Executive summary
AT&T Alien Labs recently analyzed the Linux version of the Darkside ransomware, one of the most active ransomware in the last quarter. Shortly after hitting Colonial Pipeline, Darkside developers announced they would be closing operations.
Key Points:
- Unlike common Linux ransomwares which mostly zip files with a password, Darkside encrypts files using crypto libraries. This likely makes recovery impossible without the encryption key, if properly implemented.
Background
Linux and UNIX servers have always been a preferred option for servers and data centers, likely due to the small attack surface of the servers, tight configurations, and lack of user interaction. However, they are often set up and then forgotten, left without detection or protection mechanisms. This makes them very attractive to attackers. By infecting unprotected virtualization servers, attackers can perform devastating attacks on companies, taking down all the services of a company with a single infection.
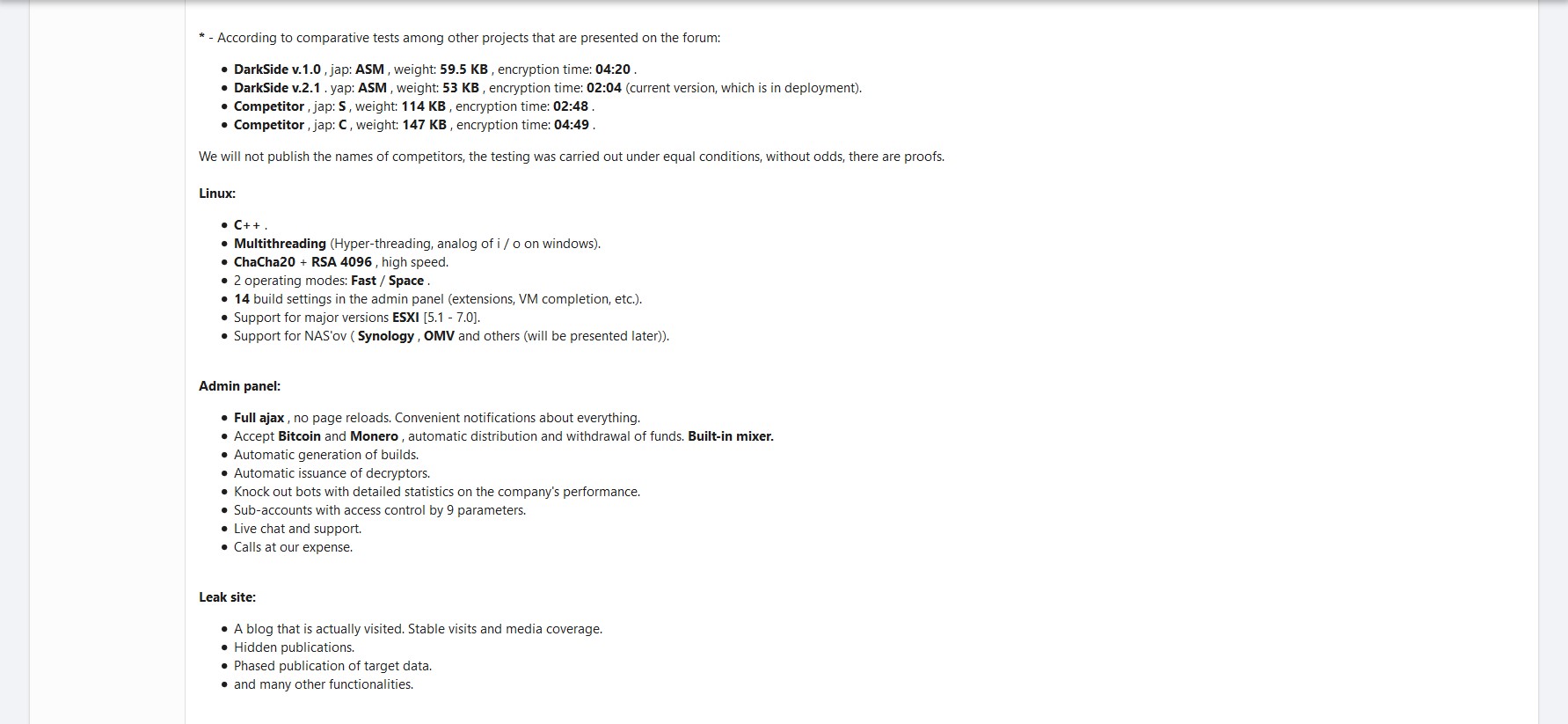
First discovered in August 2020, Darkside is a group that operates ransomware as a service (RaaS), and attacks by their network of affiliates have infected many companies worldwide. The most high profile infection happened when a Darkside affiliate hit the network of one of the major oil pipeline companies in the US, Colonial Pipeline, causing the company to shut down operations for days. After this attack — likely due to the fact that it drew unwanted levels of attention to the group globally — the malware authors announced publicly the closure of their service. Nevertheless, there is evidence that the group has completed a Linux version of its malware that is targeting ESXi, servers hosting VMware virtual machines. To this point, the authors announced the Darkside 2.0 version with Linux capabilities on March 9, 2021 in the XSS Forum:
Figure 1. Example of Linux version features and information announced by malware authors on XSS Forum.
Analysis
Unlike the Windows version of the malware that targets any Windows endpoint, Darkside Linux version is mostly targeting ESXi servers. Its default configuration includes the root path of ESX server machines. Targeted extensions are 'vmdk', 'log', 'vmem', 'vmsn' that are used in ESX servers for saving virtual machines information, data, and logs.
The malware is quite informative and prints to the screen most of the actions it performs, which is an uncommon behavior for malware. This could imply that the malware is being deployed manually. The malware is written in C++ and it’s also using several open-source libraries that were imported and compiled with the malware code into one binary. Some of these libraries are: crypto++ used for encryption, boost used for logging purposes, and curl used for HTTP requests. The use of these libraries enables the final binary to be a 2.7MB file size. For example, to communicate with an infected machine with its Command and Control (C&C), the malware uses libcurl functions that were compiled with the rest of the code.
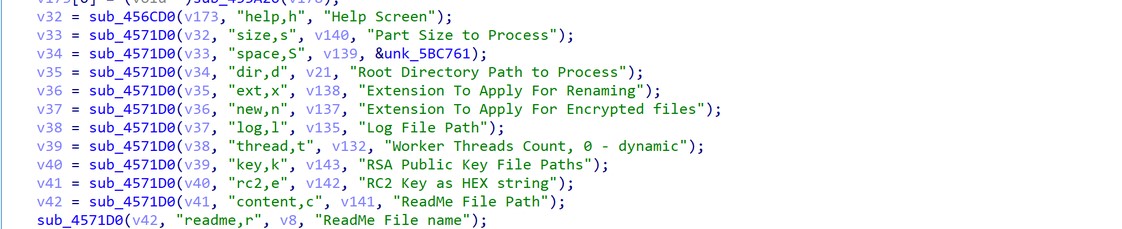
In addition, the malware supports command line parameters during execution to replace almost, if not all, of the default configuration variables.
Figure 2. Parameters supported by the malware.
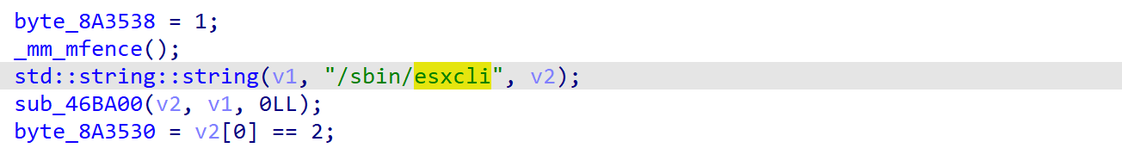
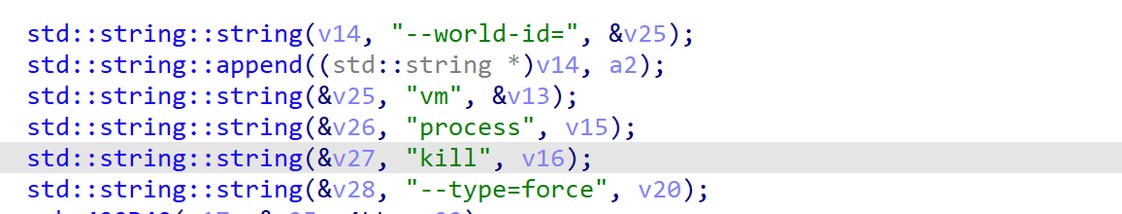
The malware also supports shutting down virtual machines by executing the esxcli commands, a special console on ESX servers that allows it to interact with virtual machines from the command line.
Figure 3. Abusing esxcli command.
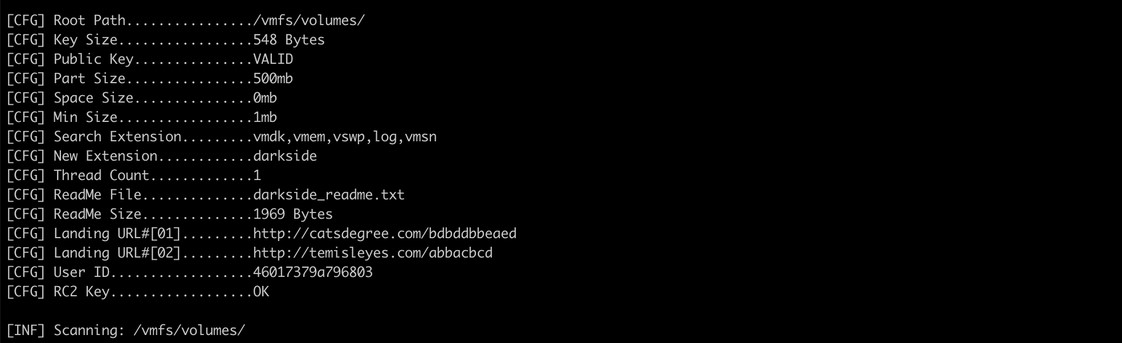
When executed, the malware prints its configuration to the terminal. This includes the root path to encrypt, RSA key information, targeted file extensions to encrypt, C2 addresses, and more, as seen in figure 4.
Figure 4. Darkside configuration.
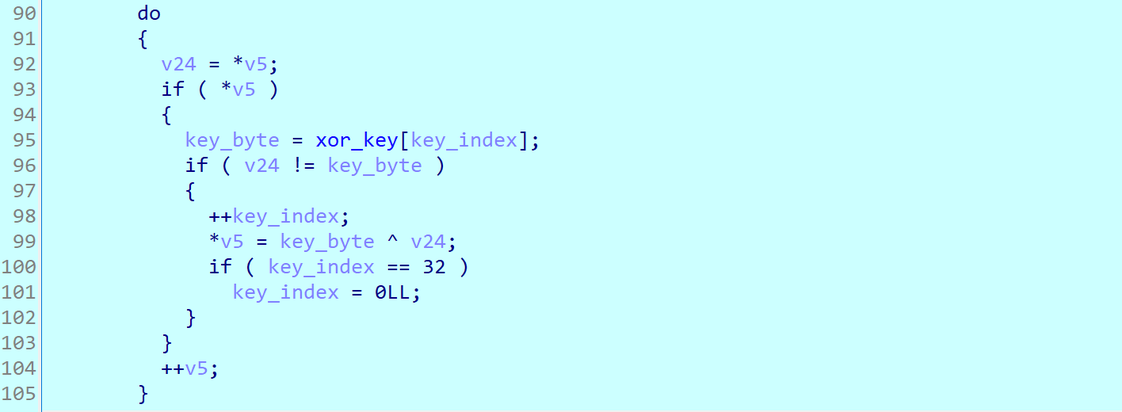
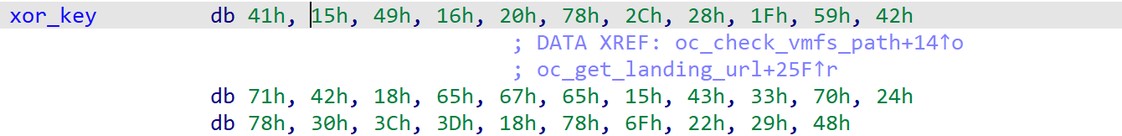
The C&C addresses are encrypted using a rotated XOR key, which will be decrypted when the malware is executed. The decrypted addresses can be found in Appendix A:
Figure 5. Decryption loop to extract C&C.
Figure 6. Malware XOR key.
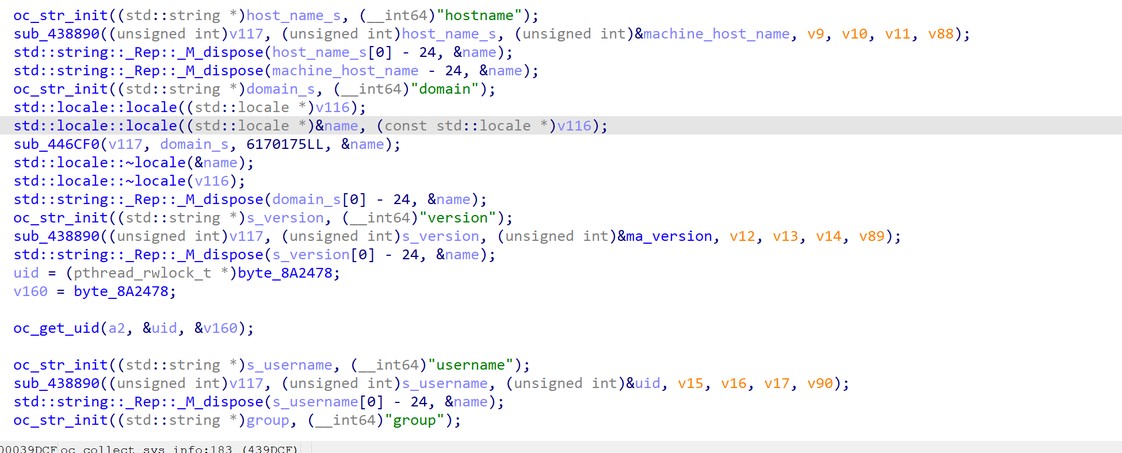
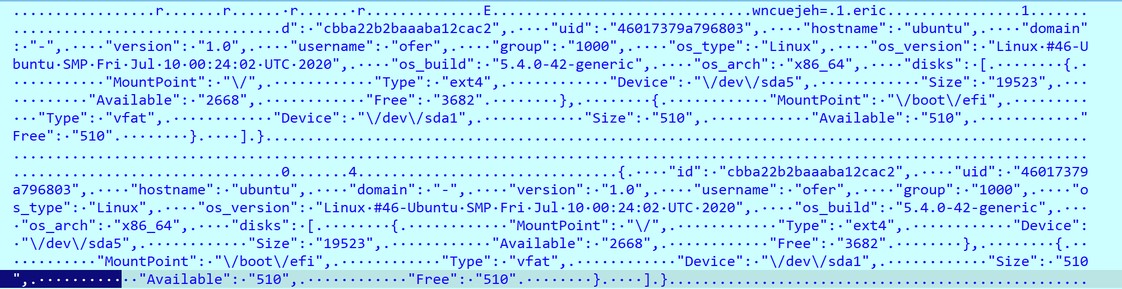
The malware will then count the files to be encrypted, and it collects information from the infected machine, sending it to the C&C server after encryption. The exfiltrated information includes: user name, OS version, hostname, build, and more:
Figure 7. Collecting system information.
Figure 8 shows an example of the information collected from an infected machine.
Figure 8. Example of collected system information.
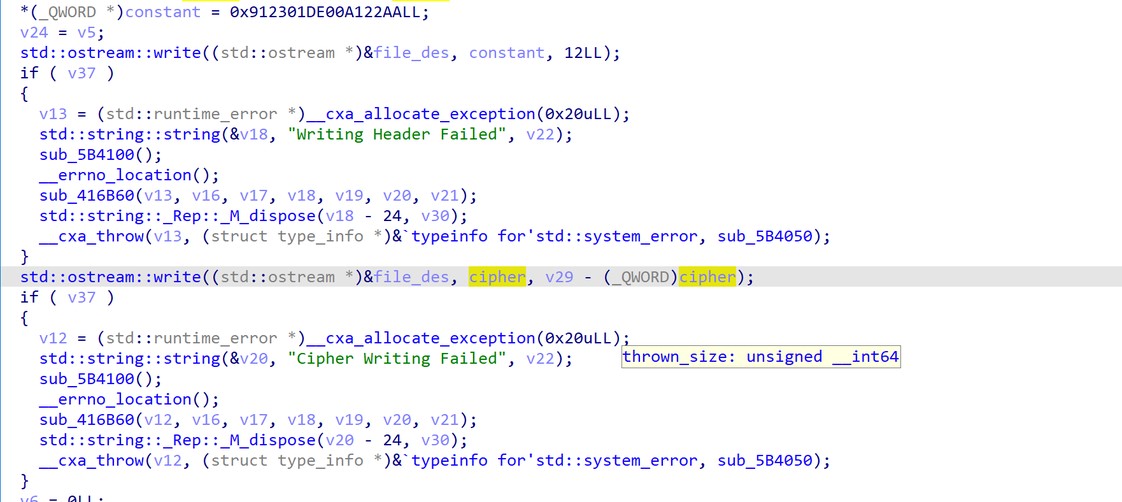
The malware will loop through the files to be encrypted and then encrypt them using ChaCha20 with the RSA 4096 key taken from the configuration. After encryption, the malware will add a tail at the end of the encrypted file that includes a constant and the cipher, as seen in figure 9.
Figure 9. Adding header after successful encryption
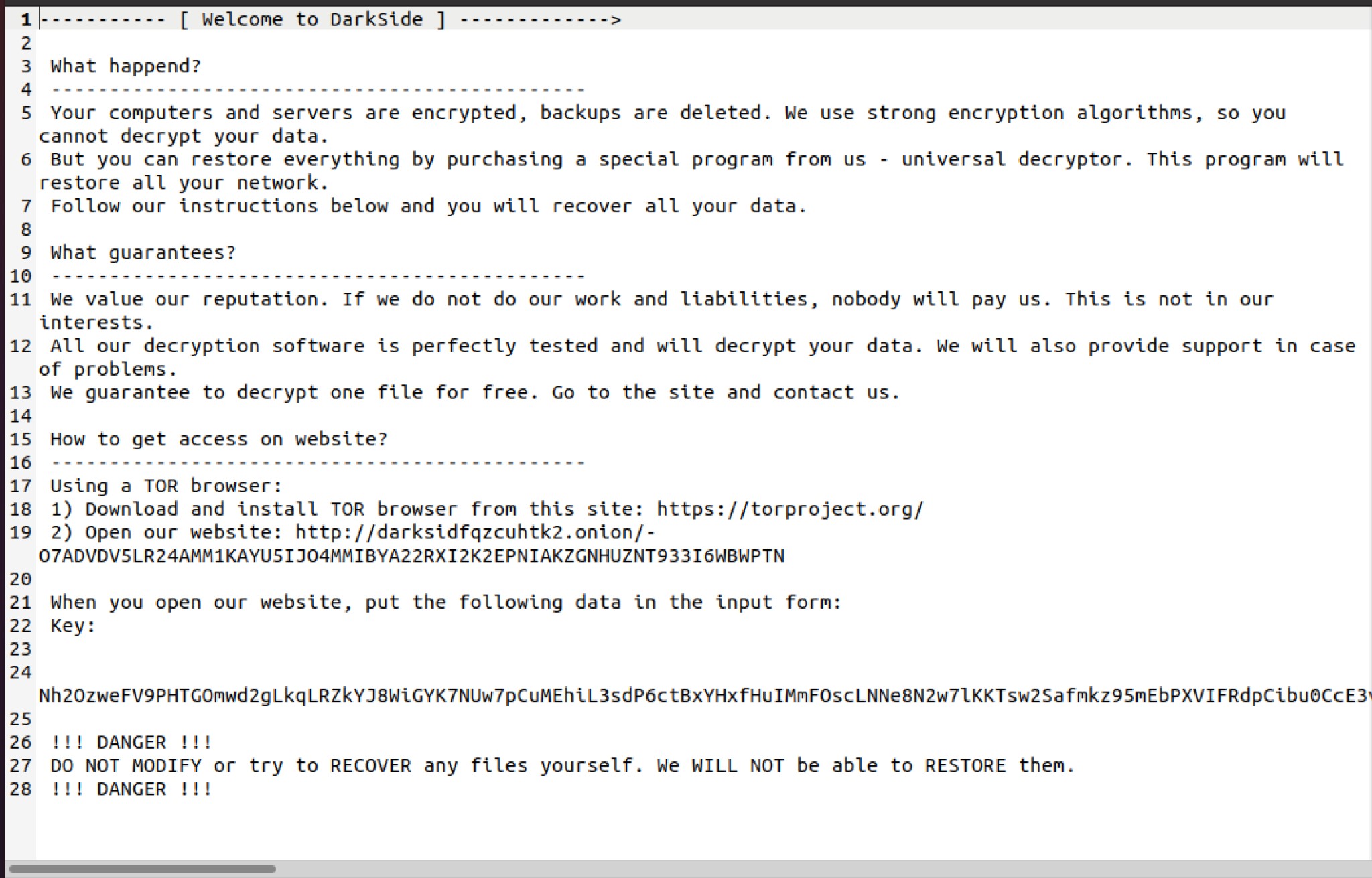
After encryption, the malware creates a ransom note in each folder where files were encrypted.
Figure 10. Ransom note
Recommended actions
- Keep software up to date with security updates.
- Carefully monitor and manage suspicious emails.
- Use a backup system to backup server files.
- Install Antivirus and/or endpoint detection and response (EDR) in all endpoints.
- Make sure two-factor authentication is enabled in all services.
Conclusion
Ransomwares remains one of the biggest threats to companies globally, especially when it comes to virtual machine servers that may contain multiple machines that are primary targets for Darkside malware.
Darkside will search files on the main folder of the infected server and encrypt any file that matches its configuration limits. It will also collect information from the system and send it to its C&C.
Detection methods
The following associated detection methods are in use by AT&T Alien Labs. They can be used by readers to tune or deploy detections in their own environments or for aiding additional research.
|
YARA RULES |
rule Darkside_linux
{
meta:
description = "darkside ransomware linux version"
author = "Alienvault Labs"
copyright = "Alienvault Inc. 2021"
strings:
$s1 = "[END] Remove Self"
$s2 = "[CFG] Landing URL#["
$s3 = "Welcome to DarkSide"
$dec_loop = {0F B6 02 84 C0 74 1C 0F B6 B1 DF A7 89 00 40 38 F0 74 10 48 83 C1 01 31 F0 48 83 F9 20 88 02 49 0F 44 C8}
condition:
uint32(0) == 0x464C457F and all of them
}
|
Associated Indicators of Compromise (IOCs)
The following technical indicators are associated with the reported intelligence. A list of indicators is also available in the OTX Pulse. Please note, the pulse may include other activities related but out of the scope of the report.
|
TYPE |
INDICATOR |
DESCRIPTION |
|
DOMAIN |
http://catsdegree[.]com/ |
C&C |
|
DOMAIN |
http://temisleyes[.]com/ |
C&C |
|
DOMAIN |
http://securebestapp20[.]com |
C&C |
|
SHA256 |
9cc3c217e3790f3247a0c0d3d18d6917701571a8526159e942d0fffb848acffb |
Darkside Linux version |
|
SHA256 |
984ce69083f2865ce90b48569291982e786980aeef83345953276adfcbbeece8 |
Darkside Linux version |
|
SHA256 |
c93e6237abf041bc2530ccb510dd016ef1cc6847d43bf023351dce2a96fdc33b |
Darkside Linux version |
Mapped to MITRE ATT&CK
The findings of this report are mapped to the following MITRE ATT&CK Matrix techniques:
- TA0043: Reconnaissance
- TA1592: Gather Victim Host Information
- TA0042: Resource Development
- T1583: Acquire Infrastructure
- T1587: Develop Capabilities
- TA0040: Impact
- T1486: Data Encrypted for Impact
- TA0005: Defense Evasion
- T1027: Obfuscated Files or Information
- TA0007: Discovery
- T1083: File and Directory Discovery
- TA0009: Collection
- T1005: Data from Local System
- TA0011: Command and Control
- T1001: Data Obfuscation
- T1041: Exfiltration Over C2 Channel