“It’s Reigning CATs…”
Scenario comment from the board room…“What’s our risk to external threats, and are we prepared? Better yet, how will we know?” asked a board member.
Gone are the days where the board is not intimately involved in cybersecurity assessment and having an understanding as to the organization’s security posture. Like it or not, cybersecurity assessment tools become required because oftentimes not enough is proactively done and there is a disconnect between security and the rest of the business. Once governing bodies pass down their guidance and requirements, executives and boards begin to pay more attention. The next question; “is this forward-thinking or good enough?”
Some have argued that tools like the Cybersecurity Assessment Tool (CAT) from the FFIEC mimic that of others, such as PCI. Regardless of the opinion, while nothing is bulletproof, these tools do raise awareness and can help achieve necessary buy-in where it otherwise may not have gotten noticed. Naysayers will be quick to shoot this down, but on the other hand they can help move security in the right direction versus standing still. No, catering to compliance is not strategic and it shouldn’t be the minimum standard to “ride the Internet.” But let’s face it, this is what is getting attention and so teams must embrace this. Rather than poking holes in the assessment tool from the FFIEC, there’s an opportunity to try and drive this more into the business. If executives and boards are being asked to be part of the solution, then teams may have some momentum to advance their cause.
The FFIEC’s assessment tool is broken out into two parts and with maturity levels;
- Inherent Risk Profile
- Technologies and Connection Types
- Delivery Channels
- Online/Mobile Products and Technology Services
- Organizational Characteristics
- External Threats
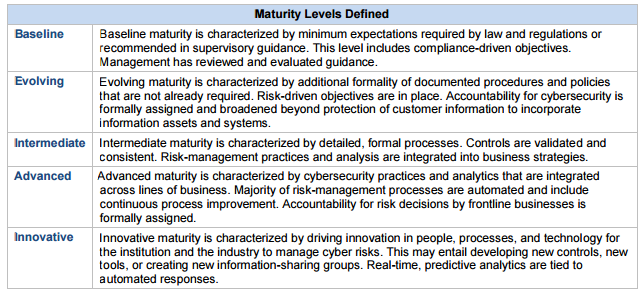
- Cybersecurity Maturity
- Cyber Risk Management and Oversight
- Threat Intelligence and Collaboration
- Cybersecurity Controls
- External Dependency Management
- Cyber Incident Management and Resilience
Initially the tool was tagged with the words ‘self-assessment’. This caused some in the financial services community to view this as voluntary, or optional. The OCC has issued comments stating, “while use of the Assessment is optional for financial institutions, OCC examiners will use the Assessment to supplement exam work to gain a more complete understanding of an institution’s inherent risk, risk management practices, and controls related to cybersecurity[1]. OCC examiners will begin incorporating the Assessment into examinations in late 2015.”
The OCC continues to say, “The Assessment helps banks and examiners determine a bank’s inherent risk profile and level of cybersecurity preparedness. The results may be reviewed to determine whether the bank’s cybersecurity maturity levels align with the bank’s inherent risk profile.”
So while some may get stuck on the word, optional, it is clearer that this assessment tool will be used, and therefore it would be in an organizations best interest to adhere to its structure. In fact, “late 2015” may already be here based on some in the industry indicating the tool is part of the engagement. This should not come as a surprise.
Knowing that many in the industry are not fans of tools such as this, it is irrelevant. What teams should do is use this along with other industry drivers to call attention to security and have some heart-to-heart discussions on the security posture. If this is a benchmark, why not address this proactively? Even if catering to the audit is not popular. Technically, “compliance” should be a byproduct of security done well.
The next order of business should be to:
- Review the cybersecurity assessment tool with stakeholders, executives, and the security steering committee to gain support
- Use the tool as a way to assess program maturity
- Share the results with stakeholder, executives, and the security steering committee
- Agree on next steps to move the program more towards innovative (if so desired) practices
- Measure the progress and align to the overall benefit to the organization
The innovation level is what some have clamored for and so this is a chance to move well beyond “checking the box” and to be forward-thinking. With executive and board oversight, this can help propel the security program forward towards a more innovative and proactive position.
[1] http://www.occ.gov/news-issuances/bulletins/2015/bulletin-2015-31.html