Introduction to Ransomware
The recent wave of ransomware attacks on healthcare institutions is not only raising questions about contingency planning, but also about whether healthcare is becoming the “go-to” target for cyber extortionists looking to make quick money.
Just last week alone, there were three new ransomware attacks on mid-size hospitals and - according to the Department of Health and Human Services’ breach database - 13 such attacks in the past month alone. While not all of these DHSS breaches necessarily involved ransomware, these stats indicate the poor state of security as a whole in the healthcare industry.
However, while the use of ransomware by cyber extortionists has been increasing, if you understand the threat and take certain precautions, then a major compromise of your organization is not inevitable.
Ransomware, Step-by-Step
Before looking at specific ransomware cases and how to defeat them, it’s important to understand why ransomware is so successful. Ransomware is a form of malware which encrypts sensitive files on a target system, effectively holding them hostage until the ransom is paid. While delivery methods are expanding, ransomware typically utilizes social engineering as the primary means of attack, disguising malicious emails as business-related correspondence. Many such emails use malicious Word or PDF attachments, which often bypass typical AV scanners and appear legitimate, to target users. Once executed, the malicious payload runs in the background and within seconds, the targeted files are encrypted and the private key sent back to the attacker’s server.
Soon a ‘helpful’ message will appear to walk the new victim through the Bitcoin payment process required to decrypt the files.
What Makes Healthcare Such A Target?
Healthcare firms struggle with many of the same security problems faced by other traditional industries. In an industry where better technology doesn’t necessarily result in higher revenue – or better patient care – investing in technology is a low priority. This lack of investment in technology often results in servers going unpatched, outdated technologies being used, and other security vulnerabilities remaining unresolved. Healthcare databases also typically contain a treasure-trove of patient information that is very valuable to attackers.
This combination of high-value data and low-security protections makes the entire industry ripe for exploitation.
PowerWare
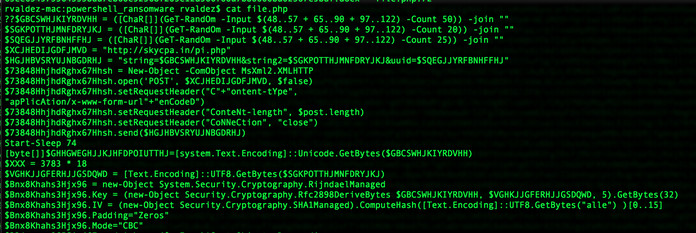
While there are a number of ransomware families to touch on here, PowerWare is a new addition which is generating buzz from its recent ‘fileless’ infection mechanism. This malware was most-recently implicated by security researchers in the compromise of another healthcare institution just last week.
Although the name of the hospital is unknown, the attack narrative is similar to other ransomware cases. Targeted phishing emails were sent to a set of users, requesting them to download a malicious Word document and enable macros – a dangerous feature which is disabled by default.
However, once enabled, rather than downloading a malicious file to perform the encryption routine, PowerWare takes another route – it uses functionality within Windows itself to accomplish its task. Also known as a ‘fileless’ attack, this malware never writes a file to disk (which would potentially allow it to be detected by antivirus and other security tools), relying on PowerShell to execute the dirty work instead.
As with other ransomware, once PowerWare executes on the targets computer, a message is presented notifying the victim to pay up to obtain the private key or lose access to their data. At least for now, the ransom starts at $500, but this amount increases to $1,000 two weeks after infection.
Defense In Depth: Detection
Every security model revolves around prevention, detection, and response – and handling ransomware is no exception. Traditional security implementations, such as AV and firewalls, are common basics but these are easily circumvented when social engineering and technical expertise are used to target unsuspecting users. Also, when malware is embedded in macros, uses PowerShell to hide its malicious commands, or is encrypted to evade antivirus, additional protections must be used.
With AlienVault USM, attacks can be mitigated through a range of tools and capabilities.
- Host-based intrusion detection (HIDS) agents deployed to each endpoint on your network identify suspicious behaviors, preventing attacks before they begin. This host-based service can negate ransomware threats as soon as they reach your workstations by shutting down encryption processes before they can cause damage. Backed by decades of research and threat intelligence, you can trust that each endpoint is protected from even emerging security threats.
- File Integrity Monitoring (FIM) similarly alerts you to changes in critical system files, configuration files, and content files, ensuring that no unauthorized changes, including the encrypting of sensitive data, occur. With FIM built into each HIDS agent, USM is able to keep a close watch on your most critical assets and systems to detect when ransomware may be present on the network.
Managed Security Options: Cyber Threat Mitigation
While AlienVault USM is an excellent platform for protecting and monitoring your environment, tools are only useful so long as they’re properly used. Many times the security problems are not due to technologies, but process and personnel, making it difficult to sustain long-term safety. Managed security service providers (MSSPs) can provide the technology, personnel, and processes needed for your business to stay HIPAA compliant and free of malware.
Rhino Security Labs, an AlienVault MSSP partner, utilizes USM to protect and monitor the security environment of dozens of healthcare organizations. Its MSSP service, Cyber Threat Mitigation, uses experienced SOC analysts to monitor and investigate intrusions, quickly remediating abnormal events on networks.
Conclusion
Ransomware is impacting more and more healthcare organizations, and such attacks are raising questions about the future of security in the industry. While limited budgets and passive attitudes have been the norm up to now, sophisticated cyberattackers are beginning to take advantage of healthcare’s unacceptably lax security practices.
Don’t be forced to pay cyber extortionists. Get ahead of attackers, and prevent ransomware with in-depth defense. If you’re interested in preventing ransomware attacks, contact Rhino Security Labs about managed security and a free trial of Cyber Threat Mitigation.
About the Author
Benjamin Caudill is the Founder and Principal Consultant of Rhino Security Labs, a penetration testing and managed security firm headquartered in Seattle, WA. As a security professional, Benjamin has seen a wide range of security environments, with clients ranging from mobile startups to government agencies and Fortune 500’s. He’s been published in Wired Magazine, CNN, Forbes and presented at security conferences such as Defcon.