I listened in on a neat webcast recently, which was jointly produced by AT&T Cybersecurity and Palo Alto Networks: “Preparing for Zero Trust and Planning your Strategy.” Panelists were John Kindervag, Field CTO, Palo Alto Networks, Steve Sekiguchi, Director, AT&T Chief Security Office, Bindu Sundaresan, Director, AT&T Cybersecurity and Tawnya Lancaster, Lead Product Marketing, AT&T Cybersecurity. You can catch the hour long webcast recording here.
The webcast focuses on five key areas, and it’s currently available on demand:
- Who to put on your Zero Trust team to help work toward success
- What essential factors must be considered ahead of time
- Where to start when assessing your organization’s readiness for Zero Trust
- Why Zero Trust strategy and planning must happen from the inside out
- How to avoid common pitfalls when starting (or continuing) your progression to ZT targets”
Here are some of the key nuggets I enjoyed from the webcast.
John Kindervag gave a great overview of Zero Trust from his experience over the past 12 years, making a point that Zero Trust is NOT a product, but rather a strategic framework. He also pointed out that Zero Trust is meant to be a straightforward framework that can be broken down to four key design concepts:
- Focus on business outcomes
- Design from the inside out
- Determine who/what needs access (we give too much access to employees who don’t need it)
- Inspect and log all traffic
We in cybersecurity are familiar with the idea of the “attack surface,” and for years cybersecurity professionals have been focused on the macro vision of protecting that attack surface. Zero Trust turns this concept on its head, advocating for security being brought closer to the workload. John suggests organizations should be breaking down the macro attack surface into what he calls the “protect surface,” which is made up of at least one of the following elements: data, applications, assets, or service (DAAS). Organizations should be designing their security architecture to highly secure individual protect surfaces. This accomplishes many things, including limiting the ability of threat actors to move laterally within your network and limiting the blast zone should a breach happen. Zero Trust protections are essentially layer 7 policy, with a single policy for each DAAS element.
- Data – credit card info, personal info, intellectual property, etc.
- Apps – CRM, HR, ERP, etc.
- Assets – IT, IoT, etc.
- Services – DNS, DHCP, AD, NTP
AT&T CSO Director, Steve Sekiguchi, agrees with the importance of establishing highly secure zones through the use of microsegmentation technologies, which include microperimeters or software-defined perimeters (SDPs) that can isolate devices and applications closer to the workload/service being protected. He also suggests there are many other tools for microsegmentation, including next–generation firewalls (NGFWs), network overlays, software–defined network (SDN) integration, host–based agents, virtual appliances, containers, security groups, and more.
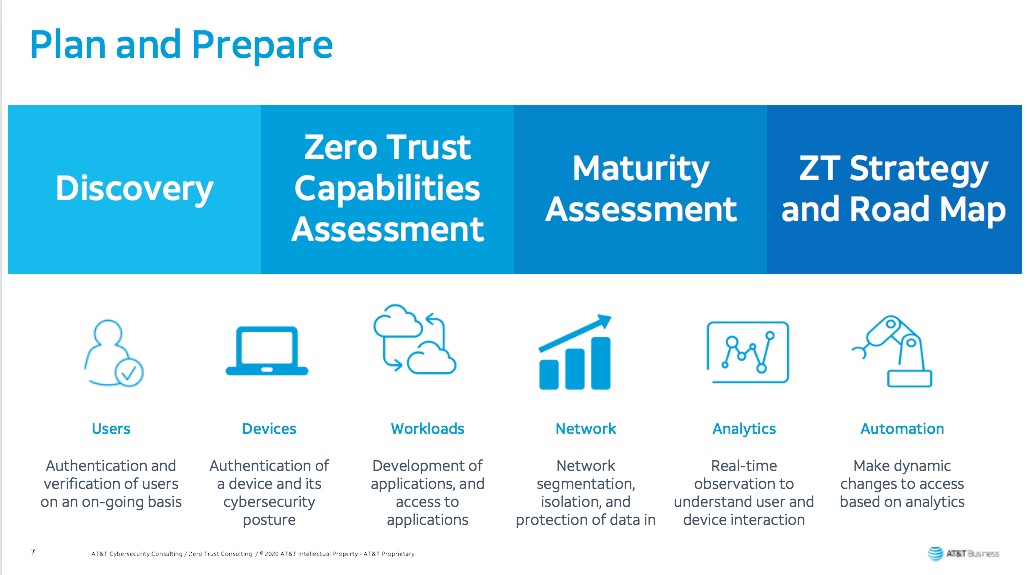
As with any approach to security, Zero Trust is a journey, and Bindu Sunderesan suggests organizations should consider deploying Zero Trust in phases. Phase 1 begins with identifying the business criticality for Zero Trust and understanding your current security posture. This is especially true for organizations who are considering Zero Trust in the wake of COVID, which most likely drove extensive changes to IT infrastructure. AT&T Cybersecurity Services offers several services designed to assist organizations in their preparation and planning, including a Zero Trust Readiness Assessment and Strategy and Road Map offering.
It’s worth noting that AT&T Cybersecurity offers a free online Security Maturity Assessment tool, which organizations can use to benchmark their security program against their peers and gauge their organization’s current security posture. The assessment is based on a benchmark survey of 500 security professionals to identify what a “mature” cybersecurity program looks like and how that impacts an organization’s ability to mitigate risks. Based on your results, you'll receive an assessment showing your organization’s security gaps and strengths, as well as how your security program compares to your peers. Interestingly, as pointed out by AT&T’s Tawnya Lancaster who directed the research, data from the study shows that an organization’s maturity in cybersecurity doesn’t directly correspond to size. “I personally was very surprised to see this data point,” she explained, “as I would have thought that a larger business with bigger budgets and more resources would inherently be more mature, but that’s just not what the data showed. This perhaps suggests that being further along the maturity curve is more about how security is infused in the culture of the organization than dollars spent.”

Zero trust network assessment
Zero Trust Readiness Assessment is designed for customers who need to evaluate their current state information security program and its maturity in attaining Zero Trust.
Learn moreAccording to the panel, even small companies can implement Zero Trust quite successfully, especially with the adoption of cloud and virtualized security controls. It’s a matter of undertaking the journey as a business imperative, working with an experienced third party who can help guide the organization in planning, strategy and execution, and taking baby steps — Zero Trust in not something that has to be done all at one. As John suggests: start with less sensitive / critical areas of the protect surface to learn and practices Zero Trust before rolling out to the “crown jewels.”
It is a very educational webcast and well worth the hour to have a listen. And of course the moderator of the webcast was my colleague, Susan Stogner, who works in Demand Generation for AT&T Cybersecurity.
If you prefer to read rather than watch, here’s a whitepaper on topic: Tightly Control and Manage Access to Applications and Services with Zero Trust.