The threat landscape is constantly evolving and it is even more of a challenge for organizations, especially those in the mid-market, to detect where the true threats lie without tapping into a broader and often already stretched IT Budget. To help solve this problem, AlienVault developed a free platform called Open Threat Exchange (OTX) to help organizations gain greater visibility into their networks and make existing IT resources more effective in rapidly detecting and responding to threats.
Since its creation in 2012, OTX has grown to now support more than 26,000 participants in over 140 countries contributing more than 1 million threat indicators daily, AlienVault has moved to develop the updated version of OTX on a foundation of a social networking architecture.
The world has changed since OTX’s creation. Adversaries are getting more and more sophisticated and they have access to a wide range of tools. A vibrant community for sharing and selling exploits, malware, and other components of attack infrastructure has created a new generation of social and sophisticated hackers.
To confront this challenge, we have worked to deliver a new evolution of Open Threat Exchange designed to empower defenders with the ability to investigate and respond to this new generation of threats.
Social Sharing “Ups” OTX value
The updated version of OTX, which is generally available for free today is modeled on social sharing and enables security practitioners from around the world to openly research and produce community-powered threat data.
The first version of OTX was based on an API and was mainly designed to Exchange data from machine to machine. In contrast, the new version of OTX is a web portal where users can create “pulses.”A pulse is a group of Indicators of Compromise (IoC’s) that can describe an actor, threat campaign or any activity that can help users to protect themselves against a particular adversary. Users can interact with the community and perform the following actions:
- Create + Share Pulses: Users who observe suspicious or malicious activity can create a pulse or add additional details to an existing pulse. Participants can up-vote and comment on individual pulses to help others identify useful IoC’s.
Also, we offer the capability to extract potential IoC’s from websites, PDF’s, text or import OpenIOC and STIX files. Our engine will help you to identify potential false positives and choose the right IoC’s from raw content.
- Subscribe + Follow Pulses: Users can automatically instrument their security defenses based on OTX pulses produced by specific users or Pulses relating to specific threats, saving time and ensuring their security controls are up to date against the threats they care most about.
-
Export + Integrate Pulses: With the new AlienVault DirectConnect API, users can automatically download IoC’s from OTX and integrate them into their existing security infrastructure using open standards such as CSV, STIX, and OpenIoC. For AlienVault customers, data from OTX is automatically instrumented into the AlienVault Unified Security Management (USM) platform.
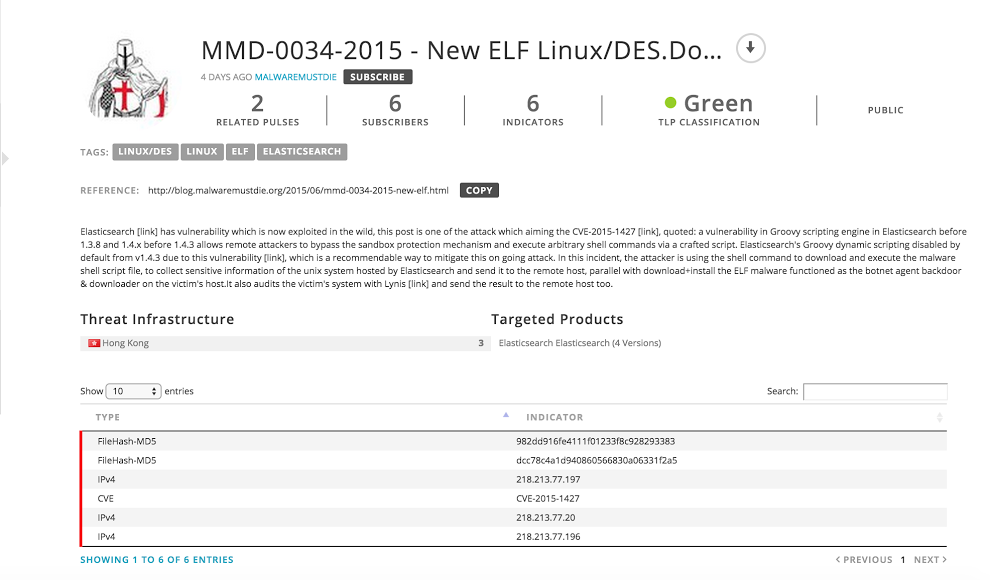
Another important feature is being able to explore and investigate individual IoC’s or those part of a pulse. For example, if you are investigating an IP address or a domain name, the OTX system will provide all the information we have about it, including related URL’s, Passive DNS data, IP Reputation data and malware samples that are known to communicate with that IP address or domain. If you are interested in specific files that our systems have analyzed, we will expose the static and dynamic analysis as well - even including network and host behavior (powered by cuckoo).
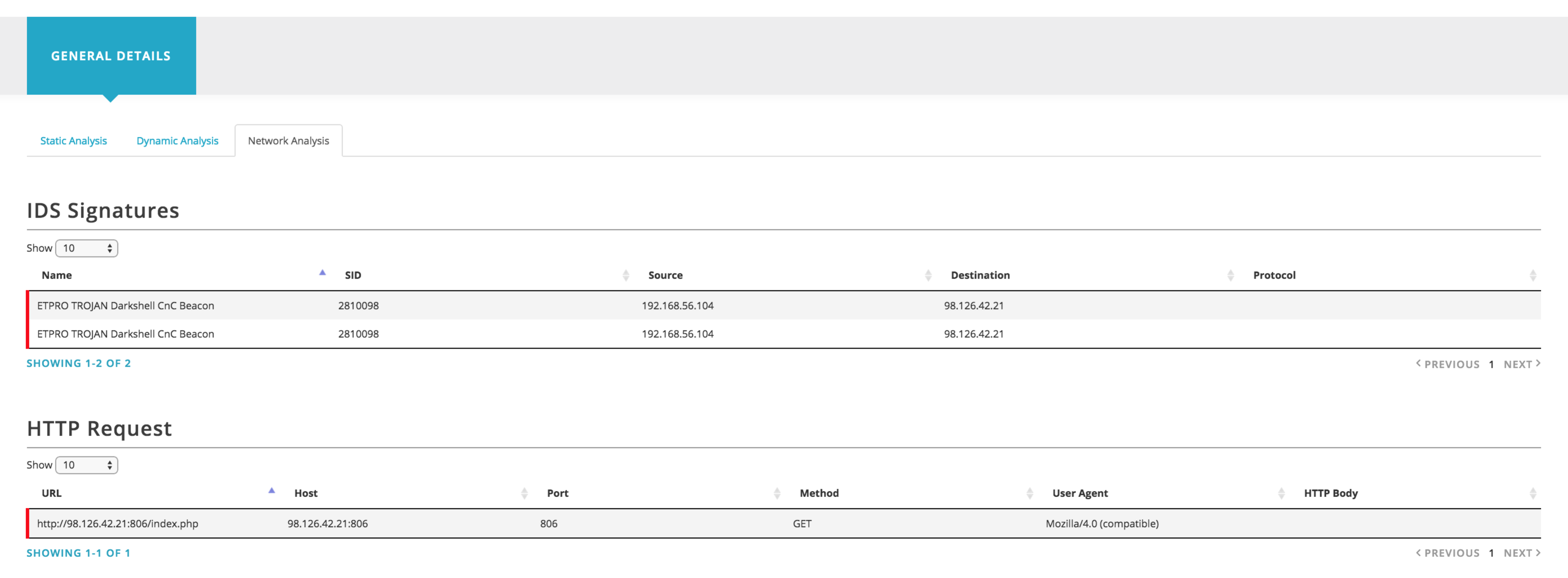
Open ways to integrate with OTX
We are also releasing two client libraries for Python and Java that developers can use to integrate other tools with the OTX data:
https://github.com/AlienVault-Labs/OTX-Java-SDK
https://github.com/AlienVault-Labs/OTX-Python-SDK
For a walk-through on how to use the Python API, you can take a look at the following notebook:
https://github.com/AlienVault-Labs/OTX-Python-SDK/blob/master/howto_use_python_otx_api.ipynb
As a demonstration, we are releasing on applications that you can use to connect OTX with your security tools.
- Connector for BRO IDS
https://github.com/AlienVault-Labs/OTX-Apps-Bro-IDS
https://alienvault.atlassian.net/wiki/display/PUL/BRO-IDS
Stay tuned for new connectors that we will be releasing during the next few weeks including a TAXII client to send the OTX data to your TAXII server where you can integrate the data with other security tools.
How this works with USM and OSSIM
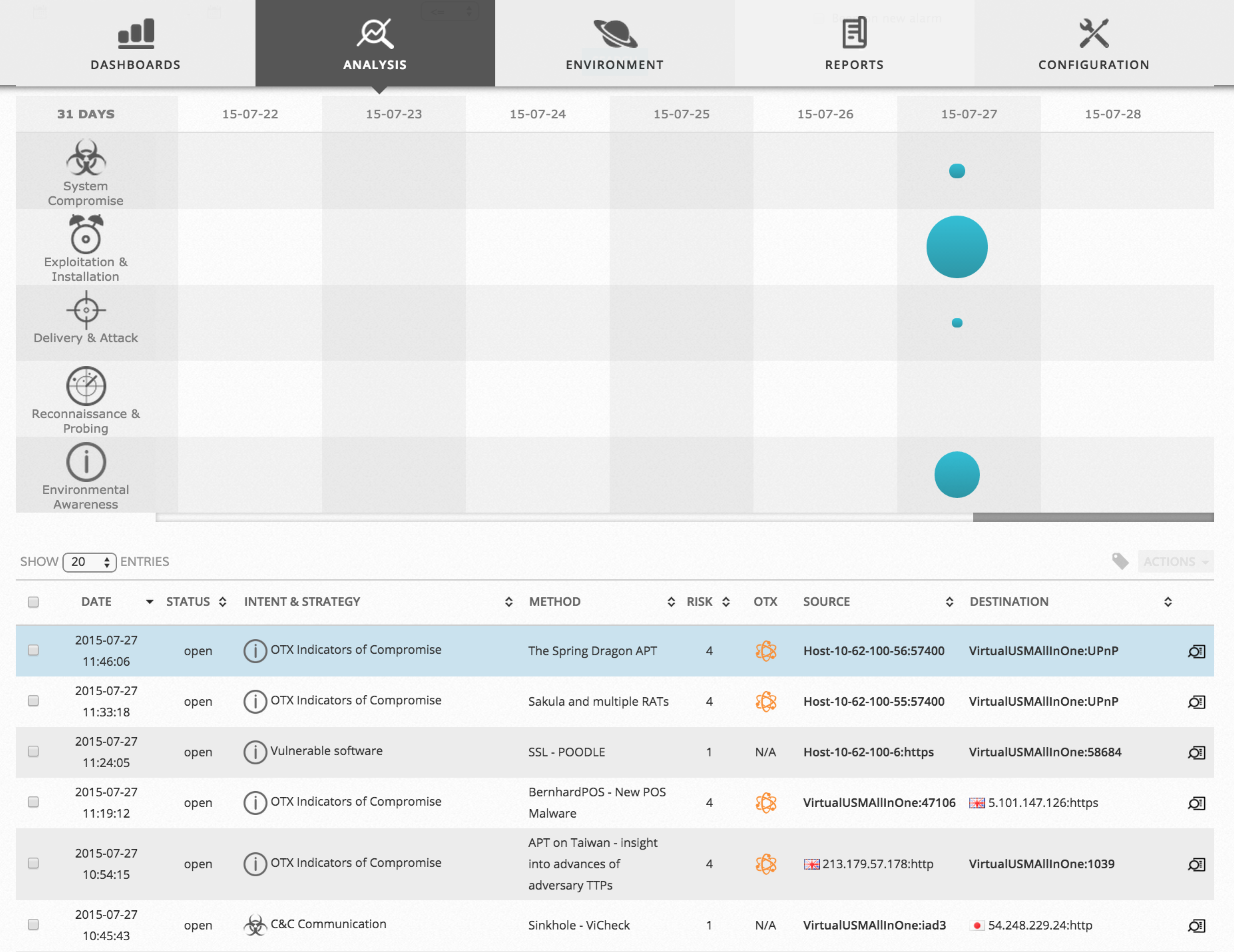
Along with OTX, today we are releasing a new version of USM v. 5.1 that integrates OTX’s threat indicators automatically into USM. OSSIM will work the same way.
When you associate your OTX API key with USM, it will automatically download IoC’s from the pulses you are subscribed to, and it will start generating alarms when a specific IoC is detected in your network.
What’s Next for OTX?
We are currently working on exciting new features that we will release over the course of the year. Following are a few things we are working on:
- Trust groups and sharing communities
- More ways to assist on the creation of a Pulse (extracting IoC’s from suspicious mails, PCAP files, etc)
- ThreatGraph: Visual graph to pivot and discover new IoC’s.
- Support for more indicators (Yara, etc)
- TAXII server