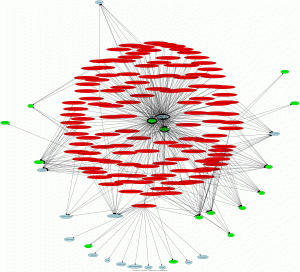
I’m developing a tool to extract interesting information from malware files with the goal of generating a relation graph.
The tool extract api calls and imported symbols of binary files, I?ve make some interesting graph from malware files collected by Nepenthes.
#
# Jaime Blasco - jaime.blasco[at]alienvault.com
#
# Thanks to Jan Goebel
# [Amun - low interaction honeypot]
#
import sys
import os
import re
def start(content, name):
### api
checksbin = {}
checksbin['listen'] = re.compile('\xa4\xad\x2e\xe9', re.S|re.I)
checksbin['bind'] = re.compile('\xa4\x1a\x70\xc7', re.S|re.I)
checksbin['closeSocket'] = re.compile('\xe7\x79\xc6\x79', re.S|re.I)
checksbin['accept'] = re.compile('\xe5\x49\x86\x49', re.S|re.I)
checksbin['LoadLibraryA'] = re.compile('\x8e\x4e\x0e\xec', re.S|re.I)
checksbin['WSASocketA'] = re.compile('\xd9\x09\xf5\xad', re.S|re.I)
checksbin['WSAStartup'] = re.compile('\xCB\xED\xFC\x3B', re.S|re.I)
checksbin['ExitProcess'] = re.compile('\x7e\xd8\xe2\x73', re.S|re.I)
checksbin['CreateProcessA'] = re.compile('\x72\xfe\xb3\x16', re.S|re.I)
checksbin['WaitForSingleObject'] = re.compile('\xad\xd9\x05\xce', re.S|re.I)
checksbin['system'] = re.compile('\x44\x80\xc2\x77', re.S|re.I)
checksbin['SetStdHandle'] = re.compile('\x1d\x20\xe8\x77', re.S|re.I)
checksbin['GetProcAddress'] = re.compile('\xcc\x10\xbe\x77', re.S|re.I)
checksbin['URLDownloadToFileA'] = re.compile('\x36\x1a\x2f\x70', re.S|re.I)
checksbin['connect'] = re.compile('\xec\xf9\xaa\x60', re.S|re.I)
checksbin['socket'] = re.compile('\x6e\x0b\x2f\x49', re.S|re.I)
checksbin['socket2'] = re.compile('\x83\x53\x83\x00', re.S|re.I)
checksbin['send'] = re.compile('\xa4\x19\x70\xe9', re.S|re.I)
checksbin['receive'] = re.compile('\xb6\x19\x18\xe7', re.S|re.I)
checksbin['WinExec'] = re.compile('\x98\xfe\x8a\x0e', re.S|re.I)
checksbin['WriteFile'] = re.compile('\x1f\x79\x0a\e8', re.S|re.I)
checksbin['Unknown (sign for correct decryption)'] = re.compile('\x68\x33\x32\x00\x00\x68\x77\x73\x32\x5F', re.S|re.I)
### plain
checksplain = {}
checksplain['possible windows cmd'] = re.compile('\x63\x6d\x64', re.S|re.I)
checksplain['http address'] = re.compile('\x68\x74\x74\x70\x3a\x2f\x2f', re.S|re.I)
checksplain['ftp address'] = re.compile('\x66\x74\x70\x3a\x2f\x2f', re.S|re.I)
checksplain['tftp.exe'] = re.compile('\x74\x66\x74\x70\x2e\x65\x78\x65', re.S|re.I)
checksplain['WSAStartup'] = re.compile('\x57\x53\x41\x53\x74\x61\x72\x74\x75\x70', re.S|re.I)
checksplain['WSASocketA'] = re.compile('\x57\x53\x41\x53\x6f\x63\x6b\x65\x74\x41', re.S|re.I)
checksplain['GetProcAddress'] = re.compile('\x47\x65\x74\x50\x72\x6f\x63\x41\x64\x64\x72\x65\x73\x73',re.S|re.I)
checksplain['CreateProcessA'] = re.compile('\x43\x72\x65\x61\x74\x65\x50\x72\x6f\x63\x65\x73\x73\x41', re.S|re.I)
checksplain['CreateFileA'] = re.compile('\x43\x72\x65\x61\x74\x65\x46\x69\x6c\x65\x41', re.S|re.I)
### plain imported symbols
checksplainimport = {}
checksplainimport['kernel32'] = re.compile('\x6b\x65\x72\x6e\x65\x6c\x33\x32',re.S|re.I)
checksplainimport['USER32'] = re.compile('\x55\x53\x45\x52\x33\x32',re.S|re.I)
checksplainimport['MSVCR80'] = re.compile('\x4d\x53\x56\x43\x52\x38\x30',re.S|re.I)
checksplainimport['ws2_32'] = re.compile('\x77\x73\x32\x5f\x33\x32',re.S|re.I)
checksplainimport['shell32'] = re.compile('\x73\x68\x65\x6c\x6c\x33\x32',re.S|re.I)
checksplainimport['gdi32'] = re.compile('\x67\x64\x69\x33\x32',re.S|re.I)
checksplainimport['oleaut32'] = re.compile('\x6f\x6c\x65\x61\x75\x74\x33\x32',re.S|re.I)
checksplainimport['advapi32'] = re.compile('\x61\x64\x76\x61\x70\x69\x33\x32',re.S|re.I)
checksplainimport['COMCTL32'] = re.compile('\x43\x4f\x4d\x43\x54\x4c\x33\x32',re.S|re.I)
checksplainimport['wsock32'] = re.compile('\x77\x73\x6f\x63\x6b\x33\x32',re.S|re.I)
checksplainimport['URLMON'] = re.compile('\x55\x52\x4c\x4d\x4f\x4e',re.S|re.I)
checksplainimport['msvcrt'] = re.compile('\x6d\x73\x76\x63\x72\x74',re.S|re.I)
checksplainimport['CRTDLL'] = re.compile('\x43\x52\x54\x44\x4c\x4c',re.S|re.I)
checksplainimport['WININET'] = re.compile('\x57\x49\x4e\x49\x4e\x45\x54',re.S|re.I)
checksplainimport['ntdll'] = re.compile('\x6e\x74\x64\x6c\x6c',re.S|re.I)
keys = checksplain.keys()
for key in keys:
match = checksplain[key].search(content)
if match:
print name + "," + key + ",2"
keys = checksbin.keys()
for key in keys:
match = checksbin[key].search(content)
if match:
print name + "," + key + ",2"
keys = checksplainimport.keys()
for key in keys:
match = checksplainimport[key].search(content)
if match:
print name + "," + key + ",1"
if __name__ == '__main__':
list = os.listdir("binaries/")
for filename in list:
if os.path.exists("binaries/" + filename):
fp = open("binaries/" + filename, 'r')
content = "".join(fp.readlines())
fp.close()
start(content, filename)
The tool generate a CSV files which can be use with Afterglow to simple generate graphs
An output of the tool looks like:
jblasco@alienvault# python functions.py 8a7b16ac83afbc89dd14885eea04fd64,GetProcAddress,2 8a7b16ac83afbc89dd14885eea04fd64,WinExec,2 8a7b16ac83afbc89dd14885eea04fd64,kernel32,1 8a7b16ac83afbc89dd14885eea04fd64,USER32,1 8ee8619debba32adbb40045316559dde,GetProcAddress,2 8ee8619debba32adbb40045316559dde,kernel32,1 8ee8619debba32adbb40045316559dde,ntdll,1 18b3e69b9ba5b0cad8a04d329f34a94c,GetProcAddress,2 18b3e69b9ba5b0cad8a04d329f34a94c,kernel32,1 18b3e69b9ba5b0cad8a04d329f34a94c,USER32,1 6439ad20608e07380428ca0dc7574c41,CreateFileA,2 6439ad20608e07380428ca0dc7574c41,kernel32,1 ... ...
The first column is the md5 of the file, the second is the name of the Api call or imported symbol and the third identyfies:
1: Imported Symbol
2: Api call
The color.properties file I made to generate the graphs looks like:
color.target="lightblue" if ($fields[2]==2) color.target="green" if ($fields[2]==1) color.source="red"