The Bridge on the River Forza
We can teach these barbarians a lesson in Western methods and efficiency that will put them to shame.” -Colonel Nicholson (The Bridge on the River Kwai, 1957)
Efficiency. Something we look to implement in everything we do, whether that be through the elimination of waste through Six Sigma, or other frameworks and methodologies, efficiency is what we strive for. When performing digital forensics, efficiency and rigor in our approach to ensure no stone left unturned is paramount to the success of the investigation.
One of the many frameworks that exists is FORZA, a group of tasks and processes in a digital forensics investigation that revolves around a triad of: Reconnaissance, Reliability, and Relevancy.
For Reconnaissance, the case examiner will collect, recover, decode, discover, extract, analyze, and convert data that is kept on different storage media to readable evidence.
Reliability speaks to the integrity of the evidence and the relationship between the people and the evidence such that it will hold up in court if prosecuted.
Relevancy speaks to the relevancy of the evidence, even if it is admissible in court.
The FORZA Framework defines eight separate roles in a digital forensics investigation, the case leader, system/business owner, legal advisor, security/system architect/auditor, digital forensics specialist, digital forensics investigator/system administrator/operator, digital forensics analyst, and a legal prosecutor.
Each of these roles are interconnected through six categories of questions that must be answered in the investigation: (1) What (data); (2) Why (motivation); (3) How (function); (4) Who (people); (5) Where (network); and (6) when (time). If you think about it, this is very similar to what a crime scene investigator must answer when investigating a murder scene, which is why I’m always saying that digital forensics is like CSI: Miami meets Bones.
Here's a short video I made on the topic.
Below is a table detailing out the responsibilities for each role in answering each of the six questions.
Okay, so now that we’ve covered FORZA (don’t get confused here), let’s discuss a newer, more novel model gaining widespread popularity, which is the Diamond Model of Intrusion Analysis; a model of intrusion analysis built by analysts, asking the simple question, “What is the underlying method to our work?” The model establishes the basic atomic element of any intrusion activity, the event, composed of four core features: adversary, infrastructure, capability, and victim.
These features are edge-connected representing their underlying relationships and arranged in the shape of a diamond, giving the model its name.
In its simplest form, the model describes that an adversary deploys a capability over some infrastructure against a victim. These activities are called events and are the atomic features. Analysts populate the model’s vertices as events are discovered and detected. The vertices are linked with edges highlighting the natural relationship between the features. By pivoting across edges and within vertices, analysts expose more information about adversary operations and discover new capabilities, infrastructure, and victims.
The Diamond Model of intrusion analysis comprises the core features of an intrusion event: adversary, capability, infrastructure, and victim. The core features are linked via edges to represent the fundamental relationships between the features which can be exploited analytically to further discover and develop knowledge of malicious activity.
The above depiction models analytic pivoting using the Diamond Model. One of the most powerful features of the Diamond — pivoting, allows an analyst to exploit the fundamental relationship between features (highlighted by edges between the features) to discover new knowledge of malicious activity.
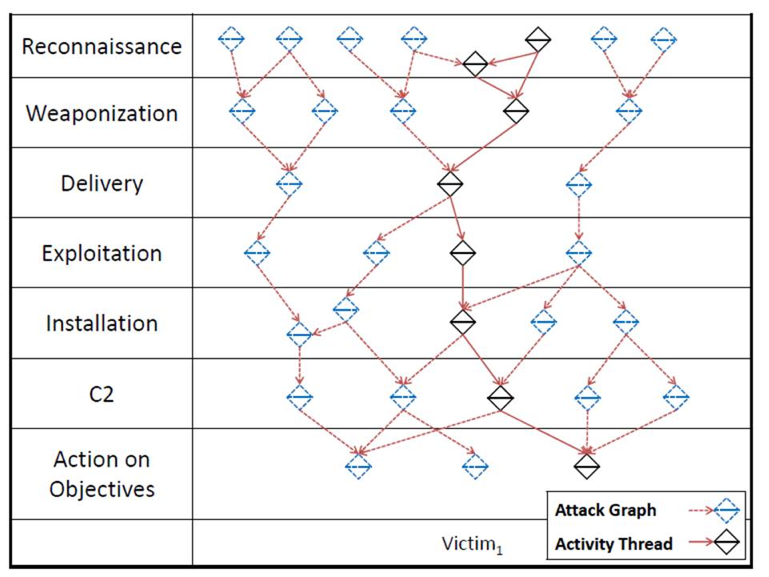
Subsequent to this analysis is an Activity-Attack Graph, diagrammed above. This chart illustrates the integration of knowledge of actual adversary attack paths with the multitude of hypothetical attack paths that could be taken. Using an activity-attack graph highlights the potential paths of an adversary in the future as well as the preferred paths based on current knowledge.
As forensic analysts, we should always look to be continuously improving our craft, especially around our methodology in how we conduct investigations. I leave it to you to decide on which methodology you adopt, or possibly even make better.
More information on the Diamond Model can be found here and here.