Internet fraud is one of the most common motivators of cybercrime. Millions of dollars are stolen every year from victims who are tricked into initiating wire transfer payments through social engineering tactics and computer breaches. This is typically accomplished using one of three methods: business email compromise (BEC), email account compromise (EAC), and spoofing.
All three of these methods can be attempted against any organization that relies on email for communication. Being a smaller company doesn’t protect you from attempts at fraud - malicious actors target organizations of all size. When proper procedures and tools are in place, it can be relatively easy and inexpensive to protect against them, but failing to take precautions and ignoring the risk can have a negative impact on both your financials and your brand reputation. For example, your customers will not be happy if your organization unintentionally loses their money by sending it to bank accounts that don’t belong to them. The good news is that each of these can be detected and prevented with proper tools and monitoring techniques.
Brian Krebs has published a fantastic article on the value of a hacked email account, which I highly recommend reading, to get a better sense of why the data held by companies is a lucrative target and why email fraud is so common.
Business Email Compromise
Business email compromise is an attack that targets customers or employees that work with your external-facing business associates. Here’s an overview of how it might work:
Customer A (we will call them Able for this scenario) falls for a phishing scam and their email credentials are compromised. The attackers snoop around Able’s email account and notice that they conduct business, including wire transfers and payments, with your company. The attackers use Able’s email account to send a request for a wire transfer or payment that doesn’t particularly stand out as unusual because it is similar to other requests you’ve received in the past. However, instead of using the bank account on file, they ask you to send the payment to a different bank account that’s not on file. The scammer may even proactively offer some kind of reason for this, such as “Our accounts are under audit right now, please send to the account below instead”.
Essentially, attackers in this scenario use a compromised email account to manipulate the trust between you and your customers. This can also happen in reverse. Your employee could fall for a phishing scam and then the attackers use his or her credentials to target your customers, hoping to initiate a fraudulent wire transfer in your company’s name.
The FBI has reported that as of May 2016, over 15,000 organizations have become victims of business email compromise scams losing a combined total over $1 billion dollars. These victims range from small businesses to large corporations in a wide array of business sectors.
Thankfully, this type of fraud can often be detected and stopped by having standard operating procedures (SOP’s) and processes in place that require your employees to verify transfer requests before initiating payment. In addition, you should never change bank account or address information for your customers or vendors via email; such changes should always require a follow up phone call at the very least for verification. Furthermore, enabling two-factor authentication for email where possible can mitigate the risk of unauthorized access to business email. As an added measure, it’s important to be aware of the information relating to your employees and your organization available on social media. Many attackers do their homework before attempting these types of scams; the more information that’s publicly available about your organization’s structure, the easier it is for them to plan and execute their attacks.
Email Account Compromise
Email account compromise scams are like business email compromise in that they both involve compromised email accounts. However, with EAC scams, attackers target internal employees using the compromised credentials of another employee. It’s relatively easy to identify high-level employees with financial responsibilities within an organization, and this information can be exploited to facilitate fraud.
This type of scam can be difficult to detect, because attackers will send what might appear to be an authentic email from the victim’s real email account. They may target accounting employees or financial officers that have authorization to initiate wire transfers. They may also use compromised email accounts to learn more information about your organization, such as lingo, employee titles, customers and vendors to make the attack seem more authentic.
This type of scam can also be stopped when SOP’s are in place that clarify who has authorization to send wire transfers and other payments, how those payments are processed, and what checks should be in place to stop unauthorized attempts. The takeaway from this is that no employee should be able to authorize or initiate a wire transfer based only on an email, no matter what their title is.
Spoofing
The third technique involves the distribution of forged electronic documents that attempt to trick the victim into believing they have received a request from a specific person, when in reality, it came from a malicious third party. This technique is known as spoofing.
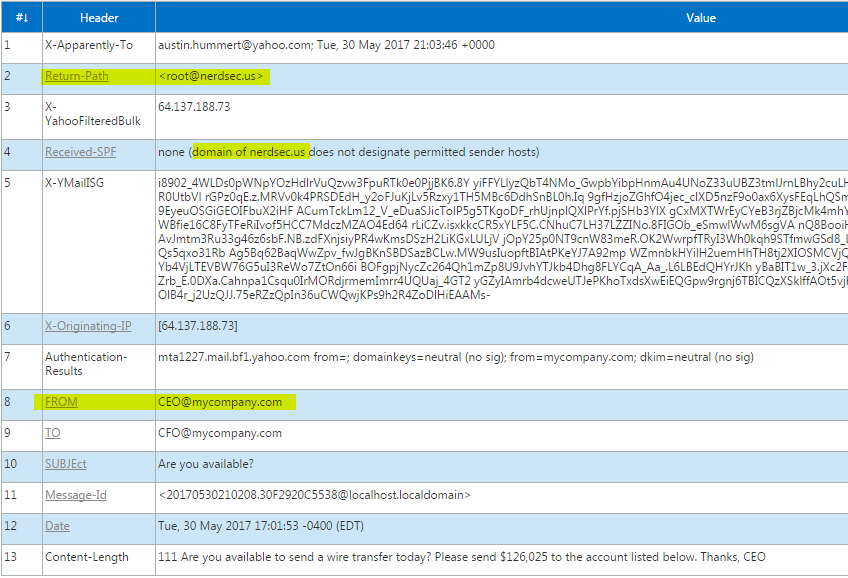
The secret to the success of this attack lies in the headers of an email. Like all good hacks, the exploit lies in a feature that has a perfectly legitimate function. The P1 MAIL FROM header within SMTP is used to authenticate the sender of an email to a specific domain name. This is who the email actually comes from. The P2 FROM header can be used to display a sender alias. This field can be manipulated to display as if it came from anyone. Unfortunately, the P2 header is normally displayed to the recipient instead of the P1, authentic sender. Here’s a practical example:
In the above email, it looks as if the sender of this email is CEO@mycompany.com. However, by looking at the email headers, you can see that is not:
In line two, notice that the return path is root@nerdsec.us. This is the true sender of the email. However, thanks to clever manipulation of SMTP, the attacker was able to add headers to the email in order to trick the receiving client into displaying a different name. Here is what the attacker sees when he sends the mail:
Normally, if someone was not authorized to send an email from your domain, SPF record lookups would fail and the email would never be delivered. However, DNS checks are not completed on your domain in this case. They are completed against “nerdsec.us” in the scenario above (the P1 header, not the P2 header). This is the essence of how fraud facilitated by email spoofing is done. Furthermore, an attacker is most likely to impersonate an executive and target a financial officer within your organization. Who says no to the CEO?
It’s also common for attackers to purchase domain names similar to your companies’ domain. For example, the domain “mycompany.com” is similar to “myc0mpany.com”. If this domain name was available for purchase, a malicious actor could purchase it and use it to send emails to officers within your company, hoping that they would not notice the incorrect domain name.
Spoofing can be detected and prevented in a few specific ways. A common method used by many large organizations is modifying the subject line of all external emails coming into the organization with an identifier that helps employees identify that said email is coming from an external source. If your organization utilizes Microsoft Exchange, you can use a Hub Transport Rule to append the subject of emails with a label such as “OUTSIDE”, “EXTERNAL”, or “UNTRUSTED”. When this label is seen by your employees, they will automatically know that the email came from outside the organization. As an example, if the CFO of your company receives a spoofed email that appears to be from the CEO, it would be easy for them to determine that the email was spoofed with little to no technical understanding of SMTP because the subject of the email would be appended with an untrusted label.
Perhaps one of the most effective ways of detecting and blocking spoofed email is by implementing DKIM functionality within your mail system. DKIM (DomainKeys Identified Mail) provides a way for verifying a domain name associated with an email message. At its essence, it’s a check to ensure that an email that claims to come from a specific domain was authorized by the owner of that domain. DKIM is the most effective way to automate the detection and prevention of spoofed emails.
Similarly, by analyzing Microsoft Exchange logs, you could theoretically write a SIEM use case that detects a difference between the source user name field (the “from” address) and the X-Sender field. By comparing the “Return-Path” or the “X-Sender field” against the “From” field, you can easily detect spoofed emails coming into your organization. If these fields do not match, it’s very possible that the email is malicious.
Large organizations that merge with or acquire (M&A) other companies can also be vulnerable to these types of attacks during the purchasing process. Smaller companies who normally consider themselves “off the radar” that don’t have processes in place that specify how wire transfers are handled can easily fall victim when they are suddenly in the news affiliated with larger companies. Attackers monitor the news for these types of purchases because organizations find themselves more vulnerable to internet fraud scams because as the two entities figure out how to organize themselves into one, it can be a very chaotic and confusing time. For this reason, it’s very important to ensure that your business understands this risk and that SOP’s are put in place from the very beginning of the M&A process, no exceptions.
Conclusion
Internet fraud is one of the most common ways a criminal can steal money from you without having to write malware or otherwise utilize large amounts of resources to effectively target your organization. If a hacker were to send out 100 spoofed emails asking for fraudulent wire transfers to be sent, and just one of them was a successful attack, they still have a very large payday coming. This makes Internet fraud an easy vector of attack. It’s important for all organizations both big and small to take steps to protect themselves from these common types of scams.