Security metrics are vital for you as a security leader to track the progress of your security program and have effective risk-focused conversations with business and operations stakeholders. Security metrics pave the way for security initiatives, facilitate resource, help communicate resource allocation and help communicate results with relevant stakeholders throughout the organization.
Today security functions are expected to plan and track contributions to the business to enable strategic alignment to win and retain customers. Security metrics should help you do your job better and demonstrate to business leadership that you’re doing a good job of managing security. You can hone your existing security metrics so that they are more meaningful and demonstrate actual value to business stakeholders.
Despite growing interest in meaningful security metrics, organizations globally continue to find it a challenging task. CISO’s can find it challenging to define security metrics, as there are no off-the-shelf standard metrics that would suit every organization. There are no established standard templates on what should be measured.
Principles for enhancing existing security metrics
You may reach out to Cybersecurity consulting organizations for help implementing industry standards and vertical-specific requirements, along with their experience in establishing and growing information security risk management combined with security metric reporting. Your consultant can review existing information security metrics so that existing / defined information security metrics align with the current technical landscape and threat environment considering the following principles.
- Review categorization of metrics for comprehensiveness: Examine the current functional categorization for comprehensiveness and framework alignment considering security and compliance requirements (e.g. PCI, HIPAA, FRB), in the light of current applicable regulatory, legislative and industry best practices. Consider metrics concerning the chosen framework for security management.
- Review individual metrics for holistic risk representation: Review existing metrics for suitable attributes such as effectiveness, efficiency, coverage, compliance, timing, cost, and process maturity. This step would help the stakeholder understand the specific risk exposure and quantifiably measure each security metric. For meaningful insight, each metric should have an appropriate unit of measurement. Measurement can be qualitative, quantitative, or binary depending upon the kind of metric.
- Review security metrics lifecycle: Review existing metrics for their continued relevance at least annually. In areas where metrics have been successful in driving maturity, recommendations should be made to modify metrics or enhance the thresholds. Determine whether metrics need to be modified based upon change in overall program maturity, changes in underlying technologies, threats, risks and/or regulations.
- Review security metrics for context, reliability, and credibility: Use metrics to provide the necessary context, reliability, and credibility by looking into the availability of supporting data and explanatory notes where needed. You should also clearly articulate the definition of the metric– your audience needs to understand what is being measured, its business impact, and the meaning of the metric (quantitative/qualitative) - and not just present data in isolation, leaving the audience to interpret the measure or what is the risk / exposure involved.
- Review action orientation of metrics: Don’t just rely on numbers. Interpret insights to help provide actionable recommendations. If the required actions are not made explicit, reporting will not serve its purpose. Be sure that metrics provide adequate information to help target audience to make relevant decisions.
Reporting security metrics
Communication and presentation are vital from a security metrics reporting perspective. While enhancing existing security metrics use communication that:
- Informs stakeholders of key risk indicators in their domains.
- Provides assurance around risk and compliance.
- Fortifies risk appetite discussions.
- Makes the case for funding.
- Satisfies stakeholder expectations for different functions to measure results.
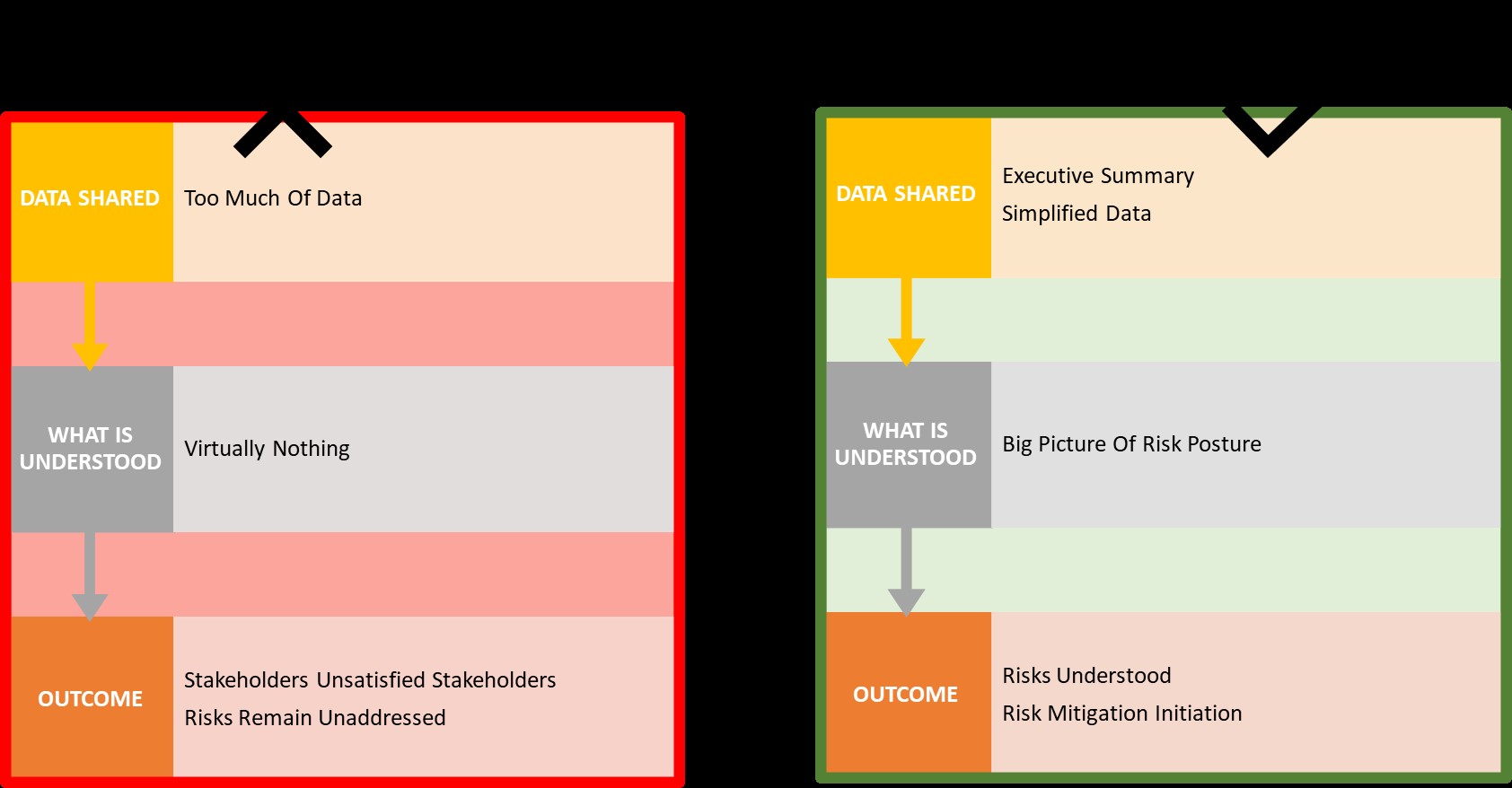
Review of metrics - complexity versus simplicity: Review existing metrics for complexity vis-a-vis purpose of the metric. Focus should be laid on consistency, simplicity, and clarity which are considered more important than elaborate detail and exactness when reporting metrics.
Figure: metrics representation - tactics for SIMPLICITY in Reporting
Presentation of security metrics
Presentations should be clear and concise and match the scope and needs of the audience. Security metrics may be presented to the Board of Directors, CEO, CISO, and CRO. Before presenting security metrics, an important task is to determine the appropriate audience and match the presentation to that audience. Such matching should include careful selection of security metrics and presentation styles to communicate effectively and efficiently to each audience.
Review and enhance your existing security reporting considering the following:
Determine level of detail based on role (function) and level: Appropriate content, formats and presentation styles should be determined. Presentations need to communicate effectively depending upon the role (function) and level of the audience.
For example, a presentation to the information security team (or equivalent) could be very detailed, with data taken from log files and focused on technical issues. A presentation for executives should focus on covering compliance activities, project successes and key business risks.
Select appropriate presentation format: Driven by the intended message and the level of detail of the presentation, one or more formats below should be selected for specific reporting requirements.
Where the requirement is to convey a large volume of information in an easily understandable and clear format non-text-based method shall be used. These allow rapid comprehension and provide a balanced, high-level, view.
Care should be taken to utilize ‘pictorial’ techniques for the board and senior management levels such as dashboards. Dashboards present a large amount of data quickly and concisely, while charts can present trends and forecasts. Traffic lights may be used to present the status of initiatives, compliance etc. supported by tables of data only where required.
Where complex graphs are required to convey an important message, organize graphs with the appropriate message (data points, trends, limits, etc.).
A variety of presentation formats can be used for presenting security metrics:
- Scorecards
- Dashboards
- Traffic lights (status indicators i.e. red, yellow, green)
- Graphs reflecting trends or comparisons
- Tables of raw data
Keep in mind that dashboards on tactical or short-term matters while scorecards cater to strategic decision making. Dashboards should be updated almost in real-time to track operational performance.
Desired outcomes for meaningful security metrics:
- Providing context and motivation for information security efforts
- Boosting credibility and understanding of information security risks and efforts
- Creating a clear call to action for risk remediation
- Providing compliance assurance
- Consistently supporting decision making and influence security strategy decisions
Engage an AT&T Cybersecurity expert
Hone your security metrics resulting in more confidence in your decisions by engaging AT&T Cybersecurity consultants. Take advantage of our industry experience and security metrics domain expertise to refine and optimize security metrics to your specific business and technology environment.