Continuing the research on the last spearphishing campaign we published yesterday, we found that the same group is using another downloader named Win32/Coswid. The dropper is similar to the one we described in the previous report.
The main difference is that instead of using an html file to hide the configuration, it gets the config values from a PNG file.
Once running, the dropper will send a request to a remote server and will try to download the PNG file.
We noted that the first part of the User-Agent header is the name of the computer running the dropper and the second part is a static string as seen in the code:
This is useful to write an IDS signature based on the User-Agent. You can also find an anomaly on the Accept header (*/*,,,,,).
The PNG file is a valid image:
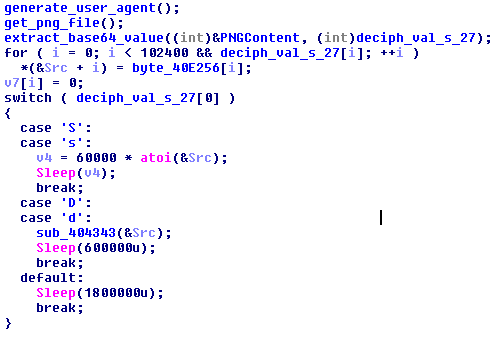
But if you open the file you will find something interesting at the end of that file:
The dropper scans the file for content between “<!—” and “—!>” and performs a base64 decode. This version of the dropper supports only two commands:
- s [sleep], example s:20
- d [download], example: d:173.10.48.242 /html/AcroRd32.gif
If the dropper finds the download command, it will grab the file specified on the configuration entry. Then it will decrypt and execute it.
There are IDS rules on both Snort Sourcefire and EmergingThreats Pro to cover the HTTP requests:
1:22103 <-> ENABLED <-> BACKDOOR Win32.Coswid.klk runtime detection (backdoor.rules)
2804876 - ETPRO TROJAN Win32/Coswid.A Checkin (trojan.rules)
We have found several configuration files containing the following values:
d:173.10.48.242/html/AcroRd32.gif
d:66.109.23.156 /temp/smss.gif
d:66.109.23.156 /images/update.gif
d:65.105.157.28 /mama/winupdate.gif
d:69.84.35.39 /netaphex/Acrod32.gif
d:69.84.35.39 /netaphex/Acrod.gif
d:69.84.35.39 /netaphex/update.gif
d:69.84.35.39 /netaphex/google.gif
d:yulepx.com /inc/update.gif
Most of these payloads are the same trojan discussed in our previous analysis and also known as Trojan.Cookies.
Some of the Coswid files we were able to find are:
726ef24b8eff4c4121c73861756fb9a3
a4ba6540520c375875bf46cf8e19cb7d
09fd067b6d944bf111857f6f60b7471e
b5cf509ec072aa281e5bdb1f7c7a36ea
06cd694d383e4951e274878b975b5785
eab862be60fdfe98ce415d38e41889bf
f791d1ad81601aac3e3d32a683189c06