2018 seems to be a time for highly profitable cryptominers that spread over SMB file-shares. Following my analysis on ZombieBoy in July, I found a new malware sample that I’m calling MadoMiner. With the help of Chris Doman, I was able to analyze it to discover that it uses techniques similar to ZombieBoy, because it hijacks Zombieboy’s CPUINFO.exe.
However, MadoMiner is much, much, larger, in terms of:
- The size of the malware;
- The amount of systems infected; and
- Total profit gained by the attackers.
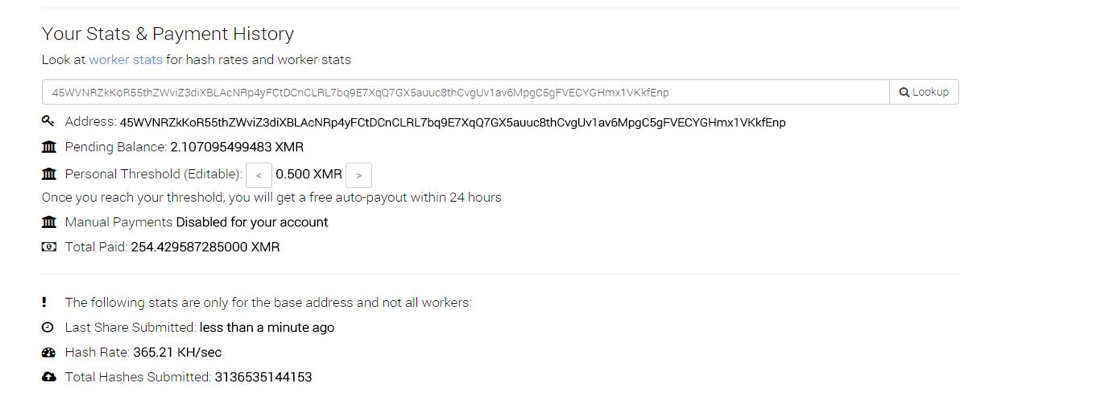
The previously analysed ZombieBoy was earning around $750 a month, while mining at its maximum power. MadoMiner, on the other hand, is earning around $6015 a month, while only mining at 50% power:
Malware Analysis
An overview of the Install module is below. Depending on the victim’s architecture, obtained from CPUInfo.exe, either x86.dll or x64.dll is installed:
X86.dll and x64.dll are virtually identical just one is specifically for x86-x64 OS architecture and one is specifically for x86 OS architecture.
Domains
MadoMiner appears to use two different servers to distribute payloads for each module.
- http://da[dot]alibuf.com:3/
- http://bmw[dot]hobuff.info:3/
In addition, in Mask.exe, the second module, here are some identified mining servers used by MadoMiner:
- http://gle[dot]freebuf.info
- http://etc[dot]freebuf.info
- http://xmr[dot]freebuf.info
- http://xt[dot]freebuf.info
- http://boy[dot]freebuf.info
- http://liang[dot]alibuf.com
- http://dns[dot]alibuf.com
- http://x[dot]alibuf.com
Exploits
During the execution of the Install module, MadoMiner makes use of several exploits:
- CVE-2017-9073, RDP vulnerability on Windows XP and Windows Server 2003
- CVE-2017-0143, SMB exploit
- CVE-2017-0146, SMB exploit
Installation
MadoMiner begins on a victim’s computer as a DLL installed by the EternalBlue/DoublePulsar exploits. Depending on OS architecture, you’ll either find x86.dll or x64.dll installed on your computer. Both are basically the same, just adjusted for operating system.
Just like ZombieBoy, MadoMiner makes use of a heavily modified version of ZombieBoyTools in order to install its DLL. The reason for this it seems, is that the CPUInfo.exe dropped by the Install module of MadoMiner appears to be the same CPUInfo.exe dropped by an earlier version of 64.exe, a module from ZombieBoy (similar to current day CPUInfo in ZombieBoy, sans embedded miner and anti-VM guards).
In fact, if CPUInfo.exe in MadoMiner is ran without the surrounding Install module, it will attempt to communicate with ZombieBoy’s servers and ultimately install ZombieBoy
Packet showing malware communicating to ca[dot]posthash.org:443
![Packet showing malware communicating to ca[dot]posthash.org:443](https://cdn-cybersecurity.att.com/images/uploads/blog/MadoMiner_Communicating.png)
Setup
Once either x86.dll or x64.dll is successfully installed and executed on a victim’s computer, several actions are performed. First, 2 UPX packed modules are downloaded from da[dot]alibuf.info, known locally as Install.exe and Mask.exe(for x86.dll, 445.exe & mado.exe; for x64.dll, mask.exe & dst.exe). These modules are both executed concurrently and are in charge of all functionality of the malware.
Install.exe
Install.exe is a curious module. Installed to ‘C:\%Windows Directory%\Install.exe’ from either http://da[dot]alibuf.com:3/445.exe or http://da[dot]alibuf.com:3/mask.exe, Install.exe seems to be in charge of spreading MadoMiner to more systems.
MadoMiner spreads to other systems by hijacking ZombieBoy’s CPUInfo.exe. Install.exe consists of a couple batch scripts for persistence and evasion, a dropper, CPUInfo.exe, and 2 dlls, x86.dll and x64.dll. What MadoMiner does with these dll’s and CPUInfo.exe is particularly unique. CPUInfo.exe on its own drops over 70+ files to IIS, including the 2 dll’s that it installs on computers, x86.dll and x64.dll. In its base form, these dll’s contain the ZombieBoy installation. MadoMiner writes over CPUInfo.exe’s x86.dll and x64.dll with its own dlls. When CPUInfo.exe goes to install the dlls, it installs MadoMiner’s dlls instead!
Install.exe also runs 2 tasks for persistence, RavTask and GooglePingInConfigs. The first task, RavTask, and runs every 4 hours, indefinitely. RavTask runs a batch file dropped by Install.exe called Free.bat that will be discussed more below. GooglePingInConfigs’ job is simple; all it has to do is run CPUInfo.exe at startup.
The commands for starting Ravtask and GooglePingInConfigs are as follows:
‘@schtasks /create /sc minute /mo 240 /tn “RavTask /tr “C:\windows\IIS\free.bat” /ru “system” /f’
‘@schtasks /create /tn “GooglePinginConfigs” /tr “C:\Windows\IIS\CPUInfo.exe” /sc onstart /ru “system” /f’
Install.exe batch scripts
Install.exe has 3 batch scripts that it uses in its runthrough. Free.bat, DemO.bat, DemC.bat. Dem(open) or Demo.bat is used at the beginning, when Install.exe is first launched, Free.bat is used by RavTask, and Dem(close) or DemC.bat is used at the end of install.exe’s runthrough.
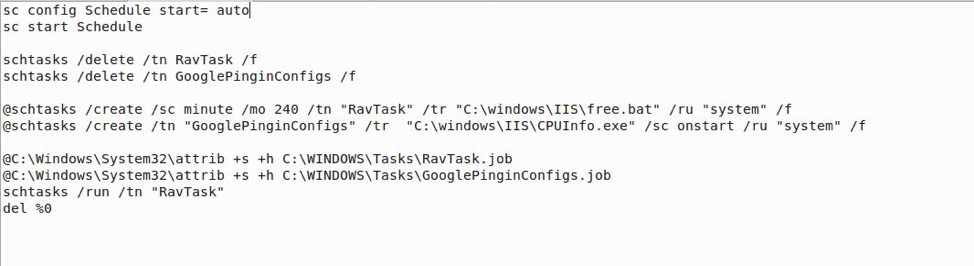
DemO first sets a task named Schedule to autorun. Next, it deletes and then recreates the 2 tasks used for Persistence --- Ravtask and GooglePingInConfigs. Finally, access is removed from RavTask and GooglePingInConfigs, RavTask is run, and then the script deletes itself.
DemO.bat
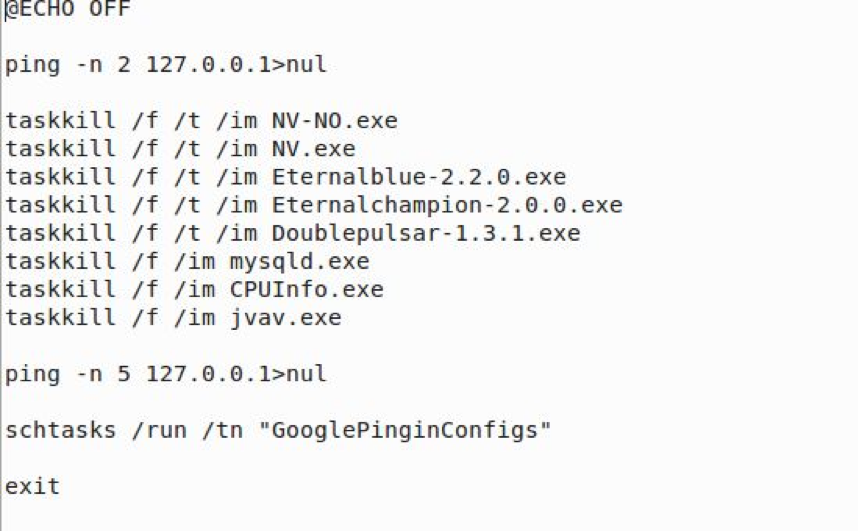
Free.bat, which is executed by RavTask every 4 hours, is a small batch script with a fairly important job. First, Free.bat ends any of the programs/dlls used by CPUInfo.exe including DoublePulsar and EternalBlue(This is done to guarantee a clean start). Next, Free.bat runs GooglePingInConfigs (which will execute CPUInfo.exe). In addition, Free.bat also checks to make sure the NIC is up by pinging it.
Free.bat
Finally, DemC is ran to hide the malware and appears to be a partial wiper module. For example, if the malware detects a VM, DemC is ran. DemC closes a lot of open processes, in addition to deleting some of the modules dropped by MadoMiner. Also, DemC deletes all executables in the ProgramData folder.
x64 and x86 - The Hijacking Dlls
x64.dll and x86.dll start their journey packed into Install.exe. When Install.exe is ran however, they are dropped in C:\Windows\IIS with CPUInfo.exe, however when attempting to access either x86.dll or x64.dll, access is denied. This is so that CPUInfo.exe does not overwrite x86.dll and x64.dll while executing.
As for the dll’s themselves, they each have a check to determine that you are indeed their respective OS type. If so, they download their specific malware (mask.exe and dst.exe for x64.dll;445.exe and mado.exe for x86.dll) from their download server and run WinExec to run the applications.
x86.dll urldown function
CPUInfo.exe - The Hijacked malware
CPUInfo.exe is very similar to the CPUInfo.exe used by ZombieBoy. In fact, I believe it to be an earlier version of CPUInfo.exe before ZombieBoy packed the miner with CPUInfo.exe and made it impossible to run on a VM(Running CPUInfo.exe without running Install.exe first causes ZombieBoy to be dropped). Just like in ZombieBoy, CPUInfo.exe drops over 70+ files into C:\Windows\IIS. These files contain the exploits used, ZombieBoyTools, the web scanner, a copy of CPUInfo.exe, the 2 dlls used to spread (x86.dll and x64.dll).
In addition, CPUInfo.exe appears to have some keylogger functionalities, just like in ZombieBoy. A static strings analysis shows that CPUInfo.exe imports a lot of commands used for keylogging, such as SetWindowHookEx and GetKeyState.
CPUInfo.exe is the main payload of Install.exe and all of the other files in Install.exe seem to support CPUInfo in one way or another. As we’ve seen, x64.dll and x86.dll are both used to spread MadoMiner, but how it all comes together is quite interesting.
CPUInfo.exe - Runthrough
When CPUInfo first launches, it connects to ip[dot]3322.net in order to obtain the public IP netrange. Next, CPUInfo.exe obtains regional info about the host using www[dot]ip138.com. As this is happening, CPUInfo.exe is also unpacking itself, dropping a total of 3 exploits, a web scanner, the batch scripts for scanning the files, as well as necessary dll’s and other misc files adding up to over 70 files into C:\windows\IIS.
After dropping the necessary files and obtaining the IP netrange, CPUInfo.exe begins to use the lightweight TCP web scanner, WinEggDrop, in order to scan all private IP’s from XXX.XXX.0.0 - XXX.XXX.255.255 to identify an IP with port 445 open. If said IP is located, this ip is extracted and saved into com.dll for future use and then a heavily modified version of ZombieBoyTools is ran. This version of ZombieBoyTools identifies the OS architecture and then, using either EternalBlue/DouplePulsar or EternalChampion/DoublePulsar, installs and executes either x86.dll or x64.dll(after extracting the saved IPs from com.dll). This starts the infection process on a new host, running and downloading the Install and Mask modules.
Batch script to scan Private IP’s.
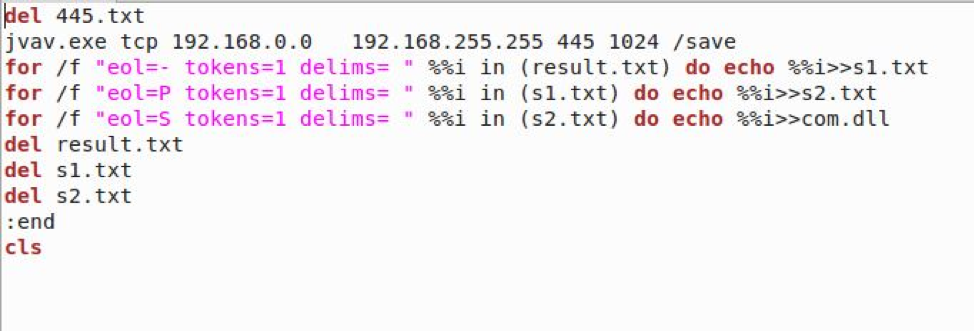
After finishing the private IP infection stage, CPUInfo.exe then moves onto the private IP infection stage, which is nearly identical to the public IP infection stage, except that CPUInfo.exe does not need to obtain the private IP again, since the value is already saved in memory. When scanning the private IP, it also follows the same scan pattern as the public IP scan.
Avoidance and Removal - Install.exe
Install.exe uses several NSA exploits, just like ZombieBoy. In fact, if your computer is patched for ZombieBoy, you’ll also be patched for MadoMiner. Specifically, the patch that will protect you from MadoMiner is MS17-010. In addition, you’ll want to block traffic to the following web servers (ip’s are subject to change unfortunately, so I’ve provided the alphanumeric address instead):
- http://alibuf[dot]com:3/ (distribution server)
- http://hobuff[dot]info:3/ (Distribution server)
- http://freebuf.info (Mining server)
While I always advocate avoidance as the best practice sometimes that just isn’t possible. As always, if you become infected by MadoMiner, do not panic. However, you should backup any important files now, if you haven't already. MadoMiner has a nasty trap that when CPUInfo closes, it sometimes triggers demC.bat, which is Install.exe’s wiper module, in which it deletes any suspicious files for anti-analysis.
The key deleted/changed files/settings are:
- Remove ownership from ftp.exe
- Delete host file and then remake it, saving “127.0.0.1 localhost” to it
- Flush dns
- Delete several services that may be from past campaigns.
- Delete all executable files in C:\%ProgramData%\
- Make C:\Progra~1\dll
- Stop all running modules from MadoMiner
- In addition, MadoMiner appears to take advantage of the IFEO. Anytime the modules are executed, taskkill.exe /f is ran as a debugger, killing the module
In addition, unless you use port 445, all traffic into and out of it should be blocked.
While I am including a chart with all of the installed modules of MadoMiner in total, the amount of files installed by both are too large to fit into one analysis, so in this part I will cover in depth the steps to remove Install.exe.
Note: This requires safe mode! One of CPUInfo.exe’s batch files will delete a lot of files in ProgramData, in addition to other important files on CPUInfo.exe’s close. Be careful, and back up any important files before attempting this.
Since MadoMiner installs 2 jobs, those jobs will need to be deleted from either HKLM\Software\Microsoft\Windows NT\CurrentVersion\Schedule\Taskcache\Tasks or HKLM\Software\Microsoft\Windows NT\CurrentVersion\Schedule\Taskcache\Tree. The jobs are known as RavTask and GooglePingInConfigs.
In addition, if you open Task Scheduler and go to the scheduled tasks, you should delete the “action” field from the jobs, so that they are rendered null and void.
Also, you should delete DemC.bat and DemO.bat from C:\%WindowsDirectory%\ along with Install.exe and \IIS. You should then be able to run your favorite Antivirus software in order to scan for any remaining artifacts.
Detection
Yara Rule
rule MadoMiner_Install
{
meta:
author = “quinnjp13@gmail.com
reference = "https://www.virustotal.com/#/file/1a90dbc1db60930614a1e78b9ecfff4d772d48c4d08e9c66986b695316253062/"
strings:
$string_1 = "d09f2340818511d396f6aaf844c7e325" nocase wide ascii
$string_2 = "tem.vbs" nocase wide ascii
$string_3 = 'taskkill /f /t /im CPUInfo.exe' nocase wide ascii
$string_4 = '@taskkill /f /t /im svshostr.exe' nocase wide ascii
$string_5 = '@Wmic Process Where "Name='cmd.exe' And ExecutablePath='C:\\ProgramData\\Microsoft\\Natihial\\cmd.exe'" Call Terminate' nocase wide ascii
condition:
all of them
}
rule MadoMiner_Install_CpuInfo
{
meta:
author = “quinnjp13@gmail.com
reference = “https://www.virustotal.com/#/file/9b5223806c1662084d0cdaf98b040d4b205c7dd8ad2a997e7debc8287ea1825f/detection”
Strings:
$string_1 = “epykkfnx” nocase wide ascii
$string_2 = "ahwsresh" nocase wide ascii
Condition:
all of them
}
rule MadoMiner_Install_x64dll
{
meta:
author = “quinnjp13@gmail.com
reference = “https://www.virustotal.com/#/file/2480b6faef77e7446bae9630a7bcb403c5aa94e97ccb9f28db83e8476ae57093/detection”
Strings:
$string_1 = "http://da.alibuf.com:3/dst.exe" nocase wide ascii
$string_2 = "http://da.alibuf.com:3/mask.exe" nocase wide ascii
Condition:
All of them
}
rule MadoMiner_Install_x86dll
{
meta:
author = “quinnjp13@gmail.com
reference = “https://www.virustotal.com/#/file/f534fcd5a3648c77811f2986cc6da9460ad7d913f1c3f0829656bb0e6c2628bb/detection”
strings:
$string_1 = “http://da.alibuf.com:3/mado.exe” nocase wide ascii
$string_2 = “http://da.alibuf.com:3/445.exe” nocase wide ascii
condition: all of them
}
Indicators of Compromise
|
Samples |
MD5 |
Size |
IP |
IOC |
|
x86.dll[first x86 installed dll] |
69833a3ecc52f57a02656d46e1799dcc |
70.7 KB |
http://da[dot]alibuf.com:3/ |
- |
|
x64.dll[first x64 installed dll] |
e9c6bf0de42aa2449f1ed4bbb50ddcd6 |
39.4 KB |
http://da[dot]alibuf.com:3/ |
- |
|
445.exe [x86 Install.exe] |
3c720a55b043564313000a4efb1d85c0 |
6.4 MB |
Ip[dot]3322.net www[dot]ip138.com |
C:\Windows\Install.exe C:\Windows\IIS\* C:\Windows\DemO.bat C:\Windows\DemC.Bat |
|
Mado.exe [ x86 Mask.exe] |
4ae31911c1ef2ca4eded1fdbaa2c7a49 |
741.0 KB |
gle[dot]frebuf.info:80 Bmw[dot]hobuff.info:3 |
“C:\Windows\Fonts\svchost.exe” “C:\Windows\Fonts\rundllhost.exe” “HKLM\SYSTEM\CurrentControlSet\Services\EventLog” “HKLM\SYSTEM\CurrentControlSet\Services\ServiceMaims” “HKLM\SYSTEM\CurrentControlSet\Services\ServiceMais” |
|
Mask.exe [ x64 Install.exe] |
d8470f5c12f5a5fee89de4d4c425d614 |
1.3 MB |
Ip[dot]3322.net www[dot]ip138.com |
C:\Windows\Install.exe C:\Windows\IIS C:\Windows\DemO.bat C:\Windows\DemC.Bat |
|
Dst.exe [ x64 Mask.exe] |
4ae31911c1ef2ca4eded1fdbaa2c7a49 |
741.1kb |
gle[dot]frebuf.info:80 BMW[dot]hobuff.info:3/ |
“C:\Windows\Fonts\svchost.exe” “HKLM\SYSTEM\CurrentControlSet\Services\EventLog” “HKLM\SYSTEM\CurrentControlSet\Services\ServiceMaims” “HKLM\SYSTEM\CurrentControlSet\Services\ServiceMais” |
|
CPUInfo.exe |
2df2d6d9db08558e88f1636ed2acc146 |
5.7 MB |
Ip[dot]3322.net www[dot]ip138.com |
C:\Windows\IIS\CPUInfo.exe |
|
Sogou.exe [ 2nd module file] |
4a14e7fb274462e844b5595210350400 |
4.6 MB |
Ip[dot]3322.net www[dot]ip138.com |
C:\Windows\Installer\conhost.exe |
|
360Safe.exe [2nd Module File] |
ce606d80b44ea2aae81056b9088ba1e4 |
3.6 MB |
gle[dot]freebuf.info:80 |
C:\Windows\Fonts\rundllhost.exe |