During the previous days, Sophos has reported several attacks related to the Windows XML Core zero-day vulnerability:
- http://nakedsecurity.sophos.com/2012/06/26/hotel-jobs-malware/
- http://nakedsecurity.sophos.com/2012/06/20/aeronautical-state-sponsored-exploit/
- http://nakedsecurity.sophos.com/2012/06/19/unpatched-microsoft-security-vulnerability-exploited/
The CVE-2012-1889 vulnerability is related to Google’s warnings on state-sponsored attacks .
We have recently found another website exploiting this vulnerability that is related to the attacks reported by Sophos. It shares exploit code as well as server infrastructure, meaning that it seems to be the same group is behind all these attacks.
In this case, a Thailand NGO portal related to ASEAN human rights has been hacked and malicious code has been planted on the site, infecting the users that visit the portal.
Every time a page is displayed to the visitor the content is modified and some html is appended to it:

As can be seen, the file news.html is opened with every request and contains the actual exploit code:

The malicious code checks the operating system version, as well as the Java JREs present on the system using the javascript file deployJava.js. Therefore if the system is running Windows XP or the system is running Windows 7 with Java JRE 1.6 the flash file Geoffrey.swf is loaded.
The flash file is in charge of heap spraying and setting up the shellcode that drops the malicious payload on the system.
Another interesting file included is icon.js that is loaded from an external server. It seems this file is included to do reconnaissance obtaining information about the visitor’s system. Once loaded, the javascript code sends the following information to an external server:
- Address
- Cookies
- List of software
- Browser version
- Flash version

The tricky part on this file is that it uses a list of software to check the presence of known files on the system, mainly Antivirus. This method seems to work only with Internet Explorer <= 8.
The function that performs the check is the following.

This technique tries to load an image embedded on the resource section of a Dll/Exe. If the image can be loaded it means the DLL is present and the software is installed on the system.
An example using explorer.exe:
{id: 'Windows Explorer', res: 'res://explorer.exe/#2/#143'}
Exploring the resource section of the executable we can find the resource named 143 within the Bitmap directory

The function uses the following array of files, cut out:

The complete list of applications is:
- Webroot
- Sophos
- Microsoft Security Client
- F-Secure
- BitDefender
- Norton Antivirus
- McAfee Antivirus
- Kingsoft Antivirus
- Avira Antivirus
- Kaspersky Antivirus
- 360 AV
- ESET NOD32
- Trend Micro Internet Security
- Rising Antivirus
- Vmware Player
- Vmware Tools
- Windows Explorer
Due to an error on the malicious server, we were able to get the logs generated by the icon.js requests. Here are some statistics generated based on the data collected by the attackers since June 21st:
- Top countries:

- Top Browsers:

- Operating systems:
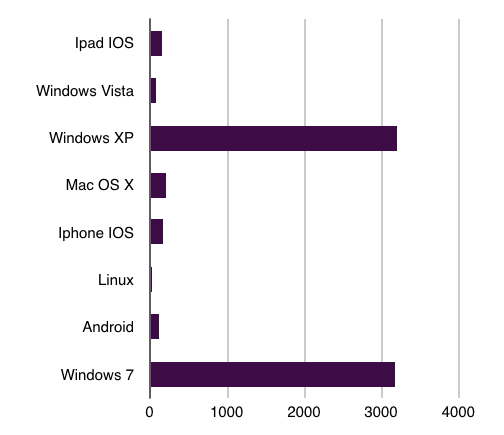
- Antivirus:

Conclusions
As we have previously discussed, the number of state-sponsored incidents involving Southeast Asian Nations have been increasing steeply during the last months, specially those related to non-governmental organizations (NGOs).
We have described a technique used by attackers to perform reconnaissance that gives them information about potential targets, including software and Antivirus versions. This information can be used to perform future attacks on the victims.
Being able to detect the Antivirus used by the victim within the browser opens new options when exploiting systems. Using that technique the attacker can drop different payloads based on the installed Antivirus to evade detection.