entries was useful is subject to debate. But there was nothing alarmist about CCleaner's GUI, and a lot of functionality is provided in its free version.
I feel the same way about Registry Repair, System Mechanic, and Advanced SystemCare. I wouldn't classify any of them as malware. But I don't think they do any good either. They try to scare you into paying for activations, but you don't need them.
Advance System Care is an obvious Trojan. Don't touch it or Softonic with a ten foot pole.
And remember, Microsoft, Malwarebytes, and BleepingComputer.com don't recommend registry cleaners.