Background
Malware that attempts to harvest credentials from compromised systems is nothing new. However, the crew at ESET recently announced a new threat targeting Mac OS: Keydnap. Keydnap is noteworthy for two reasons:
- It establishes a permanent backdoor to a C&C server
- Its goal is to exfiltrate the Keychain file in Mac OS
And, as Dan Goodin of Ars Technica points out, it’s one of three new pieces of malware to target Mac OS by installing backdoors.
How it Works
So far, it’s not clear how the malware gets on the victim’s system initially. The usual suspects, such as email attachment or malicious web sites…are the usual suspects.
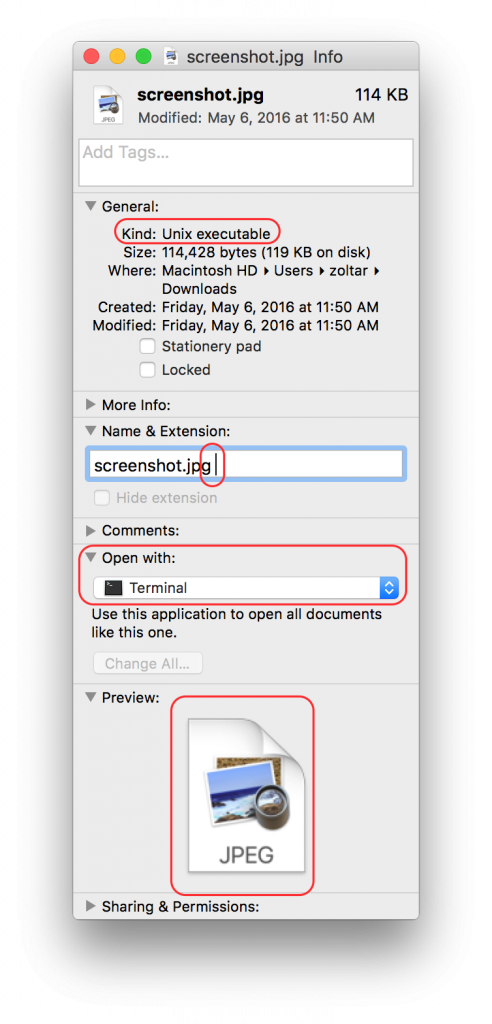
The malware is in a zip file that contains a Mach-O executable with a seemingly innocuous extension, such as .jpg or .txt (Mach-O is a format used by iOS and OSX for native executables).
Upon closer inspection, however, of the contents of the zip file, you’ll see that there is a ‘space’ character at the end of the extension (see screenshot below). The write-up from ESET explains that “…double-clicking the file in Finder will launch it in Terminal and not Preview or TextEdit.”
Screenshot showing details of the malware file masquerading as an image
Source: ESET
Once launched, the file does several things in rapid succession:
- Downloads and installs icloudsyncd, a malicious process that maintains the backdoor to the C&C server
- Swaps out the contents of the Mach-O executable with a decoy document that matches the format of the executable’s extension (e.g., .jpg or .txt), to appear legitimate
Impact on you
Once installed, the Keydnap backdoor starts looking for the Mac OS keychain. For those of you not familiar with the pot of gold the keychain represents in Mac, it contains:
- Application passwords
- Login credentials
- Credit card info
- You get the idea...
Good news: If you have not disabled or modified the settings on Gatekeeper, it’s on by default in OS X, and it will detect the downloader file as an unsigned Mach-O executable, block its execution and instead display a warning. If you have modified Gatekeeper, you may want to rethink your strategy.
How AlienVault Helps
The AlienVault Unified Security Management (USM) platform provides the essential security capabilities that organizations of all sizes need to detect, prioritize, and respond to threats like Keydnap. The AlienVault Labs team regularly updates the rulesets that drive the threat detection and response capabilities of the AlienVault USM platform, to keep users up to date with new and evolving threats. The Labs team performs the threat research that most IT teams simply don’t have the expertise, time, budget, or tools to do themselves on the latest threats, and how to detect and respond to them.
The Labs team recently updated the USM platform’s ability to detect this new threat by adding IDS signatures to detect the malicious traffic and a correlation directive to link events from across a network that indicate a system compromised by Keydnap. Learn more about these updates in the latest Threat Intelligence Update summary posted in our forum.
The AlienVault Open Threat Exchange (OTX) is also a valuable tool for detecting this threat in your environment. The following OTX pulse provides the related Indicators of Compromise (IoC’s) that can be used to detect this threat.
The integration between OTX and the USM platform means that you get alerted whenever indicators of compromise (IOCs) being discussed in OTX are present in your network. The result is that USM customers are up to date on the latest threat vectors, attacker techniques and defenses.