As energy and utilities companies strive to use the edge to innovate new solutions for delivering more efficient and resilient services, cybersecurity risks to carrying out those business missions loom large. Ransomware attackers and other cybercriminals have increasingly found energy and utilities organizations a profitable target, lobbying high-profile attacks in the last few years that have threatened safety and uptime in the process.
Operational and security experts at these companies are well aware of the balancing act they must achieve under these conditions, according to a new industry breakout of the AT&T Cybersecurity Insights Report. Released this week, the AT&T Cybersecurity Insights Report: Focus on Energy and Utilities shows that technologists in these organizations are called upon by the business to roll out edge use cases such as remote-control operations, self-healing assets, and intelligent grid management. At the same time, they must ensure these deployments are done with cybersecurity as a central component, as the impact of attacks against this vertical's edge-connected assets could have drastic consequences for companies tasked with delivering the most vital resources for modern living.
Rapid rate of energy and utility innovation
One of the key areas examined by the AT&T Cybersecurity Insights Report is the rate of adoption of edge computing, the use cases in play, and their stage of maturity. This was tracked across six major sectors. This latest industry report dives into the trends for companies that provide services and resources such as electricity, oil and gas, water, and sewer. The study shows that some 77% of energy and utilities respondents worldwide are planning to implement, have partially implemented, or have fully implemented an edge use case. The study dug into nine industry-specific use cases and examined their stage of adoption across the energy and utilities sector.
Combining the mid-stage and mature stage adoption rates reveals that the use of edge computing in infrastructure leak detection has the highest combined adoption maturity (82%) among survey respondents. Some examples of how this looks in action includes using sensors to gauge the flow of water in a municipal water system and using the low latency of edge connections to monitor that data in real time for drops or spikes in pressure that could indicate the need for preventive maintenance or immediate servicing of equipment. This is of course a single example in a broad range of use cases currently under exploration in this sector.
Edge computing has opened up tremendous opportunities for energy and utilities companies to solve tough problems across the entire value chain, including the safe acquisition of energy supplies on the front end of the supply chain, the proper monitoring of consumption of energy and resources on the back end, and the efficient use of facilities and equipment to run the functions between the two phases. Some additional examples most commonly cited were:
- Remote control operations
- Geographic infrastructure exploration, discovery, and management
- Connected field services
- Intelligent grid management
Interestingly, in spite of many energy companies engaged in proof-of-concept and insulated projects, overall the sector's rate of mature adoption was the least prevalent compared to all other sectors, sitting at about 40%. Survey analysis indicates this isn't from a lack of interest, but instead a product of the justifiably cautious nature of this industry, which keeps safety and availability top of mind. The fact that this market segment had the highest level of adoption in mid-stage compared to other industries offers a clue that these companies are all-in on edge deployments but taking their time considering and accounting for the risks—including those on the cybersecurity front.
Compromise worries grow
The study shows that 79% of energy and utilities respondents believe there is a high or very high likelihood of a compromise in one of the use cases intended for production within the next three years. When respondents were asked about the impact that a successful compromise would have, energy and utilities industry respondents were the most concerned of all industry respondents. This is hardly shocking given the grave real-world, physical consequences that can stem from a loss of control or safety over operational technology (OT) assets that run the power plants and pipelines within this industry.
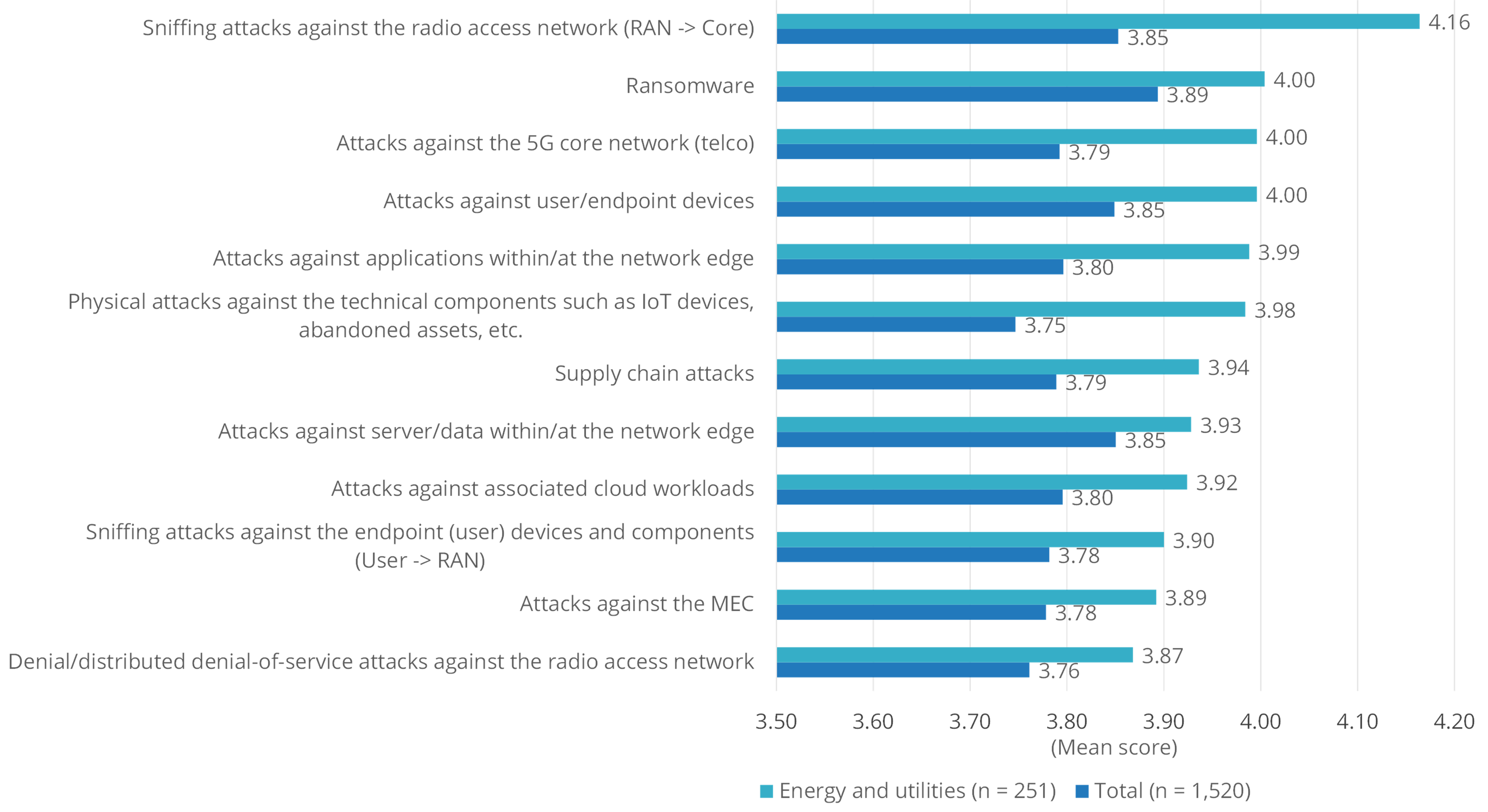
Given the media attention surrounding very public ransomware attacks in this sector recently, it's no surprise that ransomware is one of the top cybersecurity concerns for technology leaders in this space. However, it is nevertheless not the number one cybersecurity concern for technology leaders in the energy and utilities space, sitting instead as number two behind the more pressing issue of potential sniffing attacks against radio access networks (RAN). Also tied for second alongside ransomware were attacks against 5G core networks, and attacks against user/endpoint devices.
An interesting point to note about this industry is its heightened level of concern over physical attacks against technical components such as IoT devices. The industry rated this concern much higher than the average respondent. This is likely a function of the industry's growing reliance on remote sensors, devices, and endpoints in low-latency (and often far-flung) environments.
The unique cyber considerations in energy OT environs
Protecting the ability of an organization to safely provide reliable electricity, accurate bills, and safe pipelines will increasingly require cyber controls be applied to the external assets that deliver the benefits of edge computing use cases. Fortunately, energy and utilities leaders are investing accordingly in cybersecurity controls around the edge.
The study shows that the energy and utilities sector has the second-highest commitment to major security investments baked into edge use cases compared to the others, lagging only slightly behind the US public sector. Approximately 65% of energy and utilities firms are allocating 11% or more of their edge funding directly for security.
One of the challenges in applying that funding is the so-called IT-OT security gap that face industrial sectors like this one. Energy and utilities firms can't rely on many classic cybersecurity controls like other industries, due to the limitations in technology and operational factors not found elsewhere. For example, many OT systems can't be patched in a timely fashion due to the operational risks posed by a failed update and the fact that many OT devices may run months or even years between scheduled maintenance windows. Operators in this sector have an extremely low tolerance security actions that potentially risk bringing down an entire oil refinery or wastewater treatment facility. This is why when the report examined the effectiveness rating of security controls in this industry, patching ranked dead last, as compared to a relatively high rating in all other industries.
Further, it may be challenging to collect and normalize data for monitoring purposes given the increase in data across merged IT/OT networks. OT networks cannot be monitored in the same way that IT networks are, due to unique protocols and also similar risk problems that the security 'cure' may be worse than the disease. For example, active scanning techniques can often disrupt or take down OT networks. This is likely why intrusion detection solutions were rated to have the highest total cost of ownership (TCO) within this particular sector.
As energy and utilities companies strive for the right balance of innovation and security at the edge, we recommend a careful approach that accounts for the fact that traditional endpoint-centric controls like patching can't always be the go-to solution. Proactive controls such as micro segmentation, passive vulnerability scans, and threat hunting should be considered for these more difficult use cases. These organizations should consider getting professional guidance from service providers on the front end to evaluate road maps for current and proposed use cases. The experts at these providers have already tread this ground and can best advise on the potential hazards that an organization may face along the way.