This article was written by an independent guest author.
If you follow cybersecurity current events, you may know that the cost and frequency of a data breach continue to skyrocket. Organizations are constantly under attack, and the shift to remote work is only exacerbating the problem.
According to IBM’s 2020 Cost of a Data Breach Report, most respondents are concerned that identifying, containing, and paying for a data breach is more burdensome today than ever before. Seventy-one percent feel that remote work will increase the time to identify and contain a breach, while almost the same number believe remote work increases the cost of a breach.
The numbers agree: remote work has added $137,000 to the average breach cost.
In 2021 and beyond, reactive security measures—typically cumbersome and costly—are no longer sufficient. Instead, proactive strategies that anticipate potential risks or vulnerabilities and prevent them before they even happen are required.
One such strategy, network segmentation, is critical for any organization. If you’re not deploying network segmentation, it’s time to get started.
What is network segmentation?
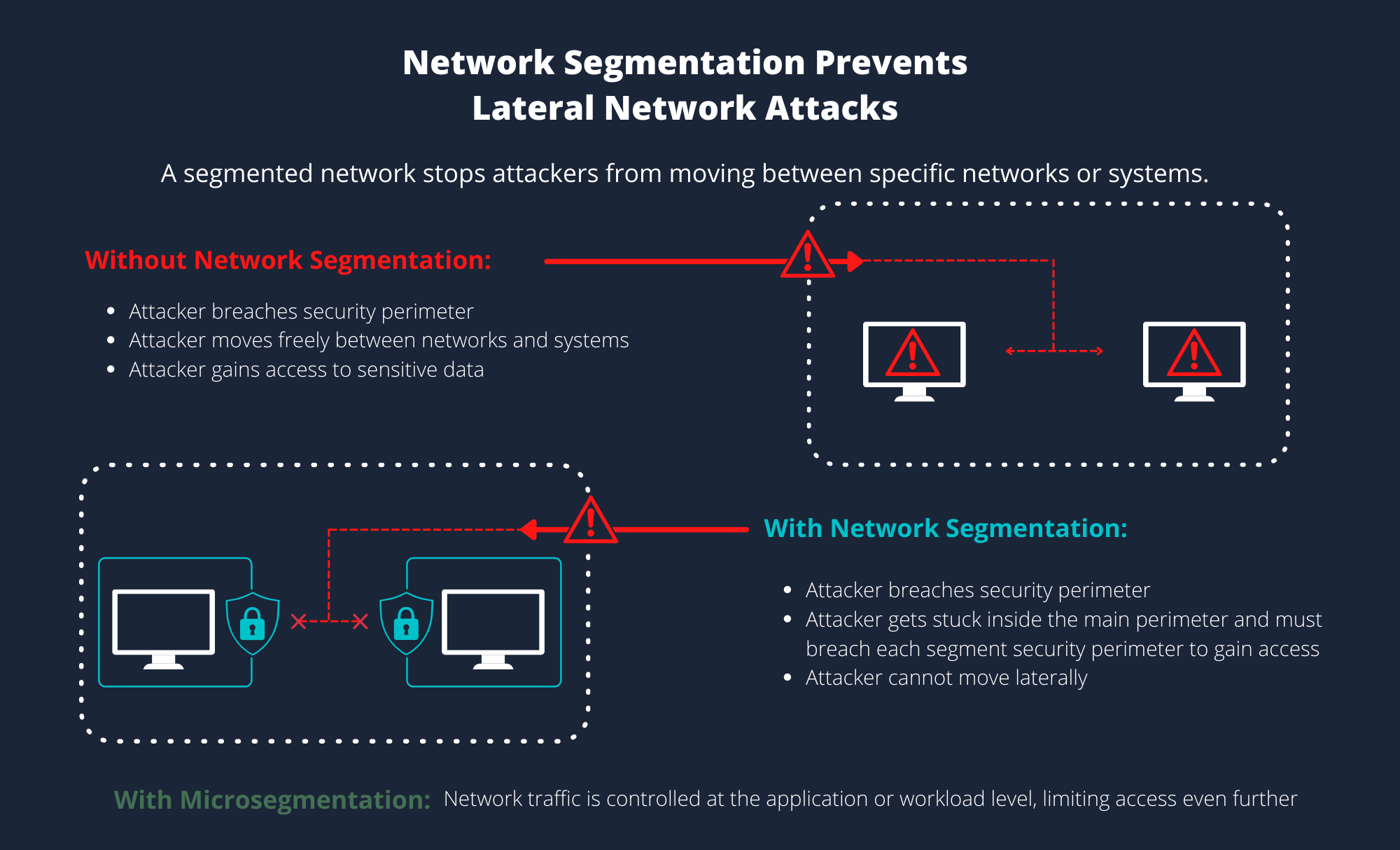
Network segmentation is a process in which your network is divided into multiple zones, with specific security protocols applied to each zone. The main goal of network segmentation is to have a better handle on managing security and compliance. Typically, traffic is segregated between network segments using VLANs (virtual local area networks), with firewalls representing an additional layer of security for application and data protection.
By separating your network into smaller networks, your organization’s devices, servers, and applications are isolated from the rest of the network. Potential attackers that successfully breach your first perimeter of defense cannot get further, as they remain contained within the network segment accessed.
How does network segmentation compare to micro segmentation?
The concept of micro segmentation was created to reduce an organization’s network attack surface by applying granular security controls at the workload level and limiting east-west communication.
While micro segmentation began as a method of moderating lateral traffic between servers within one segment, it has evolved to incorporate traffic in multiple segments. This intra-segment traffic would allow communication between both servers and applications, as long as the requesting resource meets the permissions set out for that host/application/server/user.
Microsegmentation can also be used at a device level. For example, protecting IoT or connected manufacturing or medical devices—since many ship without endpoint security or are difficult to take offline in order to update endpoint security.
The key differences between the two strategies can be boiled down like this:
- Segmentation works with the physical network, policies are broad, limits north-south traffic at the network level, and is typically hardware-based
- Micro segmentation works with a virtual network, policies are more granular, limits east-west traffic at the workload level, and is typically software-based.
An analogy: if your network is a collection of castles, segmentation is like the huge walls surrounding the buildings, while micro segmentation is like armed guards outside each castle door.
When deciding between segmentation and micro segmentation, it shouldn’t be a question of one over the other. Incorporating both models into your security strategy is best: segmentation north-south traffic and micro segmentation for east-west traffic.
Best practices for segmenting network traffic
However you go about segmenting your network, you’ll want to ensure the segmentation plan doesn’t negatively impact overall network performance.
When it’s properly planned and implemented, network segmentation should in fact improve network performance.
Here are some best practices to consider:
Resist the urge to over segment
When it comes to network segmentation, too much of a good thing can be excessive and counterproductive. As networks become too segmented, the ability to manage access can diminish, leading to decreased productivity. Finding the balance between security and ease of management is key here.
Audit your networks regularly
As the number of users, endpoints and applications accessing a network evolves and changes all the time, it’s more difficult for organizations to manage access and activity. To gain that knowledge, regular network audits—which may include vulnerability assessments—are critical to the segmentation process and will help identify security gaps.
Manage and restrict third-party access
With so many third-party vendors and providers requiring some type of access to your network or resources, maintaining specific access points for each vendor is a critical best practice. Remember, breaches happen to vendors all the time, and it’s best to keep yourself protected.
Consolidate similar network resources and categorize data
When segmenting your network, an effective tactic is to combine similar network resources into distinct databases to streamline security policies while protecting data. Regular network audits will allow you to determine which resources should be consolidated. Then, you can categorize the data by type and degree of sensitivity.
How network segmentation supports zero trust and compliance mandates
You’ve probably heard the term zero trust—a popular concept in network security because it addresses the cybersecurity issues facing most organizations today. The default posture of zero trust is that nothing should be trusted, even users or apps already inside the network perimeter.
With zero trust, all users, devices, and endpoints must pass verification before network access is granted. Unverified connections are denied by default while authenticated connections are subject to a restrictive policy for the duration of its network access.
Network segmentation, while a concept and a specific procedure, reflects a broader philosophical shift in cybersecurity towards the zero-trust model. By segmenting network paths, you’re following that “trust no one” brand of thinking.
However, network segmentation doesn’t go far enough in terms of zero trust. As a form of traffic control, network segmentation is considered to be north-south—meaning that any users, applications or devices authenticated into a designated network zone of the network are trusted. If someone is authenticated to access an entire segment, solely based on physical or logical location, and not identity, more controls are required.
This model of trust can lead to breaches, thus the need for micro segmentation.
Building a micro-perimeter
Without network segmentation, achieving zero trust is not possible. Segmentation allows network architects to define a micro-perimeter around the organization’s attack surface, with virtual firewalls to help automate and streamline security.
For compliance requirements like PCI DSS compliance, network segmentation can be leveraged to isolate sensitive credit card data into a fully secure zone. Inside this protected surface, rules are created to only allow legitimate traffic and deny everything else.
Typically, these isolated zones require virtual firewalls and virtualized SDNs (software defined networking) in order to achieve PCI DSS compliance.
Ultimately, segmentation—when combined with zero trust—creates additional headaches and roadblocks for attackers. When they can’t move laterally within your network, they’re essentially stuck at the perimeter. The more difficult it is for bad actors, the better it is for your organization.