Introduction / Overview
There’s no doubt that the adoption of public cloud deployments has accelerated for most organizations recently. In fact, according to metrics released by Oracle recently, nearly half (49%) of all respondents to the Oracle and KPMG Cloud Threat Report expect to store most of their data in a public cloud by the end of 2020. Effectively managing the security and compliance of public cloud deployments can be tricky for many organizations. The same study revealed that 38% of the respondents indicated that detecting and responding to cloud security incidents is their number one cybersecurity challenge.
There are multiple factors that contribute to the issues associated with deploying and maintaining highly secure cloud environments. In this article we’ll explore three of the issues most often encountered:
- Shared responsibility model
- Lack of visibility
- Misconfiguration / Configuration Drift
An exacerbating factor in all three common issues noted above is the lack of common terminology amongst components associated with the various public clouds as documented below:
|
Amazon |
Microsoft |
|
|
|
Cloud Name |
Amazon Web Services (AWS) |
Azure |
Google Cloud Platform (GCP) |
|
Machine |
Instance |
Virtual Machine (VM) |
Compute Instance |
|
Storage |
S3/EBS/Glacier |
Blob Storage |
Google Cloud Storage |
|
Serverless Code Function |
Lambda |
Azure Functions |
Cloud Functions |
In addition to the differing terminology for components between the various public cloud providers, also keep in mind that the individual components themselves often require broad capabilities to effectively monitor and provide the security to maintain the various components within a cloud deployment. For instance, the machines deployed within the cloud may be most effectively monitored using conventional solutions often used in traditional on-prem deployments. These solutions include scan engines and / or host agents. The associated storage and serverless code functions require solutions providing functionality specific to the cloud that has the capability to derive account configurations and resources associated with the machines deployed. We’ll delve into more detail as we discuss the other common issues encountered in highly securing cloud deployments below.
Shared responsibility model
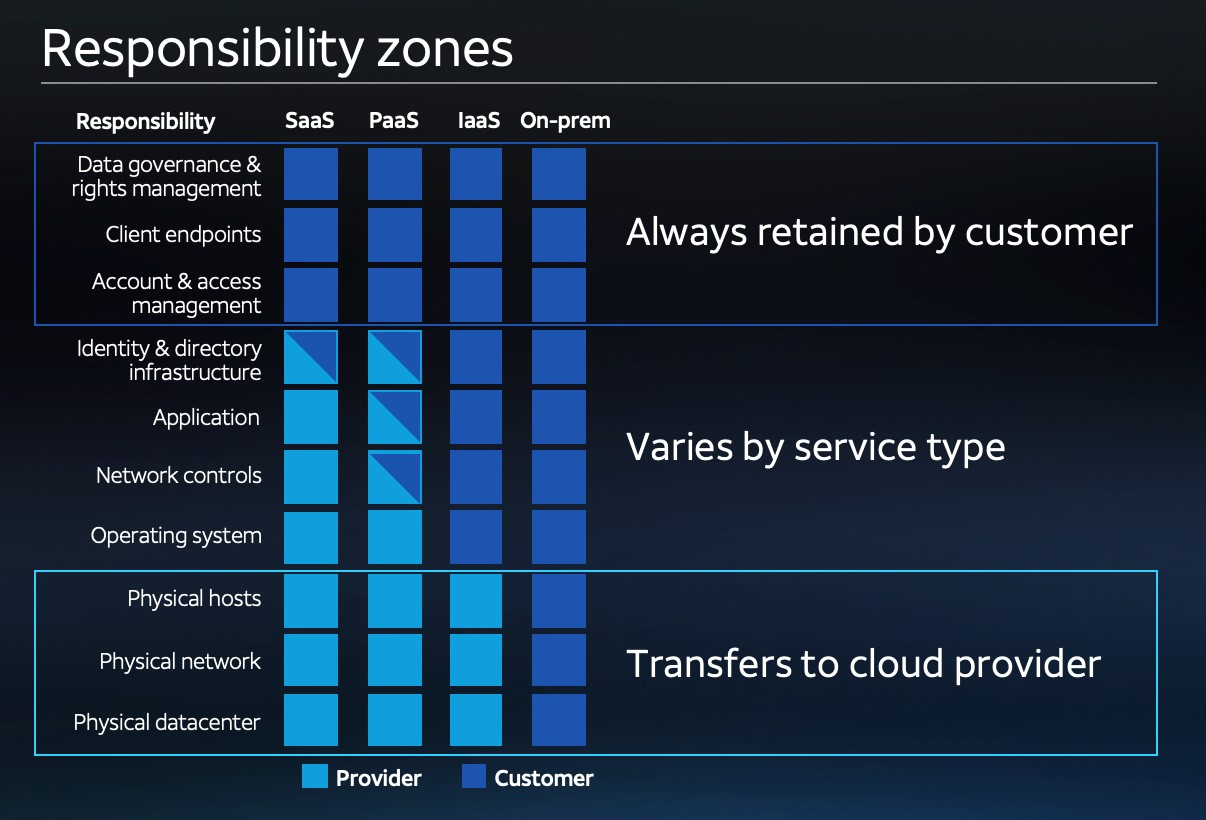
Unlike security and compliance controls in more traditional on-premise deployments, the security of public cloud deployments is always a shared responsibility between the cloud provider and customer. This shared responsibility model can be challenging for many different organizations. In fact, according to a recent Gartner report, 82% of cloud users have experienced security events due to confusion over Shared Responsibility Security Models. As you can see in the graphic below, depending on the type of cloud deployment you have, the elements that organizations are responsible for changes:
As illustrated above, while a Software as a Service (SaaS) deployment minimizes the number of elements that a public cloud customer is responsible for, that responsibility increases when using a Platform as a Service (PaaS) and continues to expand with Infrastructure as a Service (IaaS) deployments. Because of this, it’s key that organizations with public cloud deployments know which cloud components and associated security controls they’re responsible for so that they can implement appropriate controls and monitor them over time to provide for their on-going effectiveness.
Lack of visibility
Another common challenge facing many organizations is providing that they have a complete and up to date visibility into their cloud deployments. One study noted that 38% of CISOs responding expressed inadequate visibility into public cloud workloads as their top cloud security challenge. It’s important to realize that visibility into the workloads / machines and all associated resources is a key requirement. Just as important is visibility into the overall public cloud account’s configuration and security controls. Without that complete picture it’s impossible to effectively protect public cloud deployments and provide that they remain protected over time.
Misconfiguration / Configuration drift
Once organizations have a complete understanding of the components that they’re responsible for protecting and complete up to date visibility into their cloud assets and associated resources, the next important challenge to address is establishing, maintaining and enforcing approved configurations. Such configurations should include both internally defined security and compliance controls while including applicable industry standards and best practices. Once those approved configurations are defined and deployed, it’s critical that the assets and associated resources deployed within public clouds be consistently monitored and their approved configurations enforced.
AT&T Cybersecurity Consulting can help
Know that while the common cloud challenges noted above can be daunting for some organizations to address, AT&T Cybersecurity Consulting can be of great assistance when it comes to the security and maintenance of your public cloud deployments. Our Managed Cloud Security Monitoring Service not only effectively addresses the common challenges noted, it also includes access to and assistance from dedicated AT&T Cybersecurity Consultants who will provide expert assistance on-demand to help maintain your public cloud deployments. Please reach out to us at scan@att.com with any questions at all, or to request a demo of our Cloud Security Monitoring Service.