MITRE ATT&CK™ (Adversarial Tactics, Techniques and Common Knowledge) is a framework for understanding attackers’ behaviors and actions.
We are pleased to announce that AlienVault USM Anywhere and Open Threat Exchange (OTX) now include MITRE ATT&CK™ information. By mapping alarms to their corresponding ATT&CK techniques, we are assisting in prioritizing analysis work by understanding the context and scope of an attack.
Below we’ve outlined how this new capability can help you investigate two threats - TrickBot and RevengeRat.
Mapping a Trickbot infection with ATT&CK
Trickbot is a malware family that was discovered a few years ago targeting the banking industry, but following some investigations, it is still active and evolving. The malware is usually delivered using attached Office documents via spear-phishing emails.
This particular sample works by running a PowerShell script via command line from the malicious Excel document. The script will load the code that needs to be executed in memory and run the payload. In order to run the payload without being detected, the malware will try to disable and evade anti-malware protection. Once that is done, it will copy itself to another location and will run from there. It also spawns instances of the svchost.exe process to perform several tasks such as downloading config files and injecting into browsers to steal user credentials.
AlienVault USM Anywhere detects and tracks the previous malware behavior and maps all different behaviors to ATT&CK definitions. This provides a clean understanding of the attack’s stage and tactics, and makes the analysis work easier.
Running the sample in our environment we can observe different alarms that USM Anywhere is automatically triggering once the malicious Office document is opened by the user:
- Suspicious Process Created by Microsoft Office Application
- Suspicious Powershell Encoded Command Executed
- Windows Defender Disabled
- Windows Unusual Process Parent
- Tor
- Malicious SSL Certificate
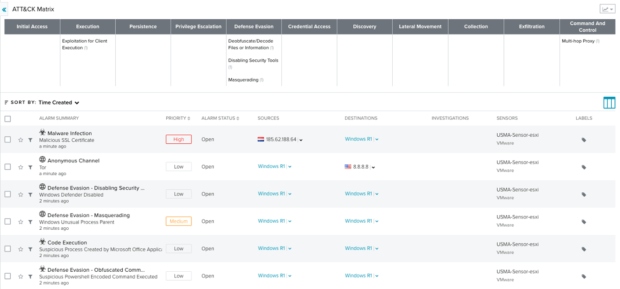
Now it’s possible to see those alarms mapped to the ATT&CK matrix:
As we can observe, the ATT&CK matrix provides visibility of the techniques and tactics that Trickbot uses. Starting with Execution tactics, Defense Evasion mechanisms and finishing with Command and Control activity.
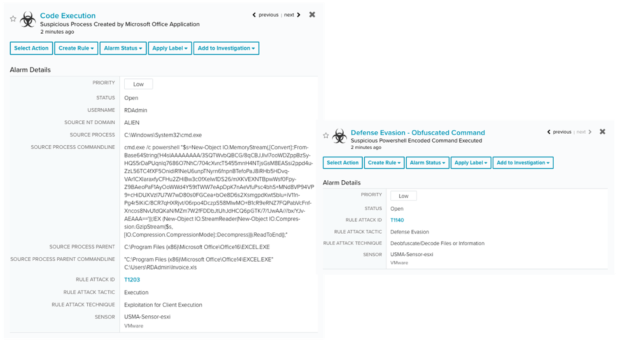
The first alarm in the kill chain is the Suspicious Process Created by Microsoft Office Application. After opening the malicious document, the process EXCEL.EXE creates a new process to run a PowerShell command and load code in memory using the IO.MemoryStream class. We can see how the alarm Suspicious Powershell Encoded Command Executed detected the malicious activity and the encoded command trying to evade detection.
Before injecting into other processes, the malware tries to disable the anti-malware protection mechanism to evade endpoint detections. In this case, we detect how it tries to stop the Windows Defender service by triggering the alarm Windows Defender Disabled.
The next step performed by Trickbot is to copy itself to another directory and run again. Some new instances of svchost.exe process are started, but as you can see, the parent of that process is not the one that Windows normally uses in the process tree.
We can see another alarm for that behavior indicating that the masquerading technique T1036 is being used:
In the last step of the kill chain, the Trickbot malware tries to contact a command and control server. Network signatures matched the SSL domain used by this family and alerted it as Malicious SSL Certificate.
Network activity has also detected a DNS query for a TOR domain, commonly used for anonymity and multi-hop proxy connections:
Revenge RAT
The Revenge Remote Access Trojan is a popular publicly available remote access trojan. Revenge RAT allows attackers to capture personal information, monitor user behavior using keylogger and webcam functionalities, stealing data and even dropping new malware in the infected system. Malspam delivers Revenge RAT via malicious Office documents while the infrastructure uses blog-publishing services like blogpost.com to host the malicious scripts that will be executed by the Office document.
Once the system is infected, this malware uses persistence mechanisms such as scheduled tasks to guarantee the continued execution and beacon functionality to command and control servers. The analyzed variant of Revenge RAT uses local scheduled tasks with code execution to download the content from remote services.
The following USM Anywhere alarms are triggered when the Office document is opened by the user:
- Suspicious Process Created by Microsoft Office Application
- Suspicious Process Created by mshta.exe
- Network Activity From mshta
- Windows Scheduled Job Created
- Taskkill killing Antivirus process
- Malware Beaconing to C&C
- Remote Access Trojan
And we can also see it with the ATT&CK matrix:
As we can see above, the RAT behavior previously detailed has generated many alarms which are all mapped to the ATT&CK framework. Now, it is simple to recognize the attack pattern, from Execution to the Command and Control beaconing.
First, the alarm Suspicious Process Created by Microsoft Office Application detected that the EXCEL.EXE process was executing mshta.exe as a child process. Then we can see Network Activity From mshta to www.bitly.com in order to download malicious content:
As a result of that activity, two alarms of Suspicious Process Created by mshta.exe were triggered. One of them detects when the code is loaded in memory using the PowerShell Reflection. Assembly class and the other one detects when the payload tries to kill the antivirus software which triggers Taskkill killing Antivirus process alarm.
The activity also generates an alarm for Windows Scheduled Job Created. If we inspect the event linked to the alarm we can see a detailed view of the scheduled task created in the system for execution and persistence and how it’s mapped as ATT&CK technique T1053.
Finally, after covering the Execution, Persistence and Defense Evasion tactics, it is also possible to review the command and control activity performed by the malware.
Using network detections, we can easily recognize that the system was infected by a Remote Access Trojan named Revenge-RAT and there is another Malware Beaconing to C&C alarm for the same malware family indicating the system is communicating with the attacker infrastructure.


.png)
.png)
.png)
.png)
.png)
.png)
.png)