This blog was written jointly with Eduardo Ocete.
Executive summary
Several vulnerabilities for Java Spring framework have been disclosed in the last hours and classified as similar as the vulnerability that caused the Log4Shell incident at the end of 2021. However, as of the publishing of this report, the still ongoing disclosures and events on these vulnerabilities suggest they are not as severe as their predecessor.
Key takeaways:
- A vulnerability in Spring Cloud Function (CVE-2022-22963) allows adversaries to perform remote code execution (RCE) with only an HTTP request, and the vulnerability affects the majority of unpatched systems. Spring Cloud Function is a project that provides developers cloud-agnostic tools for microservice-based architecture, cloud-based native development, and more.
- A vulnerability in Spring Core (CVE-2022-22965) also allows adversaries to perform RCE with a single HTTP request. For the leaked proof of concept (PoC) to work, the vulnerability requires the application to run on Tomcat as a WAR deployment which is not present in a default installation and lowers the number of vulnerable systems. However, the nature of the vulnerability is more general, so there could be other potential exploitable scenarios.
In accordance with the Cybersecurity Information Sharing Act of 2015, AT&T is sharing the cyber threat indicator information provided herein exclusively for a cybersecurity purpose to combat cybersecurity threats.
Analysis
At the end of March 2022, several members of the cybersecurity community were discovered spreading news about a potential new vulnerability in Java Spring systems that is easily exploitable and affecting millions of systems. This vulnerability has the potential to originate a new Log4Shell incident.
First, it is important to clarify that the comparisons at this point appear to be searching for sensationalism and spreading panic, instead of providing actionable information. Additionally, two similar vulnerabilities in the Spring framework were disclosed around the same time, adding confusion to the mix. What has been observed by the AT&T Alien Labs™ threat intelligence team as of the publishing of this article is included below.
Spring Cloud Function (CVE-2022-22963)
A vulnerability in Spring Cloud Function has been identified as CVE-2022-22963, and this vulnerability can lead to remote code execution (RCE). The following Spring Cloud Function versions are impacted:
- 3.1.6
- 3.2.2
- Older unsupported versions are also affected
In addition to the vulnerable version, JDK >= 9 must be in use in order for the application to be vulnerable.
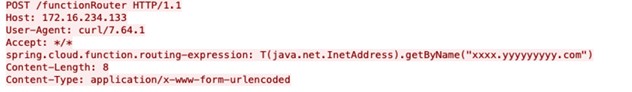
The vulnerability is triggered when using the routing functionality. By providing a specially crafted Spring Expression Language (SPeL) as a routing expression, an attacker can access local resources and execute commands in the host. Therefore, this CVE allows an HTTP request header, containing a spring.cloud.function.routing-expression object with a SPeL expression, to be evaluated through the StandardEvaluationContext, leading to an arbitrary RCE.
Figure 1. Exploitation attempt.
The vulnerability has been assigned a CVSS of 9.0 which means high severity. Exploitation of the vulnerability may lead to a total compromise of the host or the container, and so patching is highly advised. In order to mitigate the vulnerability developers should update Spring Cloud Function to the newest versions, 3.1.7 and 3.2.3, where the issue has already been patched.
AT&T Alien Labs has identified several attempts of exploitation, which we believe are researchers trying to identify how prevailing the vulnerabilities actually is, since the exploitation attempts carried canarytokens as unique payload. Nevertheless, the team will continue to closely monitor the activity, as new scanning activity appears.
Spring Core (CVE-2022-22965)
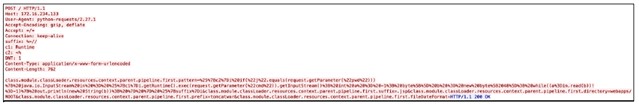
A vulnerability in Spring Core was tweeted by one of the researchers who first disclosed the Log4Shell vulnerability. The researcher then rapidly deleted the tweet. This vulnerability was originally published without a CVE associated with it, and it is being publicly referred to as “Spring4Shell.” One of the first observed proof of concepts (PoC) was shared by vx-underground on March 30, 2022. It works against Spring’s sample code “Handling Form Submission.” The PoC consists of a single POST request carrying in its payload a jsp webshell that will be dropped in the vulnerable system.
Figure 2. Exploitation attempt following PoC.
Spring has confirmed the vulnerability and has stated that the leak occurred ahead of the CVE publication. The vulnerability has been assigned CVE-2022-22965. As per Spring:
“...The vulnerability impacts Spring MVC and Spring WebFlux applications running on JDK 9+. The specific exploit requires the application to run on Tomcat as a WAR deployment. If the application is deployed as a Spring Boot executable jar, i.e. the default, it is not vulnerable to the exploit. However, the nature of the vulnerability is more general, and there may be other ways to exploit it.”
From the statement above, the specific scenario for the leaked PoC to work would have to match the following conditions:
- JDK >=9
- Apache Tomcat as the Servlet container
- Packaged as WAR
- spring-webmvc or spring-webflux dependency
However, the scope of the vulnerability is wider, and there could be other exploitable scenarios.
Spring has released new versions for Spring Framework addressing the vulnerability, so updating to versions
5.3.18 and 5.2.20 (already available in Maven Central) should be a priority in order to mitigate the RCE. The new versions for Spring Boot with the patch for CVE-2022-22965 are still under development.
As an alternative mitigation, the suggested workaround is to extend RequestMappingHandlerAdapter to update the WebDataBinder at the end, after all other initialization. To do so, a Spring Boot application can declare a WebMvcRegistrations bean (Spring MVC) or a WebFluxRegistrations bean (Spring WebFlux). At the “Suggested Workarounds” section of the Spring statement one can find an implementation example of such workaround.
According to a publication by Peking University, this vulnerability has been observed being exploited in the wild. However, AT&T Alien Labs has not identified heavy scanning activity on our honeypots for this vulnerability, nor exploitation attempts.
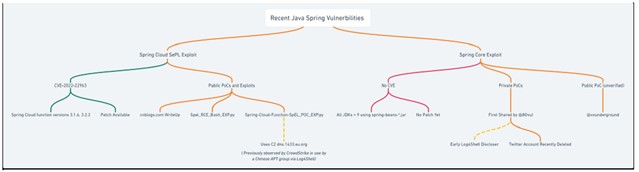
Finally, and just to provide a graphical representation of these vulnerabilities, below is a diagram shared by a CTI researcher from Sophos.
Figure 3. Java Spring vulnerability diagram.
Conclusion
Log4Shell was very impactful at the end of 2021, based on the number of exposed vulnerable devices and the facility of its exploitation. These recently disclosed Java Spring vulnerabilities remind us in the cyber community of lessons learned during the Log4Shell incident. Thus, these vulnerabilities have received a quick response by the entire cybersecurity community which is collaborating and sharing available information as soon as possible.
Alien Labs will keep monitoring the situation and will update the corresponding OTX Pulses to keep our customers protected.
Appendix A. Detection methods
The following associated detection methods are in use by Alien Labs. They can be used by readers to tune or deploy detections in their own environments or for aiding additional research.
|
SURICATA IDS SIGNATURES |
alert http $EXTERNAL_NET any -> $HOME_NET any (msg:"AV EXPLOIT Spring Cloud RCE (CVE-2022-22963)"; flow:established,to_server; content:"POST"; http_method; content:"spring.cloud.function.routing-expression"; http_header; pcre:"/(getRuntime|getByName|InetAddress|exec)/HR"; reference:url,sysdig.com/blog/cve-2022-22963-spring-cloud; classtype:attempted-admin; sid:4002725; rev:1;) |
alert http $EXTERNAL_NET any -> $HOME_NET any (msg:"AV INFO Spring Core RCE Scanning Activity (March 2022)"; flow:established,to_server; content:"POST"; http_method; content:"class.module.classLoader.resources.context.parent.pipeline.first.pattern"; http_client_body; startswith; reference:url,github.com/TheGejr/SpringShell; classtype:attempted-admin; sid:4002726; rev:1;) |
alert http $EXTERNAL_NET any -> $HOME_NET any (msg:"AV EXPLOIT Spring Cloud RCE (CVE-2022-22963)"; flow:established,to_server; content:"POST"; http_method; content:"spring.cloud.function.routing-expression"; http_header; pcre:"/(getRuntime|getByName|InetAddress|exec)/HR"; reference:url,sysdig.com/blog/cve-2022-22963-spring-cloud; classtype:attempted-admin; sid:4002727; rev:1;) |
|
AGENT SIGNATURES |
|
Java Process Spawning Scripting Process |
|
Java Process Spawning WMIC |
|
Java Process Spawning Scripting Process via Commandline (For Jenkins servers) |
|
Suspicious process executed by Jenkins Groovy scripts (For Jenkins servers) |
|
Suspicious command executed by a Java listening process (For Linux servers) |
Appendix C. Mapped to MITRE ATT&CK
The findings of this report are mapped to the following MITRE ATT&CK Matrix techniques:
- TA0001: Initial Access
- T1190: Exploit Public-Facing Application
Appendix D. Reporting context
The following source was used by the report author(s) during the collection and analysis process associated with this intelligence report.
1. AT&T Alien Labs Intelligence and Telemetry
Alien Labs rates sources based on the Intelligence source and information reliability rating system to assess the reliability of the source and the assessed level of confidence we place on the information distributed. The following chart contains the range of possibilities, and the selection applied to this report is A1.
Source reliability
|
RATING |
DESCRIPTION |
|
A - Reliable |
No doubt about the source's authenticity, trustworthiness, or competency. History of complete reliability. |
|
B - Usually Reliable |
Minor doubts. History of mostly valid information. |
|
C - Fairly Reliable |
Doubts. Provided valid information in the past. |
|
D - Not Usually Reliable |
Significant doubts. Provided valid information in the past. |
|
E - Unreliable |
Lacks authenticity, trustworthiness, and competency. History of invalid information. |
|
F - Reliability Unknown |
Insufficient information to evaluate reliability. May or may not be reliable. |
Information reliability
|
RATING |
DESCRIPTION |
|
1 - Confirmed |
Logical, consistent with other relevant information, confirmed by independent sources. |
|
2 - Probably True |
Logical, consistent with other relevant information, not confirmed. |
|
3 - Possibly True |
Reasonably logical, agrees with some relevant information, not confirmed. |
|
4 - Doubtfully True |
Not logical but possible, no other information on the subject, not confirmed. |
|
5 - Improbable |
Not logical, contradicted by other relevant information. |
|
6 - Cannot be judged |
The validity of the information can not be determined. |
Feedback
AT&T Alien Labs welcomes feedback about the reported intelligence and delivery process. Please contact the Alien Labs report author or contact labs@alienvault.com.