Our friends at BlackBerry recently released an in-depth blog post on a campaign by threat actors targeting online payment businesses that discusses what happens from initial compromise to the skimmer scripts themselves. You can read their blog here. This blog is focused on what we found across the AT&T Cybersecurity customer base as we looked for the indicators of compromise (IOCs) identified in the BlackBerry blog and on the quick-follow up analysis we performed and provided to our customers.
As a part of the AT&T Managed Threat Detection and Response (MTDR) threat hunter team, we have the unique opportunity to perform threat hunting across our fleet of customers in a very fast and efficient manner. Leveraging the logs across hundreds of data sources, we can come up with our own hunt hypotheses and develop extremely complex searches to find potential prior incidents and compromises.
We can also work with the AT&T Alien Labs team to turn that search syntax into a correlation rule. The Alien Labs team uses this backend data that we gather to create thousands of rules and signatures within the USM Anywhere platform. Threat hunters can also search for specific known tactics, techniques, and procedures (TTPs) and indicators of compromise (IOCs) as we ingest and process cyber threat intelligence from both open sources (i.e., publicly available data) and closed sources (i.e., government or private data that is not publicly available).
When we looked for the TTPs that the attackers were using to deploy the credit card skimming scripts, our searches yielded no results, but when we searched for IOCs related to where the credit card data was exfiltrated during this campaign, we observed one domain come up across a few customers. Armed with key information such as time frames and which customers and users were impacted, we could now go deeper into USM Anywhere to investigate.
Figure 1 – Web request for credit card skimming exfiltration domain
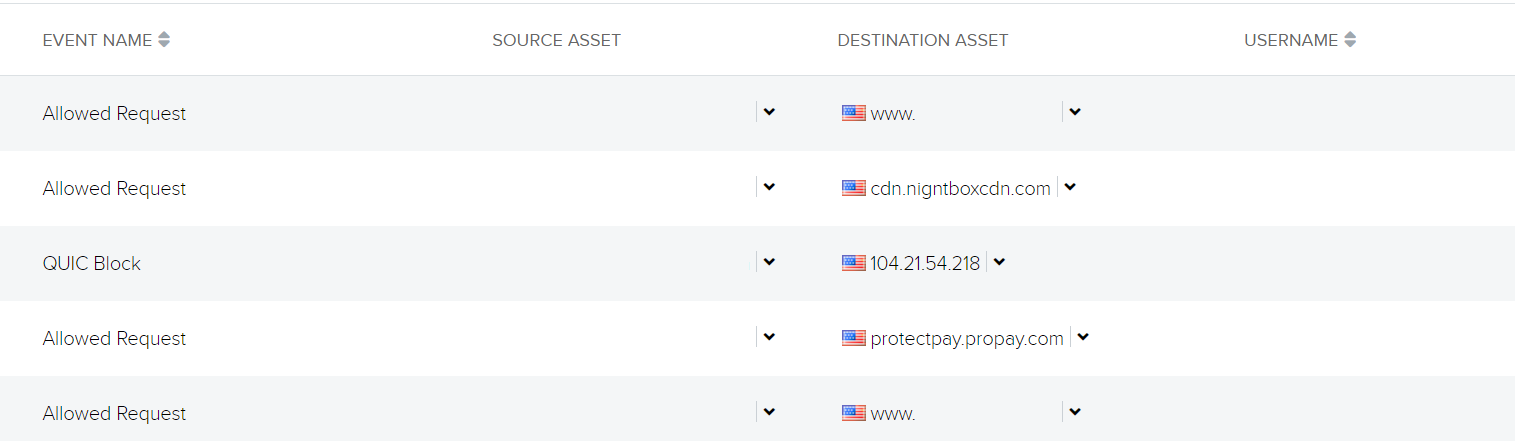
Figure 1 shows that the request for the credit card skimming site referred from another website for a well-known food company with an online purchasing option. We observed this to be the case for all the other customers too, with the food site being either the direct referer or being the HTTP request right before the connection to the cdn[.]nightboxcdn[.]com site. One of the other observed impacted customers had a user’s credit information skimmed from a different compromised site (see Figure 2).
Figure 2 – Traffic going to shopping site (redacted) followed by traffic to the skim exfiltration and then a legitimate payment site
We can see that the user is on an online shopping site (redacted) followed by traffic to the exfiltration domain as well as to a legitimate payment portal service. We can conclude from the traffic flow that the user went to checkout and that after they input their payment details, this information went to both the exfiltration site and the legitimate payment service, ProPay.
By using the website scanning tool urlscan.io and by looking at a scan of the shopping site from May 23, 2023, we could see the skimming script appended to the jquery.hoverIntent.js file (legitimate script ends after });).
Figure 3 – Skimming script appended to legitimate script
Once we decode the attacker-added code snippet and simplify it down to its most basic parts, we can see that it extracts the field values of first name, last name, phone number, email address, address, city, state, zip, card holder name, card number, expiration month and year, and CVV. The data will then be sent to the exfiltration domain via a XMLHttpRequest:
Figure 4 – Decoded and simplified skimmer script
After we uncovered what was happening, we quickly notified our impacted customers so they could advise their employees to request new credit card numbers from their banks. While it was good to know that our customers were not directly compromised by the threat actor deploying these card skimmer scripts, the attacks demonstrate the need to be to be constantly aware of the potential for other organizations to be compromised and the impact this could have for your end users.
Leveraging a defense-in-depth strategy that includes endpoint detection and response tools, network controls and defense, security monitoring, and employee education programs is critical to protect against threat actors that can cause your business financial and reputational loss.
AT&T Cybersecurity has a broad portfolio of managed security services to help you protect across your attack surface. Contact us if you’d like to learn more.