Last week, our friends from Norman published a great report on a cyber espionage campaign named Operation Hangover.
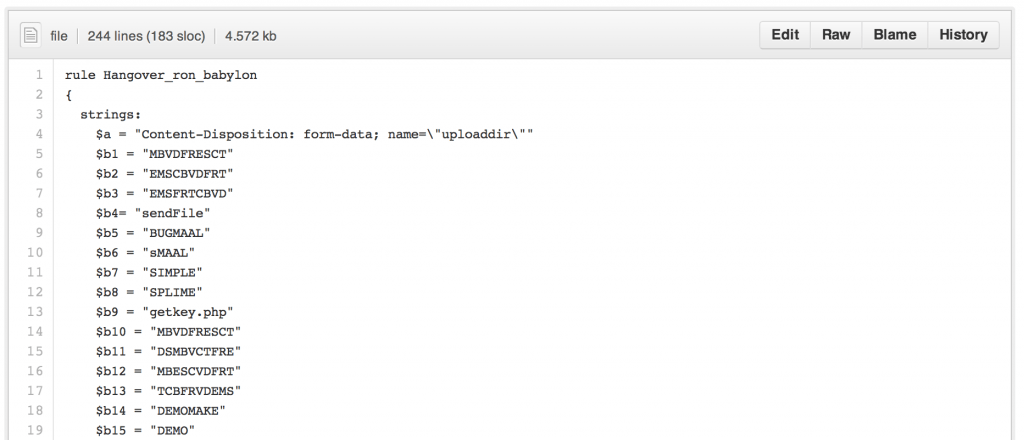
We have released some Yara rules to detect most of the payloads mentioned on the paper. You can download the rules from our Github space:
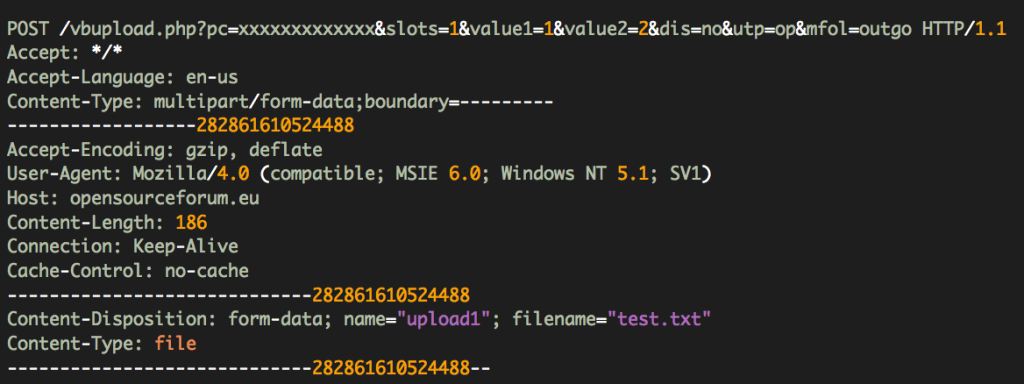
On the other hand the Hangover attackers have been using several payloads with network capabilities to steal data including documents, keystrokes and downloading other payloads. Following are some examples of network traffic performed by these payloads:
- Smackdown Minapro
- Hangover
- Several keyloggers and data harvesters
Some of the network requests made by these payloads were covered by Snort rules (Emerging Threats) months before the Operation Hangover was uncovered) so our product was alerting on these connections from at least several weeks.
AlienVault Unified Security Management (USM) will detect all the threats mentioned on the blog post (and it’s available as a Free 30 day trial download).