Breaches and cyberattacks are on the rise in the healthcare industry. The recent acceleration of digital technology and connectivity within Healthcare has led to significant patient care delivery improvements, more effective population health management, and better patient outcomes. With this increased technology and connectivity, however, comes increased exposure to cyberattacks that can impact patient care delivery, safety, and privacy.
- Cybersecurity Ventures predicts that Healthcare will suffer 2-3X more cyberattacks in 2021 than the average amount for other industries. Woefully inadequate security practices, weak and shared passwords, and vulnerabilities in code expose hospitals to perpetrators intent on hacking treasure troves of patient data.
- Ransomware attacks on healthcare organizations were predicted to quadruple between 2017 and 2020 and will grow to 5X by 2021, according to a report from Cybersecurity Ventures.
- The Secretary of U.S. Department of Health and Human Services (HHS) Breach of Unsecured Protected Health Information lists 592 breaches of unsecured protected health information affecting 500 or more individuals within the last 24 months are currently under investigation by the Office for Civil Rights. Three hundred six of the breaches were submitted in 2020.
- HIMSS 2020 Survey findings: A broad attack surface exists within many healthcare organizations due to the profound lack of resources. Relatively few healthcare organizations are conducting end-to-end security risk assessments. Many risks are unaddressed due to the lack of comprehensive security risk assessments. Furthermore, the legacy system footprint is growing within many healthcare organizations. Sensitive information is exposed, and such systems are vulnerable to attack.
Diagnosis, prognosis and a prescription to help cure
Diagnosis:
- Healthcare data valuable in the black market
- Connected medical devices vulnerable
- Medical data availability is as vital as Confidentiality, Integrity
- Business Associates and Security Risk (Supply chain)
- Compliance regulations scrutiny
- Legacy systems (still uses end of life OS)
Prognosis:
- Threat intelligence information on Healthcare
- Future of telehealth in Healthcare
- Post COVID threat landscape shift
- Prescription for cure
- Proactive best practices
- Lessons learned based on current diagnosis
- Digital risk management in Healthcare
Prescription to help cure:
- Verify that data is backed up frequently.
- Frequently test restore procedures on randomly selected files.
- Review the threat surface regularly or each time a system is implemented.
- Require strong, complex passwords and change them at regular intervals.
- Use only authorized software on the enterprise network environment.
- Use the “Principle of Least Privilege” approach to user accounts and data access.
- Establish controlled entry points for a remote network or data access.
- Implement network monitoring and benchmarks for “normal” activity.
- Conduct tabletop exercises to test cybersecurity response plans.
- Implement multi-factor authentication.
- Provide that file encryption utilities are enabled on portable user devices.
- Offline off-premise backup to facilitate recovery if backups are compromised.
- Segment the network.
Healthcare information workflows
The flow of healthcare information follows the patient, starting at the doctor’s office, to laboratories, imaging centers, pharmacies, and other care facilities. This natural flow of medical records provides many points where information security must be considered and proper processes implemented. While extremely beneficial for patient healthcare, increasing interconnection also raises risks related to patient privacy and confidentiality. There is a heightened consumer awareness regarding the confidentiality of sensitive information. The potential impact of reported data breaches has caused consumers to expect and demand the protection of their personal health information.
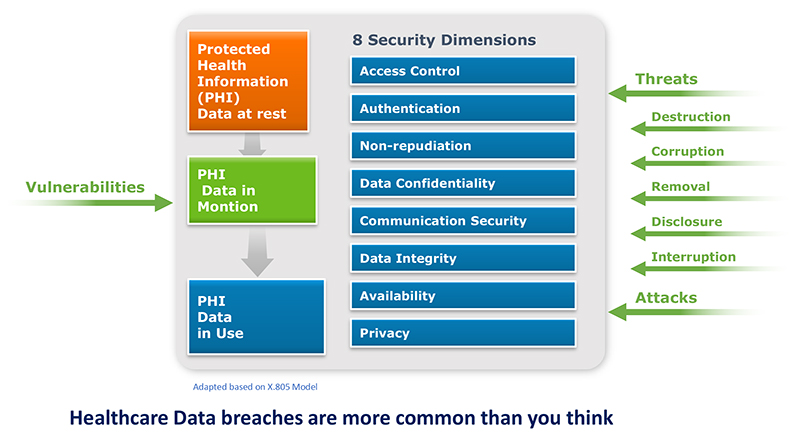
As healthcare operations benefit from advancing technologies which promote information sharing, it is necessary to build and use the appropriate information protection framework to help preserve the integrity and protect the confidentiality of Protected Health Information (PHI.)
Are you ready for an information protection framework focused on health information in 2021? Keep in mind all the different threat vectors and the eight security dimensions, as shown in the figure below.