This blog was jointly written by Fernando Martinez Sidera and Ofer Caspi, AT&T Alien Labs threat intelligence researchers.
Executive summary
AdLoad malware is still infecting Mac systems years after its first appearance in 2017. AdLoad, a package bundler, has been observed delivering a wide range of payloads throughout its existence. During AT&T Alien Labs’ investigation of its most recent payload, it was discovered that the most common component dropped by AdLoad during the past year has been a proxy application turning MacOS AdLoad victims into a giant, residential proxy botnet.
Key takeaways:
- AdLoad malware is still present and infecting systems, with a previously unreported payload.
- At least 150 samples have been observed in the wild during the last year.
- AT&T Alien Labs has observed thousands of IPs behaving as proxy exit nodes in a manner similar to AdLoad infected systems. This behavior could indicate that thousands of Mac systems have been hijacked to act as proxy exit nodes.
- The samples analyzed in this blog are unique to MacOS, but Windows samples have also been observed in the wild.
Analysis
AdLoad is one of several widespread adware and bundleware loaders currently impacting macOS. The OSX malware has been present since 2017, with big campaigns in the last two years as reported by SentinelOne in 2021 and Microsoft in 2022. As stated in Microsoft’s report on UpdateAgent, a malware delivering AdLoad through drive-by compromise, AdLoad redirected users’ traffic through the adware operators’ servers, injecting advertisements and promotions into webpages and search results with a Person-in-The-Middle (PiTM) attack.
These two previous campaigns, together with the campaign described in this blog, support the theory that AdLoad could be running a pay-per-Install campaign in the infected systems.
- The main purpose of the malware has always been to act as a downloader for subsequent payloads.
- It has been identified delivering a wide range of payloads (adware, bundleware, PiTM, backdoors, proxy applications, etc.) every few months to a year, sometimes conveying different payloads depending on the system settings such as geolocation, device make and model, operating system version, or language settings, as reported by SentinelOne.
- In all observed samples, regardless of payload, they report an Adload server during execution on the victim’s system.
- This beacon (analyzed later in Figure 3 & 4) includes system information in the user agent and the body, without any relevant response aside from a 200 HTTP response code.
- This activity probably represents AdLoad's method of keeping count of the number of infected systems, supporting the pay-per-Install scheme.
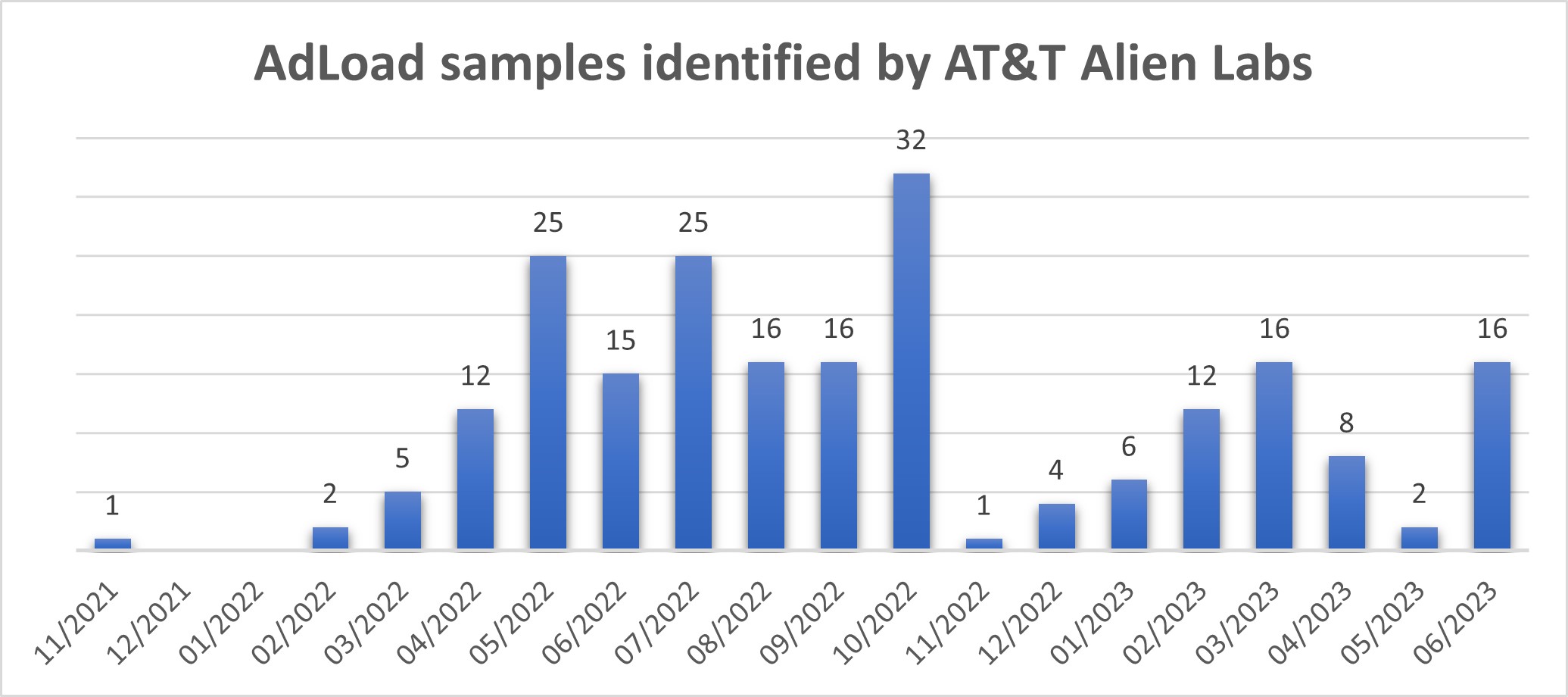
AT&T Alien Labs™ has observed similar activity in our threat analysis systems throughout the last year, with the AdLoad malware being installed in the infected systems. However, Alien Labs is now observing a previously unreported payload being delivered to the victims. The payload corresponds to a proxy application, converting its targets into proxy exit nodes after infection. As seen in Figure 1, the threat actors behind this campaign have been very active since the beginning of 2022.
Figure 1. Histogram of AdLoad samples identified by Alien Labs.
The vast number of samples in the wild have consequently led to many devices becoming infected. Alien Labs has identified over 10,000 IPs reaching out to the proxy servers each week that have the potential to be proxy exit nodes. It is unclear if all these systems have been infected or are voluntarily offering their systems as proxies, but it could be indicative of a bigger infection globally.
The intentions behind the users of this botnet for residential proxy systems is still unclear, but so far it has already been detected delivering SPAM campaigns. A campaign was suffered by the University of Illinois, who had to release an internal alert to notify their students of this thread.
Figure 2. University of Illinois alert at https://answers.uillinois.edu/illinois/page.php?id=120871.
This blog will focus on a sample of AdLoad, which AT&T Alien Labs observed in the wild during the month of June: 6587e61a8a7edb312da5798ffccf4a5ef227d3834389993b4df3ef0b173443dc. This sample was named “app_assistant”. Together with ‘main_helper’ or ‘mh’ are the most common filenames observed for this malware.
The sample initiates the execution with a system profiler. The system profiler pulls system information focusing in on the UUID (Universally Unique Identifier) that can be used later to identify the system with the Command and Control (C&C) on the proxy servers.
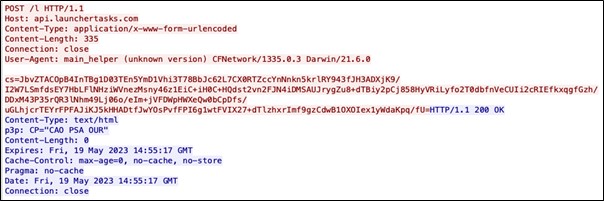
It then reaches out to an AdLoad server to report the infection. The URL is hardcoded in the sample. Alien Labs has observed two different patterns thus far:
Pattern 1 includes:
- POST request to a URL with path “/l”.
- Host with api. Subdomain.
- Content Type is “application/x-www-form-urlencoded".
- The body starts with “cs=” and is followed by around 300 base64 characters.
This behavior had already been observed in the wild and is detected by ET (Emerging Threats) with a public rule attributing the activity to OSX/SHLAYER (Rule in the appendix).
Figure 3: Example from Alien Labs of network traffic of sample 54efc69cb6ee7fde00c0320202371dcdad127d0e7c8babce4659be8230d81a81.
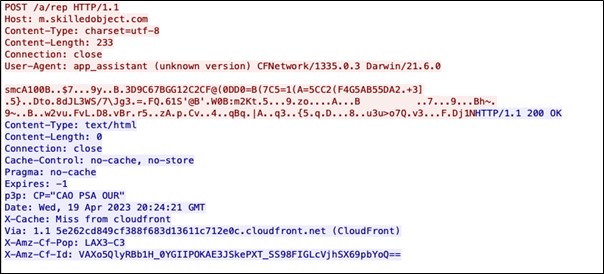
Pattern 2 includes:
- POST request to a URL with path “/a/rep”
- Host with m. subdomain
- Content Type is charset=utf-8
- The body starts with “smc” and is followed by encrypted data.
No public rules were identified for this behavior as of the publishing of this blog, however Alien Labs has provided a rule in the appendix.
In both cases, the User Agent is formed by the filename of the executed file followed by “(unknown version) CFNetwork/$version” plus the Darwin version number.
Figure 4: Example from Alien Labs: network traffic of sample 6587e61a8a7edb312da5798ffccf4a5ef227d3834389993b4df3ef0b173443dc.
After beaconing to the AdLoad server, the sample reaches out to a different domain, usually vpnservices[.]live or upgrader[.]live, appearing to be a proxy server’s C&C. The request carries as a parameter the UUID of the infected machine among other encoded parameters. This request responds with a link of the file to download, usually in digitaloceanspaces[.]com. It also includes the environment to use and the version number of the payload.
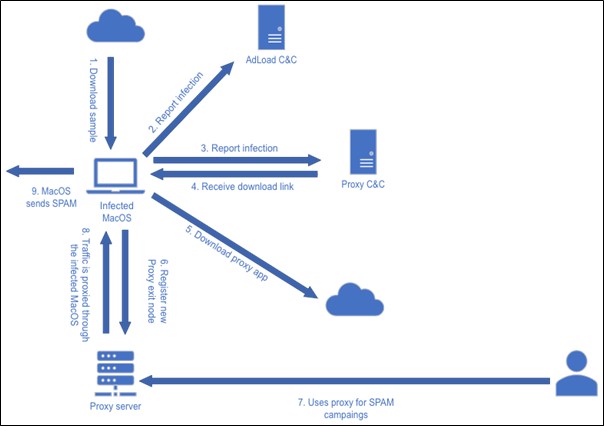
Figure 5 summarizes the different connections Alien Labs has observed as of the publishing of this article (steps 1-5), and the activity we will describe next (steps 5-8).
Figure 5: Infection process as analyzed by Alien Labs.
Attack chain, Steps 5-8
- Once the malware downloads the proxy app, it is unzipped with a password, and xattr -rd is executed on the files to remove the quarantine attribute from them. This bypasses Gatekeeper’s security.
- The existing files are copied to ‘/Users/$user/Library/Application Support/$randomstring’. Any unnecessary files placed in the system, the /tmp directory, and the original zip file are deleted.
- At this point, the newly generated folder under Application Support has two files: the first is a version control named ‘pcyx.ver’ and the second contains the proxy application, usually named ‘helper’ or ‘main’. If the proxy application is already running, the malware kills it, and then executes it in the background. During its execution, AdLoad gains persistence by installing itself as a Launch Agent with organization name usually formed by org.[random long string].plist, which points at the proxy application executable in the Application Support folder.
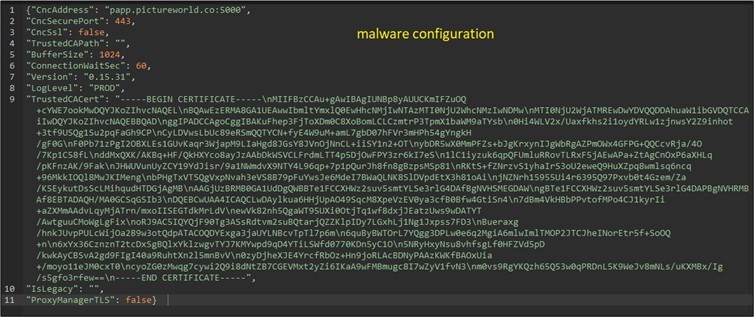
- The application is already running, and the hosts start operating as a proxy server. Its initial configuration is usually hardcoded (figure 6), but it can be modified through the previous request to the proxy C&C, modifying the used domain, port, environment, etc. The communication with proxy servers usually occurs over port 7001, but it has also been seen over port 7000 and 7002, probably alternatives in case 7001 is taken.
Figure 6: As observed by Alien Labs: the malware configuration includes C&C address, certificate, malware version and more.
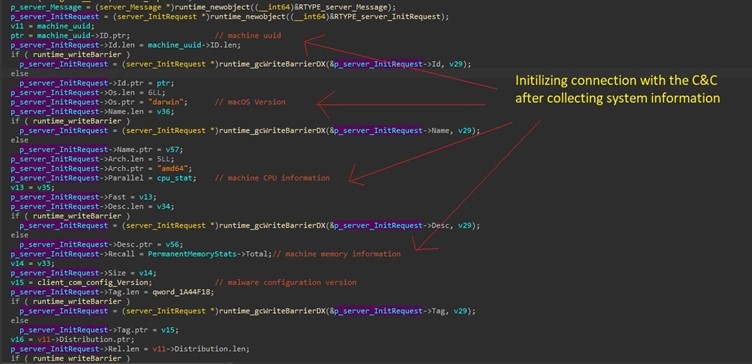
- As the application runs, its first action is to beacon system information and status to the proxy server. It sends a registration message to its C&C after collecting the machine’s information. This data includes macOS version, hardware stats like CPU, memory, and battery status. Additionally, it extracts the machine’s UUID, labeled as “peer_id”, that is used as identifier of the machine with the C&C (figure 7).
- After registration with its C&C, the malware receives the proxy manager server to which it forwards proxy requests.
Figure 7: Collecting system information before registering as new peer.
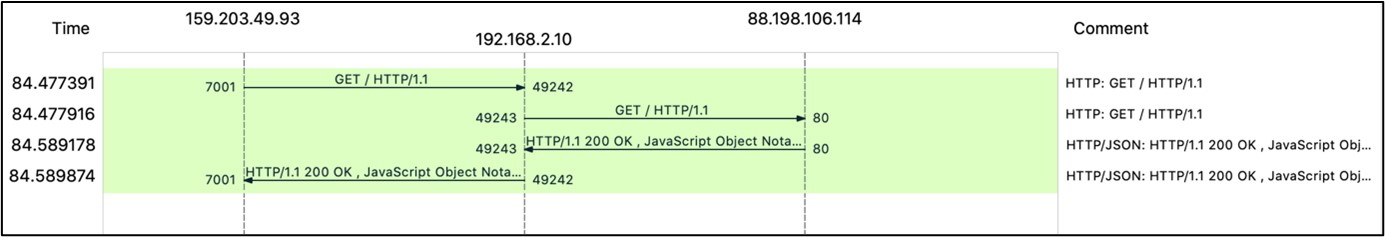
Many of the proxy requests immediately issued after an infection appear to be testing queries, i.e., iplookups or access to streaming services like Netflix, HBO or Disney, from specific locations. Figure 8 shows the beacon and the response from the server, together with the request for an IP Lookup, which arrived at the infected system through port 7001.
Figure 9 shows more clearly how the IP Lookup is forwarded to its actual destination and the received response is sent back to the proxy server.
Figure 8: Beacon and and IPlookup as observed by Alien Labs, d94f62ec4b6ffcec35d5e639d02a52ce226629a5eb3e2a7190174ea8d3b40b5b.
Figure 9: Proxy flow, as observed by Alien Labs, d94f62ec4b6ffcec35d5e639d02a52ce226629a5eb3e2a7190174ea8d3b40b5b.
The beacon message shown in figure 8 is sent every few seconds to get further instructions from the C&C. This includes requests for updated hardware information to check if the machine may be running into issues soon and should not be loaded as proxy (low battery or high CPU usage) (Figure 10).
Figure 10: Pinging C&C for further instructions, observed by Alien Labs.
Alien Labs has identified several domains as proxy server nodes that were relaying the proxy requests to the infected systems. These domains all had generic randomly generated names, like bapp.pictureworld[.]co and were hosted in usually reliable cloud services, like Amazon or Oracle. However, they appeared to only be used as DNS resolvers, since those IPs happened to all resolve to a private company domain around the time of infection. The company name also showed up in the certificates of some of these generic domains.
Based on the above information, a small business selling proxy services appears to be behind the proxy activity. The list of prices published in this private company webpage, does include residential IP proxys as an offered service.
In addition to the Mac samples analyzed in this blog, Alien Labs has also identified other Windows samples replicating the behavior just explained. These Windows samples also end up acting as proxies through the known ports 7000, 7001 and 7002, with traffic coming from the same domains. AT&T Alien Labs will be releasing a new blog in the upcoming weeks with that analysis.
Recommended actions
To remove AdLoad samples from the system:
- AdLoad samples can be identified with the Yara rule included in the Appendix, originally created by SentinelOne in a previous AdLoad report.
- Analyze any system matching suricata rules 4002758 and 2038612.
To remove the proxy application from the system:
- Review ‘/Users/X/Library/Application Support/’ and look for a folder named with a string of over 20 randomly generated characters, which contains files like: main, helper, pcyx.ver; and are currently running in your system in the background.
- Understand the need for all the existing Launch Agents plists in /Library/LaunchAgents/. Especially looking for another long string of random characters, and identify the existing agents, deleting the unnecessary ones.
- Analyze any systems communicating though port 7000, 7001 or 7002 to suspicious IPs (or matching suricata rules 4002756 and 4002757).
Conclusion
The pervasive nature of AdLoad potentially infecting thousands of devices worldwide — indicates that users of MacOS devices are a lucrative target for the adversaries behind this malware and are being tricked to download and install unwanted applications. The underreporting of MacOS based threats may lead users to a false sense of security and underscores that any popular operating system can become a target for skilled adversaries.
AT&T Alien Labs is not aware whether the private company relaying the proxy requests is actively infecting the systems, or they are buying what they believe to be legitimate systems. However, their proxy servers are accessing these systems and selling a similar service to their clients. Buyers are leveraging the benefits of a residential proxy botnet: anonymity, wide geolocation availability and high IP rotation; to deliver SPAM campaigns through the last year.
Detection methods
The following associated detection methods are in use by Alien Labs. They can be used by readers to tune or deploy detections in their own environments or for aiding additional research.
|
SURICATA IDS SIGNATURES |
|
alert tcp $HOME_NET any -> $EXTERNAL_NET [7000:7002] (msg:"AV TROJAN AdLoad Proxy Node Beacon"; flow:to_server,established; content:"|7B 22|peer_id|22 3A|"; offset:0; depth:11; content:"|22 2C 22|connect_version|22|"; distance:0; content:"|22|action|22|"; distance:0; classtype:bad-unknown; sid:4002756; rev:2;) |
|
alert tcp $EXTERNAL_NET [7000:7002] -> $HOME_NET any (msg:"AV TROJAN AdLoad Proxy Node Response"; flow:established; content:"|7B 22|result|22 3A|"; offset:0; depth:10; content:"|22|error|22 3A 22|"; distance:0; content:"|22 2C 22|action|22 3A 22|result|22|"; distance:0; content:"|22|uuid4|22|"; distance:0; content:"|22|version|22|"; distance:0; classtype:bad-unknown; sid:4002757; rev:2;) |
|
alert http $HOME_NET any -> $EXTERNAL_NET any (msg:"AV TROJAN OSX AdLoad CnC Beacon"; flow:established,to_server; content:"POST"; http_method; content:"/a/rep"; http_uri; depth:6; isdataat:!1,relative; content:"m."; depth:2; http_host; content:"|20 28|unknown|20|version|29 20|CFNetwork|2f|"; http_user_agent; fast_pattern; content:"charset=utf-8"; http_content_type; pkt_data; content:"smc"; http_client_body; depth:3; content:"$"; distance:7; within:1; http_client_body; isdataat:200,relative; threshold:type limit, count 1, seconds 600, track by_dst; classtype:trojan-activity; sid:4002758; rev:1;) |
|
alert http $HOME_NET any -> $EXTERNAL_NET any (msg:"ET TROJAN OSX/SHLAYER CnC Activity M2"; flow:established,to_server; content:"POST"; http_method; content:"/l"; http_uri; depth:2; isdataat:!1,relative; content:"|20 28|unknown|20|version|29 20|CFNetwork|2f|"; http_user_agent; fast_pattern; content:"cs="; http_client_body; depth:3; pcre:"/^(?:[A-Za-z0-9+/]{4})*(?:[A-Za-z0-9+/]{2}==|[A-Za-z0-9+/]{3}=|[A-Za-z0-9+/]{4})/PR"; http_content_type; content:"application/x-www-form-urlencoded"; depth:33; isdataat:!1,relative; threshold:type limit, count 1, seconds 600, track by_dst; classtype:trojan-activity; sid:2038612; rev:1; metadata:affected_product Mac_OSX, attack_target Client_Endpoint, created_at 2022_08_25, deployment Perimeter, former_category MALWARE, malware_family Shlayer, performance_impact Low, signature_severity Major, updated_at 2022_08_25;) |
|
YARA RULES |
|
private rule Macho { meta: description = "private rule to match Mach-O binaries" condition: uint32(0) == 0xfeedface or uint32(0) == 0xcefaedfe or uint32(0) == 0xfeedfacf or uint32(0) == 0xcffaedfe or uint32(0) == 0xcafebabe or uint32(0) == 0xbebafeca }
rule adload_2021_system_service { meta: description = "rule to catch Adload .system .service variant" author = "Phil Stokes, SentinelLabs" version = "1.0" last_modified = "2021-08-10" reference = "https://s1.ai/adload" strings: $a = { 48 8D 35 ?? ?? 00 00 48 8D 5D B8 BA B8 00 00 00 48 89 DF E8 ?? ?? FB FF 48 8B 43 08 48 2B 03 66 48 0F 6E C0 66 0F 62 05 ?? ?? 00 00 66 0F 5C 05 ?? ?? 00 00 0F 57 C9 66 0F 7C C0 48 8D 7D A0 0F 29 0F F2 0F 59 05 } condition: Macho and all of them } |
Associated indicators (IOCs)
The following technical indicators are associated with the reported intelligence. A list of indicators is also available in the OTX Pulse. Please note, the pulse may include other activities related but out of the scope of the report.
|
TYPE |
INDICATOR |
DESCRIPTION |
|
SHA256 |
d94f62ec4b6ffcec35d5e639d02a52ce226629a5eb3e2a7190174ea8d3b40b5b |
AdLoad sample |
|
SHA256 |
956aae546af632ea20123bfe659d57e0d5134e39cdb5489bd6f1ba5d8bbd0472 |
AdLoad sample |
|
SHA256 |
6587e61a8a7edb312da5798ffccf4a5ef227d3834389993b4df3ef0b173443dc |
AdLoad sample |
|
SHA256 |
3d063efde737b7b2e393926358cbb32469b76395e1a05e8c127a12e47550f264 |
AdLoad sample |
|
SHA256 |
2d595880cfb1691dd43de02d1a90273919f62311a7668ef078709eff2fd6bd87 |
AdLoad sample |
|
SHA256 |
7cb10a70fd25645a708c81f44bb1de2b6de39d583ae3a71df0913917ad1dffc3 |
AdLoad sample |
|
SHA256 |
4a7c9829590e1230a448dd7a4272b9fbfbafccf7043441967c2f68f6082dde32 |
AdLoad sample |
|
SHA256 |
68b6beb70bd547b75f2d36d70ca49f8b18542874480d39e33b09ee69eb1048b3 |
AdLoad sample |
|
SHA256 |
1904b705105db4550371d678f8161826b98b1a9fca139fa41628214ed816d2f5 |
AdLoad sample |
|
SHA256 |
2fb1d8e6454f43522f42675dcf415569e5df5d731e1d1390f793c282cce4a7aa |
AdLoad sample |
|
SHA256 |
ee9ebdb1d9a7424cd64905d39820b343c5f76e29c9cd60c0cdd3bfe069fb7d51 |
AdLoad sample |
|
SHA256 |
c7721ab85bad163576c166a0a71c0dbe4cc491dda68c5a5907fd1d8cac50780d |
AdLoad sample |
|
URL |
hxxp://m.skilledobject[.]com/a/rep |
AdLoad beacon |
|
URL |
hxxp://m.browseractivity[.]com/a/rep
|
AdLoad beacon |
|
URL |
hxxp://m.enchantedreign[.]com/a/rep
|
AdLoad beacon |
|
URL |
hxxp://m.activitycache[.]com/a/rep
|
AdLoad beacon |
|
URL |
hxxp://m.activityinput[.]com/a/rep
|
AdLoad beacon |
|
URL |
hxxp://m.opticalupdater[.]com/a/rep
|
AdLoad beacon |
|
URL |
hxxp://m.connectioncache[.]com/a/rep
|
AdLoad beacon |
|
URL |
hxxp://m.analyzerstate[.]com/a/rep
|
AdLoad beacon |
|
URL |
hxxp://m.essencecuration[.]com/a/rep
|
AdLoad beacon |
|
URL |
hxxp://m.microrotator[.]com/a/rep
|
AdLoad beacon |
|
URL |
hxxp://m.articlesagile[.]com/a/rep |
AdLoad beacon |
|
URL |
hxxp://m.progresshandler[.]com/a/rep
|
AdLoad beacon |
|
URL |
hxxp://m.originalrotator[.]com/a/rep
|
AdLoad beacon |
|
URL |
hxxp://m.productiveunit[.]com/a/rep
|
AdLoad beacon |
|
URL |
hxxp://api.toolenviroment[.]com/l
|
AdLoad beacon |
|
URL |
hxxp://api.inetfield[.]com/l
|
AdLoad beacon |
|
URL |
hxxp://api.operativeeng[.]com/l
|
AdLoad beacon |
|
URL |
hxxp://api.launchertasks[.]com/l
|
AdLoad beacon |
|
URL |
hxxp://api.launchelemnt[.]com/l
|
AdLoad beacon |
|
URL |
hxxp://api.validexplorer[.]com/l
|
AdLoad beacon |
|
URL |
hxxp://api.majorsprint[.]com/l
|
AdLoad beacon |
|
URL |
hxxp://api.essentialenumerator[.]com/l
|
AdLoad beacon |
|
URL |
hxxp://api.transactioneng[.]com/l
|
AdLoad beacon |
|
URL |
hxxp://api.macreationsapp[.]com/l
|
AdLoad beacon |
|
URL |
hxxp://api.commondevice[.]com/l
|
AdLoad beacon |
|
URL |
hxxp://api.compellingagent[.]com/l
|
AdLoad beacon |
|
URL |
hxxp://api.lookupindex[.]com/l
|
AdLoad beacon |
|
URL |
hxxp://api.practicalsync[.]com/l
|
AdLoad beacon |
|
URL |
hxxp://api.accessiblelist[.]com/l
|
AdLoad beacon |
|
URL |
hxxp://api.functionconfig[.]com/l |
AdLoad beacon |
|
Domain |
hxxps://vpnservices[.]live |
Proxy C&C to report infected systems |
|
Domain |
hxxps:// upgrader[.]live |
Proxy C&C to report infected systems |
|
Domain |
hxxp://bapp.pictureworld[.]co |
Proxy Node |
Mapped to MITRE ATT&CK
The findings of this report are mapped to the following MITRE ATT&CK Matrix techniques:
-
- TA0001: Initial Access
- T1189: Drive-by Compromise
- TA0003: Persistence
- T1543: Create or Modify System Process
- T1543.001: Launch Agent
- T1543: Create or Modify System Process
- TA0005: Defense Evasion
- T1140: Deobfuscate/Decode Files or Information
- T1497: Virtualization/Sandbox Evasion
- T1497.001: System Checks
- T1222: File and Directory Permissions Modification
- T1222.002: Linux and Mac File and Directory Permissions Modification
- T1553: Subvert Trust Controls
- T1553.001: Gatekeeper Bypass
- T1562: Impair Defenses
- T1562.001: Disable or Modify Tools
- TA0007: Discovery
- T1082: System Information Discovery
- TA0011: Command and Control
- T1090: Proxy
- T1571: Non-Standard Port
- TA0040: Impact
- T1496: Resource Hijacking
- TA0001: Initial Access